Open ports through OPEN VPN
-
Hello all,
I have a PFsense firewall using openVPN client to connect out to my vpn provider, I have got the setup working where I can browse out through OpenVPN and do everything like being on a normal VPN connection, and to check I am actually going out through the VPN a speed test shows where I can connecting from, so 100% happy with that..
I have a static IP and port forwarding through my VPN provider, which I know works, tested using a windows machine running the VPN client and I can get to the machine running a web server, so 100% happy that so far the VPN setup is working... it allows port 80 inbound
Now my lack of knowledge is 100% to blame for this. I want to have pfsense pass incoming requests on certain ports to go to their respective devices. sounds simple I thought...
I set up a NAT with OpenVPN as the incoming port (instead of WAN) pushed port 80 to my client ip address, allowed it to create the firewall rule, it all looks good, but I can never get to the web site on port 80 from my static IPaddress, from the internet
I am guessing that somewhere the outbound traffic gets lost, my web server has its default gateway set to the Lan port of PFsense, and I can browse to the internet from that device.
so I am a bit stuck as to why I cant get the web page served up through PFsense out through my openVPN connection
as the openvpn is a client I set up the interface as an assignment and applied the same rules. but nothing, I am starting with port 80 and a web server as I thought that would be easiest to test out
So to sum up above:
I have openVPN (pure VPN) which connects out and I can also get back in if I am just using the VPN client, so I know the VPN side of it all works fine.I have openvpn (openvpn client) set up and working on pfsense, goes out to the internet fine and speed test shows where my vpn is going out, so thats good too.
Now I think I need to add my client port as an assignment, but what do I need to configure to is inbound and outbound.. or is that not it
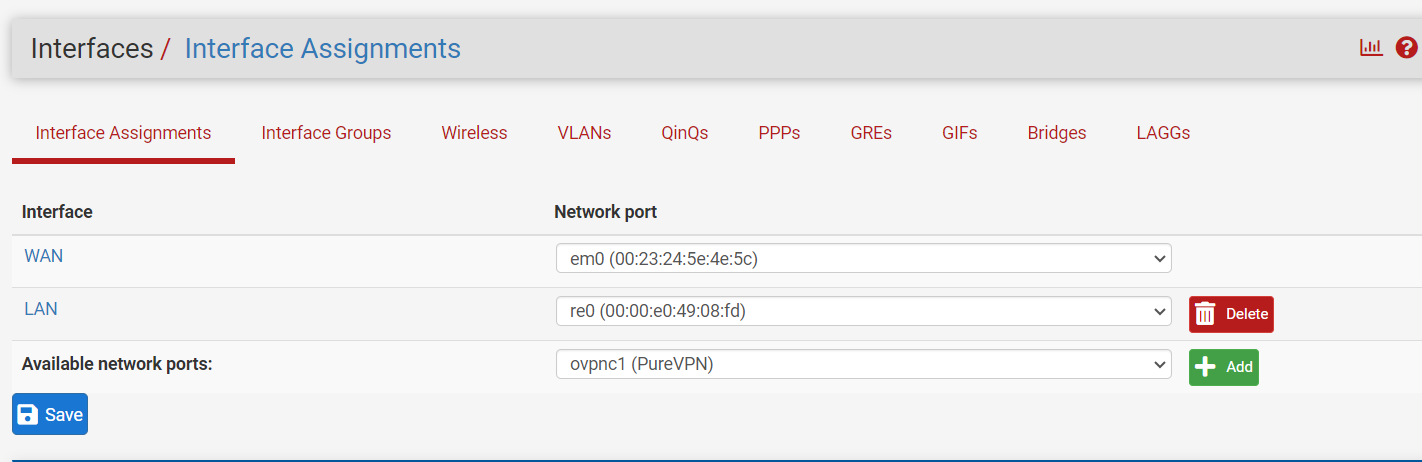
this allows my outbound traffic, but do I need to set up same for the openvpn (client) (pureVPN) network port
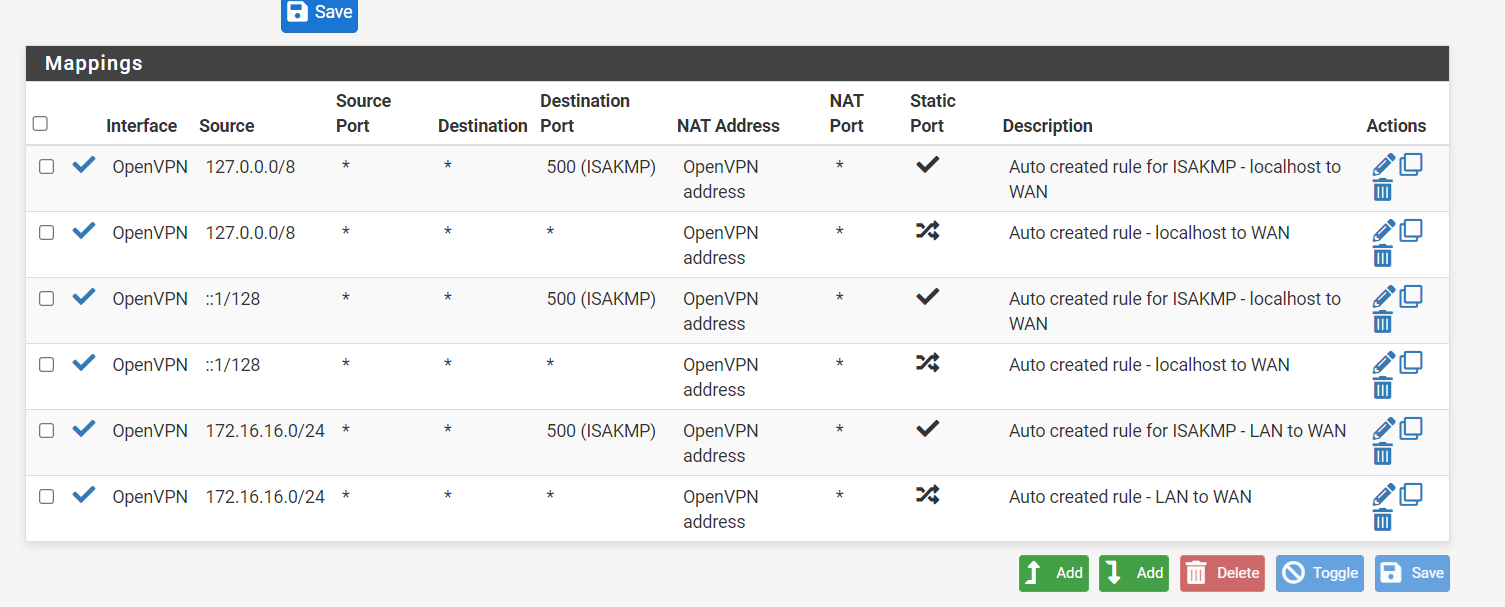
Some what confused here now...
Also after applying changes does the firewall need rebooting, as I removed some changes I made and nothing worked until a reboot..any help really appreciated, want to start with my webserver and then once I understand how this works, open ports up to my other equipment
thanks
Cliff
-
@Cliffb said in Open ports through OPEN VPN:
as the openvpn is a client I set up the interface as an assignment and applied the same rules.
The screenshot shows the ovpnc unassigned, however.
Yes, you have to do this. Enable the interface and state a friendly name. Don't call it OpenVPN, this exists already.
Then edit the NAT port forwarding rule and change the interface to the client interface, you've created before. Ensure that filter rule association is enabled.
Then go to the OpenVPN tab and remove or disable all pass rules.
-
Right, I'll give that ago again and report back, wont be until later today. I did assign the open vpn client and tried to set the rules but got nothing, but I'll give it another crack
thanks
-
Still not getting it, I know its my poor understanding, but here to learn this
ok I enabled the open vpn client interface,
set up a NAT to 172.16.16.16 which is running the web server
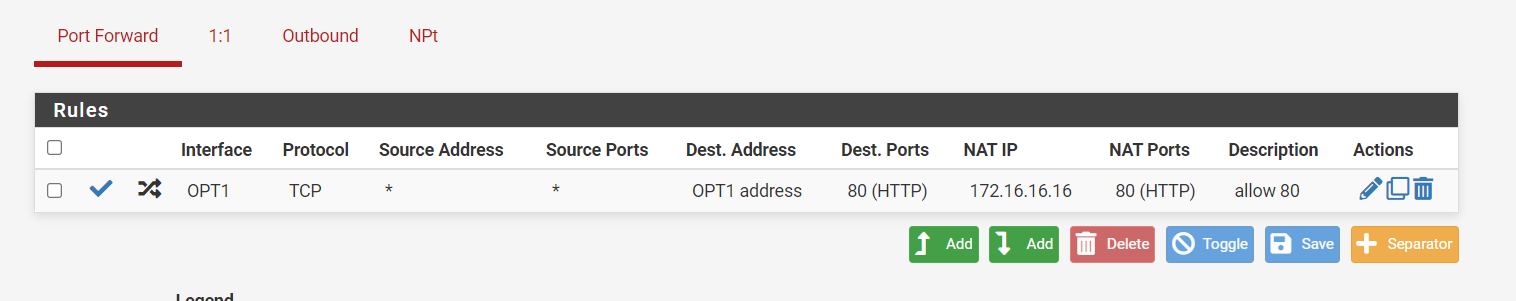
These are the outbound rules
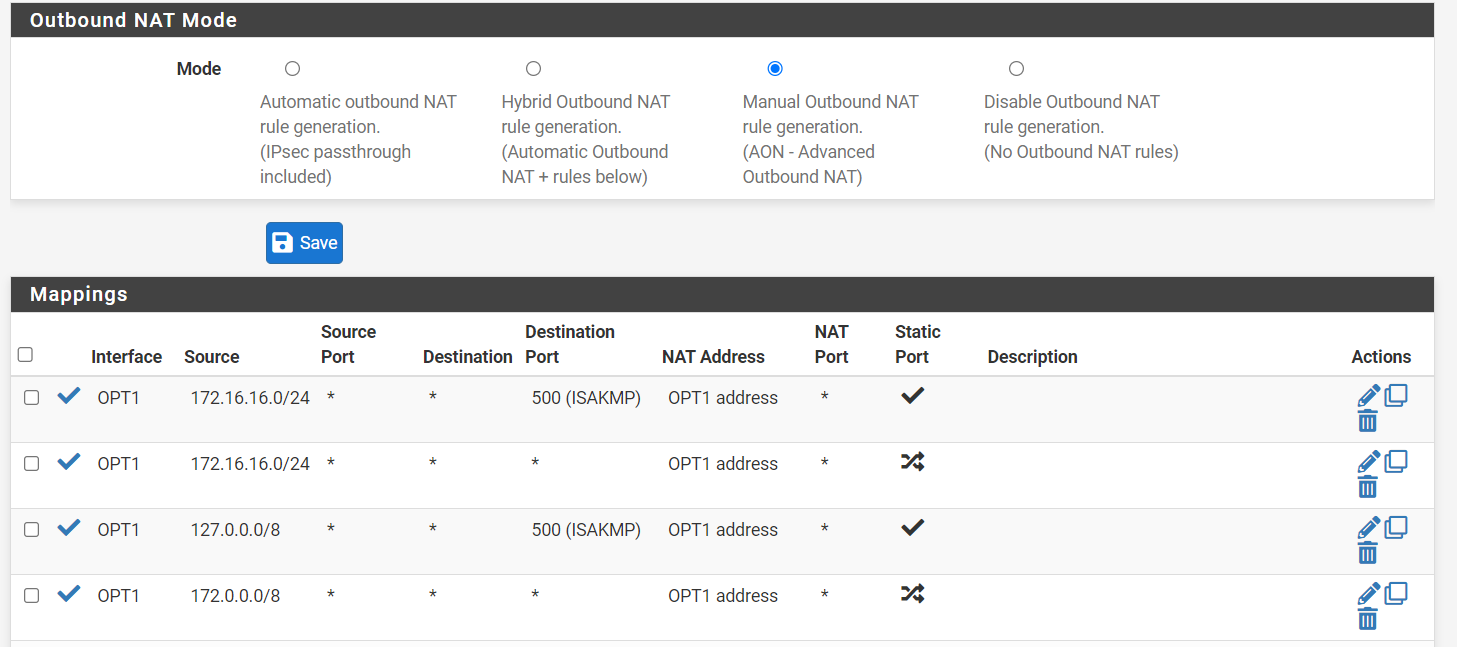
the only firewall rule I have is this one apart from the default LAN ones
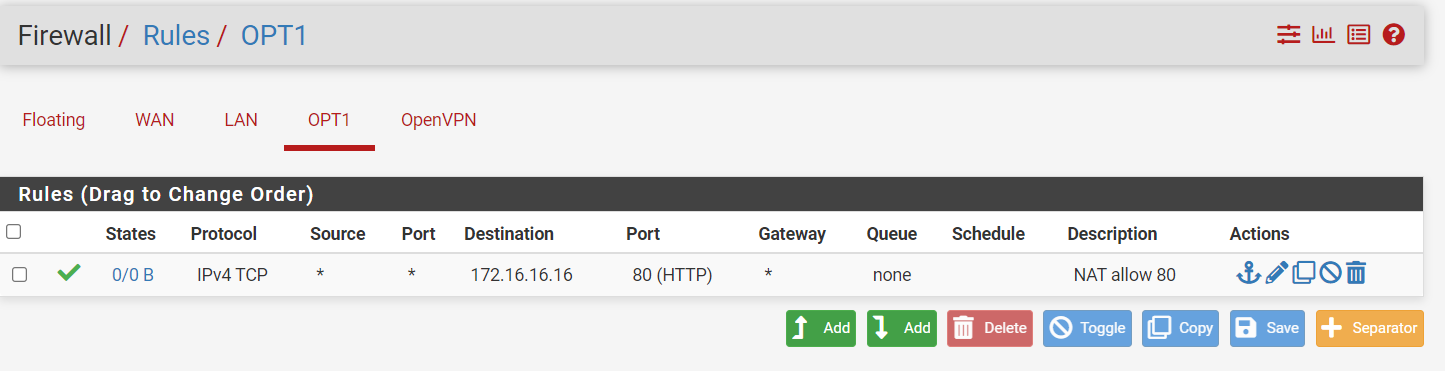
Do I need an outbound rule. the more I look the more confused I get
input greatly appreciated
Cliff
-
@Cliffb
You only need to configure Outbound NAT if you intend to make outbound connection over this VPN. If not you can leave the outbound NAT in automatic mode.
The manual mode is not needed in any case. Rather use hybrid mode.Please show the OpenVPN rules tab.
-
This is the open VPN rules tab
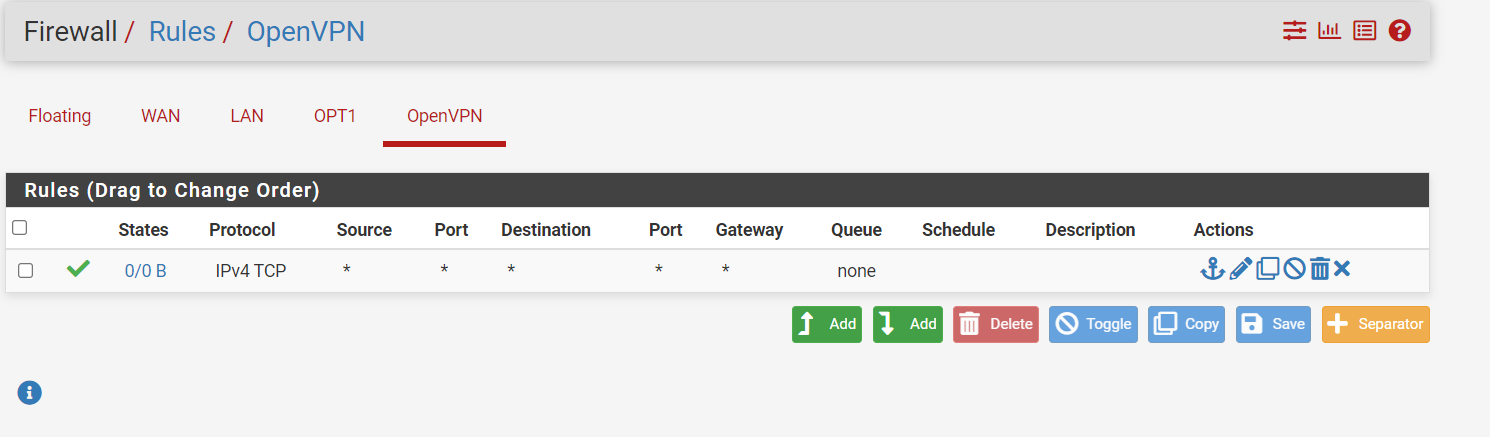
are you saying this should be set to Hybrid, I did try that but I am still getting nothing in to my web server
-
@Cliffb said in Open ports through OPEN VPN:
This is the open VPN rules tab
So why didn't you remove the pass rule as I suggested?
are you saying this should be set to Hybrid
Hybrid mode is suitable for sure. With this pfSense has enabled the automatic rules and manual rules as well.
-
Hi
I had removed the static rule but it made no difference.
but I will remove again and set to hybrid and try again, thanks for your patience
Cliff
-
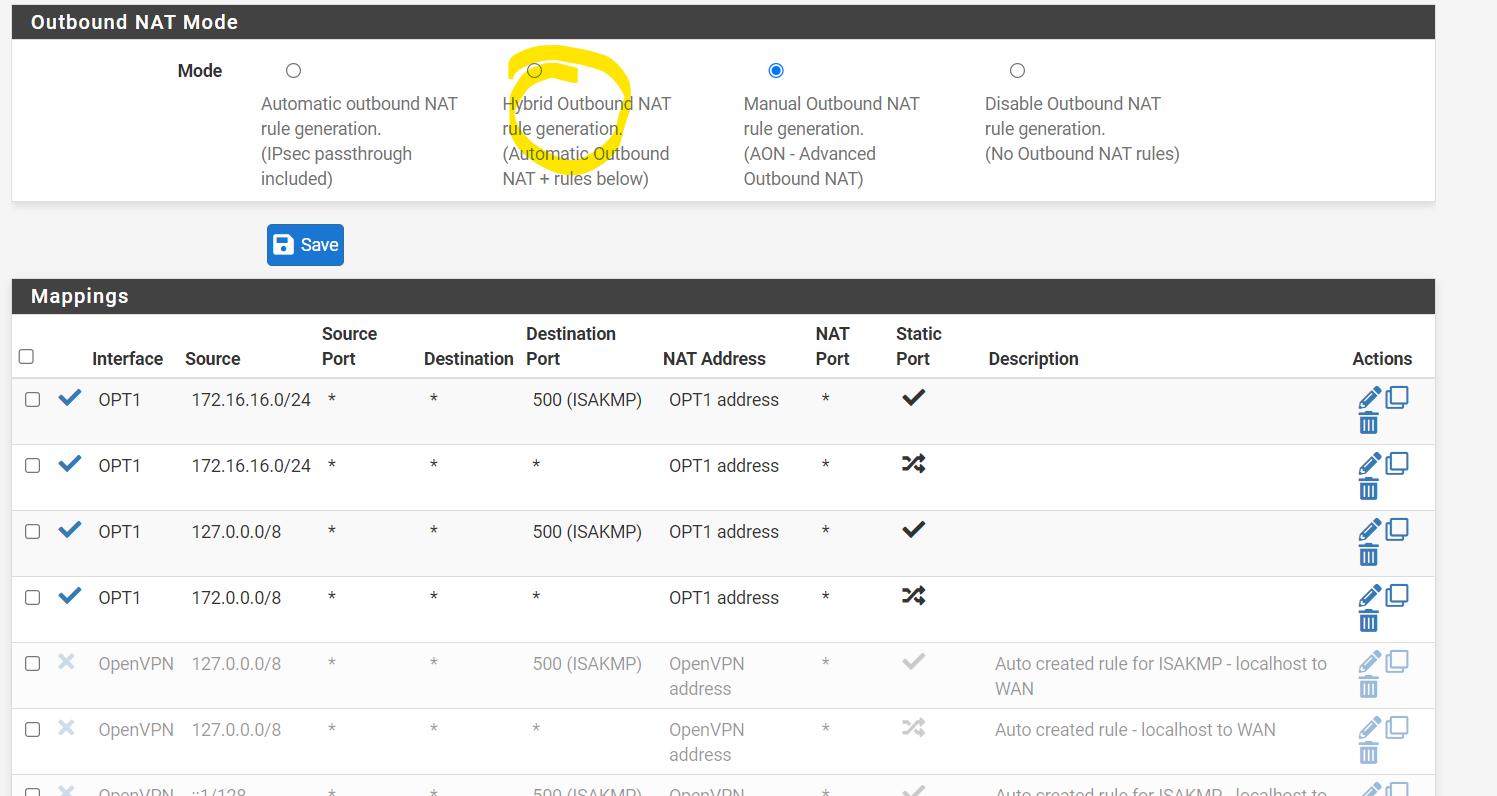
Hi, right I have enabled hybrid outbound NAT which has added some entries at the bottom
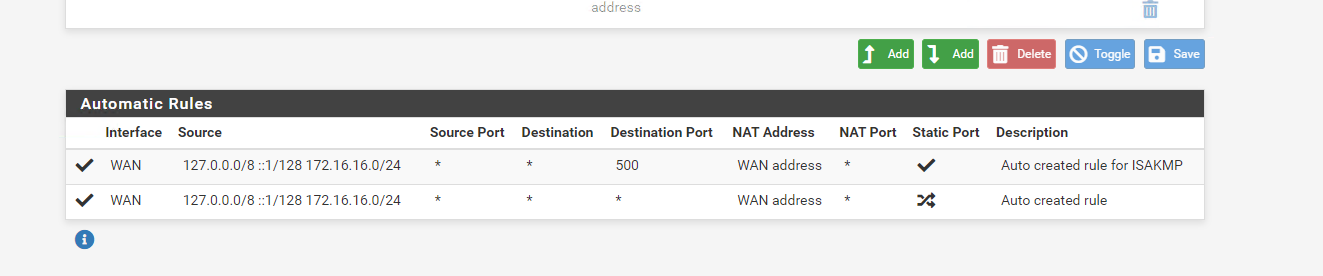
and the openVPN tab has no rules
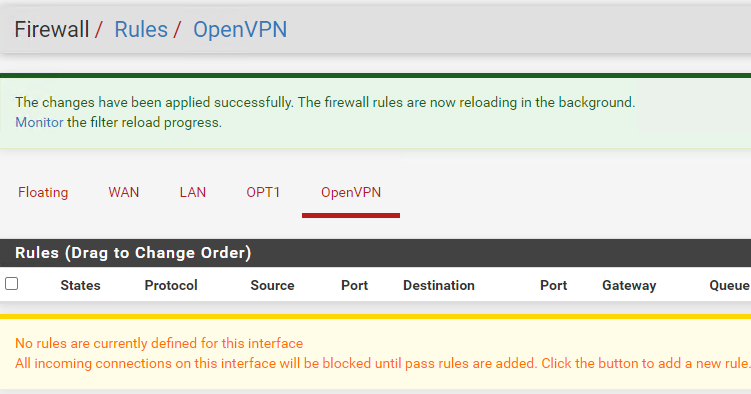
my openvpn client has only this NAT rule
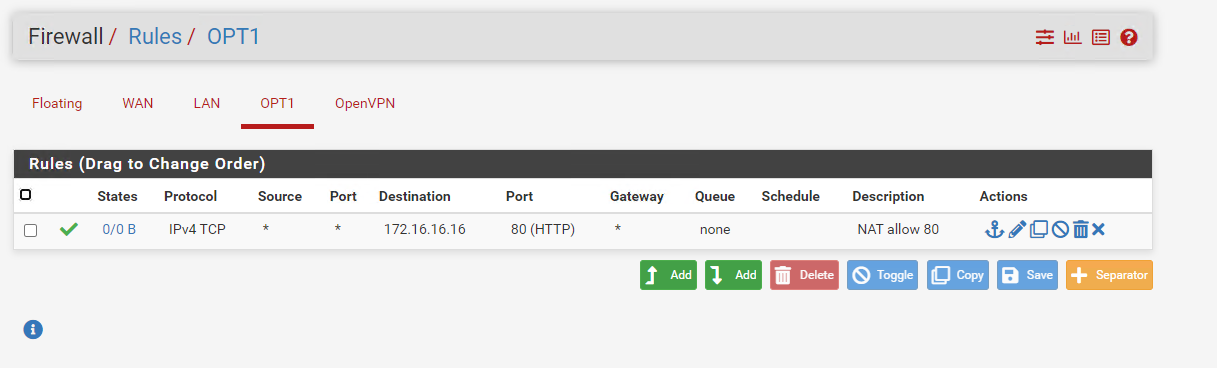
The WAN rules are empty and LAN only has the defaults
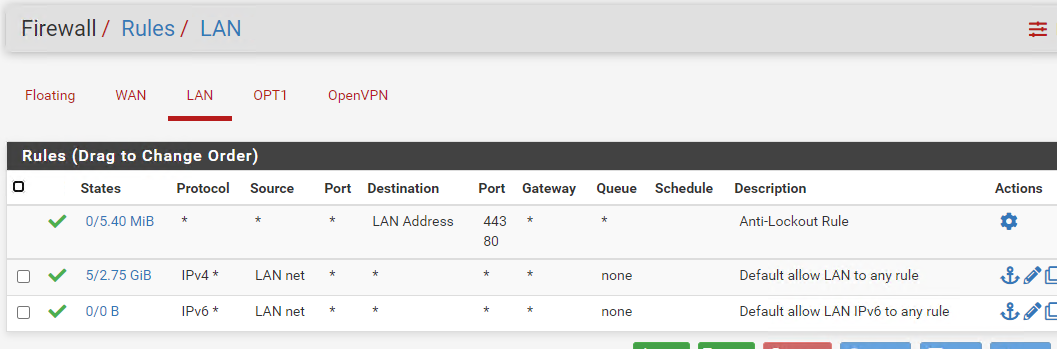
Anything I may have missed, and is there something else stopping this, if I go to diagnostics and pftop, I am not seeing any port 80 traffic.
appreciate your assistance
Cliff
-
@Cliffb
It would not work if a pass rule on the OpenVPN tab matches the incoming traffic.Could be that the destination server blocks access from outside.
To investigate on pfSense, use Diagnostic > Packet Capture to sniff the traffic.
On OPT1 interface you should see the incoming packets on port 80.
If you only see request packets there, but no responses, sniff on the LAN interface. If it's the same there your server doesn't respond. If there are response packets as well we have to dig further. -
It appears no traffic on port 80 is hitting the openvpn client interface to come in.
so incase I have missed something further upstream.
I have a ubuquiti USG3 and the PFsense is running on LAN port 2
Lan port 2 is giving DHCP address of 192.168.2.6 to the WAN side of PFsense
there are no rules in the USG3 firewall for that Lan port 2.I assume no rules are required as tunnel is established from the pfsense outbound and traffic comes in via the tunnel. ? and before the pfsense firewall was put in, I used the purevpn client on the webserver and I could get in to the webserver from the internet, just to test that I can get to the webserver from outside via the purevpn tunnel..
with the packet capture I am not seeing anything inbound looking like its headed to the webserver. So could my issue be elsewhere in the setup.?
I am still thinking its something in the pfsense setup, but dont understand where or where to look
thanks
Cliff
-
@Cliffb
Since pfSense establish the VPN to the provider, the USG is not in the play here.
The incoming packets to port 80 should be destined to the OPT1 address, which should be your virtual VPN IP. So I'd expect that you can see the packets there if the VPN is working.As you say, it works if you connect the webserver directly, this should mean that there is all setup correctly at the provider.
So on your site you can just ensure, that the VPN is connected properly.
Check Status > OpenVPN and the OpenVPN log to see if there is something wrong.On the webserver did you configure the network properly and set the default gateway to the pfSense LAN IP?
Can you try to connect the VPN on the server through pfSsense? -
hey, thanks for getting back to me
not seeing any packets coming in at all, plenty going out and I can get out through the VPN
the open vpn log is showing good, I cant put a screen shot as Currently been playing remotely from the server and changed some settings and locked myself, but that will be fixed when I get back to the machine.
I did read somewhere that openVPN client connecting to purevpn will allow outbound but not inbound.. so could be the issue that the openVPN connection to pure vpn is a one way connection..
which if so that sucks ! I needed to get to some equipment on my lan from the internet and CGNAT is stopping it, I was hoping this was the cure, may have to have a total re-think
Cliff
-
OK ,, worked out why now, so after all that effort PureVPN only support ports inbound on certain devices, OpenVpn not supported for inbound allegedly, when why I cant see any packets coming in..
not that I understand what they are saying as allegedly OpenVPN is supported for inbound on dd-WRT.. would have thought it would have been pretty much the same.
have to have a rethink now... thanks for your efforts
Cliff
-
@Cliffb
Don't know, how much you pay for this service. But consider to run your own VPS with a public IP and an VPN server. This way you can forward any port to your home network. However, it might cost a bit more. -
@viragomann That actually sounds like a proper idea. not happy with this vpn service at all..
thanks for your help, I think I'll go that route this has not got me very far, just have to find a good VPS and go with that
thanks