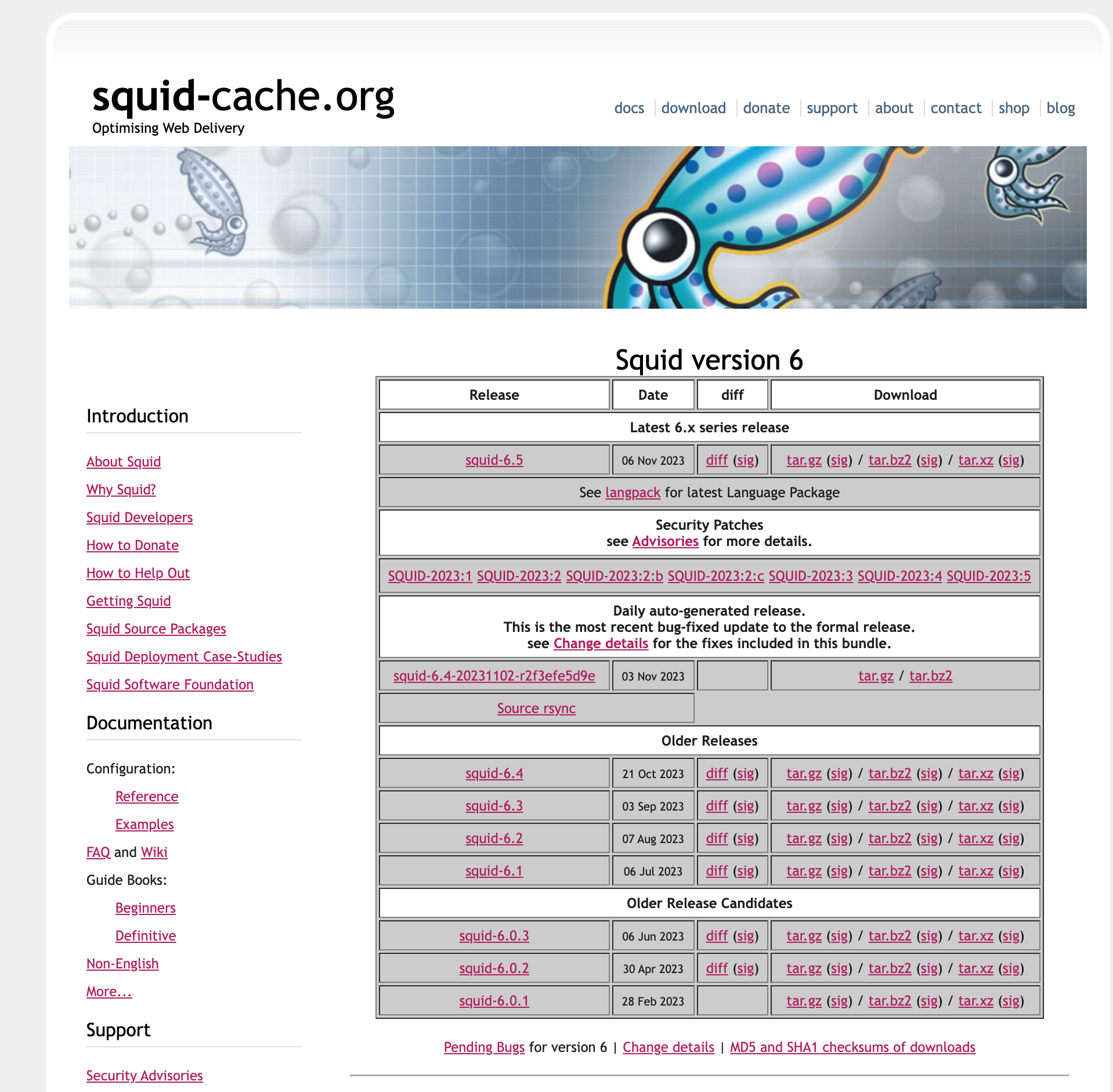
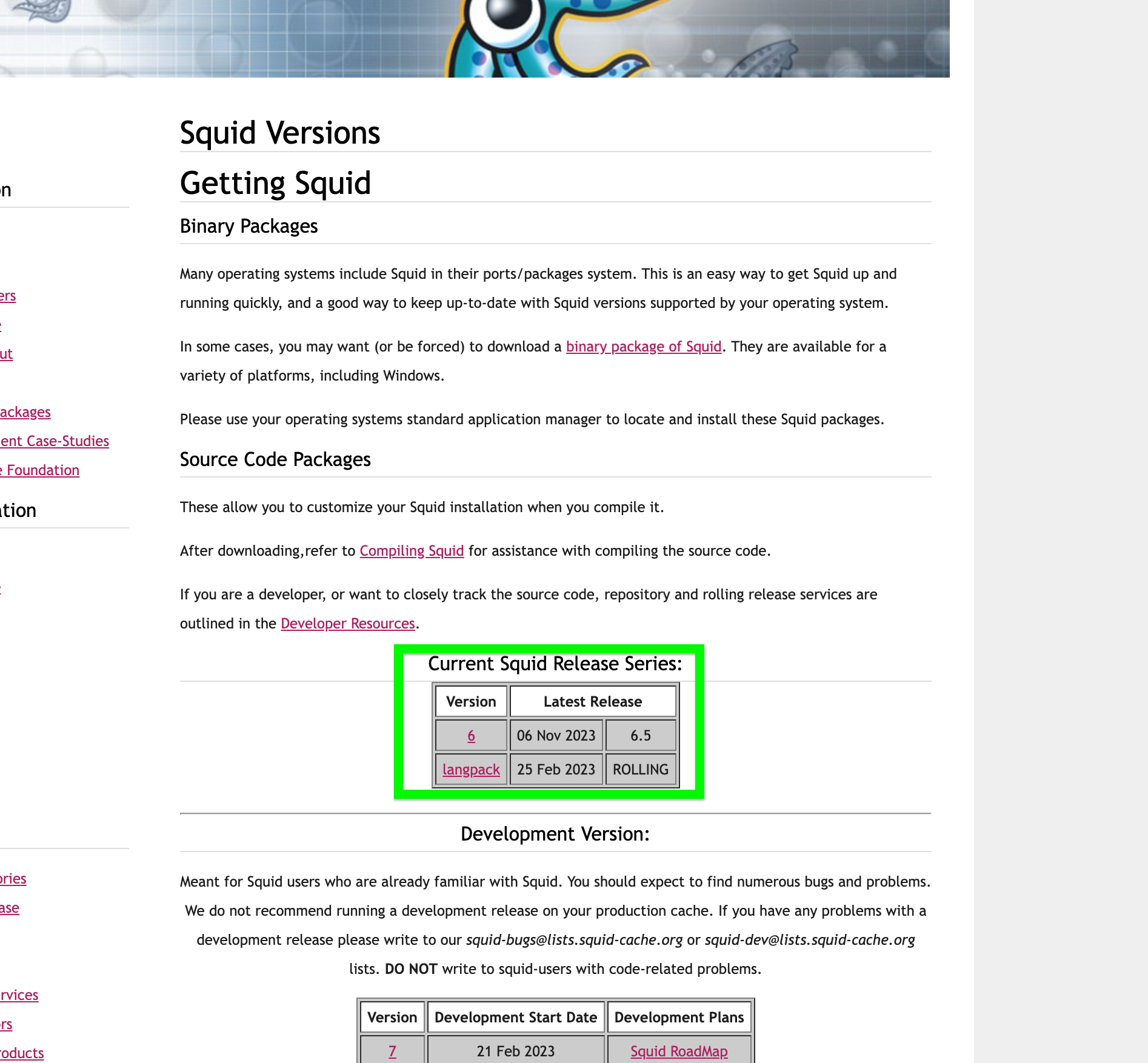
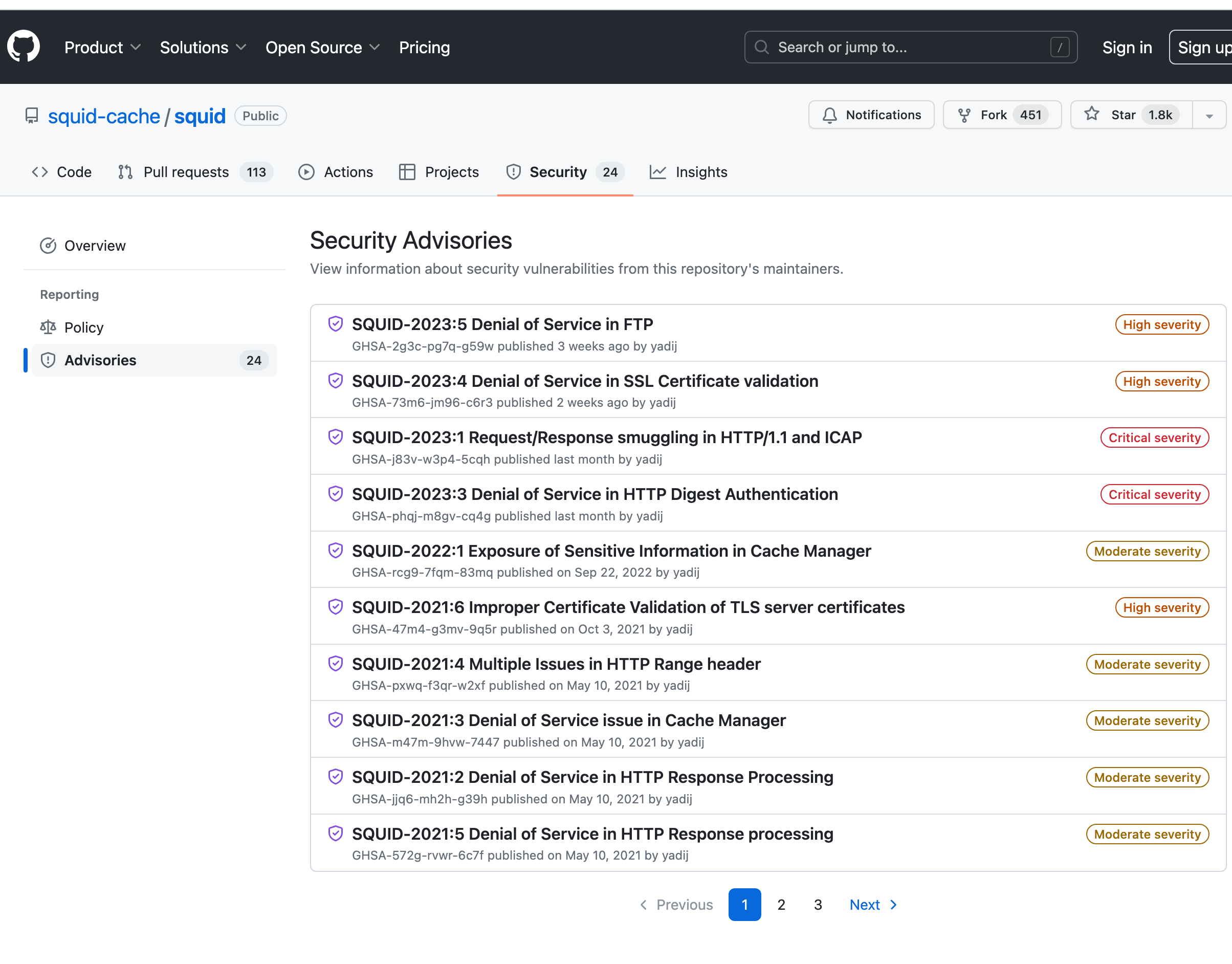
Squid 6.5 !! Nov 6th
-
@lg1980 What is the recommended donation for this update? Also I can start to test this Jan 8th or 9th when all the kids are back in school
-
@JonathanLee said in Squid 6.5 !! Nov 6th:
What is the recommended donation for this update? Also I can start to test this Jan 8th or 9th when all the kids are back in school
I have no economic interest in these updates and support from Squid, whatever I personally feel in relation to covering my hours/dedication to work financially.
-
Did you check this out Squid with all the updates !!!
-
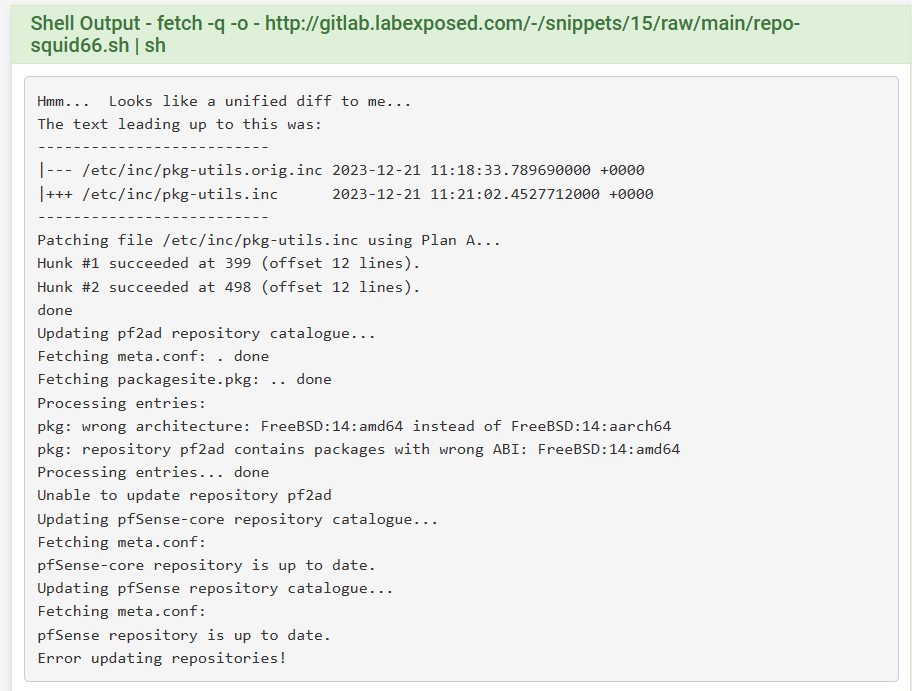
@lg1980 result for use with arm processor
-
@lg1980 how can I test the package?
-
all these updates are great but what happens when it's finally done?
Netgate said squid will no longer be available in the package manager with the next major release of pfsense, so it seems squids days are numbered, at least for pfsense, which really sucks..
there's haproxy, but that lacks av integration.. people might say "it doesn't matter b/c internet traffic is encrypted.. yes, but if you're behind a proxy, then it works well!
so what are we supposed to do?
-
@jc1976 You just manually install it if you use it like us. It will be back alot of users use this.
-
ok, but if netgate removes it from the package manager and we have to manually install it, does that mean the gui portion of it will be removed and all configuring will need to be done via cli?
-
@jc1976 You would have to do it in cmd line after, and use the old packages to install manually
-
https://forum.netgate.com/topic/185029/resolved-quest-for-older-package-wget
I would not use it but if you need it like me..
I did it with Snort to stop the core dumps
Just know that Netgate recommended it be removed.
-
@JonathanLee said in Squid 6.5 !! Nov 6th:
result for use with arm processor
Oh man ! it still doesn't compile binaries for the ARM version, I don't have Netgate hardware here to test.
This is only to AMD64 version architeture.
-
@jc1976 said in Squid 6.5 !! Nov 6th:
ok, but if netgate removes it from the package manager and we have to manually install it, does that mean the gui portion of it will be removed and all configuring will need to be done via cli?
No, personally, and even to maintain pf2ad, I will maintain in a parallel repository (in this case it will be unofficial) Squid and all the tools, as well as the web interface (as it is), with the necessary updates for each package
-
Hi Luiz,
I'm starting from a clean installation of pfsense 2.7.2 and running the command fetch -q -o - https://gitlab.labexposed.com/-/snippets/15/raw/main/repo-squid66.sh | sh
I installed the packages as shown in the image.
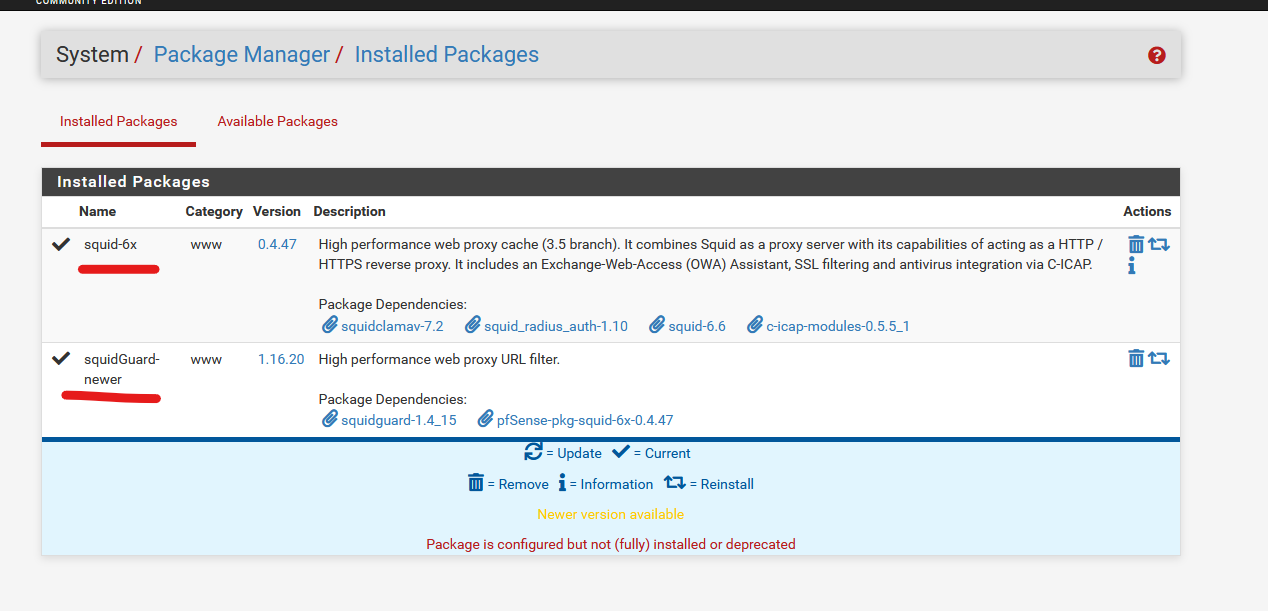
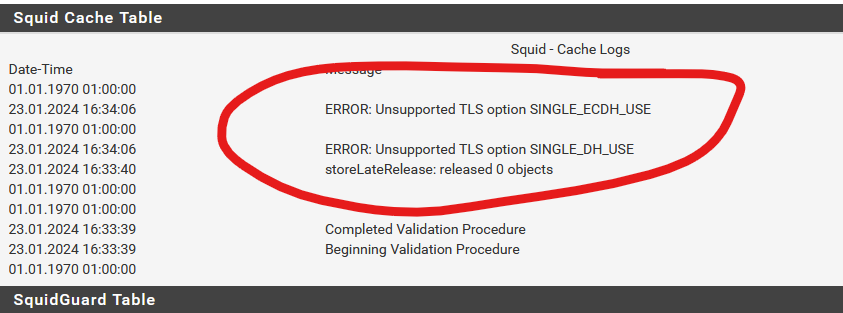
After configuring Squid and SquidGuard I have the following errors:
- in real time
-on the client
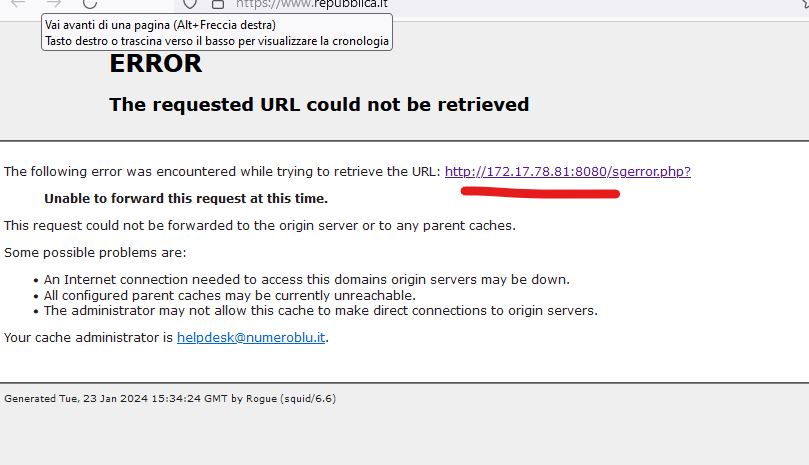
where the ip 172.17.78.81 is the proxy
Is there anything I can do ?
-
@Michele-Trotta interesting…. What does Squids official website say about that error?
-
Hi everyone, since version 2.7.1 pfsense Squid is deprecated and that's why all these strange errors occur.
I was hoping for Luiz's patch. Before abandoning pfsense+squid I will do some more tests because it is an excellent solution.
If you have other solutions to try let me know.
Greetings
Michele -
@Michele-Trotta hello everyone on this post is already aware. This post is for work arounds. Squid itself has many new security updates already available. I am sure you are aware. Thanks, this post is just the open source community coming together to help find ways to make it work. Solutions are needed and being tested in here with high hopes of bring the latest Squid version online for die hard users. Just some open source discussion at its finest. Seems it still has some bugs with that error you see above.
Leading to Ecap over icap I wonder if that would improve security as it can work directly with DoH I am told.
DoH is a big issue with dns based security….. it’s pure https based DNS you can’t force it and it’s reaction based when you block it, ever worse is QUIC. The latest Squid updates have QUIC protocol tools to detect and inspect. That’s https over udp, and it’s a big issue within dns based cyber security detection also. That’s why Squid can’t and won’t die. It’s because Squid has solutions for all the new protocols.
We make solutions not problems.
-
@Michele-Trotta Squid has custom options you can check them on there website, I wonder if something is automatically activated when the new version is installed…
-
@Michele-Trotta check this out…
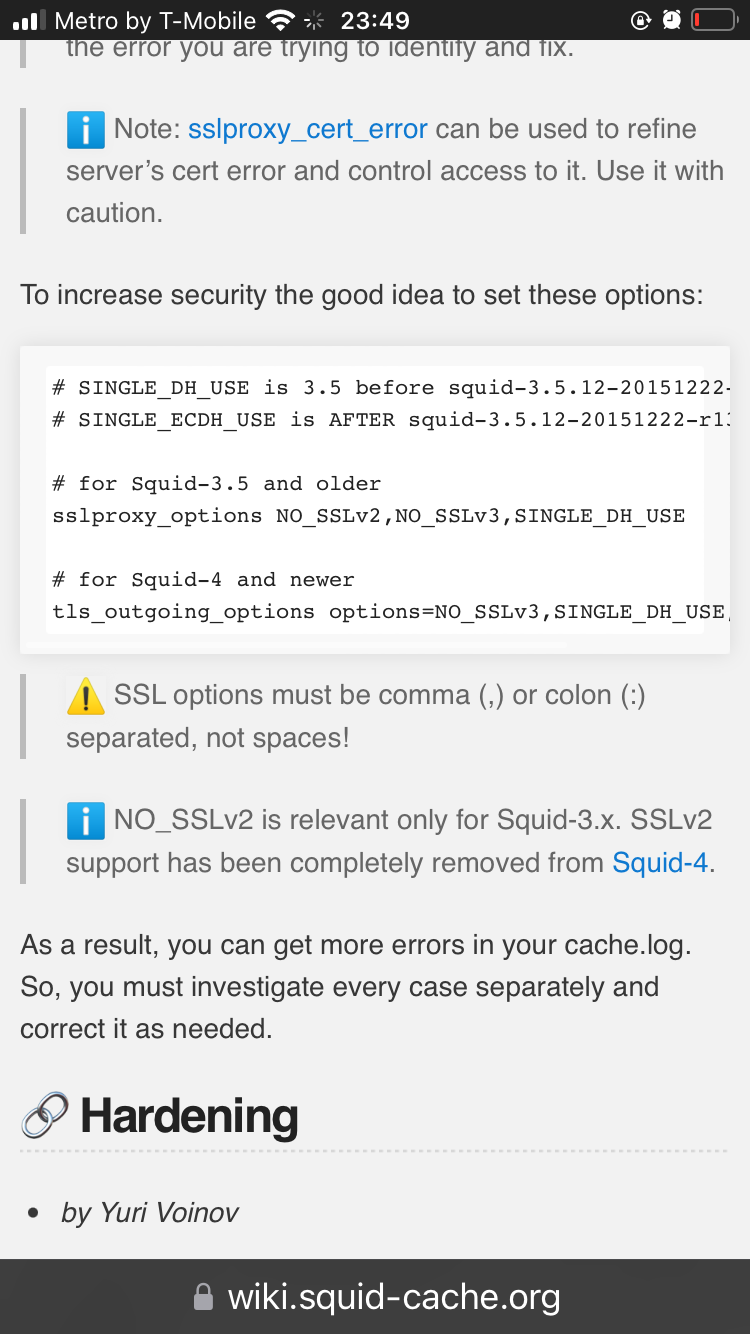
https://wiki.squid-cache.org/ConfigExamples/Intercept/SslBumpExplicit
You might have a certificate issue
-
Hi,
I added a new certificate and assigned it to squid.
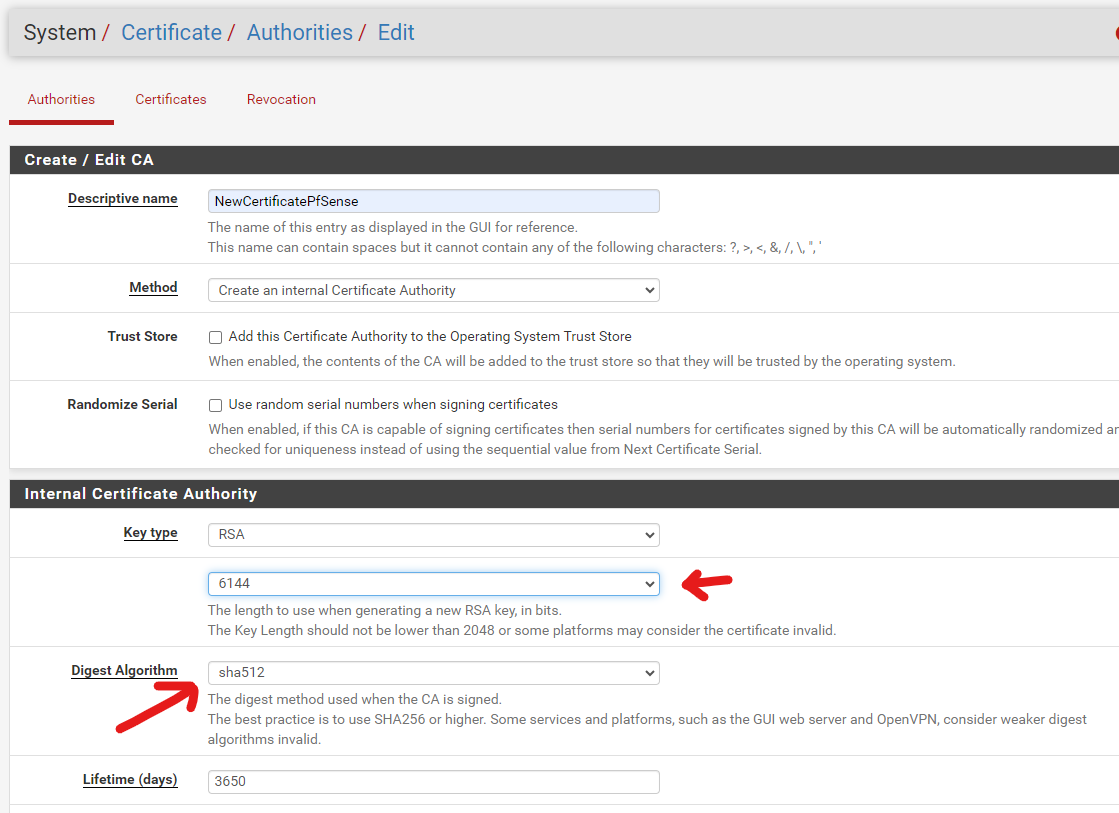
the result is always the same
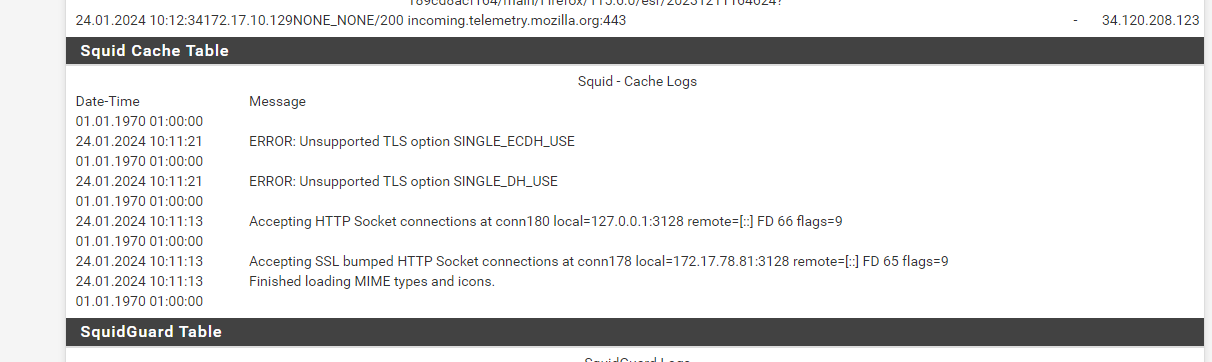
where 172.17.78.81 is proxy
and on client
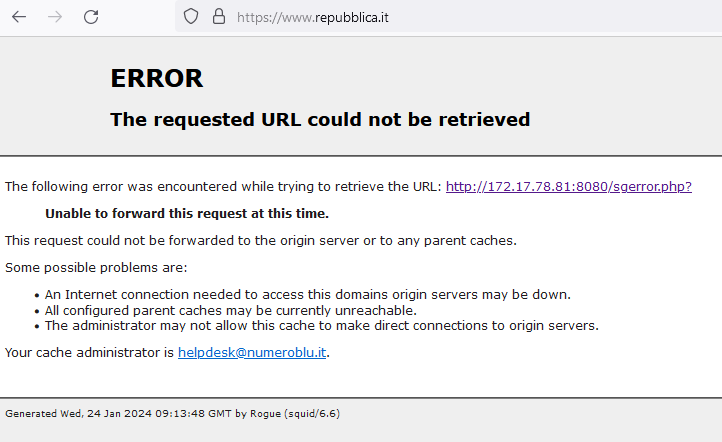
What other tests can I do?
Thank you
-
Try to change settings in this area and see if the error goes away..
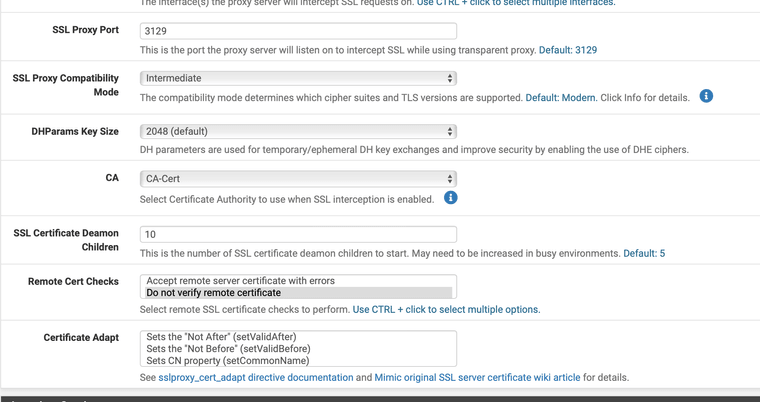
Also try to make the SSL certificate with OpenSSL in command line and import that one into pfSense so its made with Squids application
"Step 1. Configuring the root Certificate Authority (rootCA)
This is probably the part that is most confusing for people and why their setups have failed, Squid need to have a CA assigned to it so that it is able to decrypt parts of the HTTPS header so that it can determine what to do whit that traffic, otherwise all traffic is passed.I used the built-in openssl tool of pfSense to generate this rootCA, for this you need to ssh in to your firewall or connect to it over console, when at the console menu select option 8 Shell, when you are at the shell prompt you need to manually edit the openssl to give you the necessary prompts and questions for you to configure the rootCA
vi /etc/ssl/openssl.cnf
under the [ REQ ] option change the following line from: prompt=no to prompt=yes
under the [ V3_REQ ] option change the following line from: basicConstraints=CA:FALSE to basicConstraints=CA:TRUE
Then save and quit (to save and quit vi editor use :wq!).
Now we would make a known location in the filesystem to save our rootCA and key file as they need to be imported into pfSense GUI at a later stage, I like to use /tmp for any temporary filesCommand:
mkdir /tmp/ProxyfilesNow move to the folder you created whit:
cd /tmp/ProxyfilesWhen you are in this folder you are ready to start the openssl tool and start to create your rootCA, you start whit generating your KEY file by running the command:
openssl genrsa -out myProxykey.key 2048
This will create an rsa key file named myProxykey.key that we use to sign our rootCA whit in the next command for generating the pem file for the rootCA
Create a pem file signed whit key using command:openssl req -x509 -new -nodes -key myProxykey.key -sha256 -days 365 -out myProxyca.pem
This will prompt you to answer some questions to generate the needed pem file in my case it is as below, you need to change this for where you are
US []:NO - Country code
Somewhere []:Oslo - State or province
Somecity []:Oslo - Your city or town
CompanyName []:IT-Monkey - Name of your company or business, "make something up if you are a home user"
Organizational Unit Name (eg, section) []:IT-Department - What part of the company issued the cert, can also be left blank
Common Name (eg, YOUR name) []:Admin - Your name or identity in the company
Email Address []:admin@it-monkey.local - Your contact emailAt this point you should have 2 files in your /tmp/Proxyfiles directory
myProxyca.pem
myProxykey.keyThis can be double checked whit command:
ls -la
If both are there then you are ready to download them and exit the shell environment and continue to the GUI of pfSense, if not you need to look over any error or try again.
To download these files I like to use WinSCP as its fast to navigate and find the files you want to move you can also do this from pfSense Diagnostic -> Command Prompt option and select the file path of:
/tmp/Proxyfiles/myProxyca.pem
/tmp/Proxyfiles/myProxykey.keyIn the download box, this is somewhat slower to navigate but works just fine.
Now as you have these files on your desktop or computer you need to open them in a text editor, I prefer Notepad++ as it's able to adjust the formatting layout of the text but any text editor will work as you will need to copy paste the information in these files to fields in the pfSense GUI.
Navigate to System -> Cert. Manager -> CA's
Here you want to add a new CADescriptive name: SquidCA
Method: Import an existing Certificate Authority
Certificate data: Copy \ Paste the info from myProxyca.pem file
Certificate Private Key: Copy \ Paste the info from myProxykey.key file
Save and apply"Ref:
https://forum.it-monkey.net/index.php?topic=23.0