Rule order bug?
-
@fero1233 said in Rule order bug?:
But this morning, it was all re-arranged again.
have a look at the "config.xml" file.
There is a section that start with :
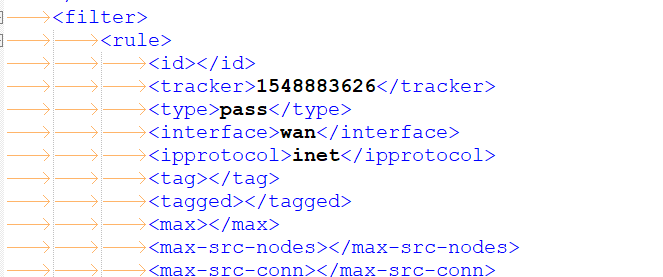
From then on, for every interface (WAN is called WAN, LAN is called LAN, the second LAN is called opt1, etc), in order ( ! ), you rules are listed as they should list in the GUI, and way more important, in the order the firewall rules are listed in 'pf'.
Having a last "pass all" rule, and then it gets listed at the top, that's a security issue (for me).
So : question : is the order in the config.xml also changed ?
If so, that would explain the miss ordering.
The question now becomes : who/what is saving the config, and what impacts the the firewall rules to be ordered differently ?What pfSense packages do you have installed ?
-
In config, it is also wrong order today. It was correct yesterday just after update/reboot/edit/save/apply
But i found this in config:
<revision>
<time>1707220801</time>
<description><![CDATA[(system): pfBlockerNG: saving DNSBL changes]]></description>
<username><![CDATA[(system)]]></username>And i am using pfblocker. So wondering if it is pfblocker, that changes the firewall(?) I might wanna try disable it.
Other plugins
-
@fero1233 said in Rule order bug?:
And i am using pfblocker. So wondering if it is pfblocker, that changes the firewall(?) I might wanna try disable it.
pfBlockerNG creates rules and rearrange the order on each update according due its settings. That's why I asked, if your have manually created the rules in my second question.
-
@viragomann said in Rule order bug?:
That's why I asked, if your have manually created the rules
Yes, on this interface all rules are created manually. There are no pfblocker rules at all, on this interface.
-
@fero1233 IIRC pfBlocker logs a config change at every cron interval. Is that when the reordering happens? Disable/reschedule its update to double check.
-
@SteveITS said in Rule order bug?:
Disable/reschedule its update to double check
I have completely disabled pfblocker for now, to test.
Will let it run like this, for a day or so. And if it works, i will try to look in to, if it is posible to disable update on that specific interface. -
@fero1233 said in Rule order bug?:
I have completely disabled pfblocker for now, to test.
Will let it run like this, for a day or so. And if it works, i will try to look in to, if it is posible to disable update on that specific interface.One thing we cannot see as you cropped the image that way is if that allow any rule is the default allow any from the LAN interface or if it's one you created yourself.
So another thing you can try would be to actually create another "pass any any" rule with a custom description so you know which one is which. Then move that below the Blocks and check if only the default/old allow is getting pushed up or if the blocks are actually pushed down to the bottom.Rule order switching is a thing I've only ever seen with pfBlocker moving rules to the top/bottom when creating automatic rules, but normally it only touches rules with "pfB_xy" aliases in them. So that would be weird. Also one thing you could check is the "Backup & Restore" / Config History Tab in case something is rolling back your configuration because of an error or something (or if someone/-thing commits a new config) - that should show who/what changes the config and why.
Cheers
-
@JeGr said in Rule order bug?:
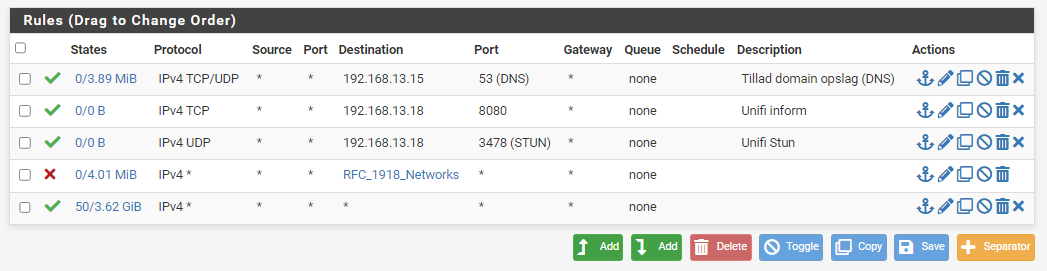
One thing we cannot see as you cropped the image that way
There is nothing else.
This is the full image, after using RFC rule instead
So i re-enabled pfblocker again, and then removed "Guest" interface from "outbound Firewall Rules" in pfblocker
,as i really only need pfblocker on wan interface - and then it seems to be staying in order.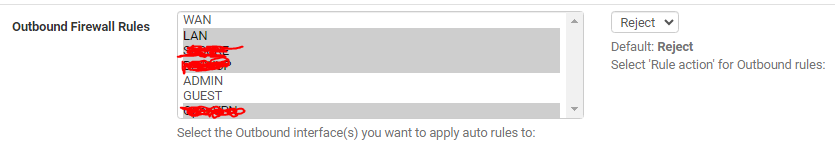
So for future refrence: pfblocker is the problem, and the solution is to remove that specific interface from "outbound firewall rules" in pfblocker :)
-
@fero1233 Did you change pfB off the default option? see:
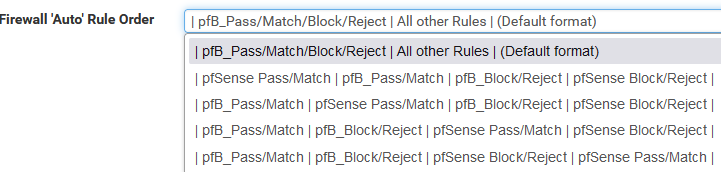
Edit: if I ever don't want the default "block on top" I create lists as Alias Native which then allows me to create my own rules however I want.
There's not a default allow any rule on networks aside from LAN.
-
@fero1233 said in Rule order bug?:
So for future refrence: pfblocker is the problem, and the solution is to remove that specific interface from "outbound firewall rules" in pfblocker :)
Or even better: Don't use automatic rules at all, as the options are quite limited with the moving around of rules.
Just set the IP Lists to "Alias Deny" or "Permit" etc. instead of "Block Deny" and just create your own rules with the pfB_xy Aliases to reject or block or allow traffic as needed. Especially when having larger or more complex rulesets, that's definetly necessary.
Cheers