Lots of blocks in log - any comments
-
New pfSense+ user here. Netgate 8200.
I see a ton of block messages in my firewall log like this filtered for WAN:
Nov 11 00:41:23 WAN [fe80::21c:73ff:fe00:99] [ff02::1] ICMPv6These are all pings. I thought fe80: is a local address though (not terribly familiar with IPv6). If these are pings from local devices what are they doing on the WAN? How do I track down what local device might be issuing them - I think I have IPv6 disabled everywhere. Can IPv6 addresses be spoofed and these are attempted hacks?
I further see a number of block messages like this:
Nov 11 00:43:26 WAN 92.63.197.131:41360 73.157.255.159:14547 TCP:S
These are invariably TCP:S. Are these attempts to hack my system? I get widely disparate source IPs. In this case, the IP is from Ukraine (and I can't think of any reason my computers would be communicating with Ukraine).
Lastly, my DHCP log entries show:
Nov 11 00:53:45 dhcp6c 96681 transmit failed: Permission denied
Nov 11 00:53:45 dhcp6c 96681 Sending SolicitI'm guessing that this is a DHCP daemon requesting an IPv6 address from my ISP. If so, I haven't been able to figure out how to disable that as I solely use IPv4 to my ISP.
Thank you for any advice.
-
@hspindel Those entries about icmpv6 could be anything on your isp networks.. Do you see a bunch from different sources? You could set a rule on your wan to not log icmpv6 completely, or you could just block it to the noise your seeing ie ff02::1 which multicast address.
As to the TCP:S from Ukraine - yeah the internet is a noisy place.. So sure you will see traffic to your IP from all over the globe..
If your not able to use dhcpv6 with your isp, set your wan interface to none for IPv6
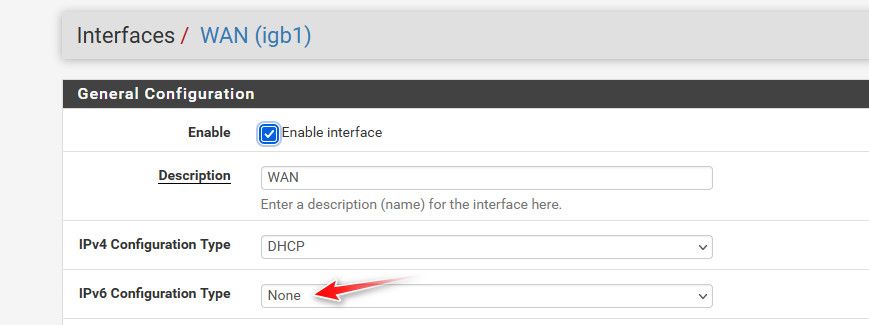
-
@hspindel we always turn off logging of the default block rules. Eliminates a LOT of log noise, and disk writes.
-
@SteveITS said in Lots of blocks in log - any comments:
we always turn off logging of the default block rules.
Same here - I only log tcp syn directed to my wan IP, and then common udp ports. Just for curiosity really to see what ports might be trending at the moment ;)
-
Thank you for the informative response.
@johnpoz said in Lots of blocks in log - any comments:
If your not able to use dhcpv6 with your isp, set your wan interface to none for IPv6

That's the setting I missed -TYVM!
-
@johnpoz said in Lots of blocks in log - any comments:
Same here - I only log tcp syn directed to my wan IP, and then common udp ports. Just for curiosity really to see what ports might be trending at the moment ;)
#johnpoz: Do you setup a new WAN firewall rule that overrides the default block in order to log tcp syn? Would you mind sharing the rules you set up?
Thank you.
-
@hspindel Just turn off default logging, and then here is what I have on wan
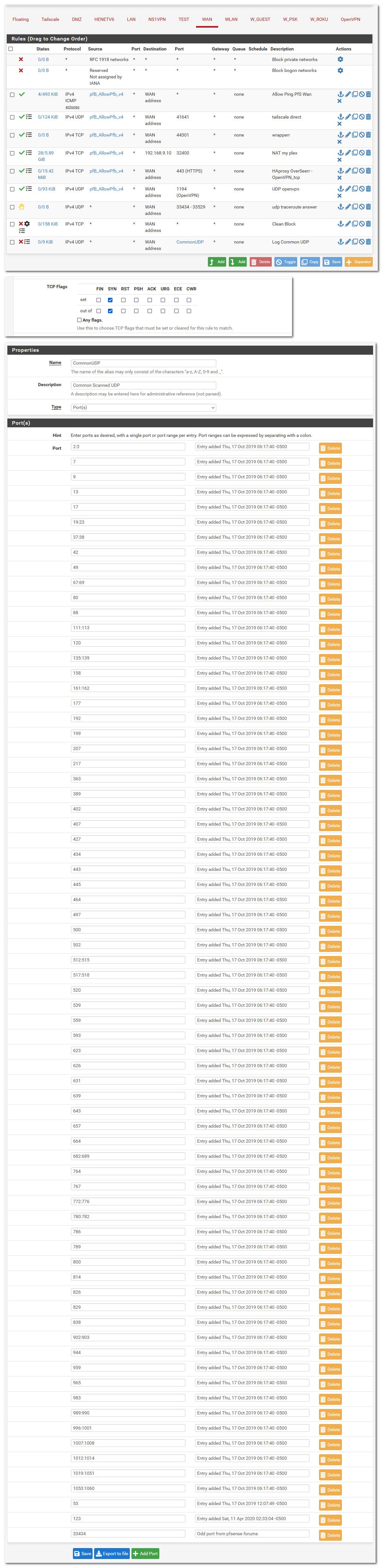
-
@johnpoz Thank you very much for the rules. Seem to be working fine for me.
-
I'm also looking way how to solve firewall log noise (for IPV6), but want to keep ON logging of the default block rules.
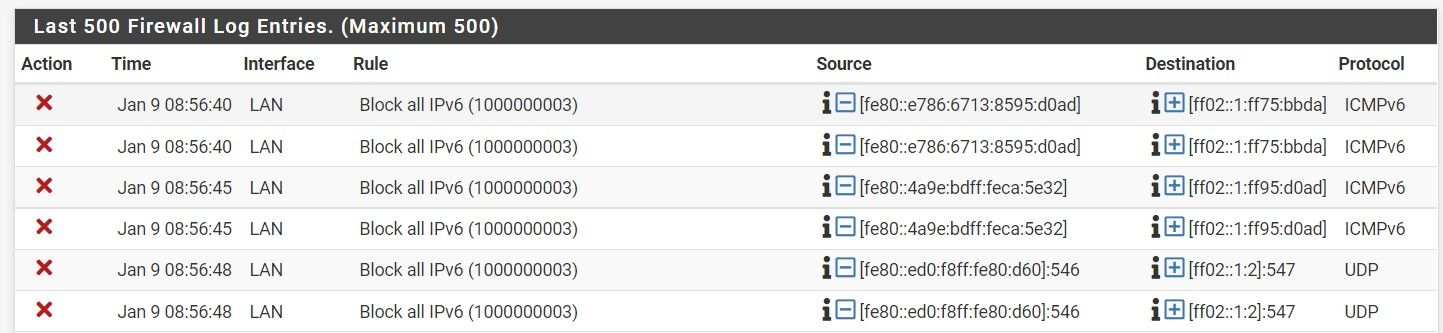
I was trying to create block rules (with "Log packets" disable) to eliminate related records, but they keep appear.
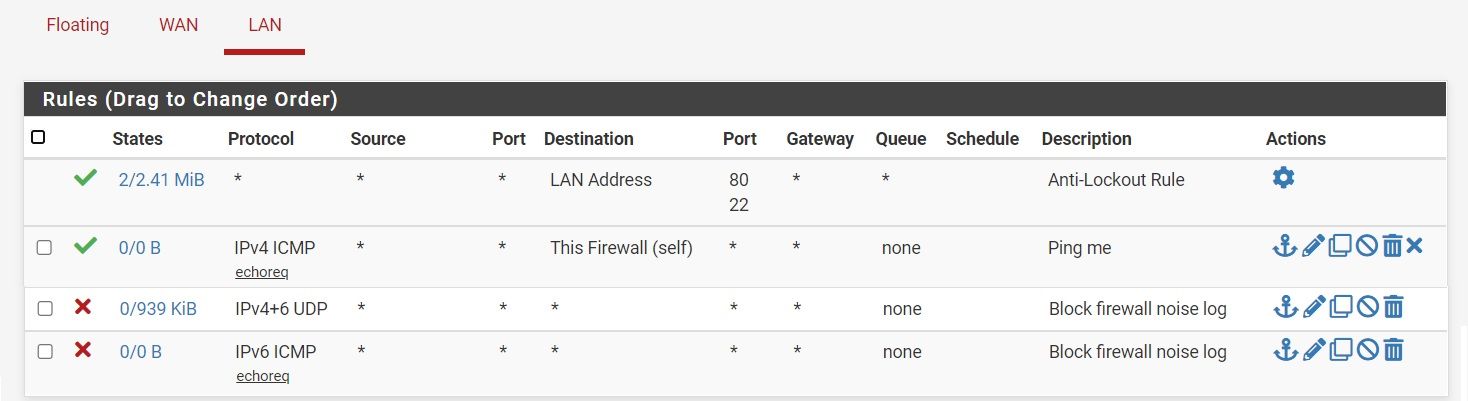
I know there are hidden implicit rules, but they should be evaluated last, isnt it ? So when packet reach my own rule, should be blocked accordingly (and not logged). Or I dont understand it corectly ? -
@CZvacko said in Lots of blocks in log - any comments:
I know there are hidden implicit rules, but they should be evaluated last,
Not when you click the BLOCK all IPv6 checkbox.. Or uncheck it if you will, if you don't want IPv6 noise, then allow IPv6, just don't create any allow rules.. Any noise then blocked by the default deny which is last, you can create rules above that do not log.
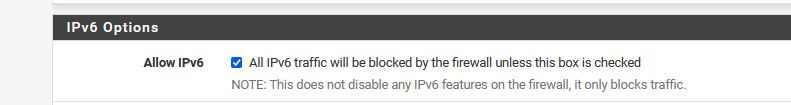
You can put in a feature request that if your blocking all ipv6, you should be able to not log it specific, but right now its tied to the log default deny.. When you uncheck the allow IPv6, it creates specific rules
# Block all IPv6 block in log quick inet6 all ridentifier 1000000003 label "Block all IPv6" block out log quick inet6 all ridentifier 1000000004 label "Block all IPv6"If you allow it then those rules are not created, and if you just do not allow it, you can put in rules to not log it which are above the normal default deny rules
If you allow it, you could then create your own rules in floating just like the above that are auto created, but not put in the log part.
You could put in a feature request, that allows not logging when you block IPv6, maybe like the log settings that allow you not to log the bogon or rfc1918 rules.
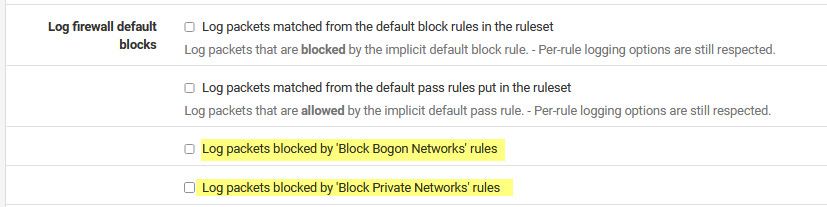
I always thought it was a bit odd you couldn't do something like that, but then again I allow IPv6 and don't even log default deny - so never an issue for me..
-
@johnpoz
I think I understand it now, implicit/hidden firewall rules are generally evaluated last, but if the Allow IPv6 checkbox is enabled, implicit/hidden IPv6 rules are evaluated first (so other IPv6 rules from the user are not reachable). -
@CZvacko said in Lots of blocks in log - any comments:
implicit/hidden firewall rules are generally evaluated last
No not the case at all.. For example there are hidden rules for dhcp, etc.. Yes the default deny rule is last..
If you explicit say block IPv6 by unchecking that box, then yes those are first.. How could that sort of rule not be first, you might have created rules that allow IPv6.. And since there is a default deny at the end any way for both ipv4 and ipv6.. Then yes wanting block all IPv6 would have to be first on the list.