P2P VPN server can't reach client, but client can reach server
-
@rlabaza I watched pings come in on as below (from the server ovpn ip to the client ovpn ip. They seem to be arriving fine.
16:24:52.961958 IP 10.0.20.1 > 10.0.20.2: ICMP echo request, id 19195, seq 0, length 64
16:24:53.052314 IP 10.0.20.1 > 10.0.20.2: ICMP echo request, id 33787, seq 0, length 64
16:24:53.972680 IP 10.0.20.1 > 10.0.20.2: ICMP echo request, id 19195, seq 1, length 64I assume that the issue is that the response is not routed correctly back to the server as per the routing tables, but how does one do that with a policy rule?
-
@rlabaza On the client I have added a rule to direct the OpenVPN ip addresses before the general "allow all rule", although it doesn't make sense to me. The "allow all rule" should take care of the OpenVPN addresses as well and send them to the default gateway?
What I don't get is that I have another point-to-point service to a different pfSense box, which is also site-to-site. It runs pfSense 2.6 and traffic between the server and client flows without any issues.
What obscure change was made to 2.7 that breaks the comms to the client without this mystery rule and why is not clearly stated in the documentation somewhere? Or am I just not able to find it?
-
My LAN rules:
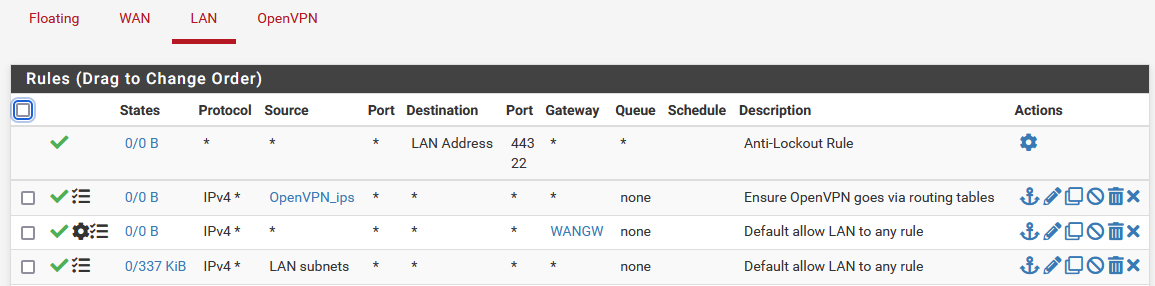
Detail of the "OpenVPN_ips" rule:
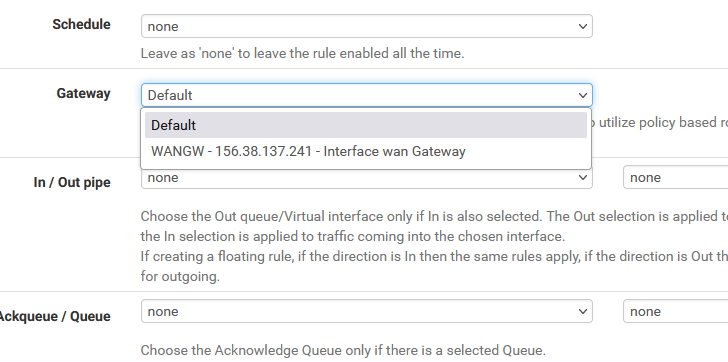
I can only select default or WAN. Default is what the next rule "Allow to any" uses as well.
?
-
So now I have disabled all LAN rules, except the one that sends all LAN subnet traffic to the default gateway.
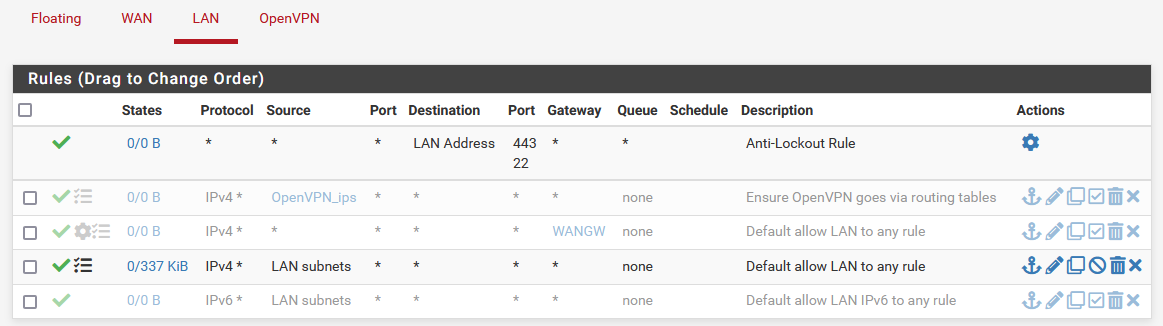
However, I still can't reach the client side LAN addresses from the server's side.
-
Please read and follow this exactly and do not skip any part of it no matter what:
https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.html
I just followed it word for word yet again for one client/one server and it resulted in a working LAN-to-LAN VPN as it has the last several times I tried it. Nothing changed here in the last several years.
You must have a Client-Specific Override even for one client. The override sets up the internal routing in OpenVPN that tells OpenVPN which client should receive traffic for a given subnet. It does not matter how many clients are on the VPN when setup this way, this is still a required step.
-
@lifeboy When I pinged the client side from the server side pfSense box, everything worked fine. But when I pinged from a server-side machine, it would not get to the VPN. Have you tried setting the source in your rule to "*" and not "LAN subnets" alias?
-
@jimp I will redo it again and follow the instructions step by step. After all, it's not a production environment yet unless I can get this thing to actually work.
-
@jimp We use ECDSA certificates instead of RSA. That would not break the routing of traffic from the server LAN to the client LAN, would it?
I'm redoing the tunnel and it connects fine, which to me means the certificates are ok.
-
Please see my reply and the resolution at https://forum.netgate.com/post/1151441.
Thanks to all for the massive effort!
-
@lifeboy Glad you're working now. What I learned on my journey to solve this problem is that there are many different causes that manifest in the same failure signature. The story of my (professional career) life. We were always the lightning rod.