Block 1 IP client while on LTE Wan Backup interface
-
Is there a way to block 1 client (IP) from accessing the WAN while the LTE Backup interface is active?
I am trying to block my Nvidia Shield to access the internet in case my WAN switches over to LTE backup as it will chew the data.
-
@iptvcld
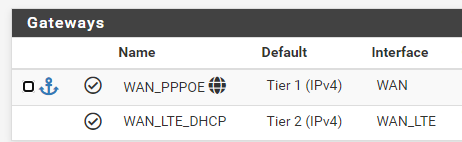
you can make an firewall rule with the PPPOE WAN gateway if I understand your question right.. -
@iptvcld yup as @slu mentions just policy route this one client out your pppoe connection before any rules that would route it out your failover group.
You prob want to make check this box..
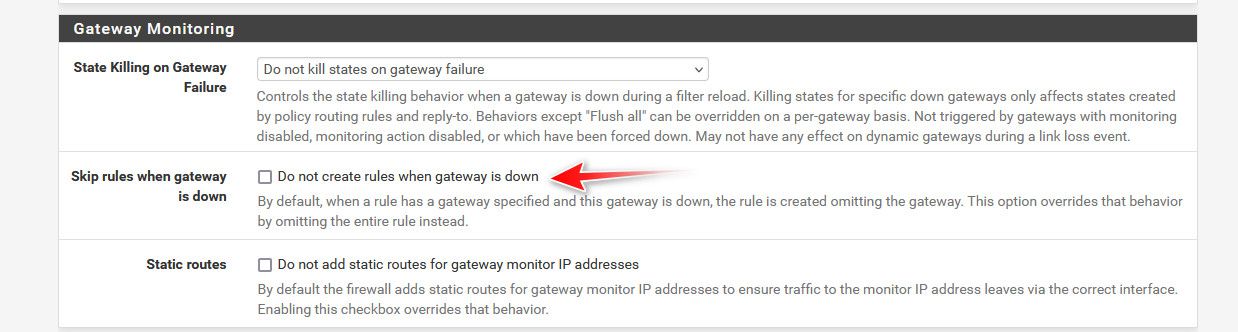
And then between the rule that sends your client out pppoe and your failover rule for everyone you will want a block rule for this client.
So when your pppoe fails and this rule isn't created he doesn't just fall thru to the allow rule out the failover group.
-
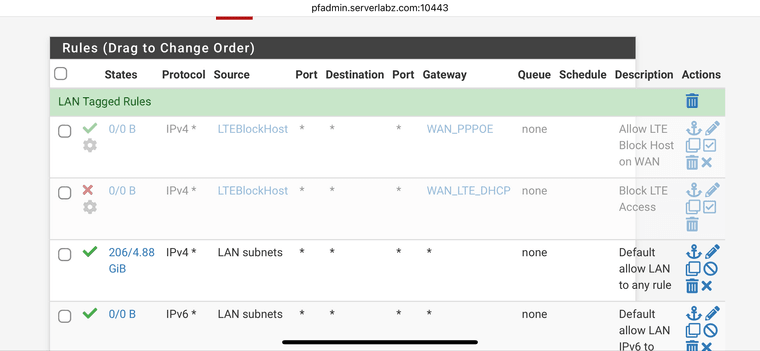
@johnpoz thanks.. I created an alias and added the IP I want to block internet access to and then added an allow while on ppoe gateway and a block while on lte gateway. But this is just blocking the device fully while on ppoe gateway.
-
@iptvcld Rule isn't even enabled.. I don't see any triggers on it.. Where is your rule that sends out your failed group? For your normal clients?
-
@johnpoz I had it enabled when I made it but then the nvidia shield stopped working and kids went crazy. LOL.. so I had to disable the rule. After I disabled the counters went to zero.
This is my lan interface so I allowed it full access out to any networks.
-
@iptvcld your shield stop doing what - loading files from some server on one of your other local networks? You would have do a bypass of policy routing..
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#bypassing-policy-routing
-
@johnpoz it stopped working as I’m not able to access the internet for YouTube. But it should not have blocked as I am on my ppoe gateway. It should only block while on lte gateway
-
@iptvcld you might have to have created a new state... I would test with some other device that wont have the kids screaming..
You have no rules for dns, where does the shield point to for dns? If it pointed to pfsense IP for example, you forcing it out a gateway before you allow it to talk to pfsense would prevent dns from working, etc.
Take a look at the policy route bypass I linked too.. You should have rules above policy routing that allows access to either pfsense IPs or other networks before you shove traffic out some gateway that can not get to these things.
And your block rules is kind of wrong underneath your policy route, it should just be a deny, it shouldn't really be a policy route.
-
@johnpoz ok I will read the doc you sent. As for my DNS, I have an external Ubuntu dns server that I am pointing my dhcp clients to. Too bad I can’t just add the source IP directly under the wan rules. Did not think it would be difficult to just block a client while going though a lte gateway.
-
@johnpoz said in Block 1 IP client while on LTE Wan Backup interface:
@iptvcld you might have to have created a new state... I would test with some other device that wont have the kids screaming..
You have no rules for dns, where does the shield point to for dns? If it pointed to pfsense IP for example, you forcing it out a gateway before you allow it to talk to pfsense would prevent dns from working, etc.
Take a look at the policy route bypass I linked too.. You should have rules above policy routing that allows access to either pfsense IPs or other networks before you shove traffic out some gateway that can not get to these things.
And your block rules is kind of wrong underneath your policy route, it should just be a deny, it shouldn't really be a policy route.
Hmmm. Yes I may need to add an allow rule from lan net to my dns server:53 at the top
-
@johnpoz so if I put an allow rule at the top of LAN as source block alias and destination DNS IP:53 and then put the 2 gateway rules under that. Would this indicate that the nvidia would be allowed to hit the dns server on any gateway and then the dns server blocks the nvidia if it sees it going out on the lte WAN?
-
@iptvcld what? Just set your rule to only allow access to lan address 53 tcp/udp.. Now anything on the lan can use this pfsense for dns. Or set it to allow any for dns.. But if nvidia wasn't using pfsense for dns then your rule would of worked allowing it out the pppoe.
Dns server doesn't block anything... So nvidia asks dns hey whats the IP for www.something.com, oh its 1.2.3.4 makes a connection to 1.2.3.4 on whatever port it was wanting to make a connection on.
Pfsense say oh nvidia IP your trying to go to something.. Here go out this gateway to get there..
If your pppoe is down, that rule wouldn't be there.. See the post about checking that box when your gateway is down.
This next rules say oh hey nvidia your trying to go to 1.2.3.4, sorry this rule says to block you.
Dns only part was letting nvidia know the IP address for www.something.com
Remember rules are evaluated top down, first rule to trigger wins, no other rules are evaluated.
-
@johnpoz excellent explanation, thank you. The screenshot I first sent with the 2 rules disabled, I now understand why that would not work as first of all there was no allow to elevate DNS (external outside of pfsense) and then that first rule was being met and no other rules were being evaluated.
I will put this all together this evening and test it out. Thank you.
-
@iptvcld said in Block 1 IP client while on LTE Wan Backup interface:
no allow to elevate DNS (external outside of pfsense)
if your client would of been pointing to some dns it could get to through pppoe wan then it would of worked.. My guess is your shield would of been asking pfsense IP for dns, which is what the default dhcp server on pfsense hands out.. Which while you could get to an IP out on the internet, you couldn't even look up what IP to go to for www.something.com
-
@johnpoz This is how i setup based on the feedback you provided and i performed a test by failing over my PPPOE WAN to LTE Backup and my test device had no internet connectivity. I then restored my PPPOE Wan and the connection resumed.
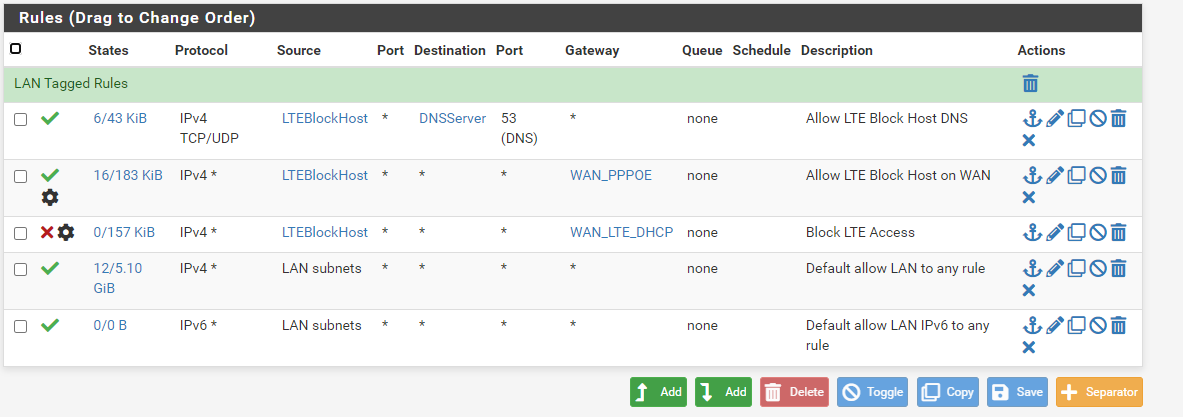
I am allowing that LTE Block Host DNS access to my DNS Servers on port 53
Then I am allowing LTE Block Host alias internet access via PPPOE WAN
And if PPPOE WAN goes down, then I have that block rule in place that will block LTE Block Host alias to have LTE WANThank you for your help again!
-
@iptvcld and again that block, your third rule should not have a gateway on it.. Did you check the box I showed you in screen shot? If not if wan pppoe goes down, then the rule will just be there without the gateway in rule 2 and would allow access through whatever gateway is up.
Why do you have another alias, for dns shouldn't it just point to pfsense lan IP? So just use the built in alias lan address.
-
@johnpoz yes, I checked that box you mentioned as well. And for the 3rd rule, I will remove the gateway as you right, it’s just a redundant option since it’s a block all rule anyways for that alias.
As for the DNS Server alias, I have 2 DNS servers (nextDNS) that I am self hosting on a Ubuntu container and those are are listening on port 53. So in pfsense, I have those 2 dns server IPs for all my dhcp clients to hand out. Pfsense is just doing my local host overrides for my domain.
-
@iptvcld ah ok so these dns servers are on some different vlan/network than this lan network.. Because if they are on the network the client is on, they would never go through pfsense to get to them.
Make sure you actually test that this works how you want it to work before you call it done ;)
edit:
On a bit of side note there was another thread today about someone sucking up their whole LTE quota 2GB in like 20 days without even moving data over it.. Do you have such a quota?Thinking about it - there might be quite a few people that have such lte backups and background traffic might be eating through their quota and either when they do need it they only have small amount left, and if they go over they get charged or dropped to a slower tier..
-
@johnpoz sorry can you explain a bit more on this?
if they are on the network the client is on, they would never go through pfsense to get to them.My DNS servers are on the MGMT vlan/network 10.200.x.x and my lan is on 192.168.x.x. So if my dns server was in my lan network, why would they never go through pfsense? Your saying they would just talk directly to the dns servers? What about my MGMT clients I have now? They are bypassing pfsense? Is this a bad thing? If I had rules set for MGMT clients, when they all be bypassed?