Allow only some websites through pfBlockerng
-
@greenlight I will try this way and tell you something
Thanks a lot for your help!
-
@greenlight said in Allow only some websites through pfBlockerng:
https://forum.netgate.com/topic/150084/is-pfblockerng-able-to-block-all-outbound-traffic-except-whitelistet-sites/17
You can follow the steps in this link without pfblockerng.
I also prepared a visual for you. I tried it myself and it works this way. You must only specify a static IP address for the device you will use. After then
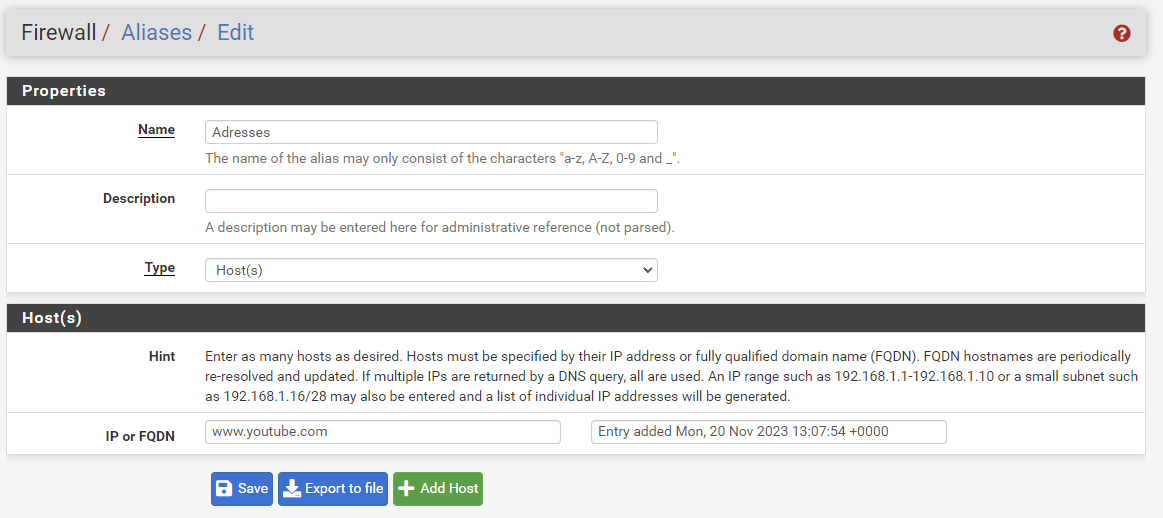
Create an aliases for websites with permissions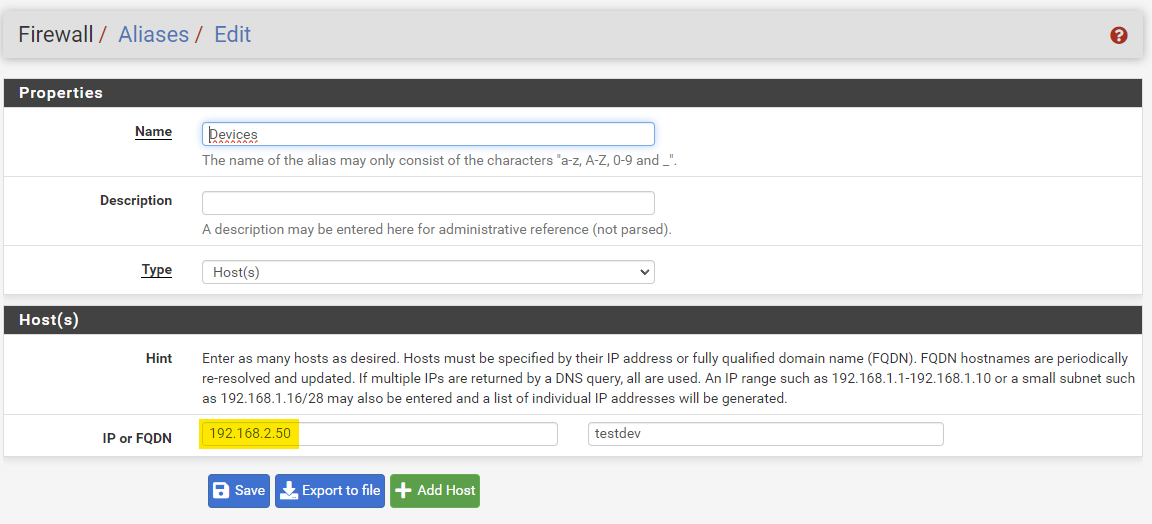
Create aliases for devices that you allow and whose IP addresses you fix. The marked IP address belongs to my device. You'll probably type 192.168.8.80 there.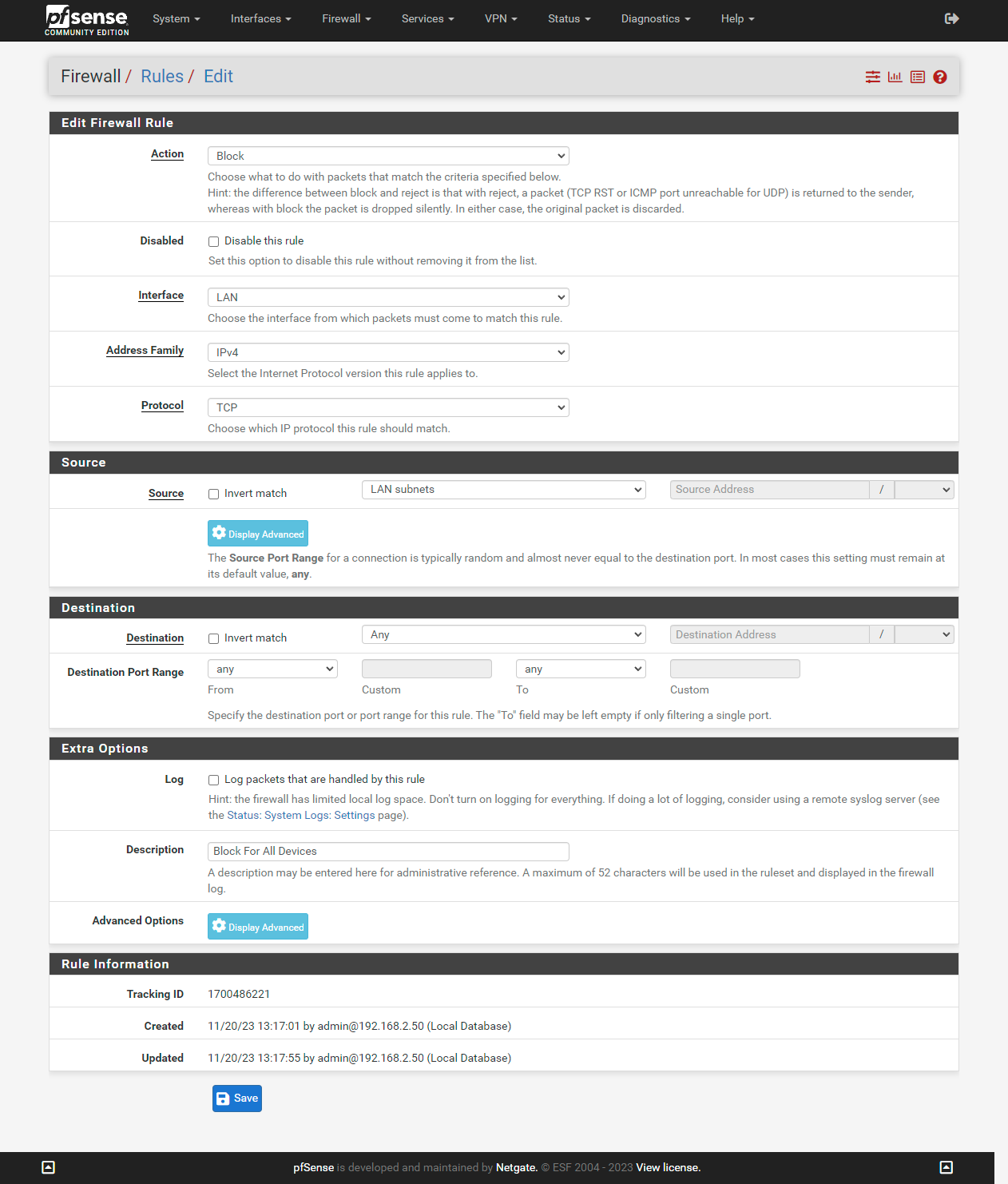
You will create a rule to block internet access for all devices.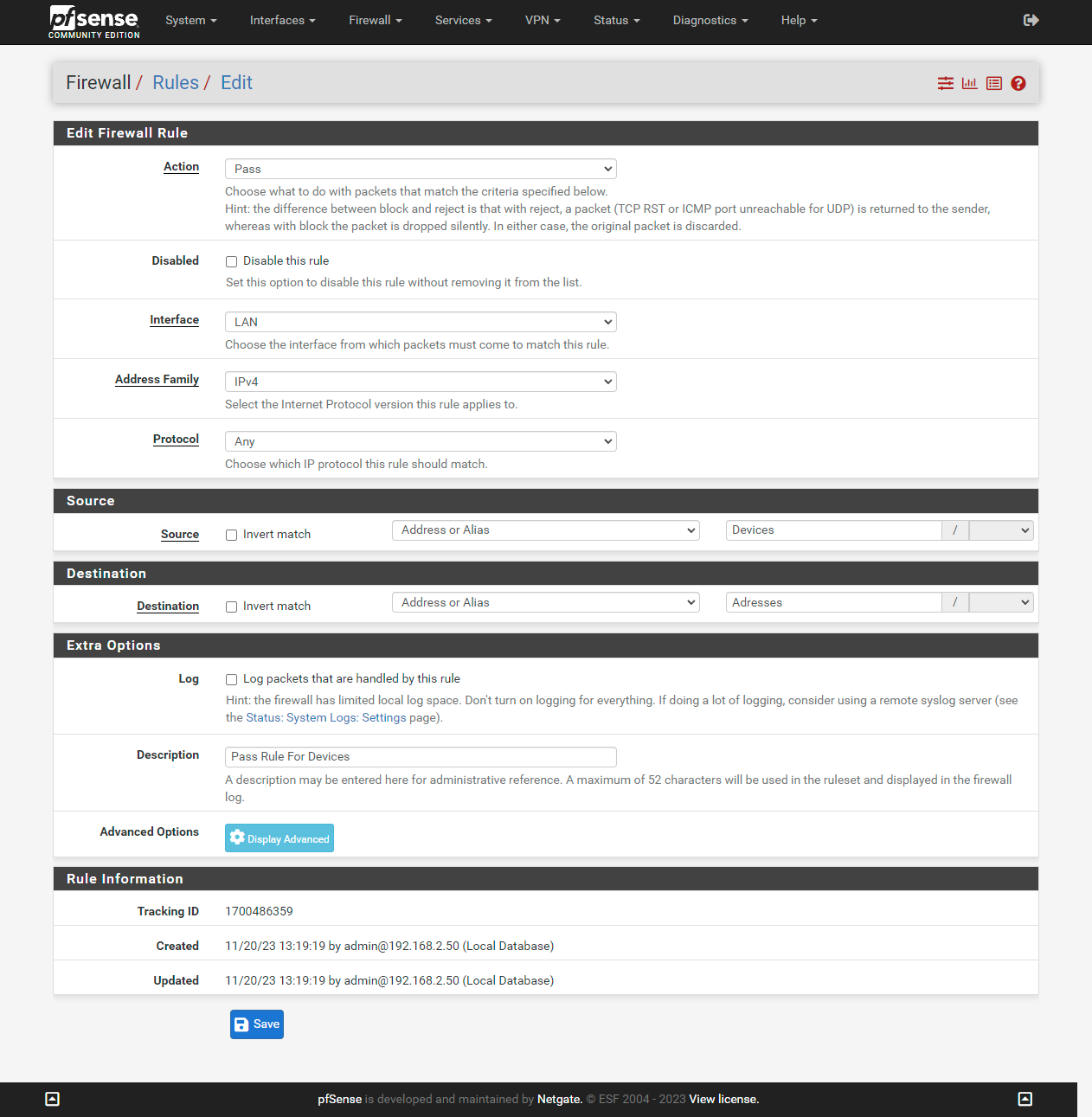
By selecting the aliases you created here, you will define the devices and the addresses they will connect to.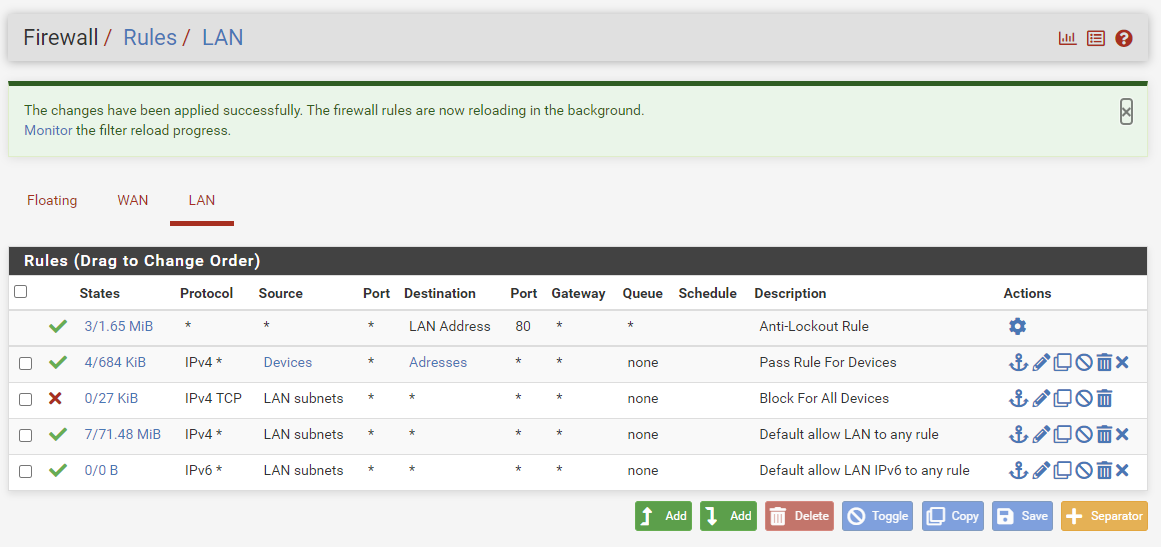
Your rules should look like this.Finally, reload the filters. You can make additions or deletions for both aliases groups. Doing this on the Aliases side will be enough.
The main way pfblockerng works is to block external connections to pfsense. Of course, connections can be blocked in both directions. Very useful for interface based restrictions. But the rules are more favorable for restrictions within the subnet.
Hi again! I tried this solution but still is blocked. I see traffic on rule but still can't connect. Any suggestion?
-
@abanet hello, the pass rule should be in the first line. Did you notice this?
-
@greenlight Hi! Yes. I put on top but didn't works. I tried create same rule in "floating rules" but still can access to web sites in "Adresses" alias
-
@abanet You must use LAN rules. Why are you trying Floating rules? I also tried this on my own system before creating the screenshots and it worked. A step you missed or something you previously configured might be preventing this from working.
-
@greenlight Floating rules are enabling by pfBlocker. I tried disable this option in pfBlocker and put your rule on top but didn't work
-
@abanet Disable pfblockerng and disable all its rules (including LAN and Floating).
Just follow the rules I have shown on the LAN side.
-
@greenlight In that way works. But I need use pfBlockerng
-
@abanet what is your pfsense version?
-
Easy.
2.7.1 (or 23.09).Those who use 2.7.0 or earlier and install pfBlockerng 'now' brake the rules : Never install packages before pfSense is on the latest version.
The latest pfBlockerng is compiled against "OpenSSL 3.0", something pfSense 2.7.0 hasn't. It will fail right away.
There is another thread, yesterday or so, that illustrates this situation. -
@Gertjan said in Allow only some websites through pfBlockerng:
2.7.1 (or 23.09).
Those who use 2.7.0 or earlier and install pfBlockerng 'now' brake the rules : Never install packages before pfSense is on the latest version.
Hi! I did a fresh installation yestarday, pfSense 2.7.1 and last pfBlockerng but still doesn't work