Nintendo Switch and repeated cURL use
-
@JonathanLee said in Nintendo Switch and repeated cURL use:
@mcury I use every AppID with custom text rules.
I can detect Nintendo use and many others.
https://forum.netgate.com/topic/183210/guide-snort-s-appid-custom-rules-quick-guide-to-blocking-example-shows-openai-chatgpt-or-itunes?_=1699913000461
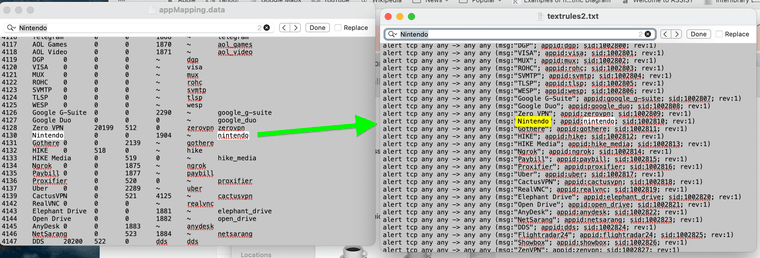
you just have to map text rules to the AppId's appmapping.data file. My
My Nintendo keeps running cURL.
Nice, good job

Thanks for sharing that link, there is a holiday coming and I'll probably be playing with it :)edit: How can that file appMapping.data can have ChatGPT in it, if it is from 2017 ?
I'm probably wrong about the last update regarding AppID ? -
-
I am starting to wonder if it is possible for someone to introduce a Pen testing softwarwe version of a Switch into a Network, that would be really sneaky like. Hackaday lists dozens of Nintendo switch items.
-
@JonathanLee Really nice..
So Nintendo uses a different User-agent ?
alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS ( msg:"OS-OTHER Nintendo User-Agent detected"; flow:established,to_server; http_header; content:"User-Agent|3A|"; content:"nintendo",distance 0,fast_pattern,nocase; pcre:"/^User-Agent\x3a[^\r\n]*nintendo/i"; metadata:policy max-detect-ips drop,ruleset community; service:http; classtype:policy-violation; sid:25525; rev:3; )25525 || OS-OTHER Nintendo User-Agent detected -
@mcury No it is the same database, just the one that downloads does not mapp to updated text rules. We get the free database but no text rules with Snort. My text rules are inputted into custom in Snort and it maps to AppID's new database. Once it updates I have to remap it again.
-
@mcury OS-Other that is cool!! So that text rule can detect the HACKADAY versions if one gets on a corporate lan??
WOW!!!
-
@JonathanLee I downloaded the community rules from Snort website, I'm checking files sig-msg.map and snort-community.rules
But I can't find the new appID rules to check, I would like to know what pattern they are checking for when detecting Nintendo or ChatGPT
-
@mcury /usr/local/etc/snort/appid/odp/appMapping.data is the appid database path on pfsense once it downloads. Could update at any time, again it seems to stay the same. Yes the pattern would be nice to know. sourcefirre stuff. I think I remember a website that lists them that Cisco has for users.
-
@JonathanLee I think I found..
You can download the rules from:
https://www.snort.org/downloads/openappid/33380It seems that these detectors are based on .lua files.
If you open the client.Bittorrent.lua file, you will see how they do :
I think that this is the relevant part of the code:
function DetectorInit(detectorInstance) gDetector = detectorInstance gDetector:addHttpPattern(2, 5, 0, 229, 1, 0, 0, 'BitTorrent', 61, 1); gDetector:addHttpPattern(2, 5, 0, 229, 1, 0, 0, 'BTWebClient', 61, 1); return gDetectorEdit: The files are from 06/09/23, so from June of this year..
-
I couldn't believe the amount of Hackaday projects out there with use of a Nintendo Switch.
-
@JonathanLee said in Nintendo Switch and repeated cURL use:
I couldn't believe the amount of Hackaday projects out there with use of a Nintendo Switch.
It is a computer, you can run Linux in it.. :)
I have been trying to understand how the appID works, and what I found is not so good..
What I'm going to say below is something that I'm not sure about, take it with a grain of salt.
Most of the times it checks for a URL in the packet (header).
If the packet is encrypted, it can't do anything other than checking the header.With SSL, it would be possible to check the SNI (Server Name Indication) header in the Hello packet, just like Squidguard in Spice all mode does, but the end of that is pretty near..
Even Firefox is prepared for that already: https://blog.mozilla.org/en/products/firefox/encrypted-hello/
-
@mcury I know that AppID can detect everything when the rules are in place. I do not know the patterns but, they do not require description it seems.