Better way to investigate alerts
-
hello everyone,
Looking to get some feedback on the best way of addressing a Suricata alert.Background. I have Suricata enabled on a Server VLAN. Typically another vlan called PublicApps , makes calls to the server vlan.
The PublicApps is where my servers that are public internet facing sit and are reachable via a reverse proxy sitting in another vlan called DMZFor those curious
My reverse proxy sits in dmz 192.168.2.x
Public Apps sits in 192.168.15.x
Server vlan sits in 192.168.3.xTight rules govern cross traffic between dmz and public and between public and server vlan.
Anyways, back to my question. I received the following email alert today
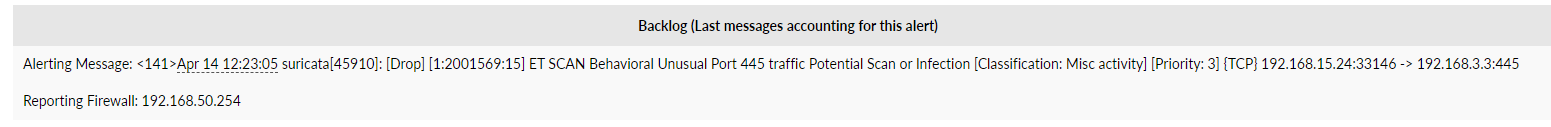
Im not worried as I know the servers involved and there is port 445 open to allow this but Suricata was triggered.
What are some of the things I should do to better troubleshoot? The things I do is check my wazuh dashboard during the alert times, zabbix for anything unusual on the system.Anything I should do for better viability?
I welcome all the feedback to address this alert better.
Side note: I do have Wazuh running and nothing was triggered there so I feel relatively comfortable that the alert is benign.
edit:
For those curious the Wazuh alert below occurred during the suricata triggers