Snort Package 4.0 -- Inline IPS Mode Introduction and Configuration Instructions
-
@tsmalmbe said in Snort Package 4.0 -- Inline IPS Mode Introduction and Configuration Instructions:
A couple more.
QUESTION: "Packets matching DROP rules are simply discarded (dropped) and not passed to the host network stack." -> Does this imply, that whenever Snort kicks in and blocks I will NOT see these blockings in my firewall logs anymore?
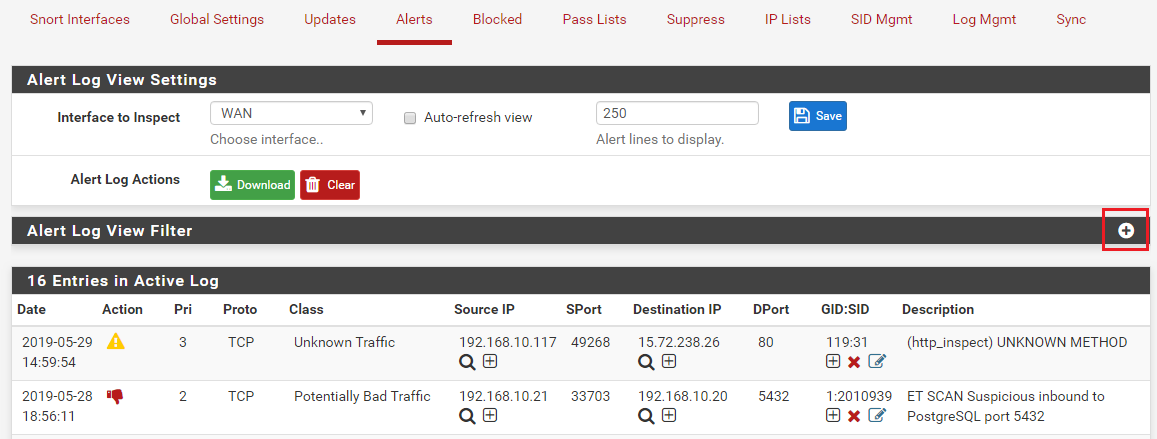
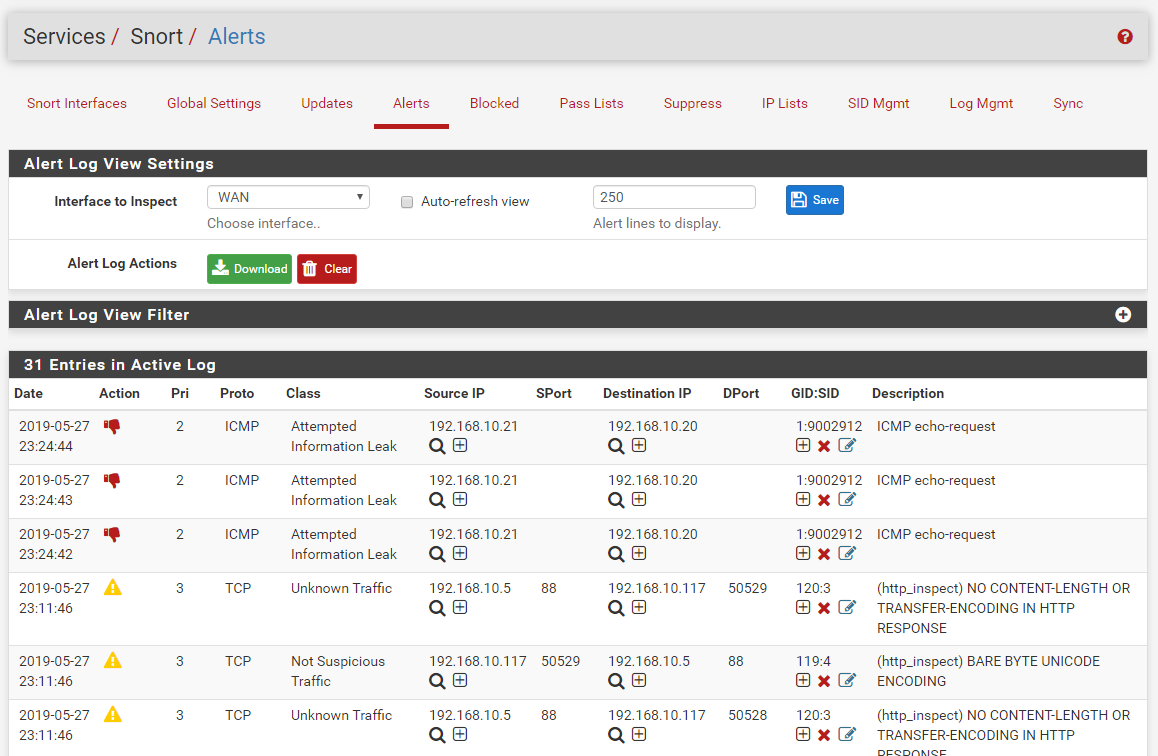
For traffic inbound on an interface, Snort sees the traffic and acts on it first, before the firewall layer. So if using Inline IPS Mode, which "blocks" by simply not forwarding a packet on to the rest of the kernel, should Snort drop a packet, then the firewall never sees it and thus won't block it nor log anything about it. You would need to look at the Snort ALERT tab which shows Snort's logs to find the dropped traffic. The log entry for dropped traffic will be printed in red text.
QUESTION. In Inline mode, will I see a difference in the Snort logs between "just alerting" and "blocking" - referring to the Snort-rules by Talos which contain this information. The others (Emerging and Appid) work as usual I assume, if an alert is triggered, it will be blocked (even in Inline mode)?
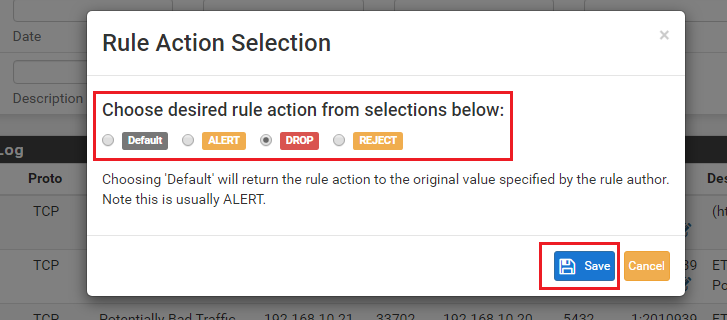
No, that is not how it works at all. With Inline IPS Mode, there are only three possible rule actions: ALERT, DROP or REJECT. The only two of those actions that result in traffic being blocked are DROP and REJECT. ALERT never, ever blocks traffic when using Inline IPS Mode. The difference between DROP and REJECT is that with REJECT the sending host (the one being blocked) is sent either a TCP RST packet (if using TCP), or an icmp-unreachable (if using another protocol). The tells the sending host its connection attempt was received but refused, so no use trying again. A DROP action simply discards the packet. It logs what it did in the log file the ALERTS tab reads and displays, but the sender of the dropped packet never knows what happened. Usually that means the sender will try a few more times before giving up and showing the user at the other end of the connection some type of error.
-
When selecting the Policy option I was expecting the drop-down onthe Rules tab to contain the Categories - but it only contains the item IPS Policy - Security. This was a bit confusing and actually one of my questions. The question was really badly written, sorry for that. The page - with 17000+ rules - takes ages to load, but I guess that is not something easily fixable.
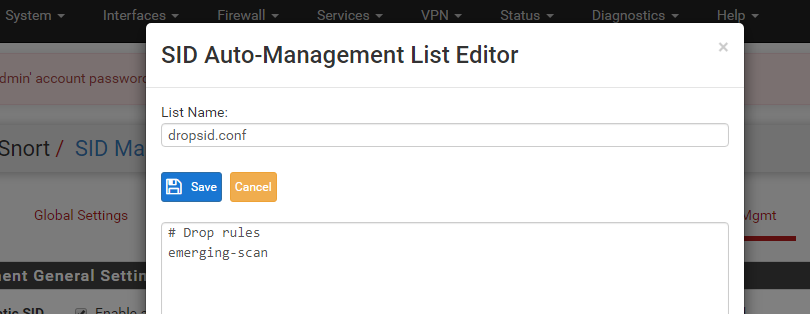
The other question was simply this (and I present it as a statement now, not a question). Let's assume a category in Emerging. In legacy mode I only need a category to alert, and that will essentially block. When turning on inline mode, the rules in the category will be alert only so for me to get the same functionality as in legacy mode of having an Emerging category blocking, I need to add a file in drop SID list containing "emerging_". Then my chosen Emerging categories will block also in inline mode.
Please explain to me why I would use the modifysid to enable ALL wordpress rules, would that not be the job of enablesid with a (for me yet unknown) regular expression? I am not trying to modify the rule, just enabling it based on free text in the description (if I understood this correctly).
I appreciate your patience. I try to write my questions and thoughts in a way that will server future readers.
-
@tsmalmbe said in Snort Package 4.0 -- Inline IPS Mode Introduction and Configuration Instructions:
When selecting the Policy option I was expecting the drop-down onthe Rules tab to contain the Categories - but it only contains the item IPS Policy - Security. This was a bit confusing and actually one of my questions. The question was really badly written, sorry for that. The page - with 17000+ rules - takes ages to load, but I guess that is not something easily fixable.
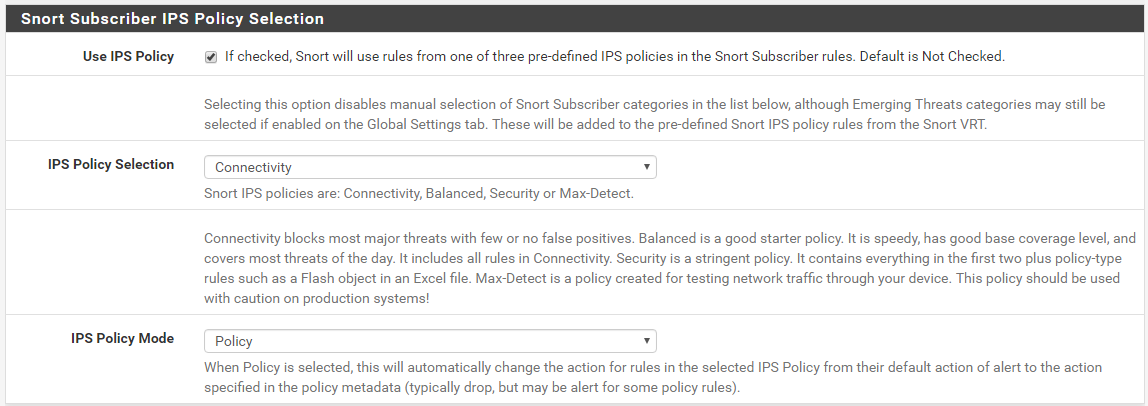
When you choose to use an IPS Policy, the GUI code on the CATEGORIES tab blocks further choice of other Snort rules as it is presumed you are giving that responsibility over to the policy. Thus the RULES tab sees only the collection of rules encompassed by the selected policy. Yes, through a fluke in the GUI code, you can still use SID MGMT to "force" additional Snort rules into the final product that are not part of the chosen Snort IPS Policy. If you want to see the actual rules in use on the interface after all the processing logic is done, in the Category drop-down is an entry called "Active Rules" - if I remember the name correctly. That choice loads all of the enabled rules that will be used on the interface. But it will be even larger as the Snort built-in rules will also be included in the list, so it will take several seconds or even minutes to fully load and render the page.
The other question was simply this (and I present it as a statement now, not a question). Let's assume a category in Emerging. In legacy mode I only need a category to alert, and that will essentially block. When turning on inline mode, the rules in the category will be alert only so for me to get the same functionality as in legacy mode of having an Emerging category blocking, I need to add a file in drop SID list containing "emerging_". Then my chosen Emerging categories will block also in inline mode.
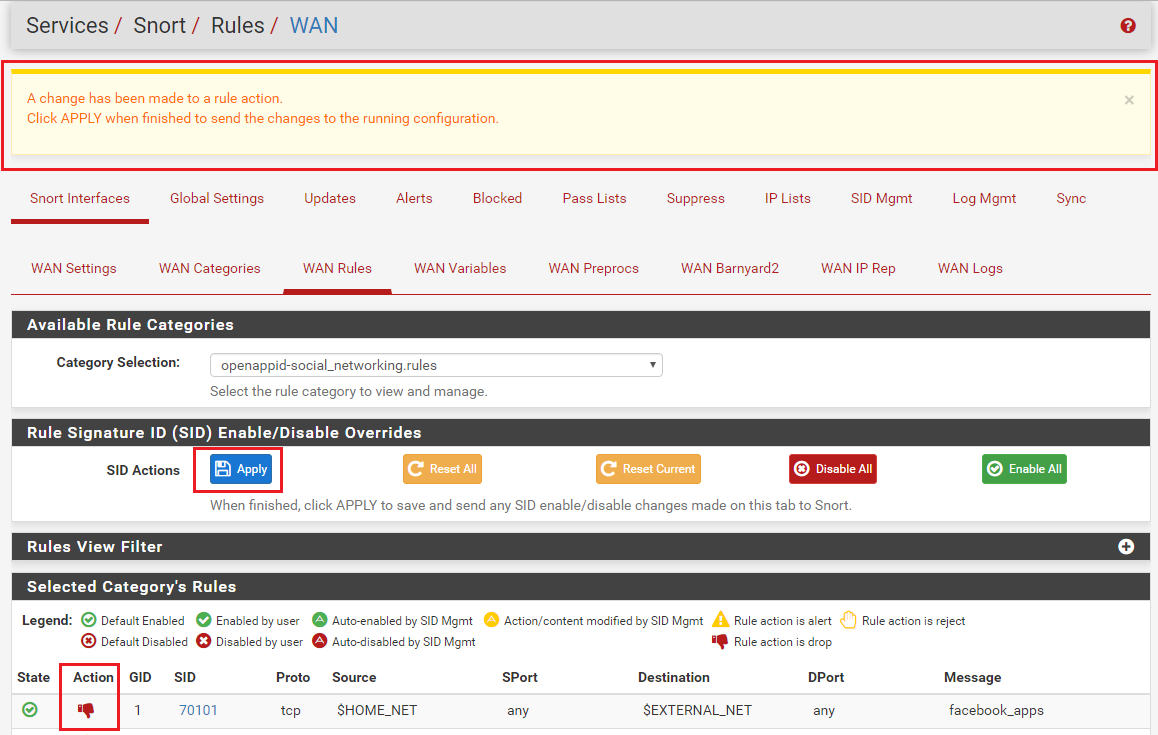
True, but literally what you are doing is changing the action for the rules matching the criteria in your SID MGMT file from ALERT to DROP. I prefer to always use the term "drop" when speaking of Inline IPS Mode to clearly distinguish it from Legacy Mode. That's exactly the same thing the GUI code does for the rules that match the chosen IPS Policy. It simply searches through all of the snort rules files and finds every GID:SID that has a matching IPS Policy tag (i.e., a tag matching the chosen policy). It then changes the action of matching rules to the value prescribed in the IPS Policy metadata tag for each rule, and then adds the rule to its list of "enabled" rules to be loaded by Snort.
Please explain to me why I would use the modifysid to enable ALL wordpress rules, would that not be the job of enablesid with a (for me yet unknown) regular expression? I am not trying to modify the rule, just enabling it based on free text in the description (if I understood this correctly).
Perhaps I misunderstood your question. I thought you wanted to find rules that had a particular keyword in their signature and change their action, because I don't recall any rules category file called "wordpress". So for example, if I want to find all rules whose signature MSG field contained something about "wordpress", then only the modifysid logic can do that. It is the only SID MGMT "function" that looks at the full text of each rule's signature. The other SID MGMT "functions" only look for one of two things: (1) the category file name, such as emerging-scan; or (2) the GID:SID. That's it. The enablesid, disablesid, dropsid and rejectsid logic only looks for those two fields. It is not looking at the MSG field in a rule. Only modifysid looks into the MSG field of a rule to search for matches.
I appreciate your patience. I try to write my questions and thoughts in a way that will server future readers.
Some of your questions lead me to think perhaps you have not actually studied the raw text of the IPS Policy rules. If you have not actually seen the metadata tags I've been discussing, then go to the RULES tab and select your IPS Policy in the Category drop-down. After the rules finish loading on the page, click on the GID:SID value for a rule, or double-click the row, to open the raw text in a pop-up modal dialog. Read the entire text of the rule signature. Look for the IPS Policy metadata tags. You will see them listed. And for many of the rules, you will see multiple tags associating the rule to more than one policy. And depending on the particular rule you choose to view, you may also see different rule actions for the different policy matches. So when you "select" an IPS Policy, all that really does is tell the GUI code to load every single Snort rule into a gigantic list in memory and then search for those policy metadata tags. It selects rules from the list that have an IPS Policy metadata tag matching the policy you specified. Then also, as it copies that rule over to the "enabled list" in memory, it changes the rule's action keyword to match what is suggested by the IPS Policy metadata tag. And not every single Snort rule has an IPS Policy metadata tag in it. Most do, but some do not. So those rules would never get selected as part of a policy.
-
S SteveITS referenced this topic on
-
S SteveITS referenced this topic on
-
@bmeeks , thanks for your detailed instructions. This is what I have done:
a) I have pfsense 2.6
b) snort 4.1.6 on my LAN interface
c) Applied "Inline Policy" to block offenders
d) I used "Connectivity" category
d) My connection to my home devices via Anydesk is blocked as expectedQuestions:
-
I want to disable the rule that blocked/dropped/rejected the connection but I can't find any such rule in the alert logs via Alert Log View Filter. How can I find the rule that's blocking my connection to Anydesk?
-
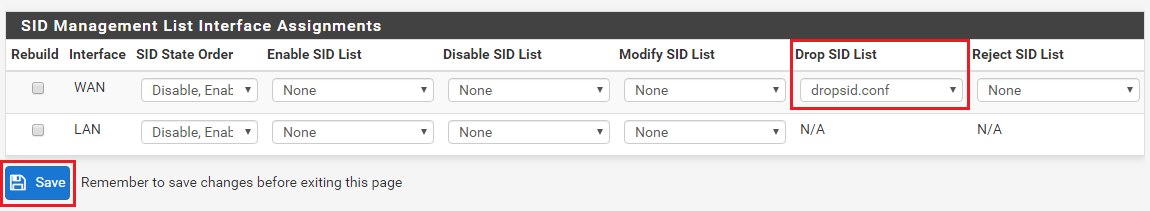
If I do find such rule, I believe I should be doing the following steps in SID management
a) Create a dropSID.conf
b) Add in the the pair of GEN_ID:SID in that file
c) Place in under the "Disable SID" List
d) Rebuild the LAN
Thanks !
-
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
@bmeeks Hi, thanks for a great explanation and for taking the time to answer everyone's questions.
Do they still recommend enabling SNORT on the LAN/VLAN interface? To clarify, you mentioned snort working before the pfSense firewall? Therefore there's no need to enable on the WAN?
And, nowadays, if we choose to use SID, do we have to include .rules in the SID Auto-Management List Editor when listing the rules?
Also, could you please discuss Choosing the Networks Snort Should Inspect and Whitelist under the SNORT INTERFACES, WAN or LAN SETTINGS tab? What that does and when and how to configure?
Thanks again!
Terry -
@terry-c said in Snort Package 4.0 -- Inline IPS Mode Introduction and Configuration Instructions:
@bmeeks Hi, thanks for a great explanation and for taking the time to answer everyone's questions.
Do they still recommend enabling SNORT on the LAN/VLAN interface? To clarify, you mentioned snort working before the pfSense firewall? Therefore there's no need to enable on the WAN?
Yes, I still suggest putting your Snort (or Suricata) instances inside the firewall perimeter on your LAN and other internal interfaces for most setups. Snort and Suricata receive network packets directly from the NIC driver BEFORE they hit the
pfpacket filter firewall engine. This is true no matter which interface (WAN or LAN) the IDS/IPS instance runs on. So, when talking about the WAN, there is very little benefit to putting Snort or Suricata there as it will be busy intercepting and analyzing traffic that the next step of packet processing- thepfpacket filter- is probably going to drop via a default rule anyway. That would mean burning CPU cycles for zero benefit.And, nowadays, if we choose to use SID, do we have to include .rules in the SID Auto-Management List Editor when listing the rules?
I don't fully understand this question. You seem to be mixing up two quite different concepts here. SID (Signature ID) is the unique serial number identifier for each rule used by an IDS/IPS. The folks who write rules tend to group them into logically related categories by virtue of including those SIDs in a common *.rules file. As an example, the Emerging-Scan.rules file contains a collection of rule SIDs that work to detect various types of scans. How you choose to use a collection of SIDs or groups of *.rules files is determined by what you want to accomplish. Using SIDs by themselves lets you be more selective than using the rules file category name would be.
Also, could you please discuss Choosing the Networks Snort Should Inspect and Whitelist under the SNORT INTERFACES, WAN or LAN SETTINGS tab? What that does and when and how to configure?
Short answer here is DO NOT touch this or change it from the default unless you fully understand how it works and what it is for.
There is information about HOME_NET and EXTERNAL_NET to be found on Google. Those terms are used in all variations of the Snort and Suricata packages whether used on pfSense or not. The simplest explanation is the HOME_NET variable contains all the interface IP and subnet addresses that you want to protect. EXTERNAL_NET contains everything NOT defined as being part of HOME_NET (usually). This is most commonly done by defining EXTERNAL_NET this way in the configuration file:
$EXTERNAL_NET = !$HOME_NETwhere the leading exclamation point is the logical NOT operator.
Getting these two variables properly set up is critical because many of the rules use $HOME_NET and $EXTERNAL_NET as conditionals for determining if a rule should trigger. Examine some of the text of the rules and you will see how those variables are used. If not correctly set up, then rules will not trigger as expected because that network conditional will not match what the rule is written to look for.
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
S SteveITS referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
@bmeeks thanks alot for all the replies these are wonderfull and give perfect explainations to all questions. i have spent my half day reading and experimenting with them to understand these things.
I am maintaining cisco FTD based environment and have got few questions.
1: It seems that snort is processed first before pf firewall so wont it be good to have the firewalls rules evaluated first as they are small compared to ips rules. just like ftd does i.e. lina engine which is the asa acts first and then the ips acts.
2: you mentioned that not all snort rules have the ips policy meta data information so wont we miss if using one of the ips template ? as non of the ips template will have those rules lacking metadata enabled ?
3: Where can i see such rules that do not have the policy meta data tag ?
4: On the interface under the Rules Tab, Category selection "IPS Policy- Security" it lists a blob of all rules. cant it show them further categorized based on various apps that its protecting ? like in cisco ftd it shows them in categories ?
I could have opened a new thread but this is such a wonderfull detailed thread and serving as a good reference that i hope anweres to these questions will help others as well.
A million thanks
-
@Snailkhan said in Snort Package 4.0 -- Inline IPS Mode Introduction and Configuration Instructions:
@bmeeks thanks alot for all the replies these are wonderfull and give perfect explainations to all questions. i have spent my half day reading and experimenting with them to understand these things.
I am maintaining cisco FTD based environment and have got few questions.
1: It seems that snort is processed first before pf firewall so wont it be good to have the firewalls rules evaluated first as they are small compared to ips rules. just like ftd does i.e. lina engine which is the asa acts first and then the ips acts.
This is not possible because of the way the network stack is plumbed in FreeBSD. This is why I now recommend users put their IDS/IPS instances on internal interfaces such as the LAN. Otherwise, you waste CPU resources scanning inbound WAN traffic that is most likely just going to be dropped anyway by the default DENY rules in place on the WAN interface.
2: you mentioned that not all snort rules have the ips policy meta data information so wont we miss if using one of the ips template ? as non of the ips template will have those rules lacking metadata enabled ?
Not Snort VRT rules -- rather Emerging Threats and any other rules not produced by the Snort Vulnerability Research Team (VRT). Most all rules produced by the Snort VRT include IPS policy metadata. It's only third-party rules such as ET and others that lack IPS policy metadata. But there may also be a handful of Snort VRT rules where the team chose not to add IPS policy tag metadata. Why they do or do not for a particular rule is question that would have to be submitted to them. There is no way within the GUI code to "find" these particular rules.
But when you choose to utilize an IPS Policy, you are trusting the judgement of the Snort VRT to tag what is really relevant to the chosen policy. So, the fact that some Snort rules might be omitted is okay when viewed in that context.
3: Where can i see such rules that do not have the policy meta data tag ?
Answered above. If the rule is not from the Snort VRT package (meaning Registered User or Subscriber), then it lacks IPS policy metadata.
4: On the interface under the Rules Tab, Category selection "IPS Policy- Security" it lists a blob of all rules. cant it show them further categorized based on various apps that its protecting ? like in cisco ftd it shows them in categories ?
To keep the GUI code simple and manageable, it simply filters by the chosen IPS policy data and displays all the rules matching that policy. It attempts no further breakdown.
I could have opened a new thread but this is such a wonderfull detailed thread and serving as a good reference that i hope anweres to these questions will help others as well.
A million thanks
-
@bmeeks Again a lot of thanks for the prompt response.
Coming from Cisco FTD end I have couple of doubts left to be confirmed.
In cisco ftd world we create an access control rule and then attach specifc ips policy which can be either the default template (security,connectivity or max detection etc) or we can create one out of above ones .. in either case we are able to see all the rules whether the ips policy has it set to drop,alert or ignore.. apart from trusting the Snort VRT team can we see in pfsense snort version as cisco offers there all rules ?Also in pfsense we can use only one policy for entire interface (source based) while its good and simple but can we use different policies for different source destination pairs ?
I will greatly appreciate any reading material related to what benefits one style of implementation offers over the other. ie. one ips policy for all traffic from lan vs customized policy for each source destination pair.
Regards
-
@Snailkhan:
It is not possible in pfSense to tie IDS/IPS rules or policies to thepffirewall engine. Thus it is impossible to tie IDS/IPS rules to IP source or destination pairs as evaluated by the firewall engine. That's just not how pfSense is designed. If you need this level of granularity, then pfSense is not the product for you. The best you could do is write your own custom IDS/IPS rules where you customize the Source/Destination fields of each IDS/IPS rule. I seriously doubt you want to get into that level of maintainence.Snort is an add-on volunteer-maintained package for pfSense. It is not baked into the operating system nor into the design of the firewall. Therefore its capabilities will be nowhere near as flexible as say a customized Cisco hardware/software solution might be.
Later Edit: but compare the price you pay for pfSense and its Snort package to what the Cisco solution costs you
 . Many times compromises are necessary when taking advantage of the "free" option.
. Many times compromises are necessary when taking advantage of the "free" option. -
S SteveITS referenced this topic on
-
S SteveITS referenced this topic on