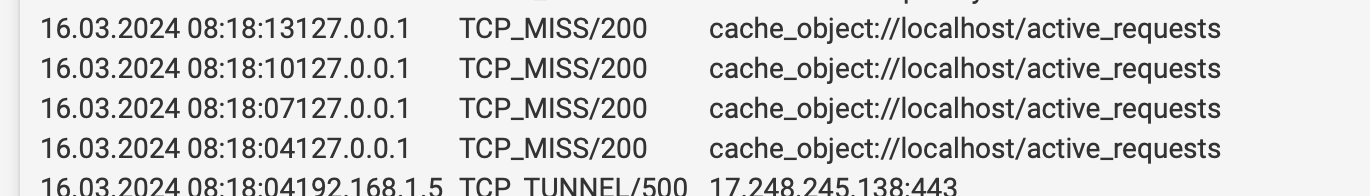
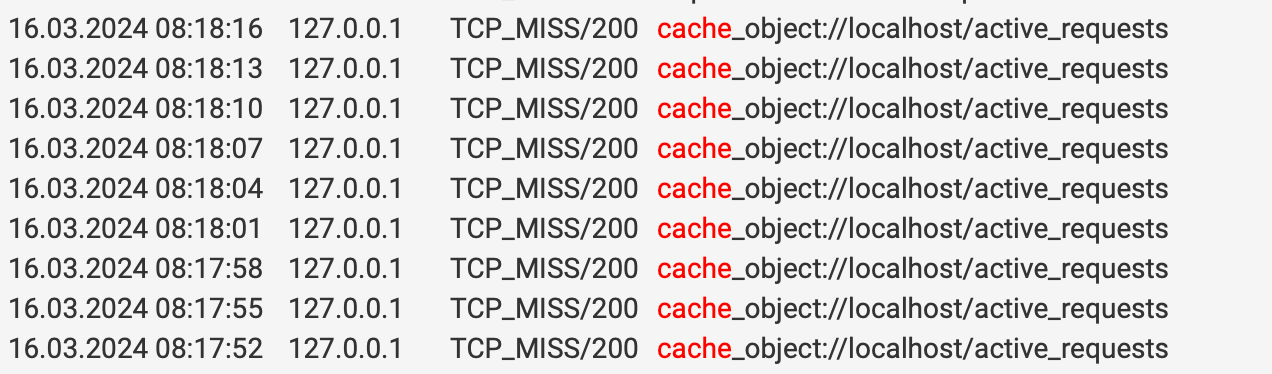
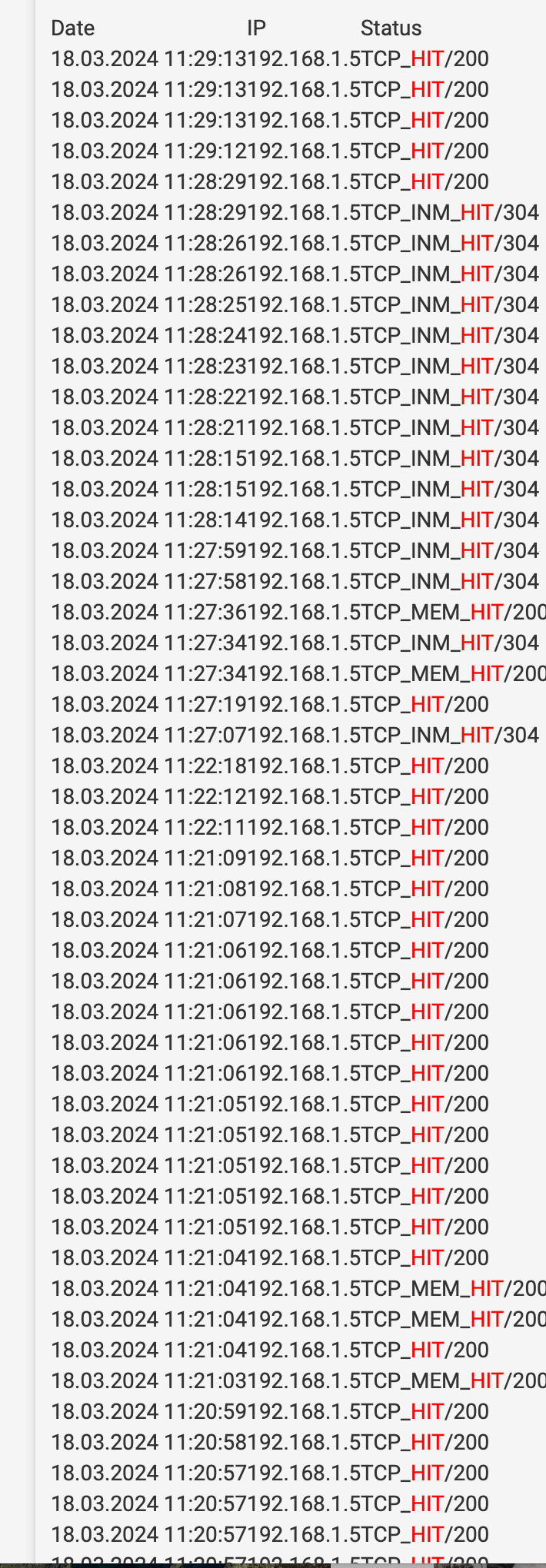
cache_object// showing miss should not cache the loopback right?
-
That is probably related to the transparent proxy.
You are forwarding connections to the Internet 80/443 to 127.0.0.1 3128, thus the proxy sees 127.0.0.1 -
@mcury I have private address set to bypass. This shows access to cache manager being a miss. That’s what is weird to me. I have the loop back inside of the do not catch nothing seems to stop it. I added the loop backs and the firewall address to the external cache manager and it seems to work better. @KOM thanks for the post from 8 years ago. I also
see a * request at times. I assumed the firewall IP and loop back were already external cache managers. @mcury I agree it’s the loopback, I got something bonked up where it is caching the cache, sounds silly caching the cache, again it shows as a miss so it is restoring the cache manager into the cache. -
@JonathanLee Are you monitoring squid with a 3rd party app ? Perhaps sarge, lightsquid or sqstat ?
Try disabling it for a moment to see if it goes away. -
@mcury light squid
 can it see that and try to cache that? Should I add a bypass in light squid?
can it see that and try to cache that? Should I add a bypass in light squid? -
@JonathanLee said in cache_object// showing miss should not cache the loopback right?:
light squid
 can it see that and try to cache that? Should I add a bypass in light squid?
can it see that and try to cache that? Should I add a bypass in light squid?I suppose lightsquid is checking cache status only.
First I would make sure it is lightsquid generating those logs, if you can, disable for a few minutes to see if those logs disappear.According to this post:
You can try this:
acl exclude dst localhost access_log none exclude -
@mcury ok it is doing this in there a way to resolve this? Bypass local host on squidguard?
-
@JonathanLee said in cache_object// showing miss should not cache the loopback right?:
Bypass local host on squidguard?
I always bypassed these networks from the proxy, perhaps you should, unfortunately there is a long time I don't use squid, so give it a shot to see how it goes.
isInNet(dnsResolve(host), "10.0.0.0", "255.0.0.0") || isInNet(dnsResolve(host), "172.16.0.0", "255.240.0.0") || isInNet(dnsResolve(host), "192.168.0.0", "255.255.0.0") || isInNet(dnsResolve(host), "127.0.0.0", "255.0.0.0") || -
@mcury thanks where are you adding this information into the WPAD? DNS entries.
-
@JonathanLee said in cache_object// showing miss should not cache the loopback right?:
@mcury thanks where are you adding this information into the WPAD? DNS entries.
I wouldn't use WPAD because I can't update the .pac file on the fly.
I used to deploy .pac file directly to the browsers, using a setting to do not cache .pac file using GPO.
So, when a new bypass was required, I would update the .pac file and ask the user to close and reopen the browser to get the newest thing.
I also used to set "do not allow the user to change proxy settings".For smartphones, I would put them in another VLAN and leave them alone, sometimes some DNS filtering only depending on the environment.
-
-
More thought this would be a better solution right outside of just not logging it?

Except http access deny at the end of the list
-
@JonathanLee To be honest, I'm not sure what is best, a lot things about squid I forgot..
I have a few .txt files here stored from years ago but that is it.. -
@mcury I think I found the solution..
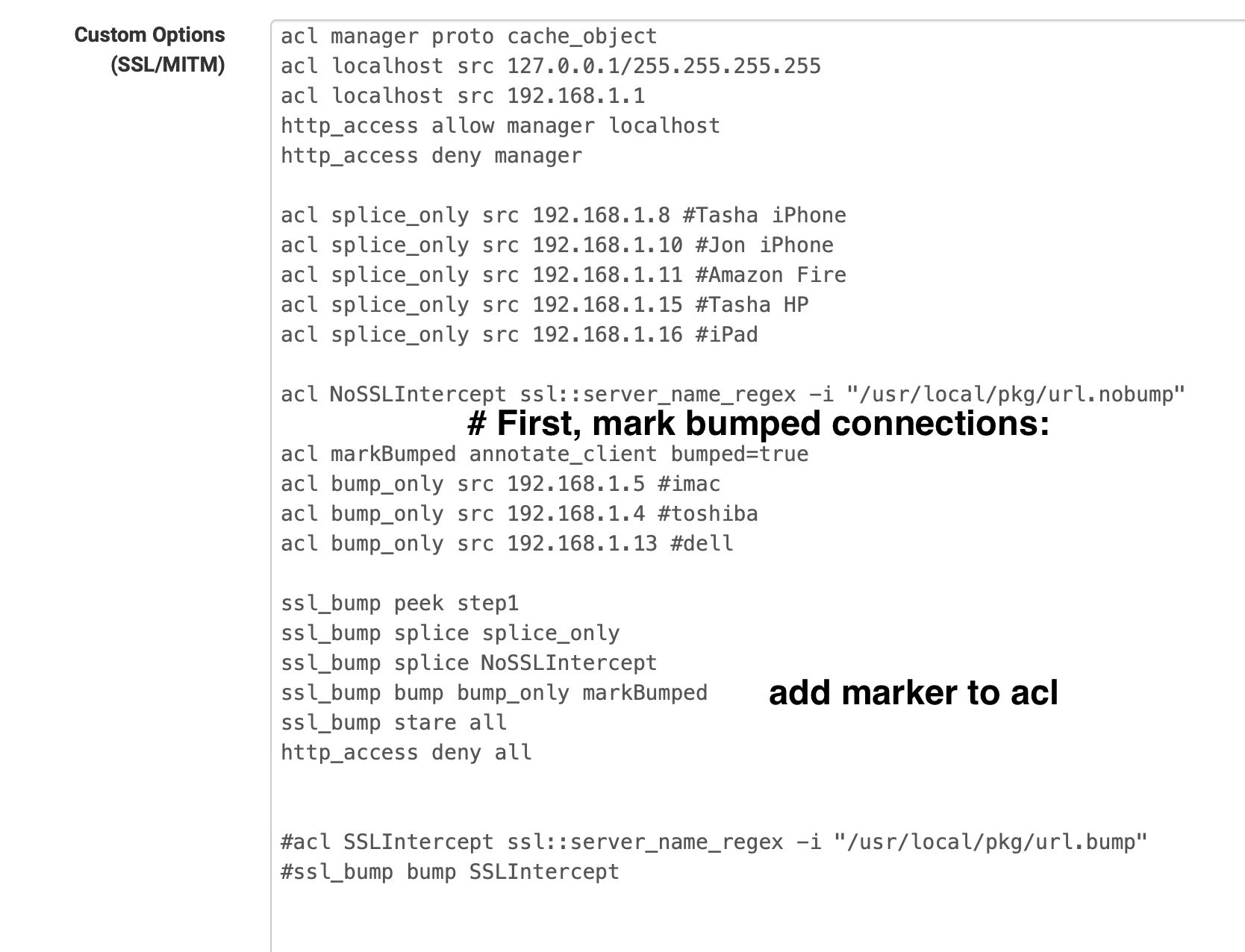
or just add loopback to splice only so it stops accessing miss_access or acl for it
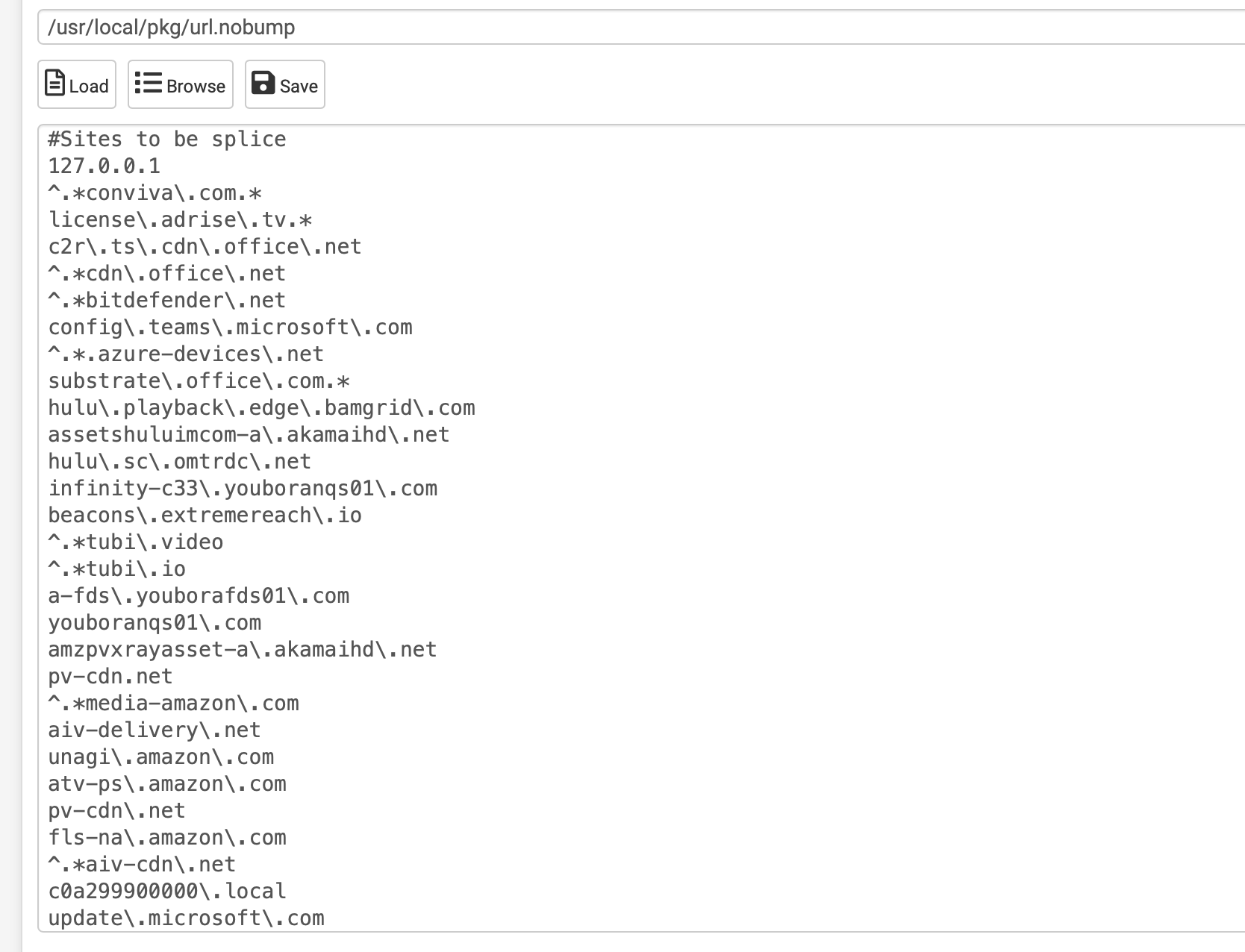
testing this

ref:
http://www.squid-cache.org/Doc/config/acl/
http://www.squid-cache.org/Doc/code/AnnotateClient_8h.dyn -
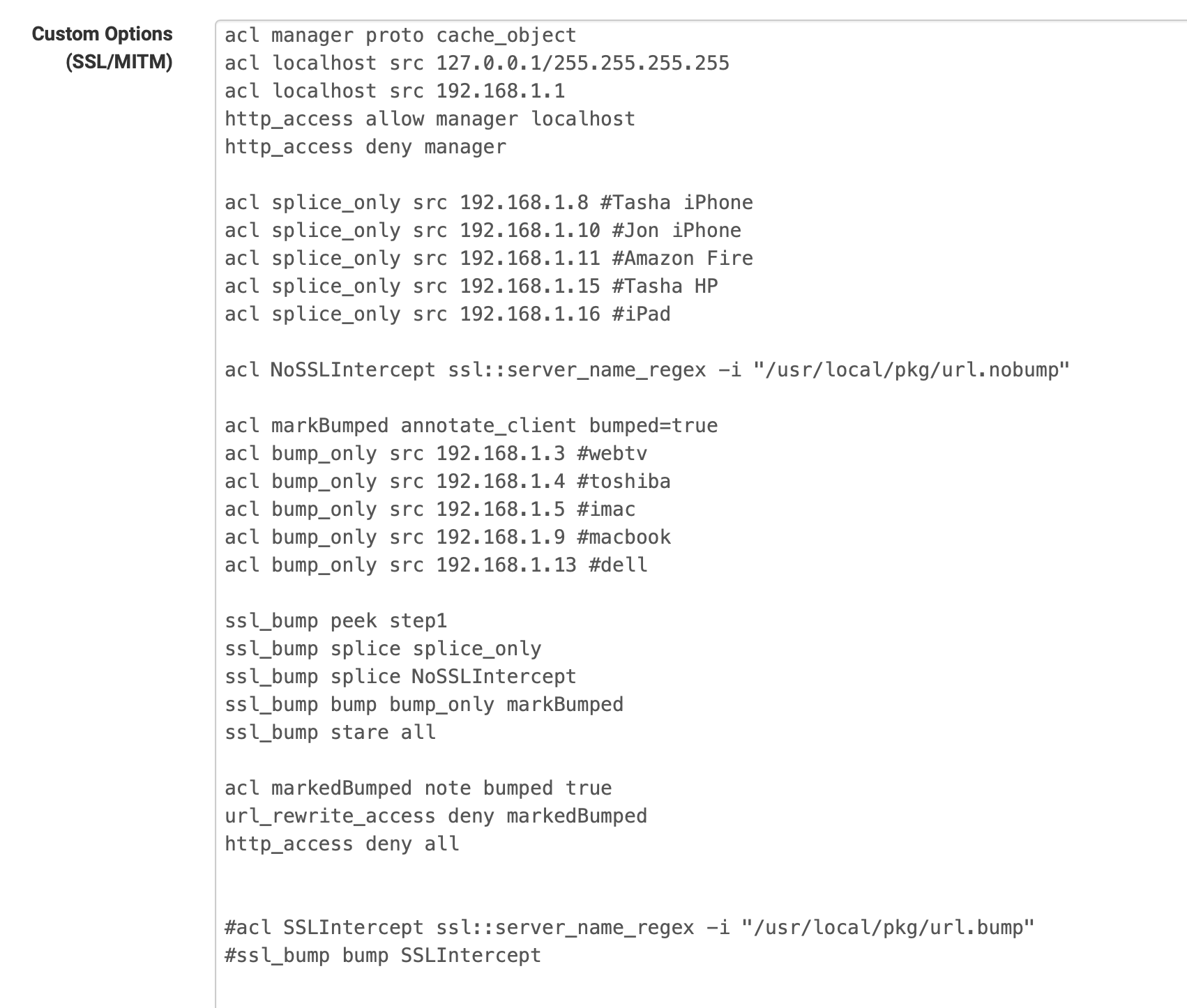
I am going to test this without use of splice the loopback. I removed it from my non bump
Per Squid Docs...
acl aclname annotate_client [-m[=delimiters]] key=value ... acl aclname annotate_client [-m[=delimiters]] key+=value ... # # Always matches. [fast] # Used for its side effect: This ACL immediately adds a # key=value annotation to the current client-to-Squid # connection. Connection annotations are propagated to the current # and all future master transactions on the annotated connection. # See the annotate_transaction ACL for details. # # For example, the following configuration avoids rewriting URLs # of transactions bumped by SslBump: # # # First, mark bumped connections: # acl markBumped annotate_client bumped=true # ssl_bump peek acl1 # ssl_bump stare acl2 # ssl_bump bump acl3 markBumped # ssl_bump splice all # # # Second, do not send marked transactions to the redirector: # acl markedBumped note bumped true # url_rewrite_access deny markedBumped # # # Note that the following would not have worked because acl3 alone # # does not determine whether the connection is going to be bumped: # url_rewrite_access deny acl3 # Wrong! -
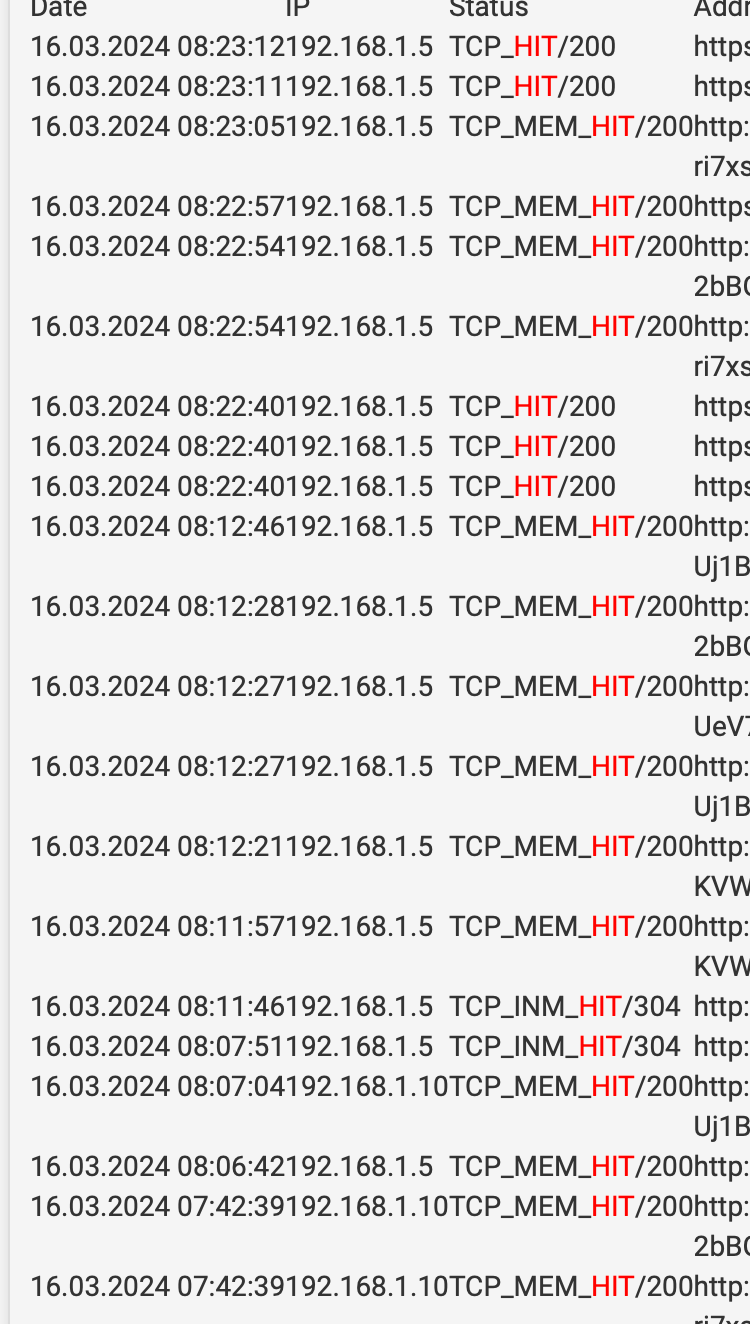
Now I got some improved hits!!! WOW
-
@JonathanLee ow, good to hear that