vLAN setup, DCHP configuration help needed
-
I want to up my Networking game a bit and add vLAN to my home network. I am attemping to setup a VLAN on a seperate IP range using my pfSense+ 2100 running v23.09. My initial setup is using 172.18.8.0/24 using LAN1
My problem is the new vLAN is not serving out IP through DHCP...I think. None of my wireless devices are getting the new IP range.
Details:
My verizon internet cable is going into the WAN port. LAN1 goes to a managed switch (irrelevant for this question). I added a TP Link AX3000 Gigabit Access Point to LAN3.
My goal is to create a vLAN for the access point with a different IP range. I have the vLAN created and DHCP server setup for this vLAN in pfSense. Wireless devices will connect but get an IP from the original DHCP range, not the new one.
Steps taken:
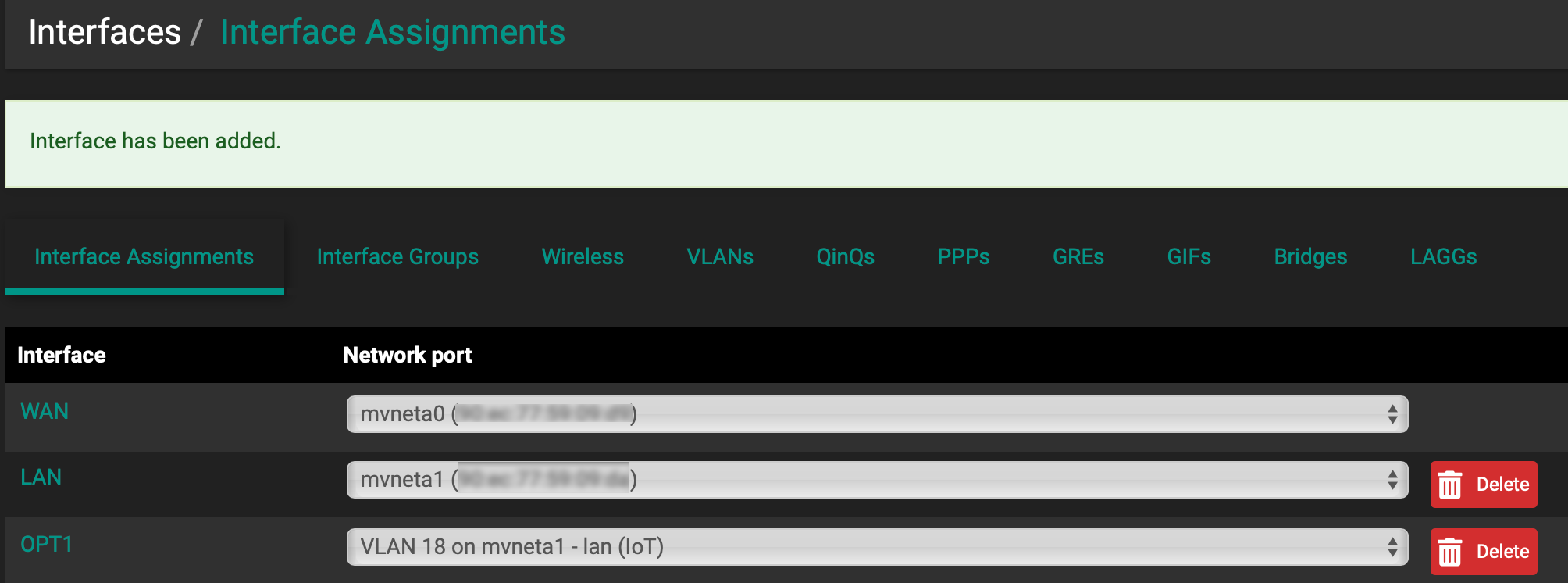
Interface > Assignments > vLAN
Added a vLAN (ID=18)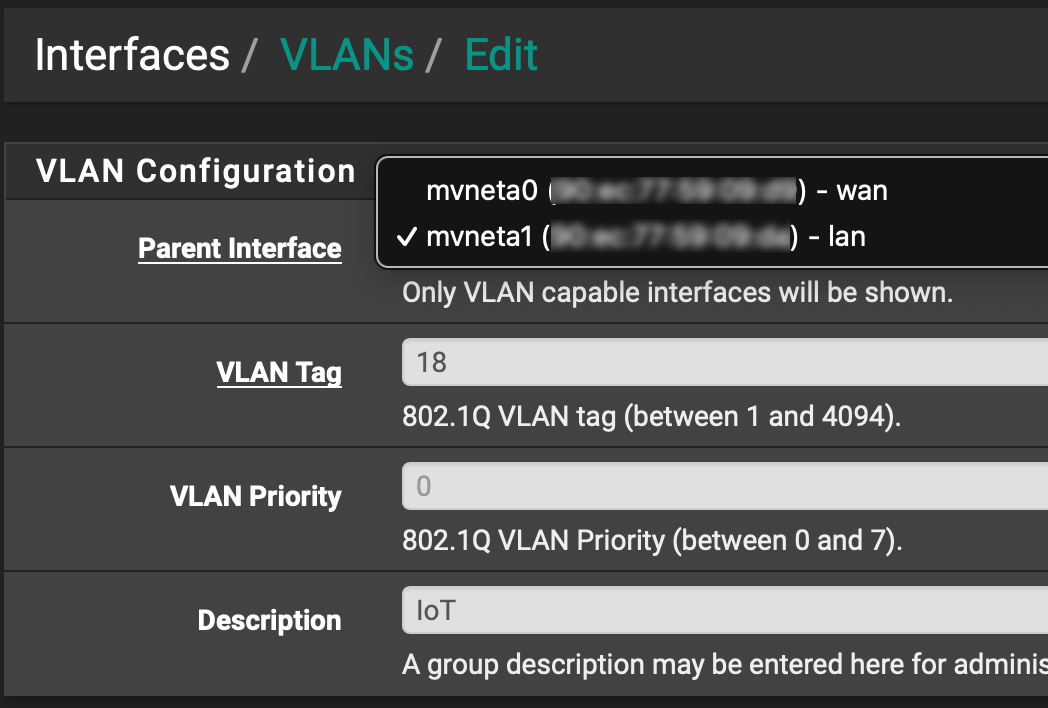
Added the new vLAN to Interfaces
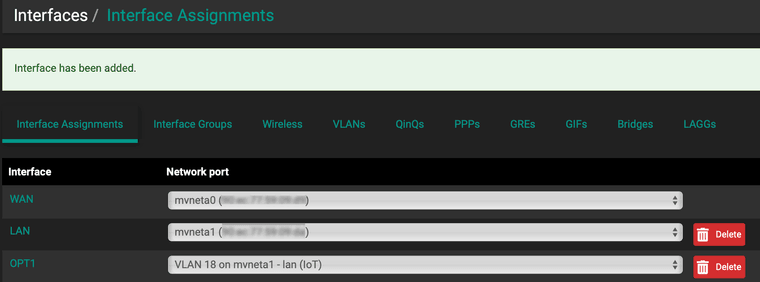
Updated the new VLAN, name, Static IPv4, IP Gateway with 24 cider. Saved and applied.
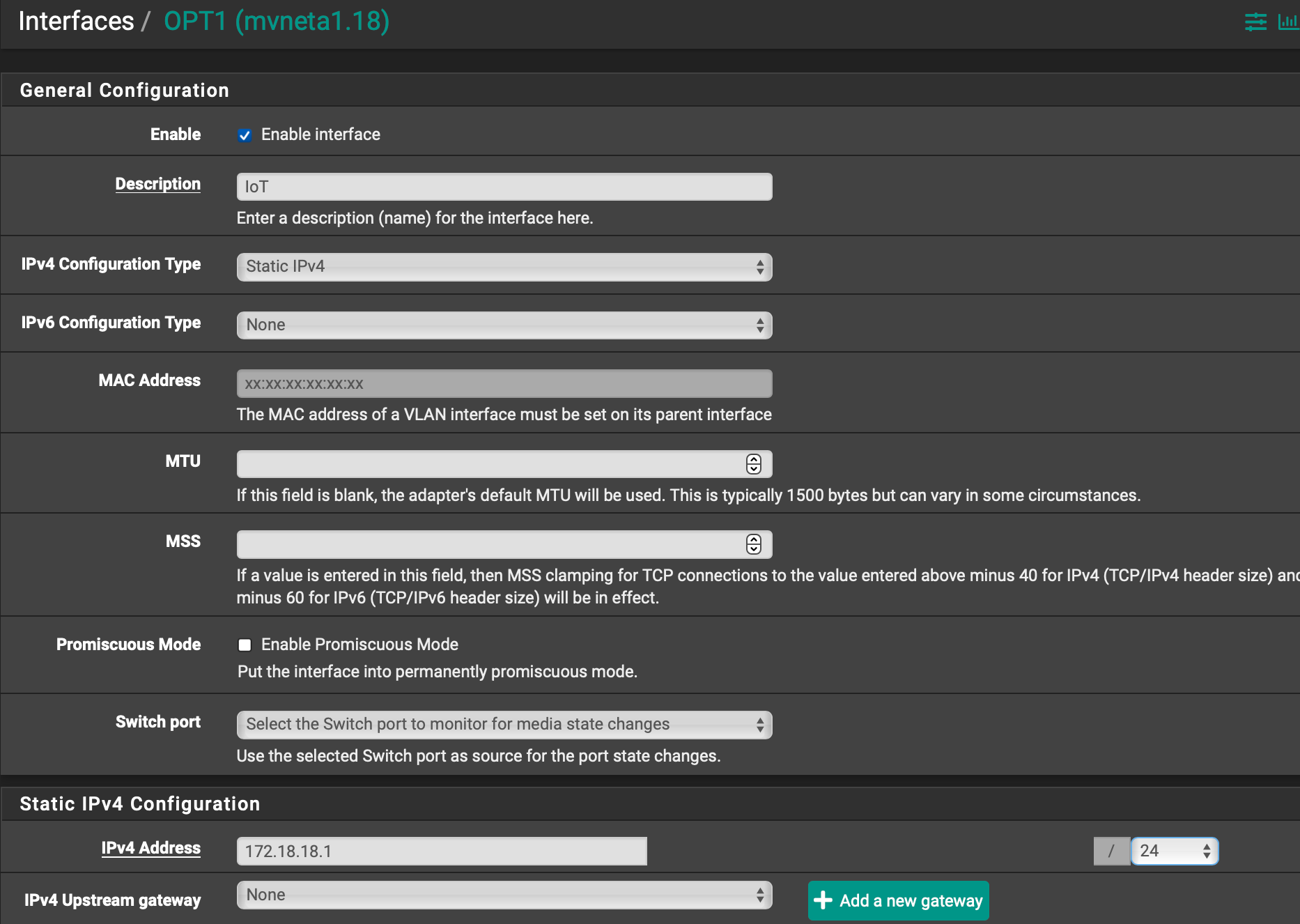
I now see my vlan name (IOT) in the Interfaces menu dropdown.
Then jump to DHCP Server and add a DHCP server to the IOT vLAN. Notice the new IP range is set here.
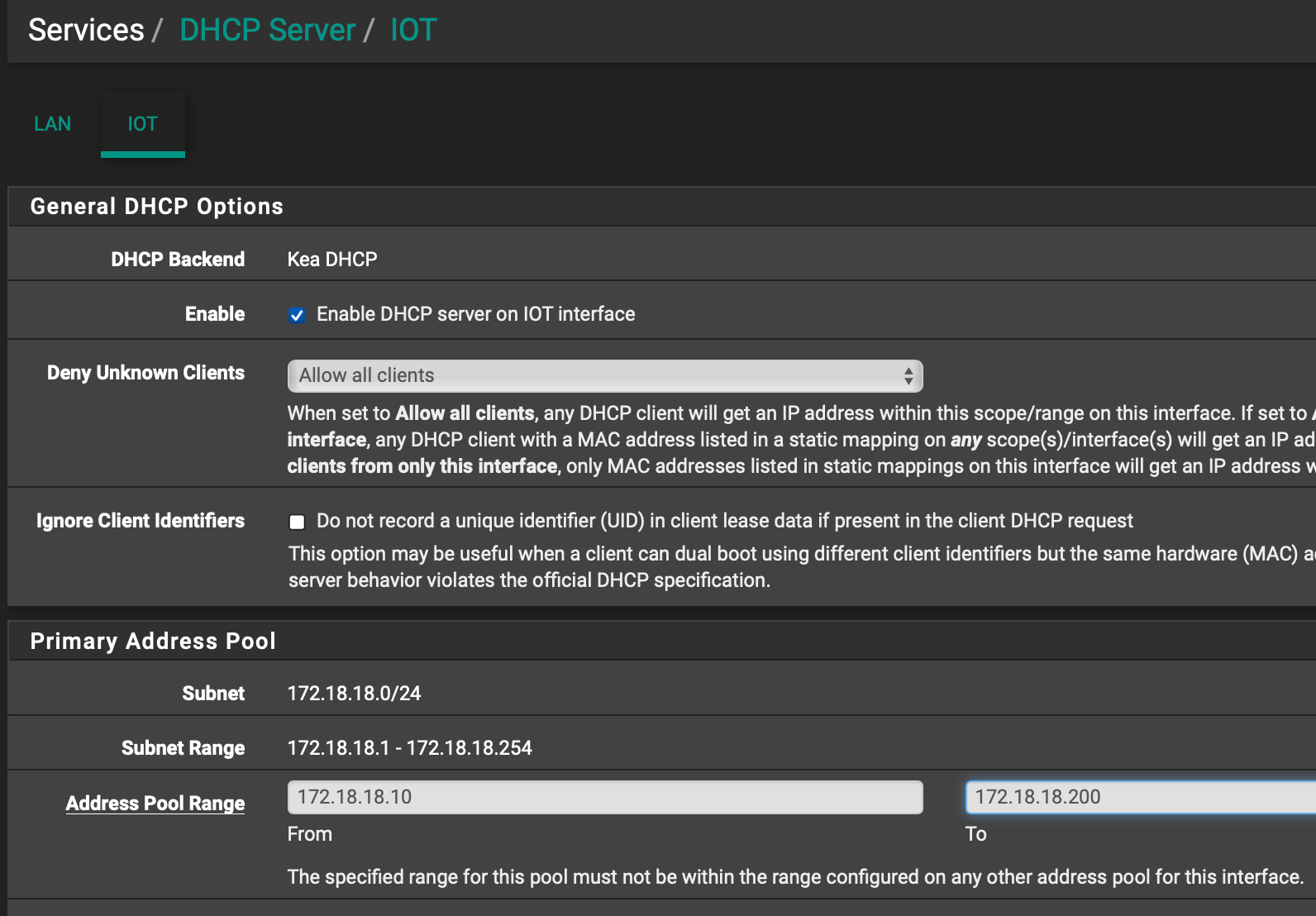
Next I go to Interfaces > Switches > Ports and update the Port VID on LAN3 to 18. Is this right? Is this saying take the vLAN IoT and run the traffic through this LAN3 since the Port VID matches?
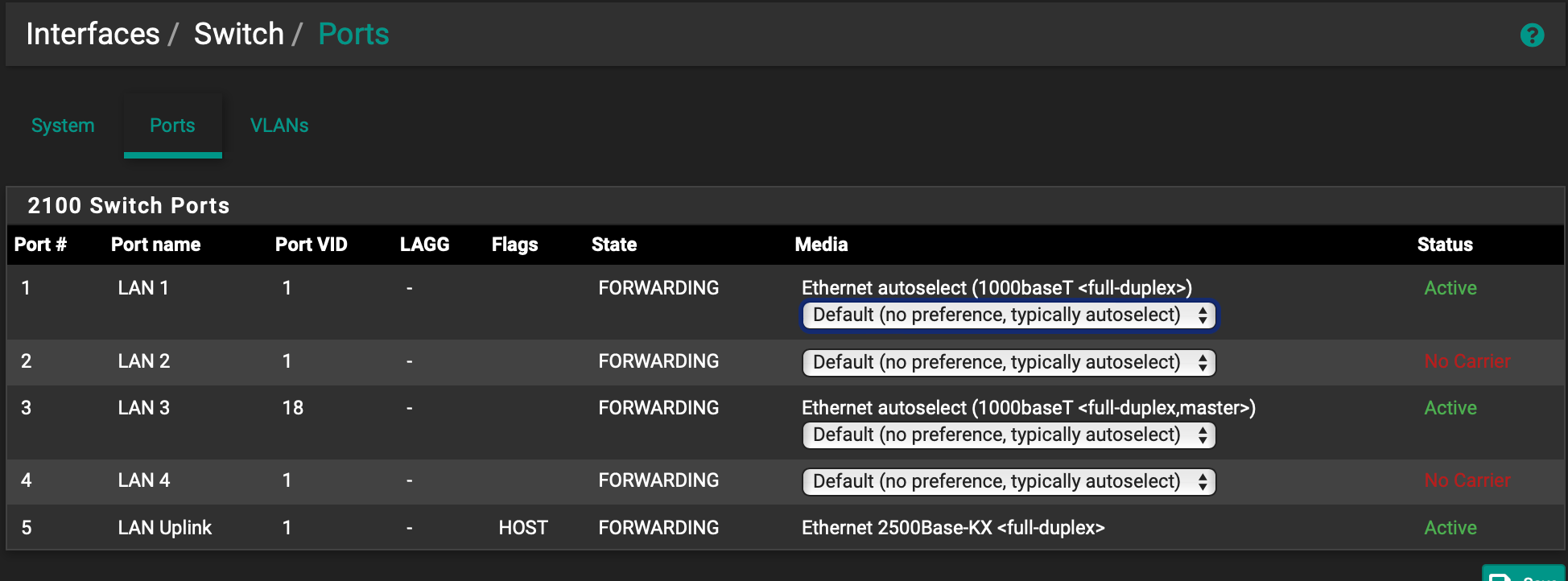
I then went one step further from something I found in youtube and went to Interface > Switches > VLANs. I enabled and added a tag, 18 and 2 members, 3 and 5. 3 and 5 because it seems that I should tell it LAN3 (3) and the Uplink (5). The text on the screen says "enter valid VLAN ID number that is not already in use." Frankly, putting in 18 was the only way I could get the wireless access port to allow connections, but it still gives out an IP in the original range (172.18.8.0/24), not the new range I wanted (172.18.18.0/24).
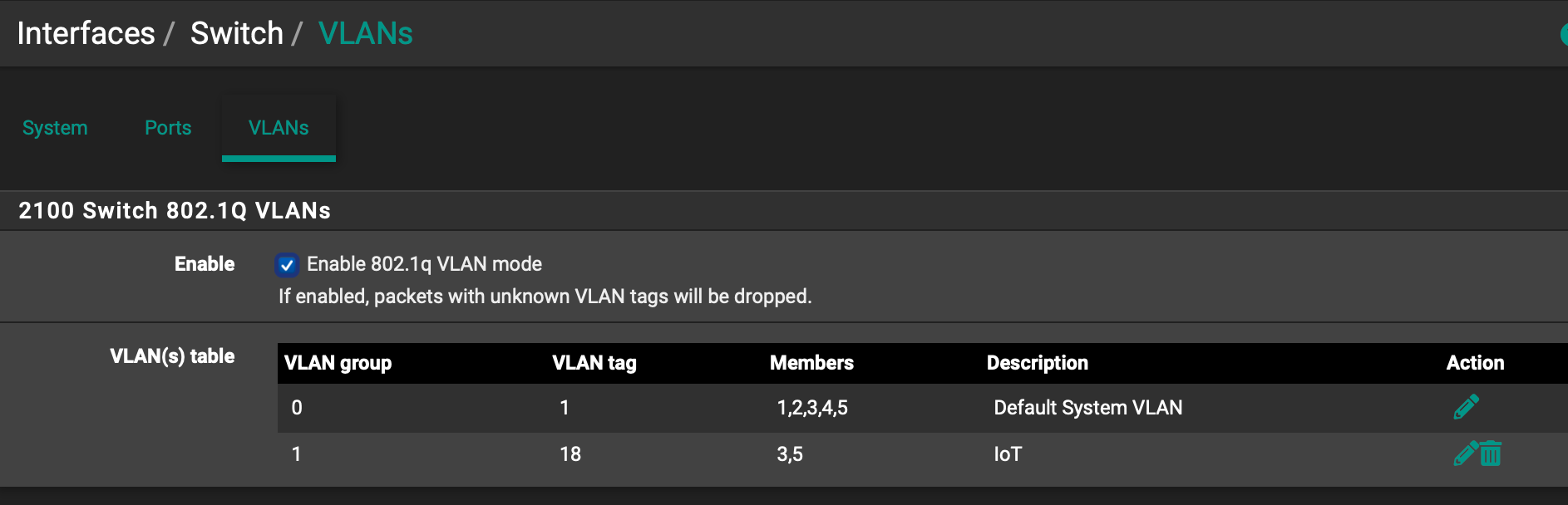
What part did I miss or is there a better way? I have read postings here that says to just use the managed switch. I felt I wanted to get this working first because less hardware involved. Once I have this working, I'll move into trying this with managed switch.
TIA!
-
-
@Popolou , thanks! Problem solved. I think I had at least 1 issue, maybe two. I never removed the LAN3 from the vLAN 0 group under Interface > Switches > vLANs. I tried that but it still didn't work. Then I erased all vLAN related stuff and followed the instructions on the web page provided. This time it worked perfectly. So I might have had a problem with the order I did things.
I will say the web page has a confusing statement near the top. "VLAN Tag: 4084 (VLAN tags should be 4081-4084 for LAN Ports 1-4)". This statement made me think that pfSense required you to use vLAN ID 4084 if LAN4 was in use. A later note states that we can use anything between 2 and 4094. I did the process twice, once with 4084 and then with 18. Both worked.
Thanks for the tip. I really appreciate the help!
-
@Aved590 Glad you got it working and merry Christmas!
-
I thought I was home free! But no.....
Just recently realized everything on the new vLAN can't get out to the internet. Not sure how I missed it.
I did some searching and seems like maybe I need a NAT rule. Then I see pfSense has automatically added one. I'll assume it works and is ok.
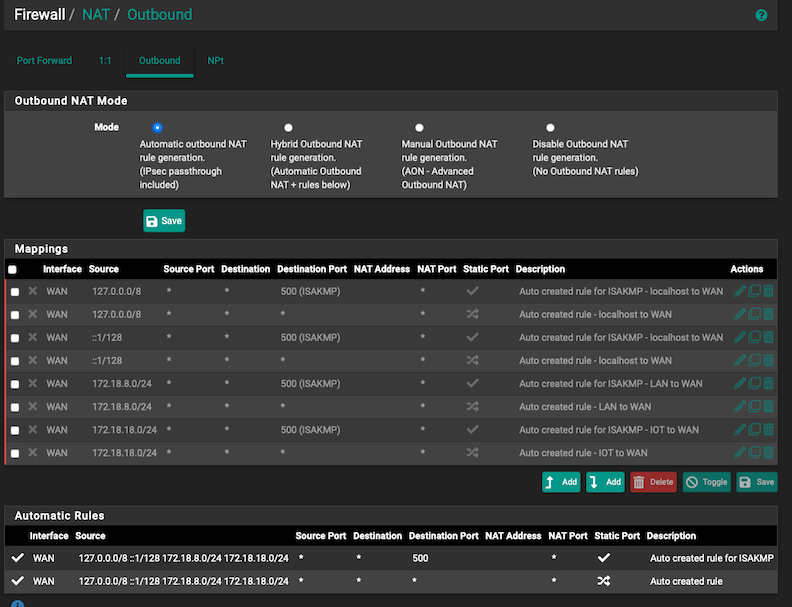
I did update my TL AX3000 to use the vLAN ID I set up (18) on each SSID.
There is an also a firewall rule on the vLAN that basically opens vLAN 18 up to the primary IP range. Maybe it can't see the gateway to the original IP range?
-
@Aved590 What happens if you do a traceoute out from one of the devices on that vlan to a public address. I normally use Hybrid NAT to have more granular control over scenarios like this.