Where do you put firewall rules? LAN1? LAN2? ...and what order do they get executed?
-
Q1) When you have WAN rules, LAN1 rules, LAN2 rules, and WG0 rules, how does pfSense decide the execution order?
Q2) Let's say you have LAN1 (your 'main' LAN) and LAN2 (a DMZ):
You want an allow rule to go from LAN1 to LAN2 (so you can reach your devices in the DMZ)...
...BUT...
...you want a block rule from LAN2 to LAN1 (so if bad-guys get into LAN2, they can't get to LAN1).Which rule goes under LAN1 rules and which goes under LAN2 rules?
Q3) Does the "allow WAN<->LAN2" rule go under WAN or LAN2?
-
@JustAnotherUser You have been a member for 5 years now and have that basic question? Ok, here we go.
All traffic is only evaluated once by the firewall, when it first enters it on an interface; top to bottom, first match wins. If it is not filtered there, the traffic can go everywhere.
Now you can answer your questions by yourself. We can check your answers if you post them here.
-
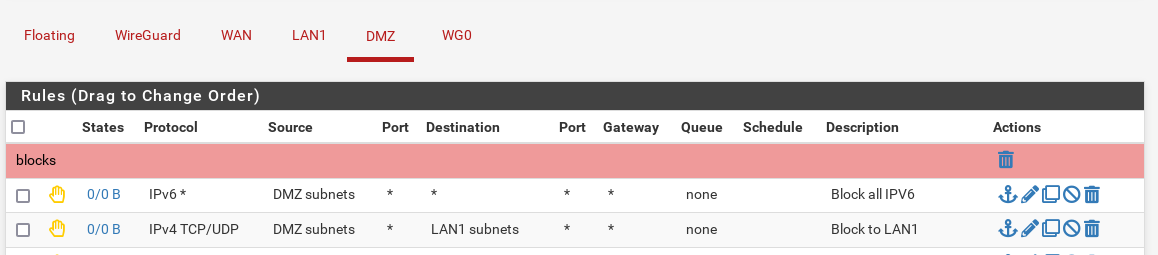
Okay, then why am I still able ssh to a machine on LAN1 from my DMZ (LAN2) with this rule at the top of DMZ's rules?
It's executed before any other rule for connections entering the pfSense box from DMZ
-
@JustAnotherUser Something must be wrong with your setup. It is not possible by the rules.
-
@Bob-Dig
It's absolutely doing it which is why I had to ask the question...The DMZ (LAN2) is a physically separate NIC card (re1) going directly to a machine with no other interconnects.
LAN1 is it's own NIC card (bge1) with no physical connections to the DMZ hardware or the WAN NIC (which is also a separate card (bge0)).
There's no VLANs, no bridges, no static routes but the firewall is NOT stopping connections from DMZ to LAN1
-
@JustAnotherUser Reset the state table and check for floating rules. If it still "doesn't work" it is your setup.
-
@Bob-Dig
Resetting the state table was the answer. TY