Firewall WAN Rules - Wildcard Port Allow Doesn't Work How I Expect
-
I have been struggling with getting some VLAN web sites/applications accessible from the WAN. I had a firewall rule that allowed ANY to 'This Firewall' with the port marked as a wildcard/asterisk. I assumed this was correct the entire time but for fun I added the same rule but with the port specified and all my desired web traffic started coming through over WAN.
Why does the single rule (such as the one Wireguard made) not allow all/any if there is an asterisk?
Here are the rules that didn't work for a couple of ports
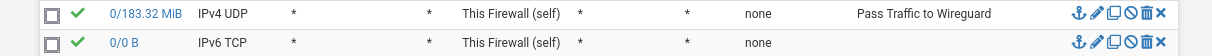
Copying the rule and just adding the port allowed that port through. Is this normal, and why? I am just a beginner, but this seems counterintuitive with my limited skill/knowledge. Can anyone explain? If I need to post more rules I will, The only other rules are ones with specific ports for OPENVPN, Wireguard, and then the standard blocking of BOGON/PRIVATE networks, with some other rules for port forwarding synology and minecraft services.
-
@kn4thx in general any port would be a bad idea because it allows the entire Internet to try to log in to your router.
Rule order issue? They apply in order.
If you’re trying to control access for clients already connected via Wireguard, that’s not on the WAN interface: https://docs.netgate.com/pfsense/en/latest/vpn/wireguard/rules.html
-
@SteveITS The Any Source/This Firewall/Any port rules are at the top. Wireguard made the ANY to This Firewall rule so I assumed that was just going to be normal and catch everything. Should that not exist even though Wireguard created it automatically?
-
@kn4thx said in Firewall WAN Rules - Wildcard Port Allow Doesn't Work How I Expect:
Wireguard created it automatically?
Your saying wireguard created a any any rule on your wan?? I find that highly highly unlikely and would for sure should be reported..
There is no way that would be correct..
-
@johnpoz You are correct. It was labeled in a way that it did not look like how I label my rules. I checked the Netgate Wireguard documentation and it has that same labeling for that Wireguard rule. I must have forgotten to pick a port for the rule back then as I was starting brand new. Thank you for calling attention to that. Now everything is making sense more with the rule being incorrect.
-
@kn4thx I find it unlikely that it would of used the "this firewall" alias as well.. I would of used the interface you set, not every IP on pfsense. Like wan address, or optX address, etc..
That built in alias has great uses, but for a rule to allow traffic into your wan for a specific service - no that would not be the correct use of that alias..
I use it for example to block a locked down vlan from talking to the pfsense IPs.. Because it includes the wan IP which is normally public and can change. And normally you allow any dest IP in an internet rule, etc..
Here is example of how I use that alias.
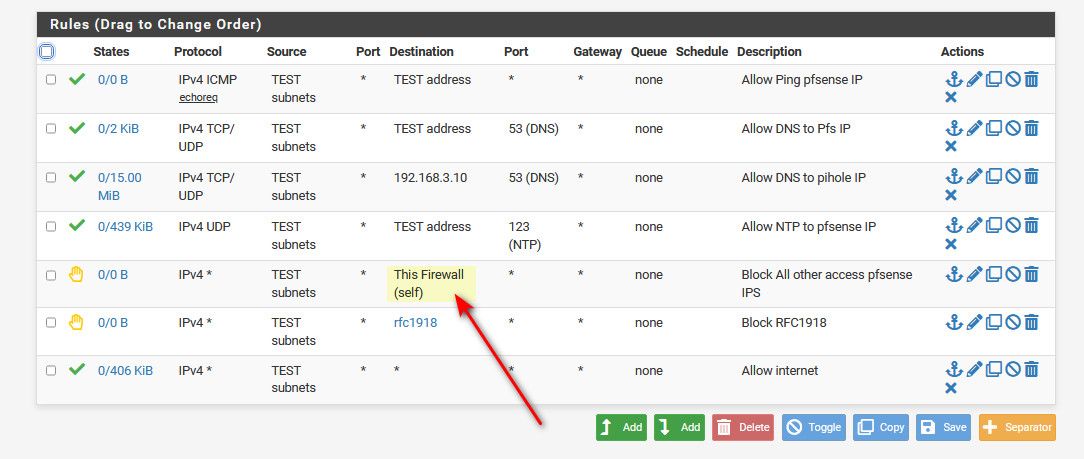
This will prevent clients on this vlan from talking to say my pfsense gui IP 8443 on the public IP, which that last rule would allow because it allows any any for internet access. And any other services I didn't specifically allow, and also if I happen to change the gui port, or the public wan IP changes, etc. etc..
So your all sorted, everything working?
-
@johnpoz Everything is working now, thank you. It looks like it's time to go back and review all of my rules now that I understand a lot more than when I first started piecing it all together. I really appreciate your education and time!