OpenVpn clients access rules
-
Hello,
I used so far pretty simple setup for my OpenVPN network. Let's say I have two LANs accessible from VPN and two other clients that access the LANs.
I have both remote LANs at OpenVPN server setting and I allowed Inter-client communication. So far no issue but I didn't like that a new computer on one of the remote LAN can access the other LAN and also I would like to manage now the access to remote LANs from different clients connected to the OpenVPN server.
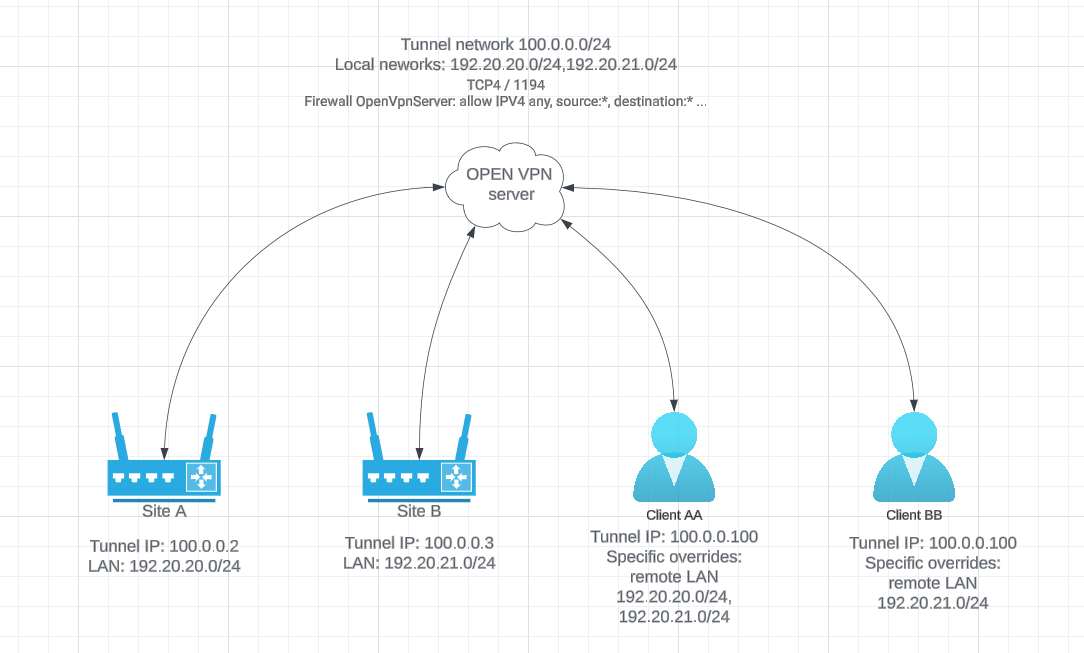
I am trying to have this setup with client-specific overrides but so far I am not able to access any remote LANs from another client.
Client AA can access both remote LANs (A,B) and client BB can access only site B.
I have an OpenVPN firewall rule to allow all communication.
Can you please direct me to accomplish this?Thank you very much for any response.
-
@LukasH
First of all, you should better use Private network ranges for both, internal networks and VPN tunnels to avoid issues with accessing public sites.The "Remote Networks" field in the client specific overrides is meant to state networks behind the respective client.
Anyway, I'd suggest to not state the local networks in the CSO.However, you need such CSO for the sites A and B. Here you have to enter the respective clients local into the "Remote Network" box.
And in the server settings you need to enter both local network into the "Local Networks" box to push the routes to the clients.
For limiting access use the CSO to assign static IPs to the clients and add proper firewall rules.
Remove the check at "Inter-client communication". -
@viragomann
Hi, I tried exactly (at least I think) what are you describing here. But with no success.Server OpenVPN:
- tunel network: 10.10.0.0/24
- local networks: (site A)10.10.10.0/24, (site B)10.10.11.0/24
- uncheck "Inter-client communication"
Client A CSO:
- tunel ip: 10.10.0.100
- local network: 10.10.10.0/24
Site A CSO:
- tunel ip: 1010.0.2/24
- remote network: 10.10.10.0/24
OpenVPN FW rules:
- allow all protocols and IPs for this moment, for OPT1 (tunnel network) as well.
I can see traffic in the firewall rule, to reach site (A), but there is no response from the site.
This setup functions only with the "Inter-client communication" option check.

Here is the client A reaching to site A device.I will do better with local IPs in the future thanks.
-
@LukasH
With Inter-client communication enabled, pfSense cannot filter the traffic, because it doesn't enter the interface.