pfblocker not blocking/working
-
@zachelle said in pfblocker not blocking/working:
assign the interfaces and setup DHCP servers for the vlans.
On these interfaces, devices did get a lease. What was the DNS IP, part of the lease, that it received ?
If the device is Microsoft base, typeipconfig /allOther OSs : You'll know the command.
Next test : even if a device got a local IP to use for it's DNS needs, software on the device can still decide to look elsewhere for it's DNS needs.
"You not the only that doesn't want to use the classic resolving, but to send DNS requests to somewhere else " : most browsers will, out of the box, use their own DNS source, and not the local pfSense (= unbound, thus filtered by pfBlockerng).
" : most browsers will, out of the box, use their own DNS source, and not the local pfSense (= unbound, thus filtered by pfBlockerng).Several ways to check :
Shut down unbound on the dashboard GUI. If your browser on your LAN is still working just fine, you'll know it's not using pfSense for its DNS needs. So, the DNS traffic can be filtered, as it bypasses the filter completely.Traffic that is handled by unbound/pfBlocker can be seen here ;
Firewall > pfBlockerNG > Log Browser, keep "Log/File type:" at "Log Files" and for "Log/File selection:" select "dns_reply.log".
Now, look at a site like "www.knmi.nl" in your browser.
Refresh the page / file you were looking at, and if unbound resolved "knmi.nl" for you, you should see it :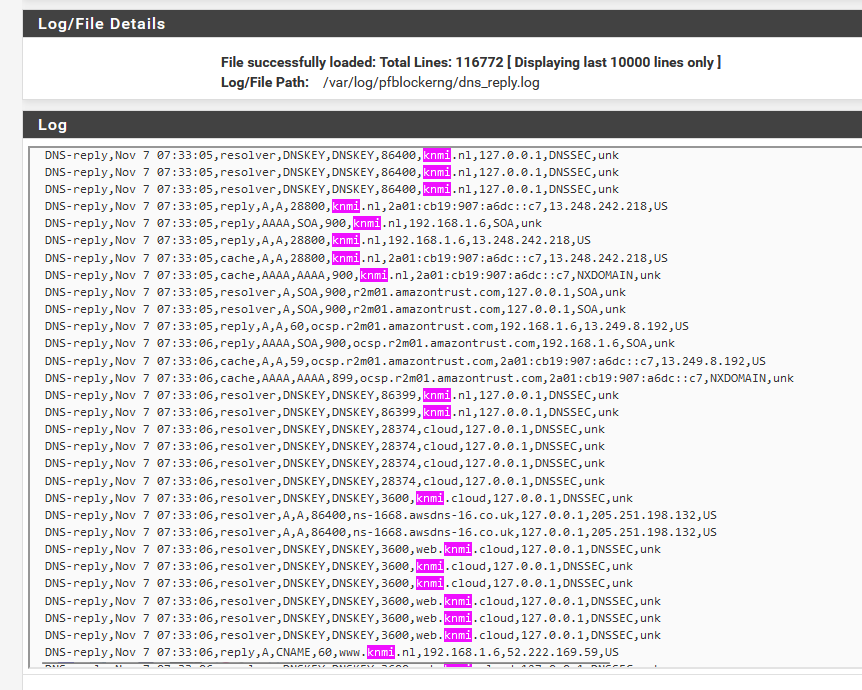
If needed, Next step :
Get a host name that is blocked.
For example : you are using "DNSBL_ADs_Basic", so : go to Firewall > pfBlockerNG > DNSBL > DNSBL Groups and 'edit' the "ADs Basic" entry.
You'll find the DNSBL feed : https://raw.githubusercontent.com/StevenBlack/hosts/master/hostsOpen it, pack a host name after :
#===================================== # Title: Hosts contributed by Steven Black # http://stevenblack.comand use it in your browser.
What happened ?
What did the pfBlockerNG dns_rply.log showed (after screen refresh) ? -
Thank you very much. I am at work right now but once I get home I will try everything. One additional question when setting up the dns under general setup and on the dhcp server should I leave it blank on both or should I state the dns on both sides?
-
@zachelle said in pfblocker not blocking/working:
when setting up the dns under general setup
This page :
I named pfSEnse pfSEnse.
And I entered a domain name.
Nothing else is needed of there, as I recall (from 12 years ago ?)I didn't change DHCP server = LAN neither :

(well, ok, I changed the pool size somewhat ).
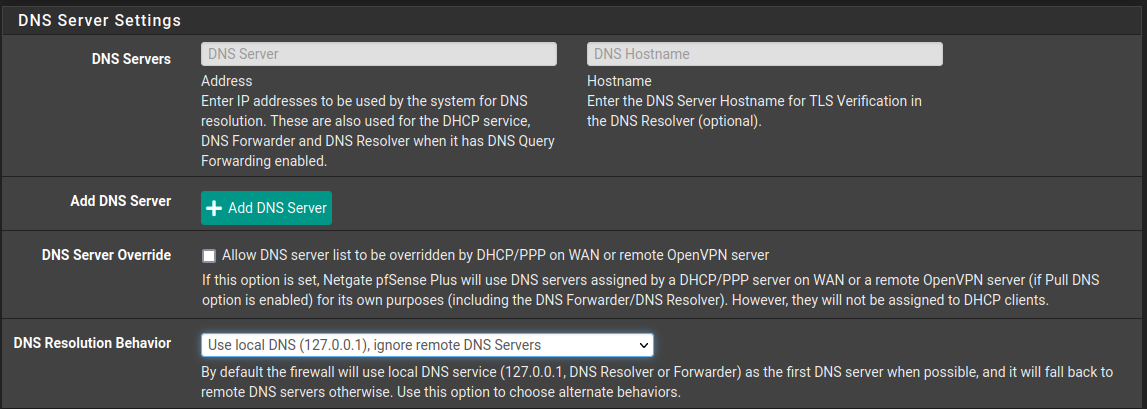
No need to add something like "DNS", as the DHCP server will include the LAN interface IP as a DNS, and that ok - unbound (the DNS resolver) is set to
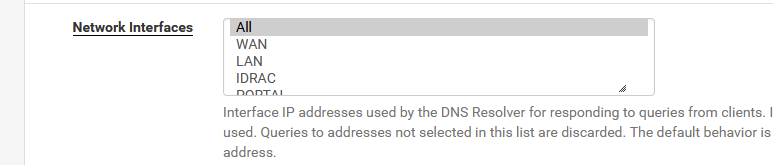
which means it listens on "All" pfSense interfaces.
-
Same settings for me. The only exception is my DNS resolution. Also have DNSSEC checked. I cant remember if its the stock setting for Resolver or not.
-
@Gertjan @Uglybrian
I did a factory reset and did all the configuration from scratch again. Per your advise I did not specified andy DNS on general setup and on the dhcp server settings. This actually worked. I picked a few addresses from two different lists and it is blocking themSomething I did was that on the DNSBL ADs basic group I added a few sources that I was using in pihole. The total number went up but in comparison with the packets resolved by unbound the percentage of blocking is minimal.
On the photo also you can see that the pfb has no packets. Since it says IP the way I think it works is by inputting the ip address itself and no the web address right? Does this means that is not working?
After all the changes I did force/reload action.
I tried to verify the dns reply logs but it is empty.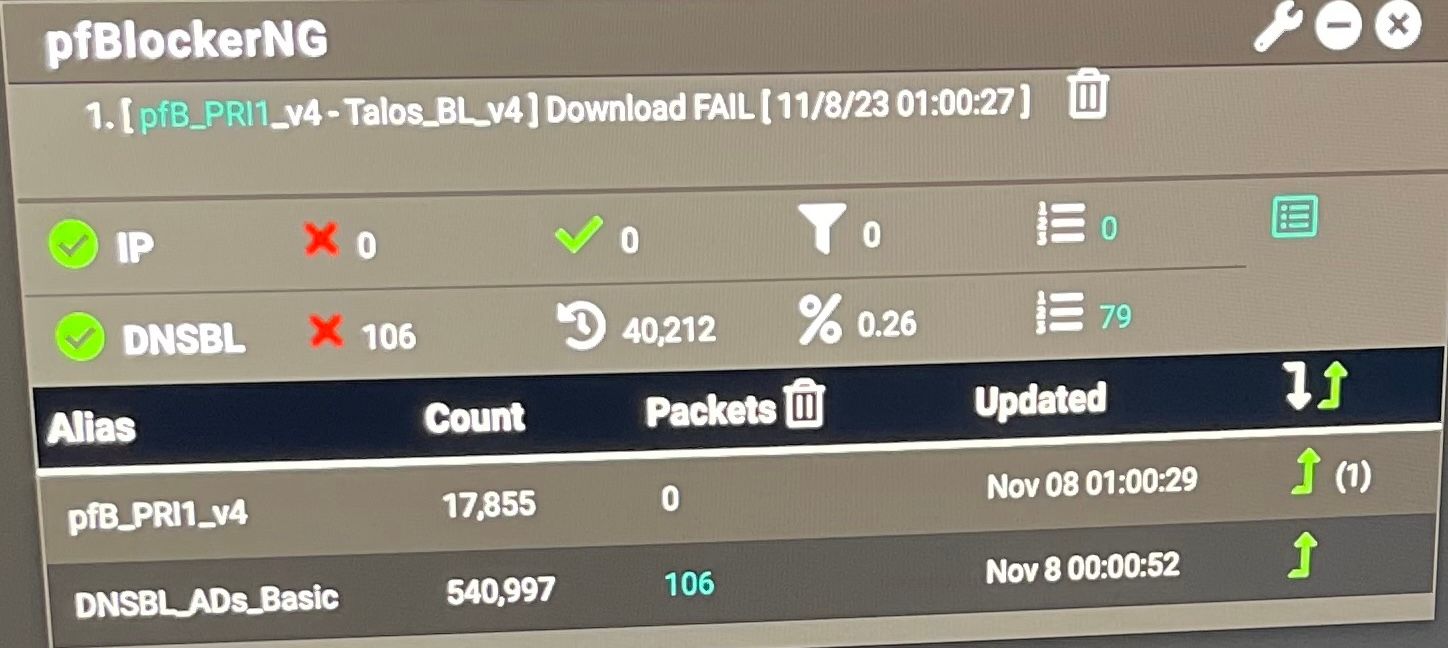 Thank you very much for your help.
Thank you very much for your help. -
@zachelle said in pfblocker not blocking/working:
Does this means that is not working?
I'm not sure.
Your saying that the list isn't (maybe) working, and your showing that it failed to download the list.
I tend to say : something that isn't there, can't work ^^
If the download error was a incidental download error, then you can dismiss it - click on the appropriate symbol (the waste bin).To check if the "pfB_PRI1_v4" works : like the DNDBL list : open it up, and see what it is. (Its a list with Ips and IP networks) Pick an IPv4 and do something with, for example, ping it, or use the IPv4 in the browser address bar like http://a.b.c.d
The list settings also determine what has been done with list : is it present on the LAN interface, which means it is blocking attempts from the IP to you, or present on the LAN interface, which blocks you from visiting it ?Not showing up any hits isn't a bad think : you not visiting any probably rubbish sites, that's a good news actually.
@zachelle said in pfblocker not blocking/working:
I tried to verify the dns reply logs but it is empty.
Empty ? It can't be empty.
That file lists all the DNS requests from pfSense itself (very little) and all devices attached to your LAN. It's the list with DNS requests that the resolver (unbound) received.
Again, that is, if these devices are using pfSense as their DNS source.
For example mine has 16 thousand lines now at 07h00 AM, and it started at line 1 last midnight.You should see something like this :
DNS-reply,Nov 8 07:13:06,reply,A,CNAME,60,z-p42-chat-e2ee-ig.facebook.com,192.168.2.93,185.60.219.175,FR DNS-reply,Nov 8 07:13:06,cache,AAAA,AAAA,2392,sync-1-us-west1-g.sync.services.mozilla.com,2a01:cb19:907:a6dc::c7,NXDOMAIN,unk DNS-reply,Nov 8 07:13:06,cache,AAAA,AAAA,2392,sync-1-us-west1-g.sync.services.mozilla.com,2a01:cb19:907:a6dc::c7,NXDOMAIN,unk DNS-reply,Nov 8 07:13:07,reply,A,CNAME,20,logs.netflix.com,192.168.1.34,52.209.135.12,IE DNS-reply,Nov 8 07:13:09,reply,A,CNAME,60,edge-mqtt.facebook.com,192.168.2.93,185.60.219.18,FR DNS-reply,Nov 8 07:13:09,servfail,HTTPS,HTTPS,Unk,mesure.streaming.estat.com,192.168.2.107,ServFail,unk DNS-reply,Nov 8 07:13:10,reply,A,CNAME,39,web.facebook.com,192.168.2.93,185.60.219.3,FRSome of the request came from my 192.168.2.x network which is a captive portal
My company LAN uses 192.168.1.x
All this within the same 60 seconds : 08h17 (within 5 seconds).O, if you have just one PC attached to your pfSense, then it is possible you see 'nothing ' for several minutes. ( launch Microsoft Edge and the dns_reply log will grow hundreds of entries in a split second )
If you see nothing : that's a solid proof you PC isn't using pfSense as a DNS server (so no need to use pfBlockerng neither ).
). -
just on the Talos feed, it is notorious for failing the download.
pfBlocker, will / should be using the last version of the file it downloaded (if it has one).https://forum.netgate.com/topic/178166/talos_bl-erros?_=1699443922118
to test the feed, goto the feeds selection screen,

Click on Talos_BL (the link) - should show
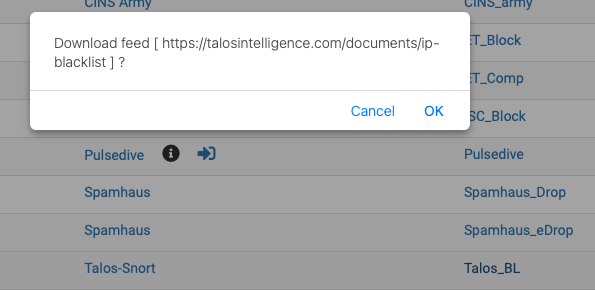
what happens when you download it ? (it should display the IP list in the browser)
I have not seen the list fail for some time. Failure of this list use to be an almost multiple time pre day event
-
I myself never got very many hits on the PFB/IP filter. Maybe one hit a month. Eventually, I stopped using it.
I also had a lot of download failure with the Talos block list. It worked fine for a few months and then start acting up with failed downloads. Then it would start working again and be fine for a few more months before the cycle came back around. After the third cycle, I just turned off that list. -
@Uglybrian said in pfblocker not blocking/working:
myself never got very many hits on the PFB/IP filter
Would be very dependant on the actual use case with so many different individual case.. IP filter lists however work well, but can also be very dependant on rule order.
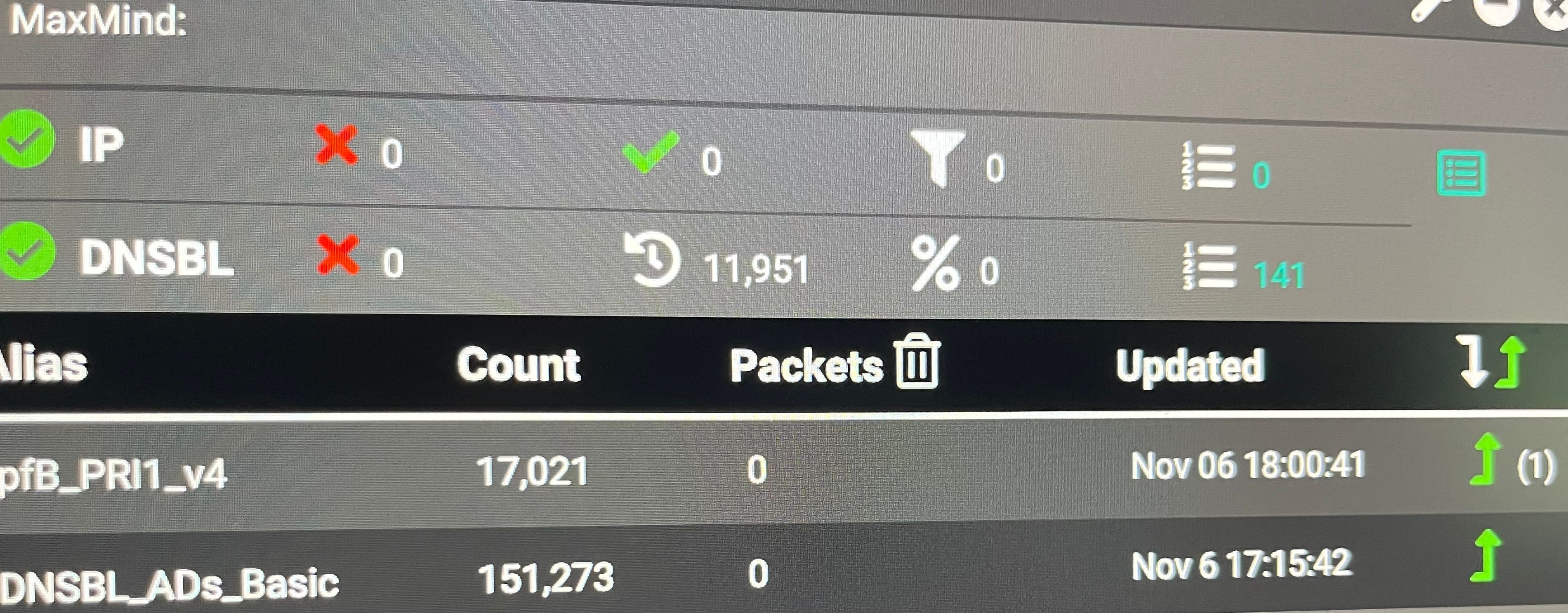
These are all in the last 2 days (since last boot, except DNSBL as those counters are not cleared on a reboot)
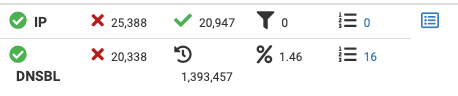
All of these are IP lists (except the last entry which is DNSBL)
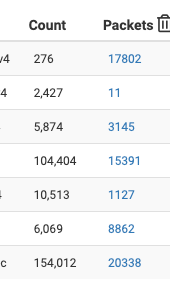
@Uglybrian said in pfblocker not blocking/working:
It worked fine for a few months and then start acting up with failed downloads. Then it would start working again
Yup
-
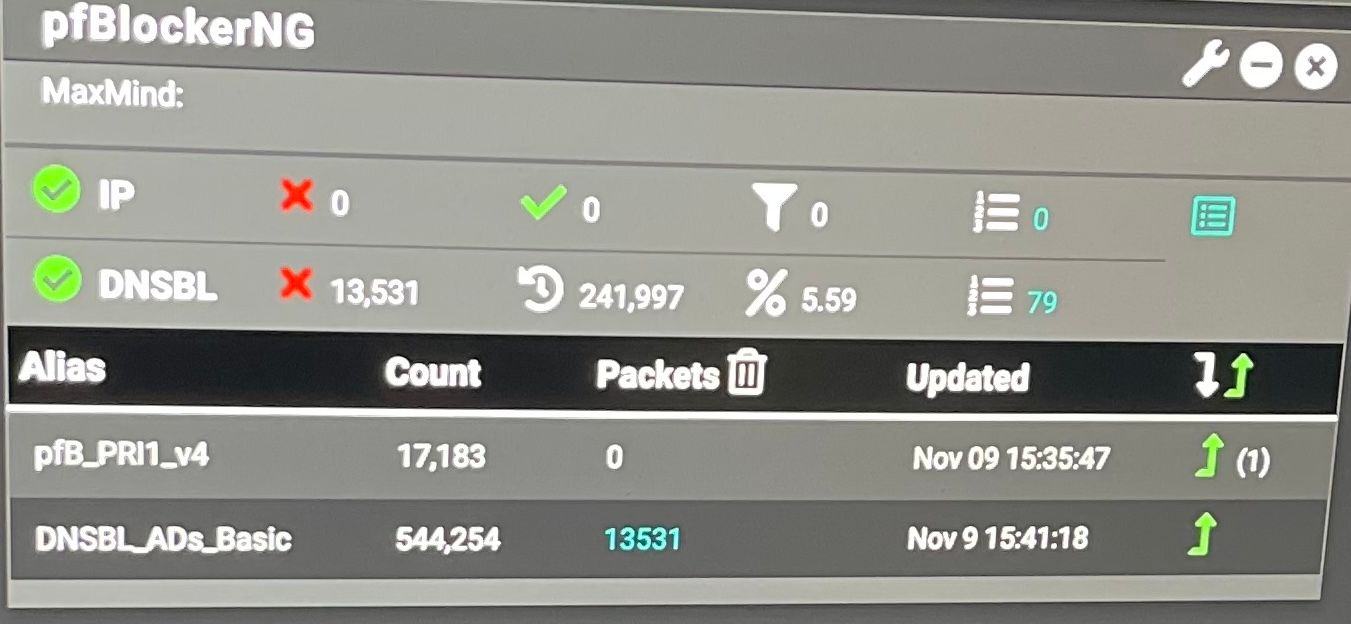
As you can see on the photo is it actually dong some blocking now. The talos keeps failing the download but since the DNSBL is working it's good I suppose.
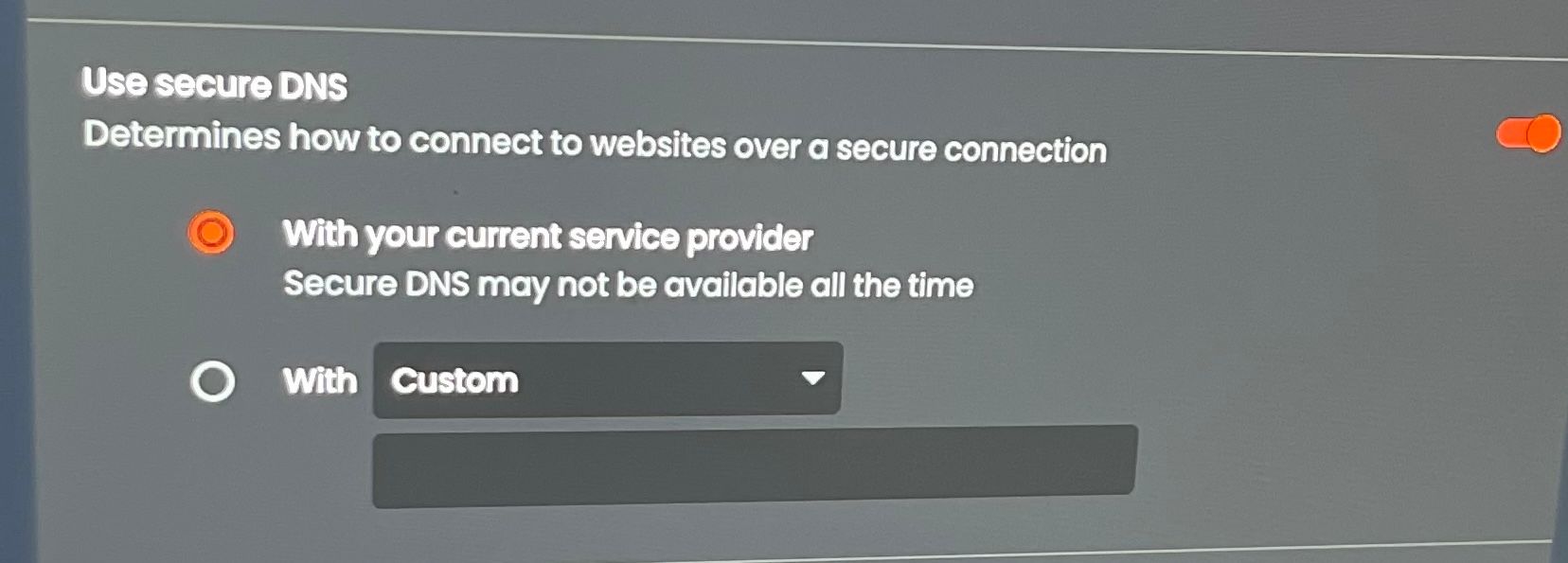
I did a test and stopped the unbound on the pfblocker and the browser still worked. I am including a photo of a dns setting of the browswer. It is turned on but I tried switching it off and still works. I am not sure where to look.
On the firewall dashboard and the pfblocker settings it is showing 127 for dns and localhost respectively. So I think this means that is set to use pfsense for DNS as I am not listing any external source.
The dns reply logs still empty. However the only place I can see some blocking logs is on Firewall>pfblockerng>reports>alerts. That is the only place I can see some info.
If there is some other place or setting that I can verify to make sure DNS is going through pfsense please let me know.
-
@zachelle
Are you on a static IP or Dynamic IP?it would be helpful to know what the associated rules for the IP (pfB_PRI1_v4) look like.
What traffic types are the rules set to block?
What other rules float, wan, lan rules do you have, Rule order matters.
Thanks
-
What is this ?:
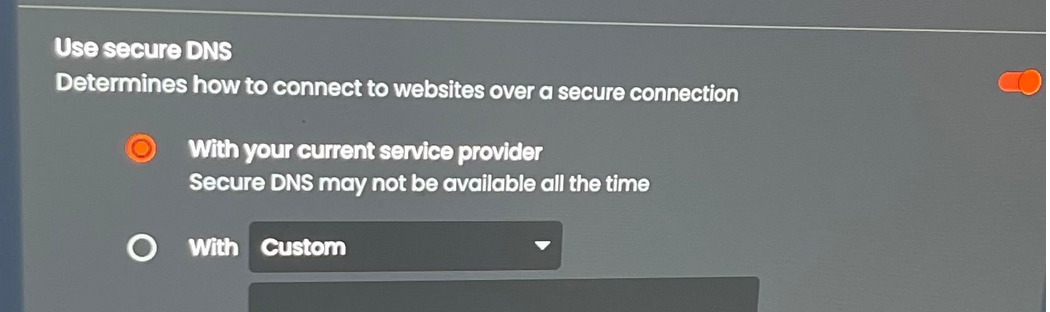
But ok, is says "Use Secure DNS", so let's presume (presuming is bad ... and great for creating a "it's not working" situation) that this means DNS over TLS.
If this is the case, pfSense got you covered.
First, set these :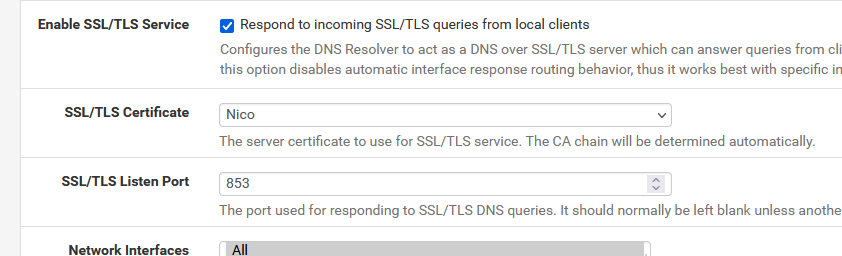
Enable SSL/TLS Service
Select a available certificate.
Use the default 853 port
And be sure this port (TCP only!) is open on any LAN where you want this DNS over TLS.Then :
AFAIK, on your device, select the second option "Custom", and enter the IP of the LAN of pfSense on which you connected your device, for example "192.168.1.1" if you use the default LAN settings.From now on, your device will be using DNS over TLS and use pfSense (the resolver) as the DNS server.
Be warned : using DNS over TLS is an advanced DNS usage case, and should be used if you do not trust your own network environment.
@zachelle said in pfblocker not blocking/working:
The dns reply logs still empty
Again : this means your (some) LAN connected devices are not using pfSense / the resolver as their DNS server. So the resolver, thus pfBlocker, never see the DNS requests, so it can't 'block' them neither.
-
@jrey @Gertjan I am so sorry for the late response. Its been a few busy days.
@jrey I am using DHCP. I will try to post the rules tomorrow.
@Gertjan I ave all settings established as you have showed me. I did try to setup on my browser the custom option and it requires a correct formatted url. I have been trying to use the format on your example something like http://192.168.1.1 but it still gives me an error.
I did noticed something today that might be the reason this is not working 100%. My modem from my ISP is on bridge mode. They are assigning two dns servers and I am not able to change them. I think that is the reason it is not going 100% to the resolver. Let me know if I am wrong or what I could try to fix it.
-
@zachelle said in pfblocker not blocking/working:
I did noticed something today that might be the reason this is not working 100%. My modem from my ISP is on bridge mode. They are assigning two dns servers and I am not able to change them. I think that is the reason it is not going 100% to the resolver. Let me know if I am wrong or what I could try to fix it.
No need to do anything.
No need to fix something. That is, maybe you should 'undo' whatever you did. pfSense (and DNS) works out of the box. Making it better from that starting point is very hard.See this one : How DNS Works - Computerphile (there are many others out there, this is, IMHO, one of the better ones).
Now, say after me : pfSEnse resolves out of the box. So DNS works ** and there is nothing to do

** when you install an application, like a web browser, that doesn't use the local router (== pfSense) ad the main "local DNS source" but it's doing its own thing, that's an application issue, not a pfSense issue.
-
@Gertjan said in pfblocker not blocking/working:
So DNS works ** and there is nothing to do
100% - but there are also so many things that can be done to change and control the behaviour of DNS traffic.
The first (next) step for @zachelle as you correctly point out, is to change the "client" as by default
that doesn't use the local
routerdnsThe OP says:
I am using DHCP.
This is where the DNS address that is being handed to the client can be assigned.
That doesn't mean however, that all clients will even "listen" or "use" the address being assigned. DoH etc. IoT devices that are simply hard coded to point to the companies own DNS etc.
It does take some understanding of the individual devices traffic and planning, but all of these things can be shaped/controlled if required.
The OP is looking as step one to have the DNS go through the local DNS where DNSBL can do what it needs to do. Then there will be new observations, "it's still doing this"
BTW that Talos feed download issue. (when it fails randomly) is a volume of traffic issue at the server.
Consider this:
I setup another test box pfSense CE and did a standard pfBlockerNG install. Meaning that the cron settings for pfBlockerNG are set to run at the 00 mark of the hour. I picked a couple of lists that people complain fail often (Talos being one of them)Shortly thereafter I noticed that the Talos feed started to randomly fail on the test box, but my main firewall wasn't having this problem. Has been downloading that feed for months without issue. Then it occurred to me that every system "out of the box" is configured the same way, (by default) and there is a high probability that most people won't change this.
Several months ago I had changed the cron timing of pfB for completely other reasons. The unknown(unrecognized) side effects at the time and since that change, is that Talos feed hasn't failed.
Then the tiny light went on, in my head, I moved the test box cron job off the top of the hour, and the Talos feed on the test bed generally hasn't failed since.
Defaults are good, Defaults are bad.