About Cryptographic Accelerator Support
-
System: SG-4100 running 23.09.1 firmware.
Environment: Wireguard Server and OpenVPN client setup.OpenVPN:
Data Encryption Algorithms: AES-256 GCM
Auth digest algorithm: SHA-256
DCO disabled since the server I'm connecting to requires compression.I'm kind of confused now, I enabled IPSEC-MB to accelerate ChaCha20-Poly1305 for Wireguard.
This part is clear to me, however, what about OpenVPN ?I know that QAT won't help OpenVPN if DCO is disabled, this is also clear to me.
But, when configuring the OpenVPN client, I can see only this option ?
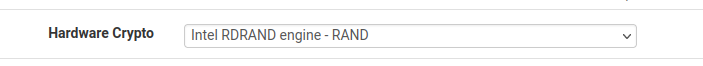
I can't find any documentation about Intel RDRAND engine, does it mean that AES_NI will be used ?
This is how my pfSense is configured:
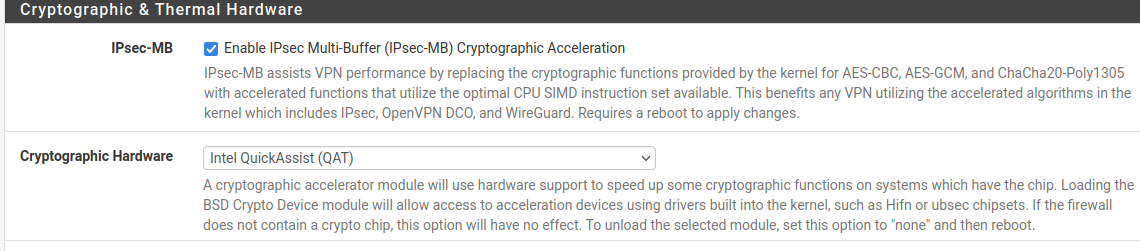
Since I'm not using QAT, I suppose the best thing would be to change the setting above Cryptographic Hardware to one of these ?
- AES-NI CPU-based Acceleration
- AES-NI and BSD Crypto Device (aesni,cryptodev)
And what is the difference between the two settings above ?
-
@mcury openVPN does its own thing, take a look at https://docs.netgate.com/pfsense/en/latest/vpn/openvpn/configure-server-crypto.html#hardware-crypto
-
@SteveITS said in About Cryptographic Accelerator Support:
@mcury openVPN does its own thing, take a look at https://docs.netgate.com/pfsense/en/latest/vpn/openvpn/configure-server-crypto.html#hardware-crypto
hmmm, thanks SteveITS.
I did some tests right now, disabled Intel QuickAssist (QAT) and enabled AES-NI and BSD Crypto Device (aesni,cryptodev), then rebooted.
Kept Intel RDRAND engine -RAND enabled in the OpenVPN client settings, and indeed I can't see any difference in performance and/or resources usage in the Firewall.
Since I'm not using QAT, I'll keep it disabled, and will use AES-NI and BSD Crypto Device and Intel RDRAND in OpenVPN, along with IPSEC-MB to help Wireguard.
Thanks again SteveITS
