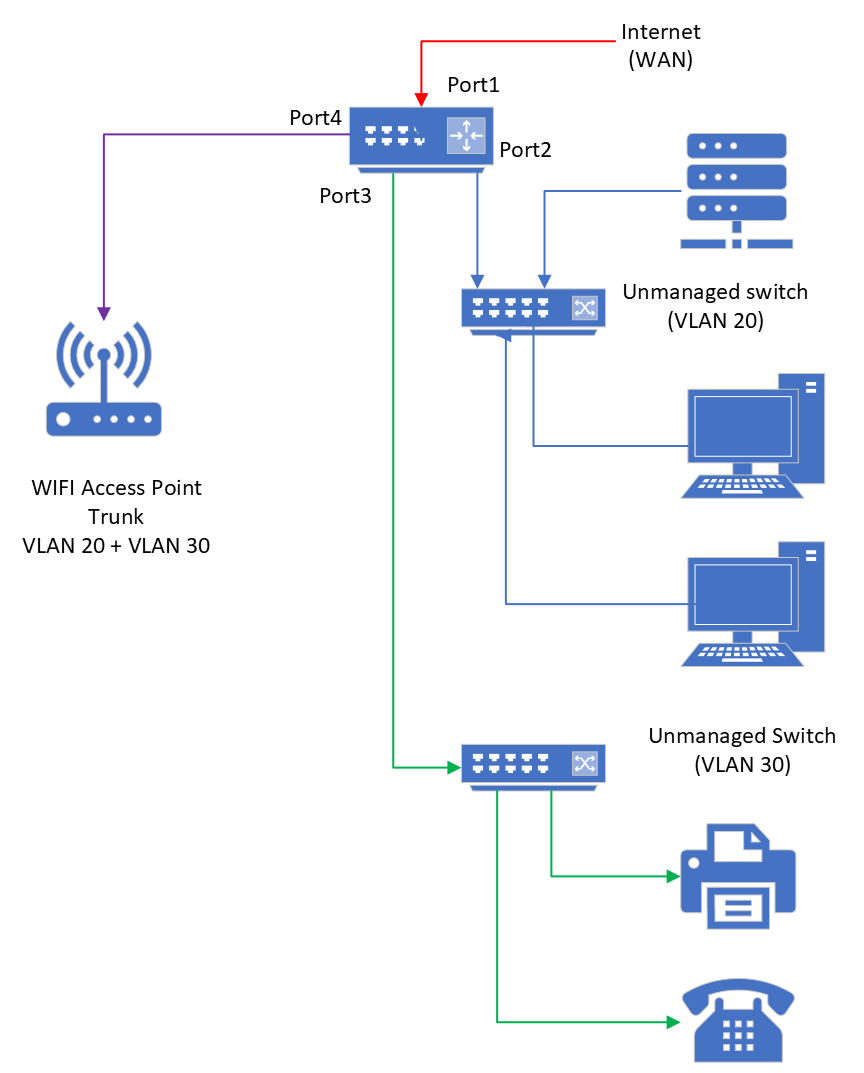
VLANS on more than one port?
-
@lrossi I agree with John. Why bother with what you're trying. By one managed switch, send a trunk port (or use separate ports) to it from pfSense, then go from there to your dumb switches as needed. For a little more you can get a POE managed switch to power your AP too.
-
@Jarhead & @johnpoz I guess you are right. I just didn't want to add more complexity and points of failure to the network if i didn't need to.
I was really hoping there was a setting I was overlooking (such as the "switches" section in the netgate SG-1100 i have at home).
But, based on your response, it seems such setting just doesn't exist in this version of pfsense.
-
@lrossi if your firewall box had switch ports then yeah you could do what your wanting.. But it doesn't it has discrete interfaces.. You could prob bridge 2 interfaces if you were talking 1 network.. Sill switch is better option!!!!
Get a 8 port smart gig switch (supports vlans) you then can have multiple uplinks vs having to trunk, etc. if you worried about bandwidth between vlans, etc. But could be done with a 5 porter as well
Looks like you only have 2 networks there so AP, dumbswitch 1 and 2 is 3 ports.. Then you can have vlan 30 uplink to port 3, and 20 to port 2 on your router.. And your cooking with gas!!
I currently see the tplink TL-SG105E for like 22 bucks.. and the TL-SG108E for like 27.. I would go with the 8 porter.. Or as mentioned for a bit more you could prob get a poe one to power your AP..
Not really a fan of tplink switches - they had problems with doing vlans in the past, but I do believe they learned from their mistakes and current models should be fine.
-
@johnpoz Thank you so much for the advisement. I guess i new the answer all along.
I don't have that many client devices. So, if 'm going to buy a managed switch, i might as well buy one with 16 ports and eliminate the 2 dumb switches.The topology would look like PFSense-->Managed switch--> AP + Clients.
And, i would use multiple uplinks as per your suggestion.
I'll take look at the models you mentioned and maybe i can find a 16 port one with a couple of POE ports. I'm thinking that i could use them for the AP and also a couple of IP phones we have.
Again, thanks for the advisement and clarification.
-
@lrossi said in VLANS on more than one port?:
might as well buy one with 16 ports and eliminate the 2 dumb switches.
There ya go - now your thinking! ;)
But from your drawing couldn't tell if they were in different locations. Its fine to put a dumb switch downstream of vlan capable one - its just all the devices would be on 1 network/vlan.
As to multiple uplinks - depends on your bandwidth requirements and how many ports you have to play with both on the switch and the router.
I use a combo - some vlans have their own uplink, and then I share an uplink with my wifi networks.. They would never have any intervlan communications between them, so no hairpinning of traffic. And they are wifi devices, so they are only doing 400-600mbps anyway even if they streaming from my plex, etc.. Most of the stuff on wifi is iot, with very little bandwidth needs. And on phones and tablets mostly just simple email checks, a few web pages, etc.. Nothing that is bandwidth heavy.
If you do not have anything that is heavy bandwidth that will go between your vlans, and your internet is no more than gig.. You could prob get away with just 1 uplink to your router, just trunk it and put all your vlans on it.
But say you like to watch a lot of movies or something off one of your servers? From another vlan, then you might want to not trunk everything on 1 uplink.
-
@lrossi
What’s the problem with making two bridges: vlan 20 port4 + vlan 20 port2 and vlan 30 Port4 + vlan 30 port3 ? -
@Viper_Rus Horrible solution.. And the traffic for both vlan20 and 30 from his access port would be coming in 1 port.
A bridge is not a switch.. Get a switch is the correct solution..
You can also hammer in your screws if you use a big enough hammer.. The proper tool for the job..
-
@Viper_Rus that is exactly the kind of thing i was hoping to do but i have no experience with the "bridge" function of PFSense.
I honestly thought you couldn't share a port between two bridges. Also, people tend to recommend not using bridges but they never say why.Have you tried this setup?
@johnpoz cold you please expand a bit why this would be so bad? I'm not challenging you, I just want to furhter develop my networking knowledge and skillset (since i don't do IT for a living).
I understand that using a managed switch would be ideal but, then again, I only need it because of 1 device (the access point).I don't know about you, but i have seen myself in situations where a screw driver is nowhere to be found and a hammer right next to me.
-
@lrossi said in VLANS on more than one port?:
in situations where a screw driver is nowhere to be found and a hammer right next to me.
Yeah sometimes in you have to do that because its the only way to get the job done. If the network is down or something you make it work - and sure a bridge might be an option then.
Sometimes a bridge is the correct tool. But if you find yourself without the proper tool, while you might use that hammer to get the job done, you also order a screwdriver to have in your toolbelt.
You don't leave your bent up not actually secure screw sticking out.
https://ipwithease.com/difference-between-a-switch-and-a-bridge/
You don't use a hammer because you're too cheap to buy the screwdriver when you bought screws.. Why did you buy screws in the first place if all you have is a hammer..
Discrete interfaces are not meant to be a half-ass somewhat like a switch port.. They are meant to be discrete interfaces into your router.
-
@lrossi said in VLANS on more than one port?:
Have you tried this setup?
I don’t have exactly the same solution, my bridges connect virtual machines on prxmox and my local network. (pfSense for me is itself a virtual machine, and proxmox works as if behind it)
And yes, one port can be used in different bridges with different vlans.As they already wrote to you, using bridges to connect different segments of the same VLAN is not very good, because The processor's performance is wasted, but if there is no other option (buying a smart switch), I don't see anything very bad about it.
-
@Viper_Rus said in VLANS on more than one port?:
my bridges connect virtual machines on prxmox and my local network
There is a difference between creating a "bridge" on a VM host to a physical interface.. And bridging physical ports on router.
but if there is no other option
Who can not afford a smart switch? Not taking 2k dollar enterprise gear here.. You can pick up a 5port gig smart switch for like 20 bucks.. And 8 port for around 40ish, etc.
If you want to go with 16 port, or add poe sure your going to be more.. But other than being "cheap" I don't see how you don't have another option.. Sure maybe it might take a few days to get a switch purchased and delivered. Putting in a switch is still the correct solution.
So you got the guy driving around with duct tape holding his fender on his car because he is too cheap to pay the insurance deductible would be my analogy ;) Vs doing it correctly and actually getting it repaired..
Clearly from the drawing the OP wants to setup a nice network, with segmentation, and putting specific devices on different segments. Has a AP that does vlans, etc. Has multiple dumb switches, etc. So doesn't seem like he can't afford a couple of bucks to do it correctly.
You can for sure do that on a budget.. You don't need to drop $$$ on a full featured managed switch with 48 ports and poe, etc. Unless you want too.. But in the modern world you can have a 20$ switch that would allow you to actually do it correctly - and learn something about setting up vlans in a switch, etc. delivered to your door if not that night the next day for cost of fancy coffee at starbucks and a bran muffin ;)
-
@Viper_Rus said
...As they already wrote to you, using bridges to connect different segments of the same VLAN is not very good, because The processor's performance is wasted, but if there is no other option (buying a smart switch), I don't see anything very bad about it.
Thank you, that is what i needed to know.
@johnpoz sometimes money is not the only factor for deciding whether you should buy another piece of gear or not.
Adding a switch is simple and inexpensive but it involves finding a spot for it, finding a receptacle for it, finding/making patch cables, labeling, documenting, etc...
In this case, i wanted to explore if i could make use of the unpopulated ports in my firewall to connect my VLAN compatible AP without having to make physical changes to the network infrastructure.
Based on your response, and the opinion of some others i have talked to, this might be possible but is not recommended in the long run if you want a stable network.
So, we have determined that a managed switch is the recommended way to go forward.
This has created a snowball effect in me since a single 16-port managed switch could replace my other 2 dumb switches (making my network infrastructure simpler).
...and, if its provided with POE it could power AP and IP-Phones?
...and, if i buy a switch form the same manufacturer as the AP i might as well use their central managing controller software.So, in order to setup VLANS on my single AP I ended up buying a software managed, 16-port, POE switch. I should get it by the end of this week.
This is very far from the original idea of just changing some settings in PFsense. But, all in all I'm happy that you guys guided me on how to do it properly as this network is extremely important for my business operations.