VLAN/Firewall Access for Admin Only on any of the firewalled Vlans
-
I have run into an issue trying to access Pfsense from another area that only has access to the internet (PrivateIP Block rule) via Wi-Fi. Yes I'm new to Pfsense and firewall Rules. I do not want to break the network.
Just a little guidance would be helpful. Thanks in advance BigA. -
You can control access to the web GUI by adding an ACL with an alias on who can access the GUI port by layer 2 address and or restrict specific networks by way of cider addresses. Be careful as another network also has access to the GUI also.
You can creat a rule that says
Interface lan source lan network destination 192.168.1.1
And change it to
Interface lan source an alias with several addresses
Or set it to block all !alias and Netgate it.
Only the alias addresses can access it that way.
Example 192.168.1.0/24 access to gui 192.168.1.1
If you create another network say 10.0.0.0/24 it will also have access to web gui on 10.0.0.1
Also you can change the port and restrict access that way.
-
@JonathanLee Great Thank You, I will try this Tomorrow. I understand the risk, but this is a Home network that will only be accessed by me. This info will be useful down the road if I can configure it as you stated.
Awesome start to learning Pfsense firewall applications!!!! -
Look at Netgate configuration examples they have a bunch
-
@BigA said in VLAN/Firewall Access for Admin Only on any of the firewalled Vlans:
to access Pfsense from another area that only has access to the internet (PrivateIP Block rule)
Rules are evaluated top down, first rule wins, no other rules are evaluated. If what your asking is how to allow some device or network that is limited to talking to other rfc1918 address (ie your other networks)..
Just create a rule that allows who (what IP or network) to talk to your pfsense gui.. Be it the pfsense address on this network, or another pfsense IP, the built in alias "this firewall" could be used to be any IP address.
So for example here is example locked down rule that prevents access to pfsense IPs other than specific (dns, icmp, ntp) etc.. And blocks all other access to any other rfc1918 address space.
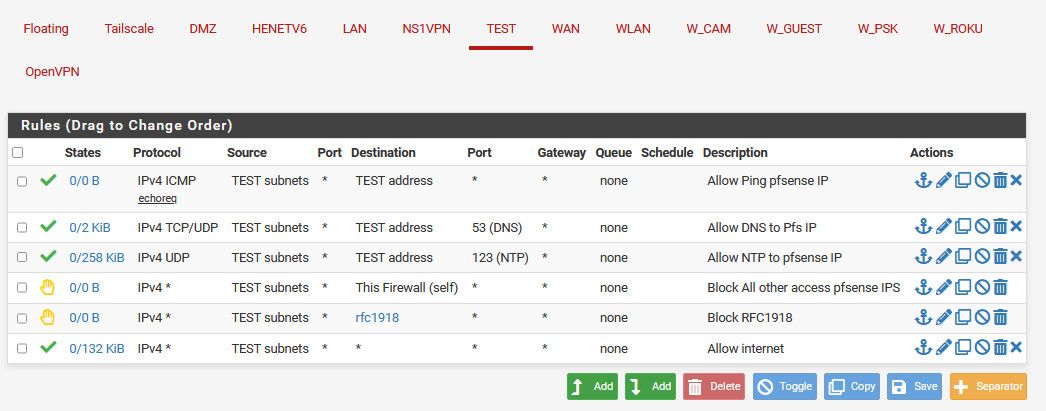
So while these rules only allow this network "test subnets" which is 192.168.200/24 in my case.. To access icmp, dns and ntp on pfsense IP address in this network 192.168.200.253 for me.
It blocks access to any other pfsense IP and rfc1918... I could if I wanted create say a rule that allows access to the pfsense IP on this network "test address" on the port my webgui listens on 8443
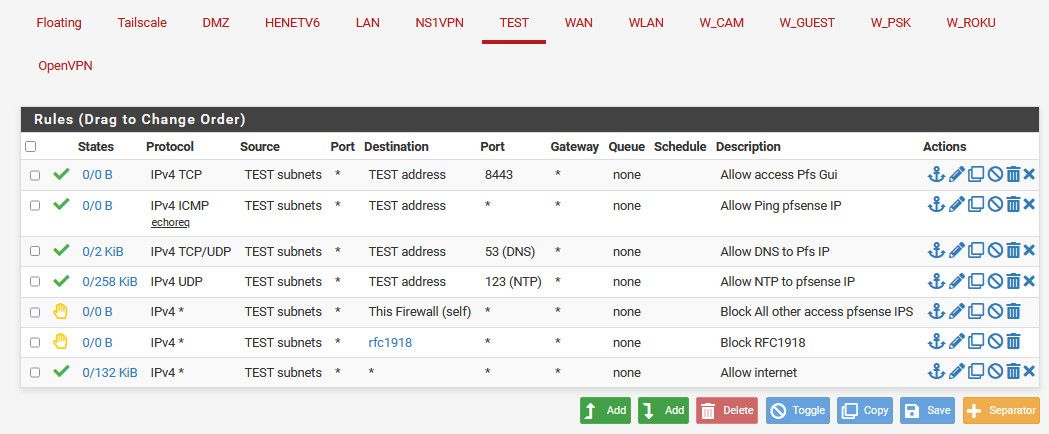
This rule could be adjusted for your needs, only say a specific IP on this network, say 192.168.200.x for my network. if you want multiple ports say 80,443,22 etc.. you could create an alias that contains these ports. Or just create multiple rules.
As long as the rule(s) are above where you block rfc1918 you would be able to access the web gui.
Rules are evaluated in order, so if you don't hit a rule that matches be it allow or deny then you fall all the way through to the bottom and are denied by the default deny rule (that isn't shown in the gui).