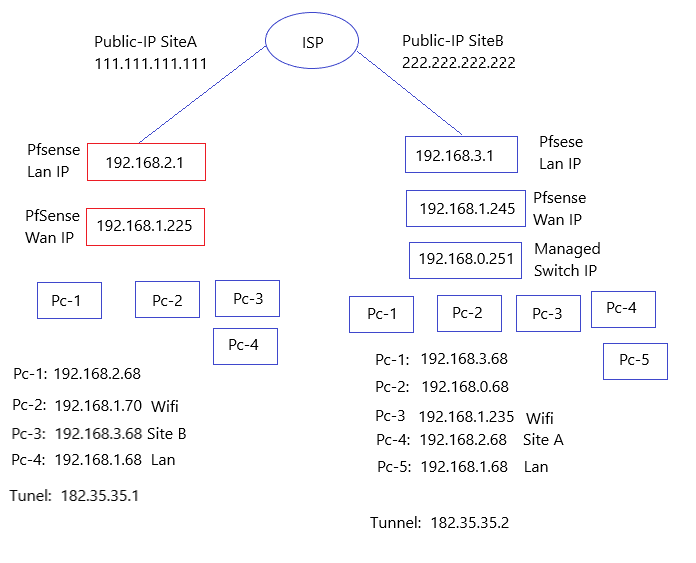
Wireguard site to site vpn, lan site not accessible.
-
Thanks for this link!
I'm sure, I'll have the same issue again but anyway. I think, this is the only way I can train myself.I'll update the outcome very soon.
-
Hi, I have completed the site-to-site VPN configuration as per the provided link. Now, I'm encountering same issue as before.
I can successfully ping both sides of the tunnel and the allowed IPs from the diagnostics page of pfSense. Additionally, I can ping any PC locally on both sides. However, I'm unable to ping any PC on the other side of the VPN connection.
My Hardware connection:
Both pfSense network port 1 are connected to my router(WAN) with a local IP assigned from my router. However, my WAN IP on my pfsense is not my public IP. I'm using my second network port for LAN connection, where my PCs are connected.I'm accessing my pfSense locally from one of the PC from on each side. But after configuring the site-to-site VPN, I can only reach up to pfSense. I'm unable to reach any PCs on the other side of network.
Am I missing any firewall rule for LAN, Currently I don't have any rule for Lan.
On wan, I'm port forwarding the wireguard port to wan address.
On tunnel interface all traffic allowed.
On LAN : None
There is a interface called wireguard, I don't have any rules in it.I have changed my managed switch as well, so both side unmanaged switch connected on lan port.
-
@sutha If you don't have any LAN rules nothing on the LAN can talk to anything.
Do you mean you have no rules other than the default ANY rule?Post pics.
Go to VPN/Wireguard click the edit button for the tunnel and post a screenshot. Block ONLY the the keys and endpoints.
Same with the peer.If you followed that link, go to interfaces, click the one you're using for the tunnel and post a screenshot. No need to block anything on here.
System/Routing. Post a sceenshot.
Firewall/Rules. Post shots on LAN, Wireguard and the Wireguard interface.
-
These are the rules, which I have in pfsense firewall.
Wireguard:
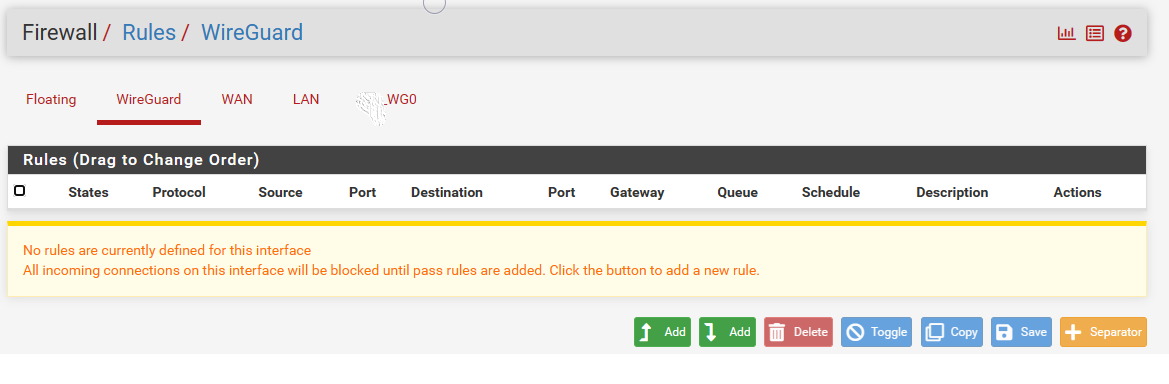
Wan:
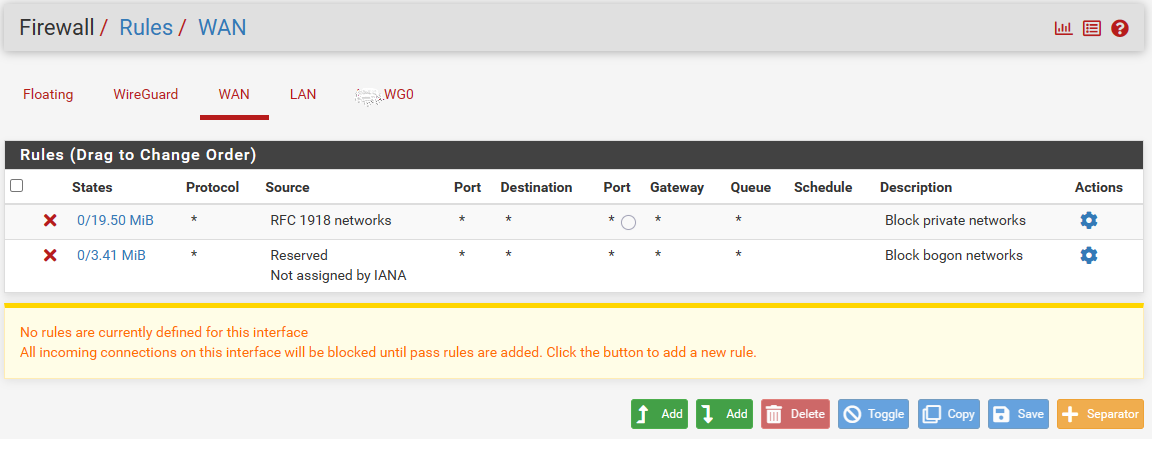
Lan:
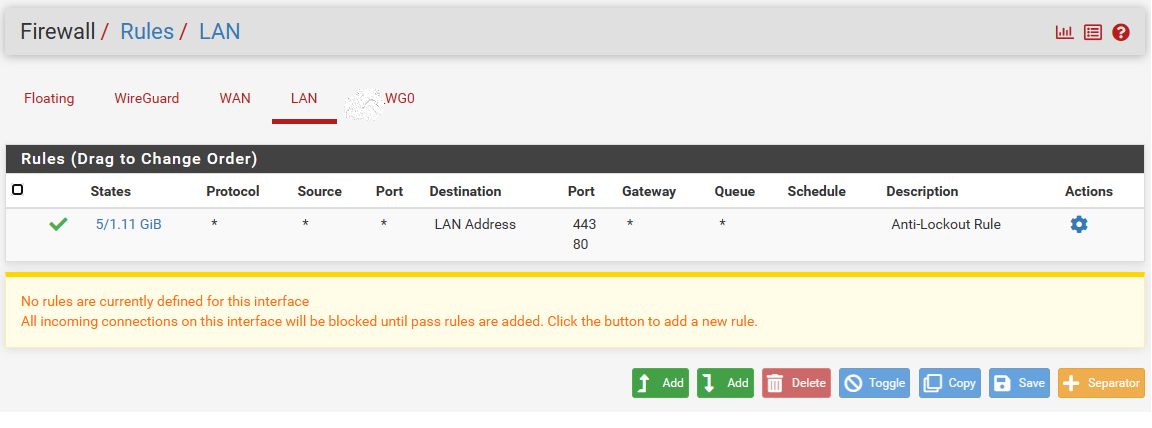
Tunnel_WG0:
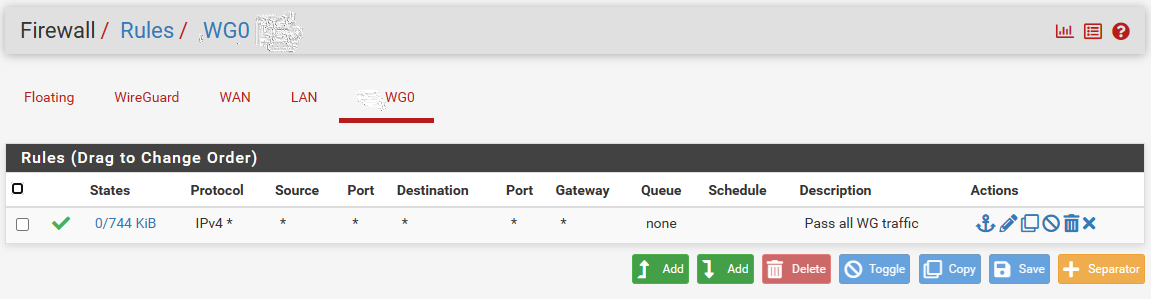
I have added the lan and wireguard rule, but lan rule make sense. After Adding lan, I'm able to ping from local pc to pfsense ip and from pfsense to local ip without any problem, but still having problem reaching other side of the tunnel.
Wireguard rule does not make any sense. I believe this is because I'm using the tunnel interface(WG0) for wireguard traffic.My current Lan after adding the rule:
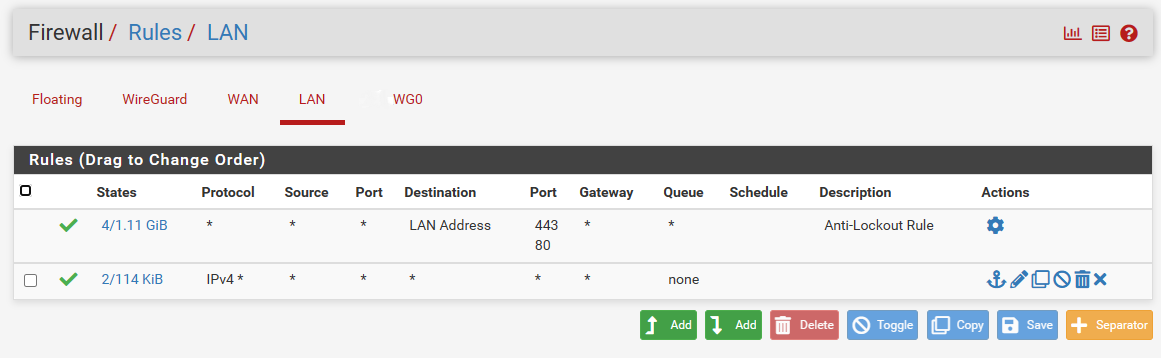
Current Status:
Currently I'm able ping from pfsense A to pfsense B, both tunnel ip and pfsense ip.
Next I'm able to ping from pfsense A to local pc's and pfsense B to local pc's as well, Both way.
I'm unable to ping from PC-A1 to PC-B1 or PC-B2, also from PC-B1 to PC-A1 or PC-A2.Routing -A:
Gateway,
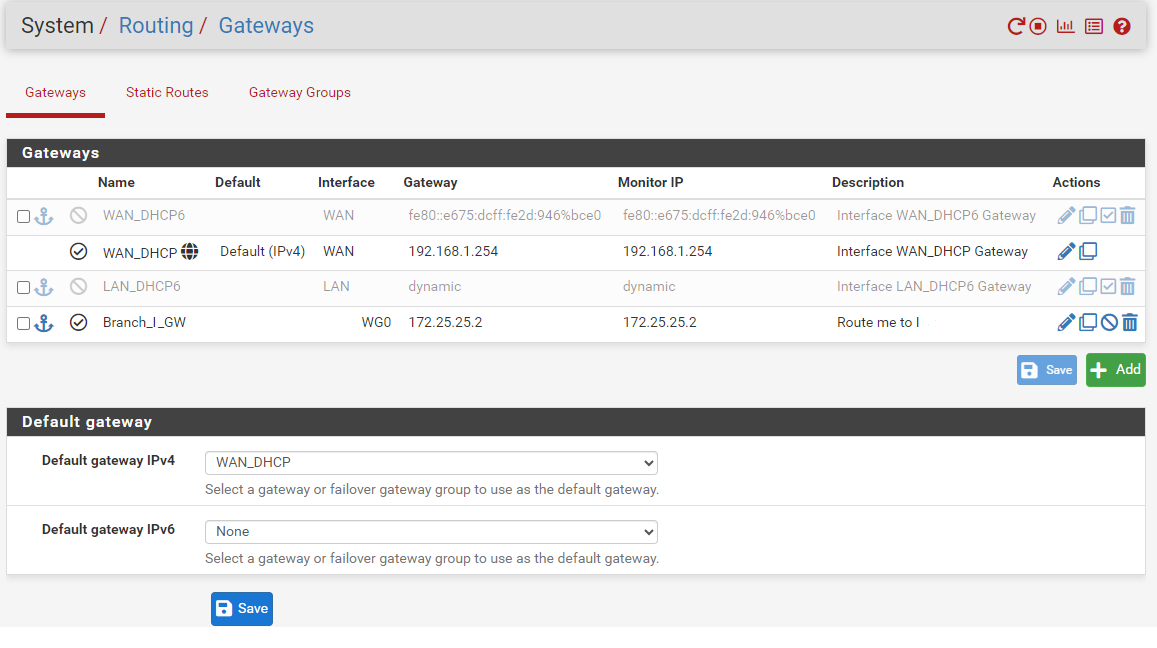
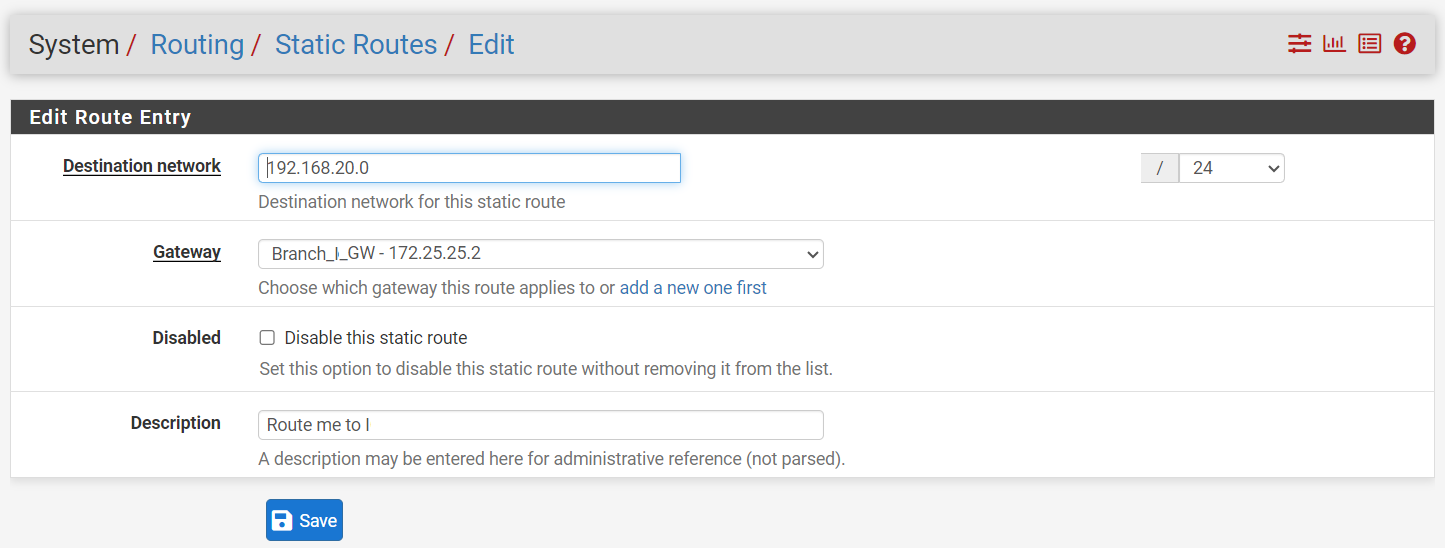
Static Route,
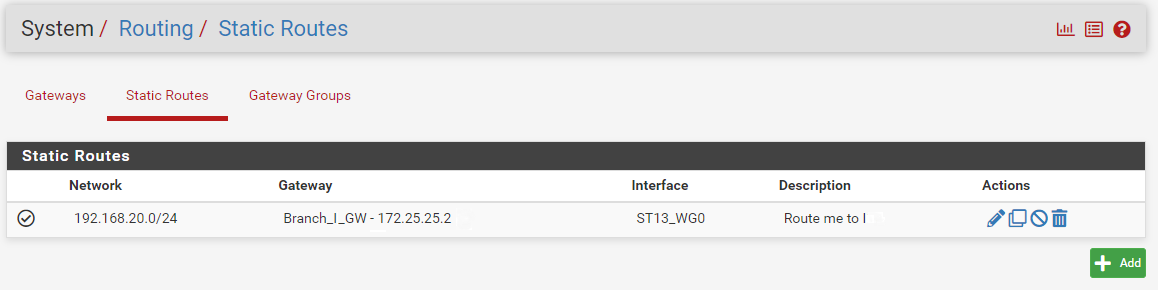
Routing-B: Same as A , but all remote IP(192.168.10.0/24) to tunnel A (172.25.25.1).
I don't know , if I forgot to forward some rule to other side of the tunnel. -
@sutha You have to allow the listening port through the WAN. Add an allow rule for it.
-
I have add a rule for wan as well, see bleo the image.
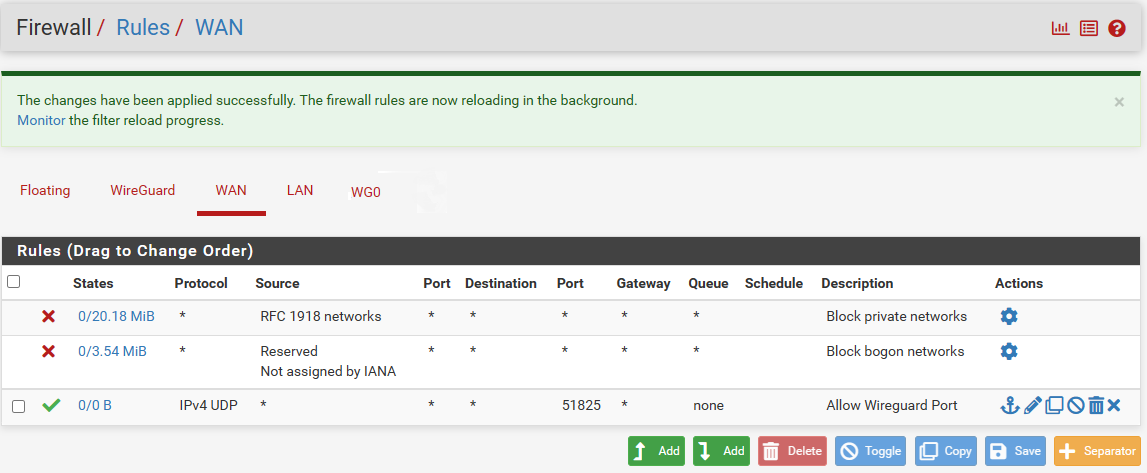
I have added for both side and also tested with any protocol, but no luck. No changes after adding the wan rule.
Curiosity question:
Actually, I'm planning to connect my three locations via VPN to share files or work via remote desktop. I aim to control all PCs from one place.I have not installed any additional software on any PCs to access my remote location, other than this pfSense site-to-site VPN setup.
-
@sutha Listen, I asked you for pics and you only gave me the firewall rules. I know you think you "have everything correct" but no one can help by just going with what you say.
Post the pictures you were asked for if you want further help.
And if you followed the link I provided exactly (you obviously didn't or the firewall rules would've been there already), it would work. -
Okay, here is what you're expecting.
Side A:
Tunnel:
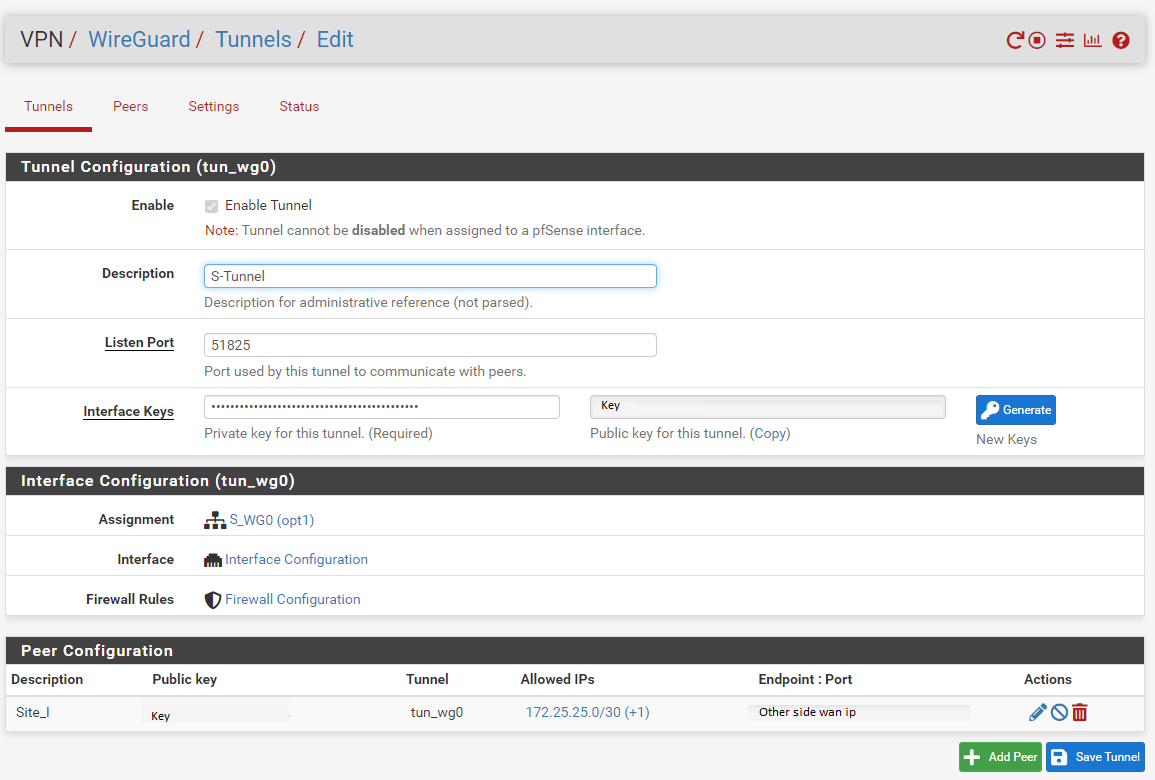
Peer:
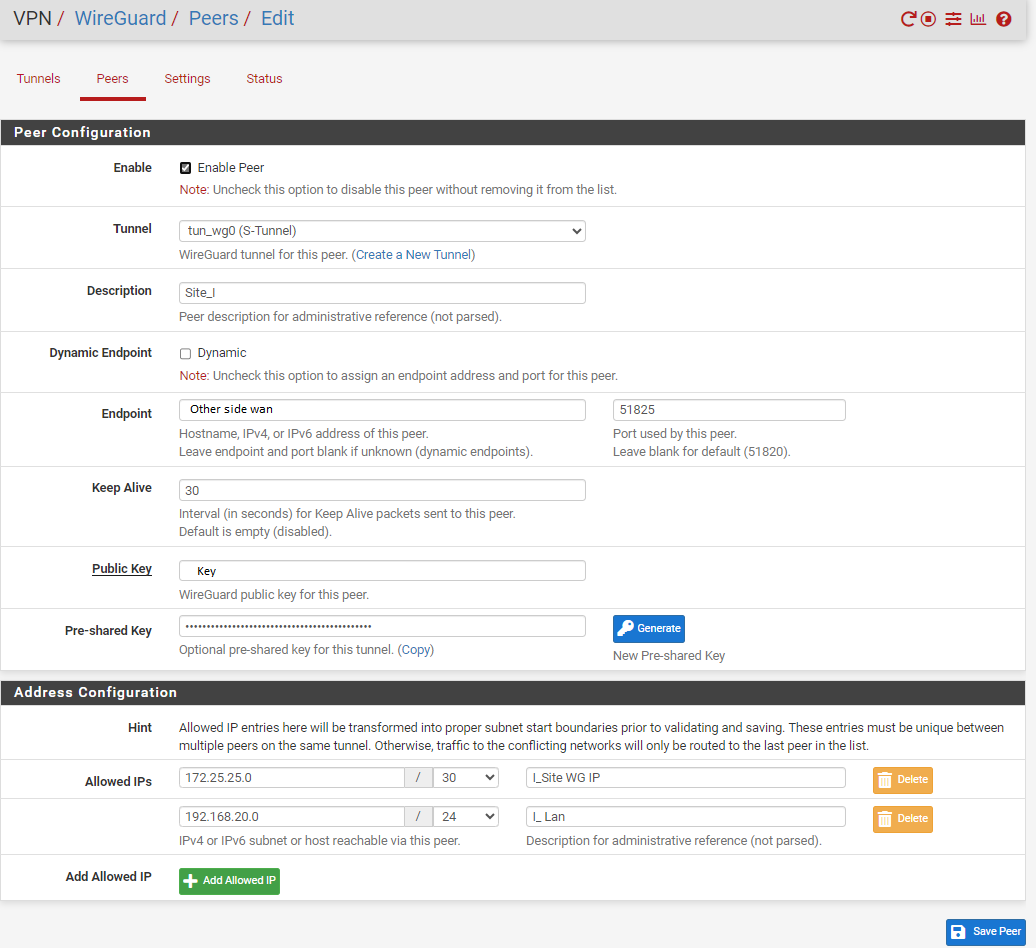
Tunnel Interface:
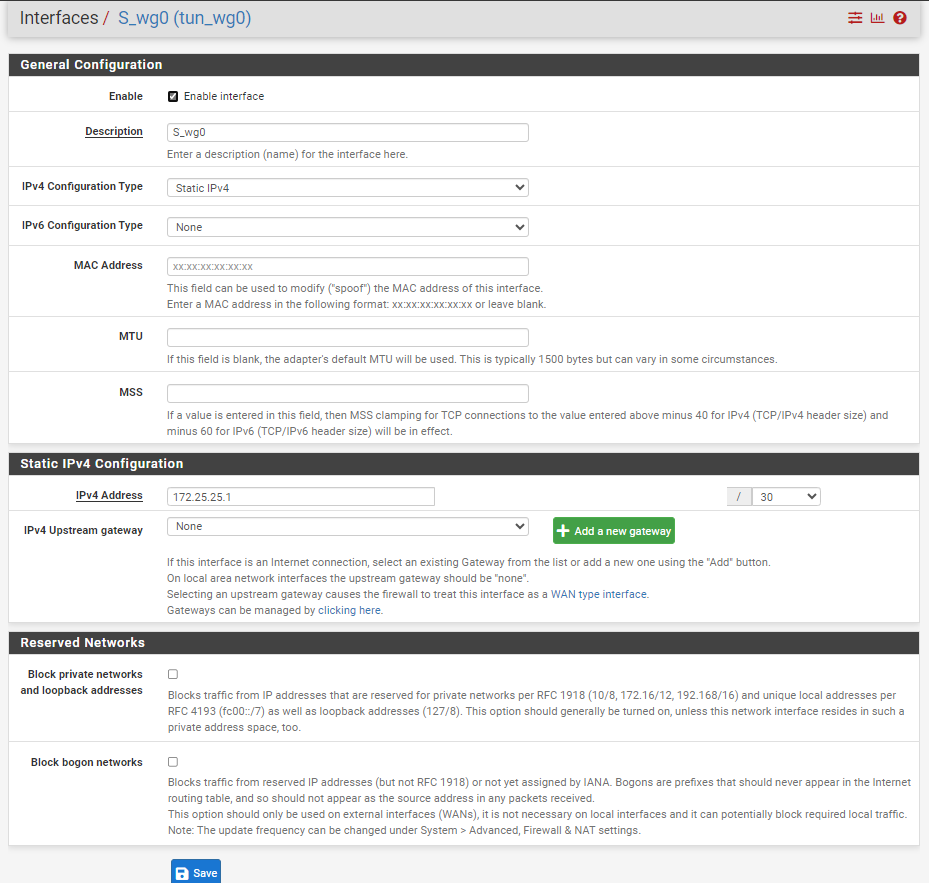
Gateway:
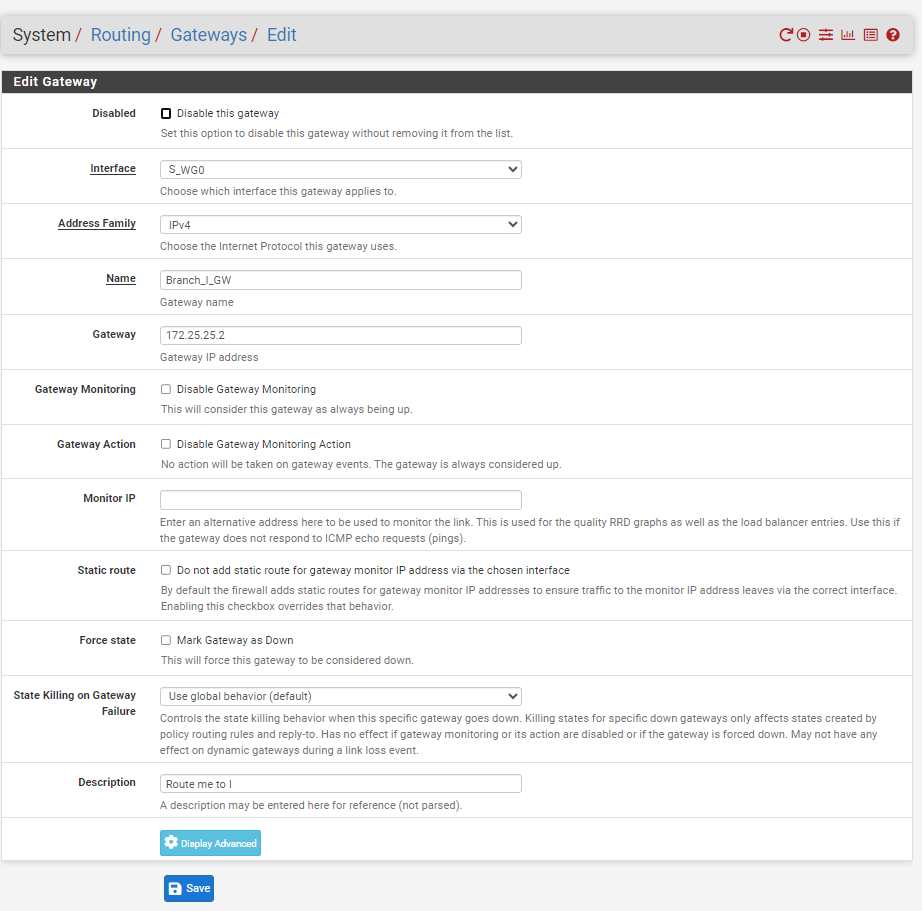
Routing:
LAN rule:
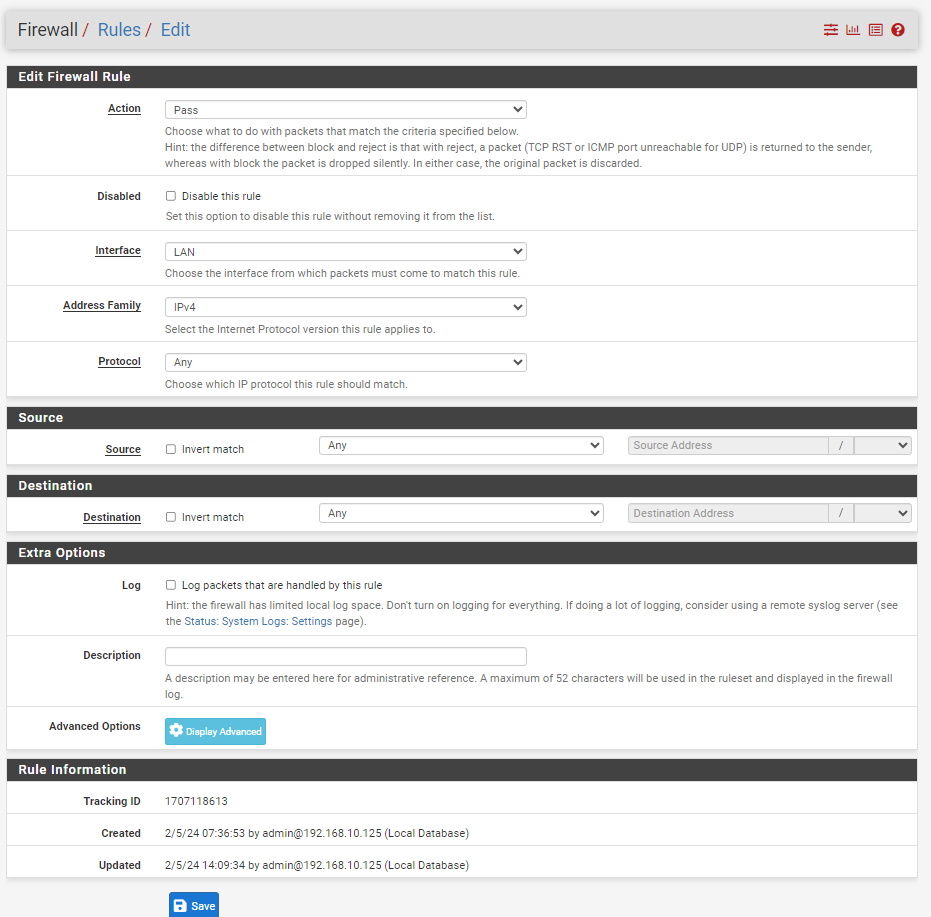
Wireguard rule:
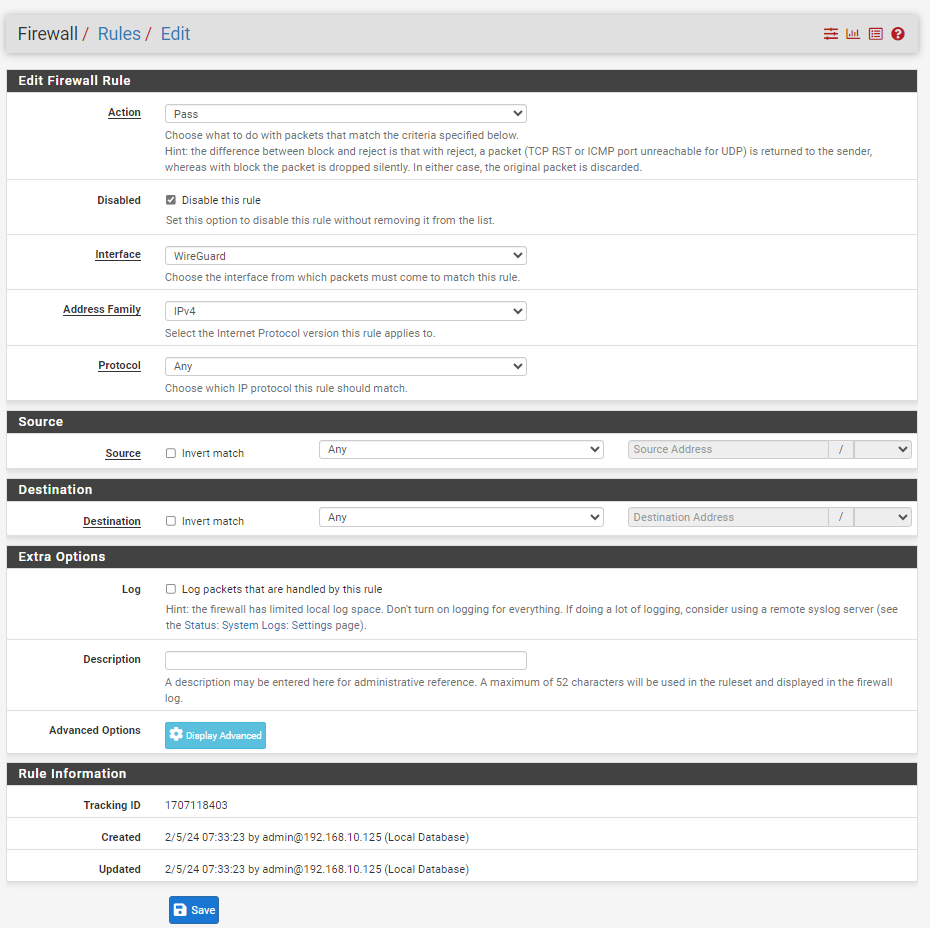
Tunnel-interface rule:
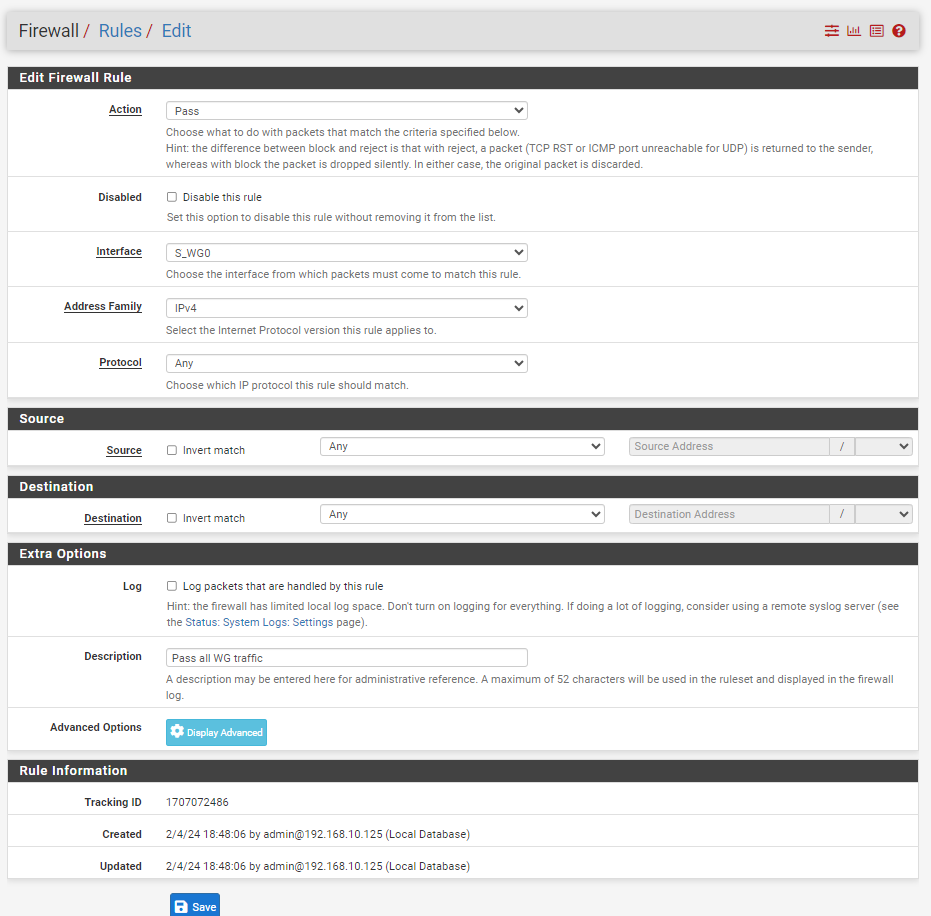
Site B:
Tunnel:
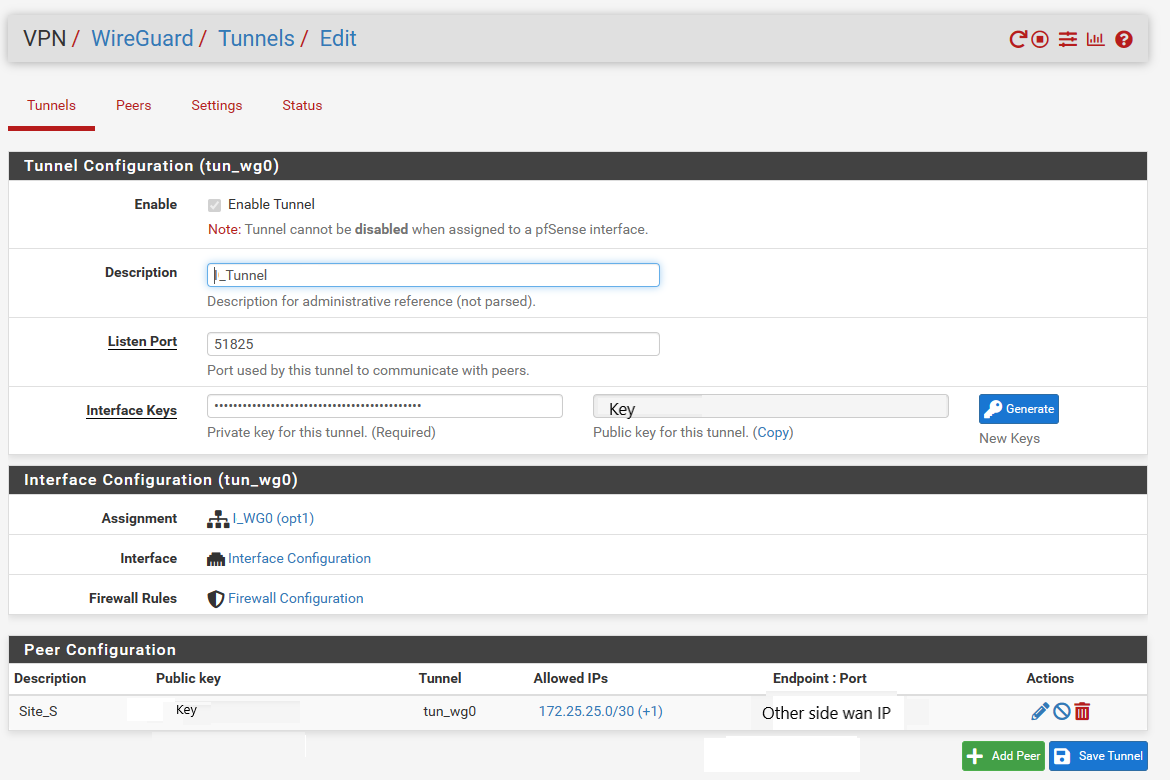
Peer:
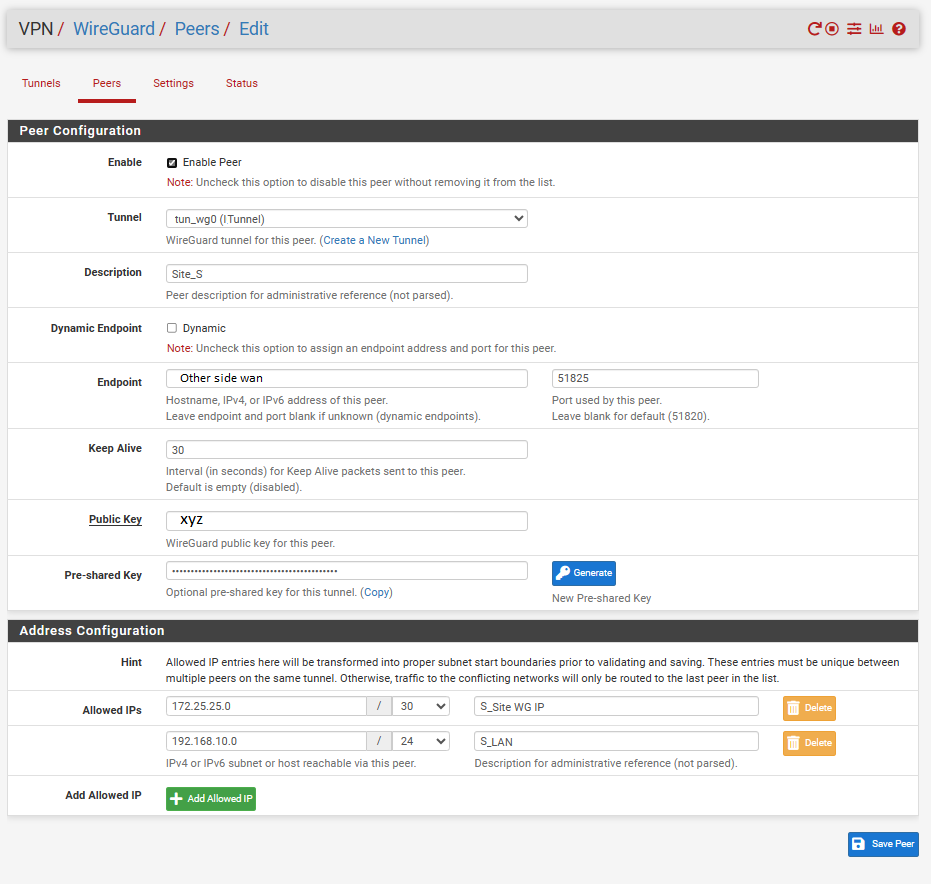
Tunnel Interface:
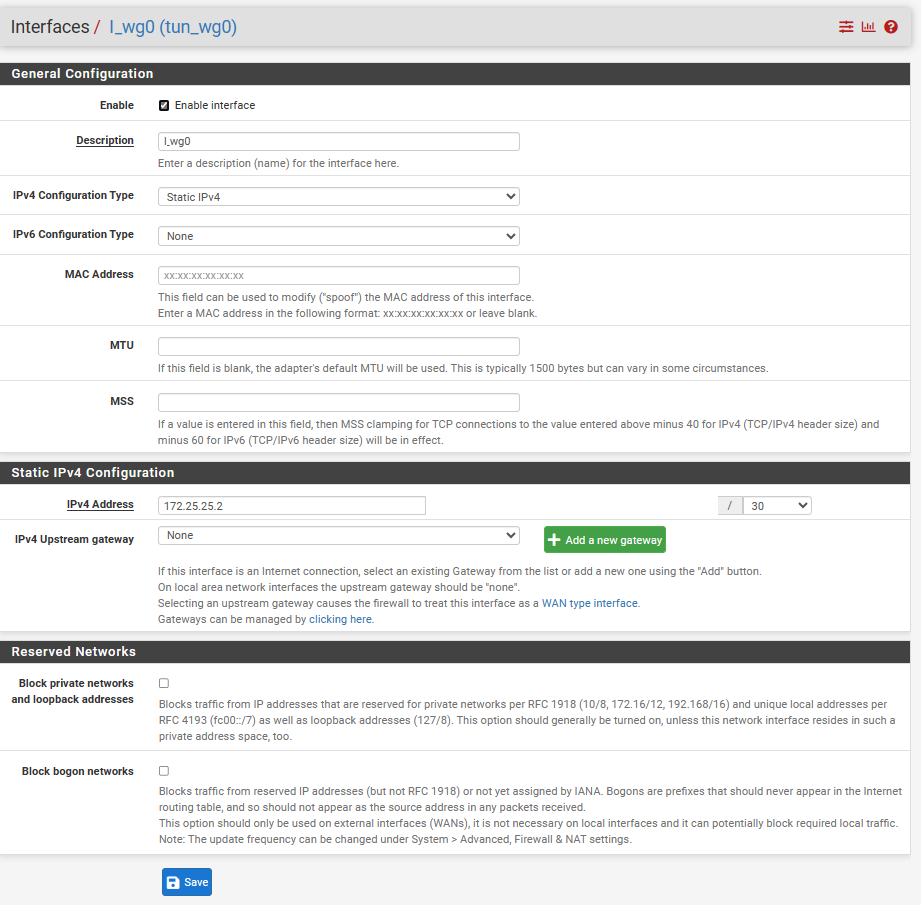
Gateway:
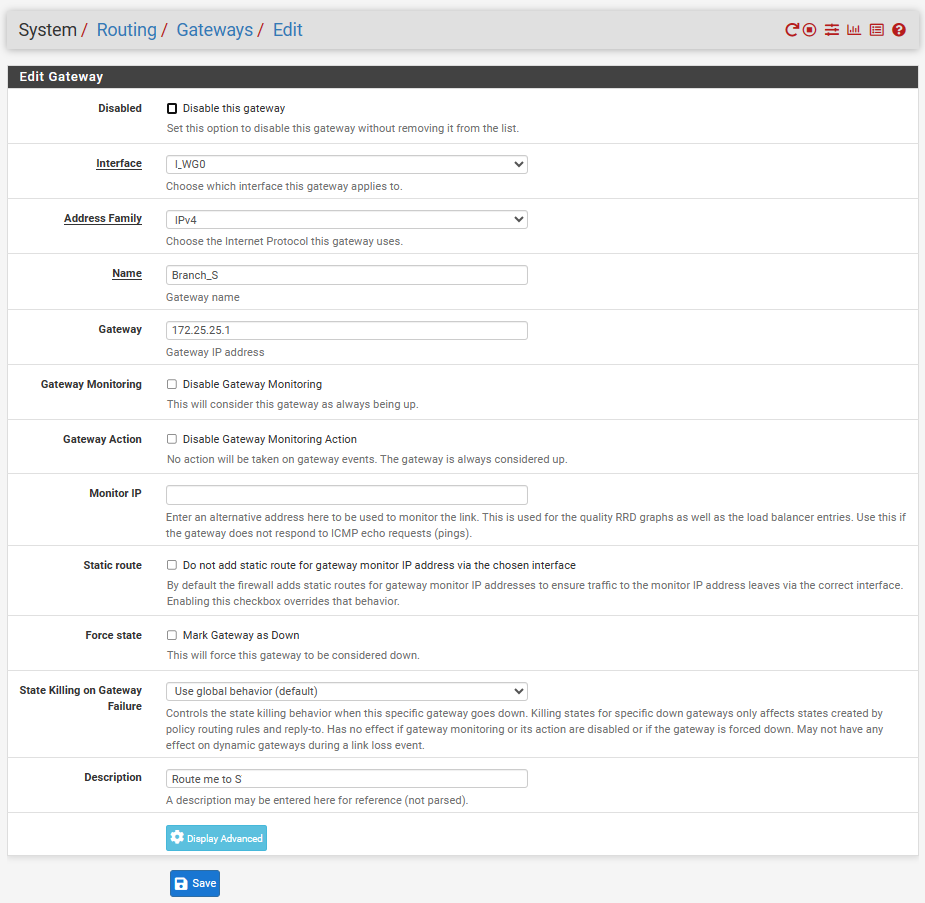
Routing:
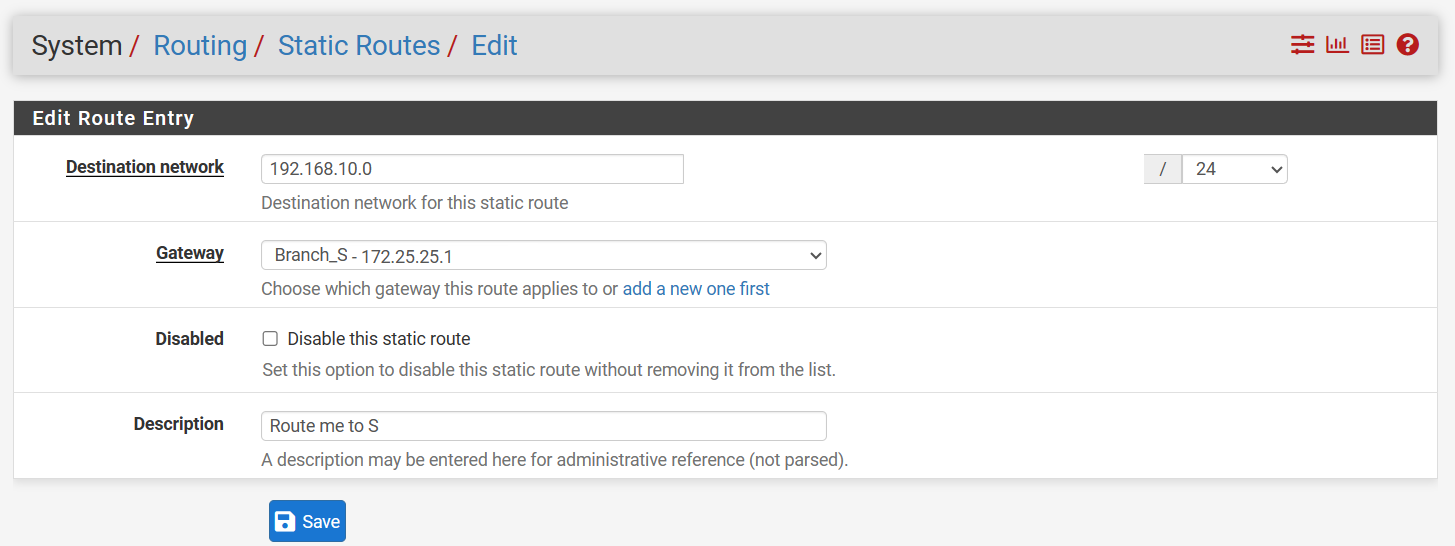
LAN rule:
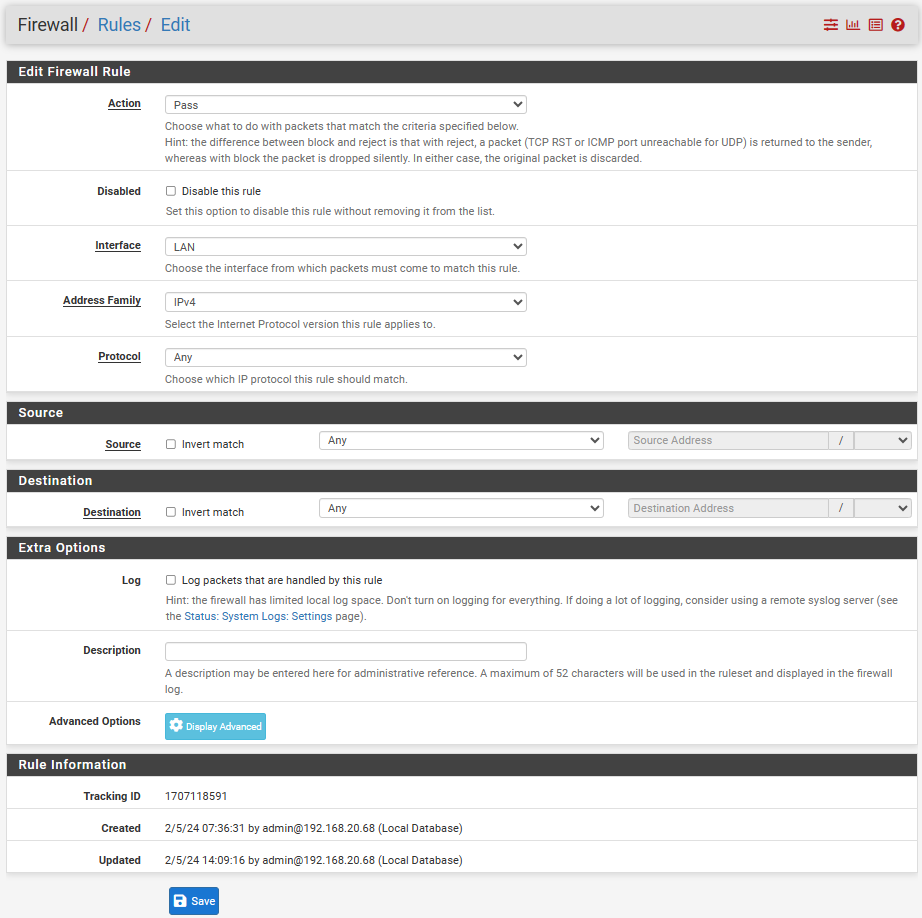
Wireguard rule:
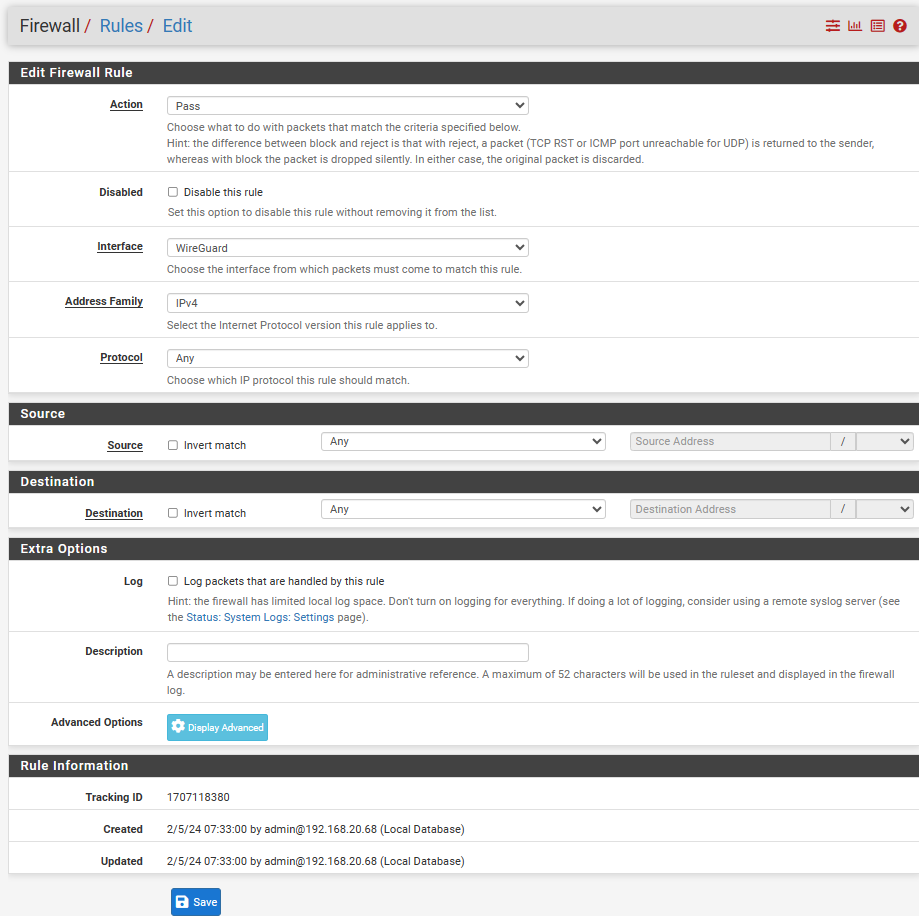
Tunnel-interface Rule
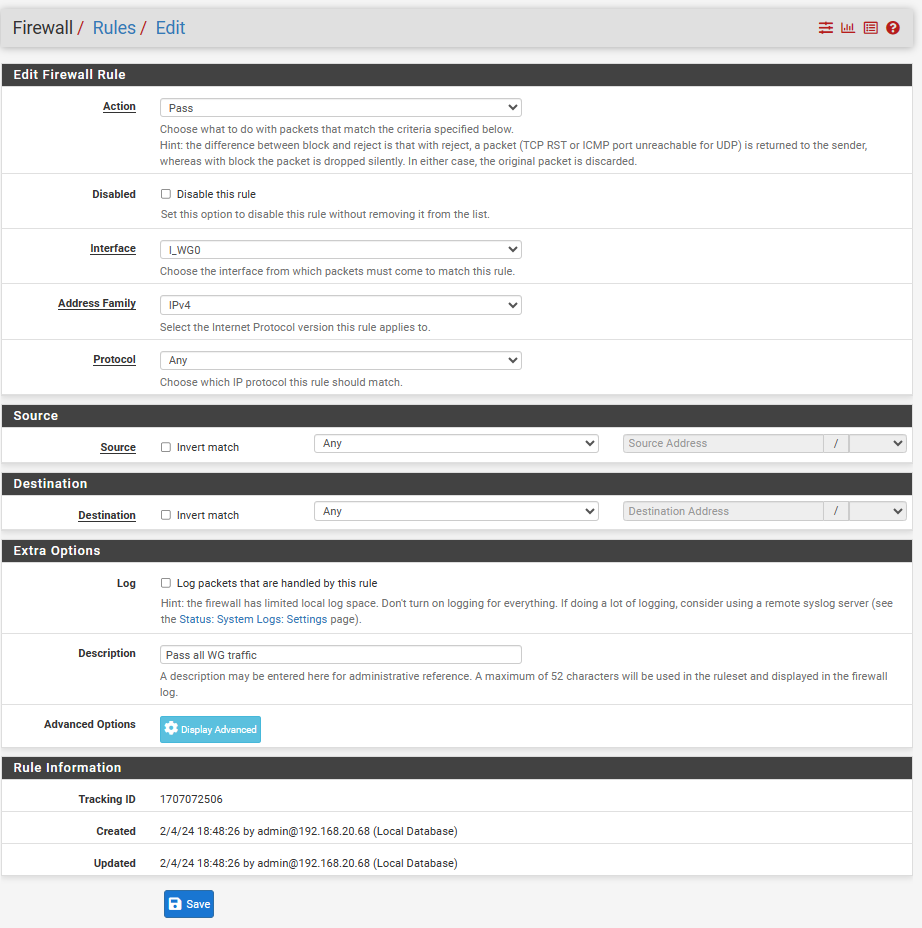
This is my total configuration.
-
@sutha You changed LAN subnets?
Not making this easy, are you?Set the interface MTU to 1420 <--- DO THIS. Very important. (May fix your problem)
What you're calling Side A, what is the LAN subnet?
-
I have change the lan range but the subnetting is kept according to the link you provided. I want to avoid the same IP range again to avoid any complication with previous setting.
I have change the lan Interface mtu to 1420, it did not work then tried to change tunnel mtu as well but this is also not successful.
I have revert the lan mtu back to blank, but still not working.Final outcome not working, current lan and tunnel interface mtu status are 1420.
Still can't ping other side local pc.
Side A is one of the location and Side B is the another location.
I have marked this in description of the Tunnel configuration as (S) and (I) .
Subnet for tunnel is x.x.x.x/30 and lan x.x.x.x/24 as you can see in the above configuration(don't compare with beginning of this chat). -
@sutha I meant the WG interface MTU only. Bith sides should be 1420. No need to change the LAN MTU.
What is the local subnet on the side A?
I can't make the question any clearer than that. Thought that was clear enough in my last post.(Hint, it's not x.x.x.x/24)
-
Local subnet is 192.168.10.0/24.
-
@sutha Ok. Wireguard is setup correctly.
Whatever the problem is, it's not Wireguard.
These PC's you're trying to get to, how are they configured? DHCP? Is the gateway correct on them?
Start checking the local PC's on both sides.Check the routing tables on both ends.
Also, do a packet capture on one end from the Wireguard interface, then do a constant ping from a pc on the other end. Do you see the replies going out the Wireguard interface?
With the same ping going, do a packet capture on the WG interface on the same side as the pinging PC. Do you see replies coming in? -
Just to clear my confusion.
Side A:
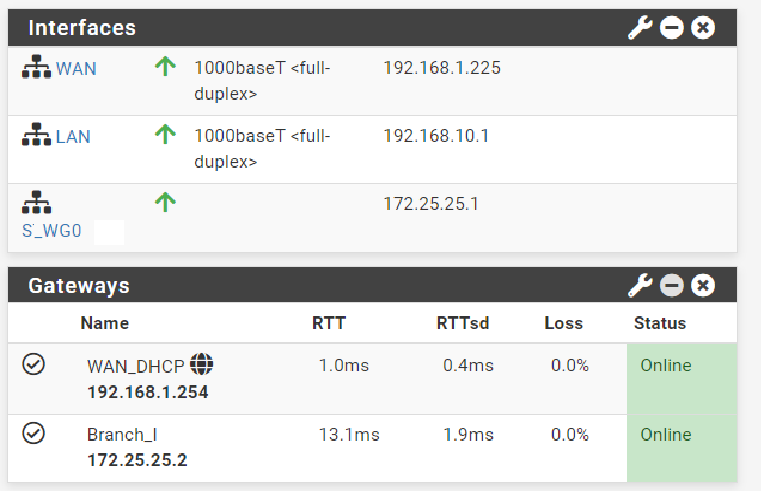
Pc1:192.168.10.125 (Pc with company files from side-A)
Pc2: 192.168.20.125 (This pc is to connect the side-B network)
Subnet: 255.255.255.0
Gateway: emptySide B:
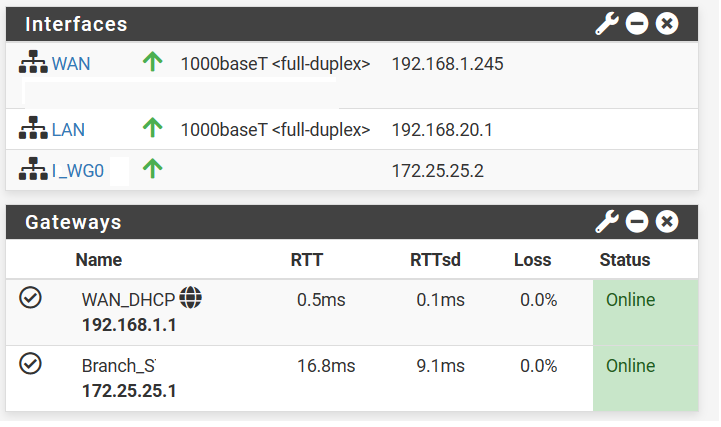
Pc1:192.168.20.68 (Pc with company files from side-B)
Pc2:192.168.10.68 (This pc is to connect the Side-A network)
Subnet: 255.255.255.0
Gateway: emptyBoth sides have a different public IP from the WAN IP shown in the images above. Therefore, I have forwarded the WireGuard port to this particular machine on each side.
Are my ip setting on the pc's are correct or do I need to add the gateway, when yes what is my gateway(tunnel ip,wan IP or pfsense ip).
-
@sutha pfSense LAN IP on both sides.
Side A gateway will be 10.0Side B gateway will be 20.1.
-
Great !
Finally, something is working.
After entering the gateway, I can ping the local PC from the diagnostic page of other side pfsense. However, I'm still unable to ping from the command prompt. Do I need to install the WireGuard peer on every system from which I'd like to connect via VPN, or is this site-to-site VPN setup with pfSense is enough? -
@sutha pfSense is enough.
You created a link from one router to the other. No clients needed. -
Thanks!
I have tried the command tracert from command prompt, it goes upto otherside tunnel 172.25.25.2(I was trying fron tunnel side 172.25.25.1)- first my router
- tunnel ip 172.25.25.2
-
- requested timed out
-
- requested timed out
and so on.
- requested timed out
If I try the same ip from the diagnostic page from pfsense, 2 jumps only.
- tunnel ip 172.25.25.2
- pc ip 192.168.20.68
I'm sure something is blocking from the exit point of the tunnel, now I'm looking for a way how to identify this block(Pc firewall is off).
-
@Jarhead said in Wireguard site to site vpn, lan site not accessible.:
Check the routing tables on both ends.
Also, do a packet capture on one end from the Wireguard interface, then do a constant ping from a pc on the other end. Do you see the replies going out the Wireguard interface?
With the same ping going, do a packet capture on the WG interface on the same side as the pinging PC. Do you see replies coming in? -
A big Thanks to Jarhead. I have succeeded in my aim today, which I had planned for. I can ping both sides and access via RDP, but I still don't understand few things. Normally, if you want to access a network, you need to be in the same range as that network. For example, I would like to access "side A" (192.168.10.0/24) from "side B" (192.168.20.0/24). I always kept a PC with an IP setting in the range of 192.168.10.50 on "side B", and actually, this is the issue with my settings, other than the gateway setting in the past. Today, when I changed this IP to the normal 192.168.20.50, it is working fine now.