'pooling' port and vLANs
-
I am not sure I am in the right place, and may be a dumb question. I will start with my setup:
Proxmox 8.1.5-2 host on HP Z240 - with add-in Intel i350-T4 card (onboard NIC disabled in BIOS)
pfSense 2.7.1 installed as VM (see image)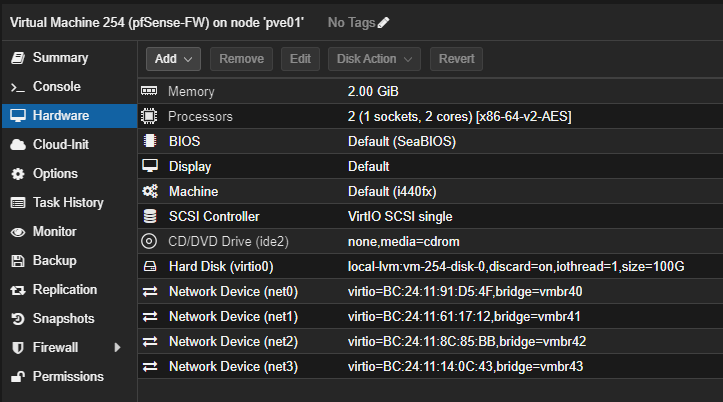
I set the NICs as Para virtualized so that the LAN port (vmbr0) will work with the WOL feature should I ever need it, and also used as the interface into the Proxmox host GUI.
Within pfSense (as follows):
net0/vmbr40 = LAN (vtnet0)
net1/vmbr41 = WAN (vtnet1)
net2/vmbr42 = OPT1 (vtnet2)
net3/vmbr43 = OPT2 (vtnet3)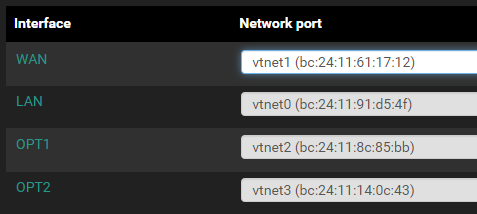
What I would like to do, since I have 2 other desktops that I have Proxmox installed on - is stack them all on top of each other - and use the OPT1 and OPT2 (as additional LAN ports - to run cable from them into the other 2 machines (as they only have the on-board NIC installed/in use).
 First question: Is this possible, and how would I "pool" them? I take it that they would all have access to the DHCP/DHCPv6 and DNS/ARP/NDP for the other items on the LAN (which gives me network through the house and to a Wireless AP (which uses the same DHCP etc.).
First question: Is this possible, and how would I "pool" them? I take it that they would all have access to the DHCP/DHCPv6 and DNS/ARP/NDP for the other items on the LAN (which gives me network through the house and to a Wireless AP (which uses the same DHCP etc.). Second question: I would like to setup a VLAN (to be used on one of these 3 PVE hosts (pfSense runs on PVE01)...so that the PVE02 (will be used for building lab machines needed for work). I would like them to be on their own IP segment (the home is 10.9.28.1/24) - but still be accessible via RDP or some other tool to remote into the VMs (most will be either Windows server or Win10/11).
Second question: I would like to setup a VLAN (to be used on one of these 3 PVE hosts (pfSense runs on PVE01)...so that the PVE02 (will be used for building lab machines needed for work). I would like them to be on their own IP segment (the home is 10.9.28.1/24) - but still be accessible via RDP or some other tool to remote into the VMs (most will be either Windows server or Win10/11). Third question: I am hoping to put them all into a PVE-Cluster (so that I can use one GUI to manage them all). Would that work? As I am thinking that the HOST port on PVE02 would need to be in 10.9.28.xxx segment, but the VMs themselves would be the VLAN (whatever IP scheme I use).
Third question: I am hoping to put them all into a PVE-Cluster (so that I can use one GUI to manage them all). Would that work? As I am thinking that the HOST port on PVE02 would need to be in 10.9.28.xxx segment, but the VMs themselves would be the VLAN (whatever IP scheme I use).I hope I made some sense - I know it has given me a 3-day headache.



-
I am having no luck - from reading the NETGATE Documentation - it sounds like I need a 'Bridge".
I am following the steps here: Creating a Bridge
and when I attempt to ADD the ports, they are not shown:

If I attempt to ENABLE them, I get the following errors:

-
Do you need to be able to filter the traffic between the LAN and those interfaces?
If not just add them the same bridge in Proxmox.
If you need to filter them and need them to be in the same subnet then, yes, you can use a bridge in pfSense.
When you create a bridge like that only one member or the bridge itself should be given an IP. You can't enable those interfaces as DHCP them selves, they should be enabled as type none. However it looks like you previously had them enabled as static IPs because the dhcp server is enabled.
Steve
-
I basically want them to act like a HUB (giving me 2 ports -- just like the LAN port). I have some 8 inch CAT6 cables that I want to plug from OPT1 and OPT2 into the NIC of 2 new ProxMox boxes (their HOST port).
I have tried everything - no setting that I try will allow me to ENABLE the ports - so that I can create a BRIDGE. I always get that pink/red warning about DHCP.

-
@bearhntr said in 'pooling' port and vLANs:
I basically want them to act like a HUB (giving me 2 ports -- just like the LAN port)
Then just add them to the same bridge in Proxmox; vmbr40. Then all three ports will be bridged there like a switch. No need to add them in pfSense at all if you don't need to filter between them.
-
Guess I will have to figure that one out.
One of them I am hoping (or was hoping) to have my LAB systems setup (for working from home) and have a vLAN (I am guessing) - so that they have their own IP Addresses which are separate from the HOME network - but still be able to access them via RDP from one of the HOME computers.
Not sure how to do that. Meaning does the Proxmox HOST need to be in the same vLAN so that all of the VMs on it are in that vLAN -- or can it be in the HOME IP Segment, but it's VMs be different?
-
-
Looks like this may have worked -- I will have to test it.
Still have the question of separate IP segments for VMs on one of the Proxmox boxes.

-
Yup all three ports on the same Linux Bridge. That's the correct way to do it if you want them to just act like a switch.
If you want a separate subnet you could use a VLAN across that. Or you could use a separate bridge in Proxmox with one or both of those ports on it.
-
Thanks very much for the confirmation and guidance.
I have changed the Proxmox bridge for 40 to include port 0, 2 and 3 and plugged a computer into port 2 - and it is acting like it would if it were plugged into the hub it was in (that as plugged into port 0 (LAN)).
Now to do some more reading on vLAN setup.

