ssh wan block bug
-
@techpro2004 said in ssh wan block bug:
It is the same 2 entries over and over
May 13 05:45:00 sshguard 11007 Now monitoring attacks.
May 13 05:48:00 sshguard 11007 Exiting on signal.That is normally logged any time a log file in pfSense is rotated. If there are a lot, something is generating a lot of logging.
-
Why would you block SSH on WAN ?
Leave no rules what so ever on your WAN interface, and use the default behavior : everything is blocked, except what you accept expressly with a pas rule ?Btw : having SSH open on the WAN is ... well .... not done.
Fire up a OpenVPN server instance, and have the user connect the VPN first.
When done, he can now SSH in safely , for example connecting to "192.168.1.1 port 22"
TCP". But first he has to activate the OpenVPN client on his device.This is what I have on my WAN :
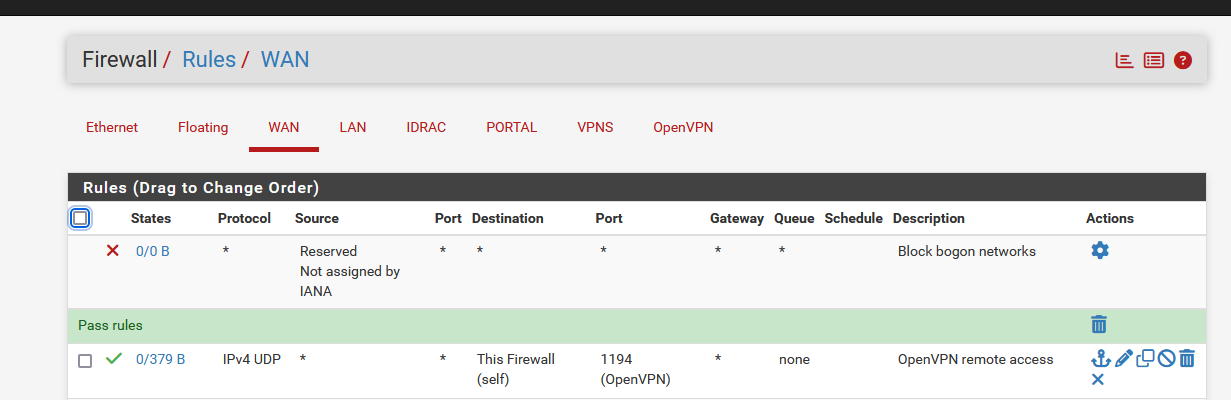
I've port 1194 UDP open, the classic OpenVPN port. That's it.
sshguard can get restarted when there is a "interface' event. Or when the systemlog get rotated, or some other processes get restarted. It harmless.
Mine did restart about 60 times the last 30 days. -
It seems to happen every 3 min. I have cut back on my logging but no luck.
-
I also have a lot of these.
May 13 11:17:30 miniupnpd 16935 ioctl(dev, DIOCCHANGERULE, ...) PF_CHANGE_ADD_TAIL: File exists
not sure how to stop them either.
-
@techpro2004 It's not every log file, it just has to be one of them. For instance leaving the dashboard up with a lot of widgets that update.
The miniupnpd error I think I saw posted here recently.
-
I do not have a lot of widgets or leave the web ui open.
-
@techpro2004 OK but we don't know which log file it is either. :) Try "ls -l /var/log/" and see if any have really close timestamps.
-
output below
total 186301
-rw------- 1 root wheel 361679 May 13 13:10 auth.log
-rw------- 1 root wheel 511143 May 9 16:01 auth.log.0
-rw------- 1 root wheel 511160 May 4 12:14 auth.log.1
-rw------- 1 root wheel 511116 Apr 29 02:03 auth.log.2
-rw------- 1 root wheel 511163 Apr 17 21:39 auth.log.3
-rw-r--r-- 1 root wheel 35193 Aug 9 2023 bsdinstall_log
drwxr-xr-x 2 clamav clamav 4 Apr 24 16:54 c-icap
drwxr-xr-x 2 clamav clamav 5 Sep 30 2023 clamav
-rw------- 1 root wheel 31264 May 13 13:10 dhcpd.log
-rw------- 1 root wheel 532574 May 13 12:48 dhcpd.log.0
-rw------- 1 root wheel 512127 May 12 18:40 dhcpd.log.1
-rw------- 1 root wheel 513660 May 12 00:47 dhcpd.log.2
-rw------- 1 root wheel 525924 May 11 20:12 dhcpd.log.3
-rw------- 1 root wheel 600929 May 11 18:08 dhcpd.log.4
-rw------- 1 root wheel 512803 May 11 10:40 dhcpd.log.5
-rw------- 1 root wheel 551188 May 11 03:39 dhcpd.log.6
-rw-r--r-- 1 root wheel 12760 May 11 20:11 dmesg.boot
-rw------- 1 root wheel 117458457 May 13 13:11 filter.log
-rw------- 1 root wheel 114864576 May 13 13:09 filter.log.0
-rw------- 1 root wheel 117943166 May 13 13:06 filter.log.1
-rw------- 1 root wheel 126299122 May 13 13:03 filter.log.2
-rw------- 1 root wheel 119374123 May 13 13:00 filter.log.3
-rw------- 1 root wheel 122887130 May 13 12:57 filter.log.4
-rw------- 1 root wheel 123248464 May 13 12:54 filter.log.5
-rw------- 1 root wheel 124701905 May 13 12:51 filter.log.6
-rw------- 1 root wheel 4195 May 11 20:11 gateways.log
-rw------- 1 root wheel 0 Aug 9 2023 haproxy.log
-rw------- 1 root wheel 0 May 11 20:11 ipsec.log
-rw------- 1 root wheel 0 May 11 20:11 l2tps.log
-rw-r--r-- 1 root wheel 0 Aug 9 2023 lastlog
drwx------ 2 www www 2 Apr 23 11:42 lighttpd
drwxr-xr-x 2 root wheel 3 Aug 9 2023 nginx
-rw------- 1 root wheel 373815 May 13 13:11 nginx.log
-rw------- 1 root wheel 511909 May 5 20:20 nginx.log.0
-rw------- 1 root wheel 513445 Apr 14 21:26 nginx.log.1
-rw------- 1 root wheel 515809 Jan 13 15:12 nginx.log.2
-rw------- 1 root wheel 518316 Dec 9 13:39 nginx.log.3
-rw------- 1 root wheel 514855 Nov 13 19:45 nginx.log.4
-rw------- 1 root wheel 511179 Oct 31 2023 nginx.log.5
-rw------- 1 root wheel 511683 Oct 25 2023 nginx.log.6
drwxr-xr-x 2 root wheel 2 Aug 9 2023 ntp
-rw------- 1 root wheel 498009 May 13 12:48 ntpd.log
-rw------- 1 root wheel 424405 May 13 12:48 openvpn.log
-rw------- 1 root wheel 514677 May 3 17:51 openvpn.log.0
-rw------- 1 root wheel 515736 Apr 14 21:14 openvpn.log.1
-rw------- 1 root wheel 519574 Mar 28 09:20 openvpn.log.2
-rw------- 1 root wheel 543139 Mar 12 16:05 openvpn.log.3
-rw------- 1 root wheel 512035 Feb 25 08:39 openvpn.log.4
-rw------- 1 root wheel 516006 Feb 8 00:21 openvpn.log.5
-rw------- 1 root wheel 512844 Jan 25 06:57 openvpn.log.6
drwxr-xr-x 2 unbound unbound 11 May 13 11:03 pfblockerng
-rw------- 1 root wheel 0 May 11 20:11 poes.log
-rw------- 1 root wheel 0 May 11 20:11 portalauth.log
-rw------- 1 root wheel 0 May 11 20:11 ppp.log
-rw------- 1 root wheel 103242 May 13 12:48 resolver.log
-rw------- 1 root wheel 513046 May 12 10:20 resolver.log.0
-rw------- 1 root wheel 553198 May 11 18:07 resolver.log.1
-rw------- 1 root wheel 520526 May 9 00:01 resolver.log.2
-rw------- 1 root wheel 513547 May 5 20:17 resolver.log.3
-rw------- 1 root wheel 538213 Apr 30 00:01 resolver.log.4
-rw------- 1 root wheel 517906 Apr 21 00:01 resolver.log.5
-rw------- 1 root wheel 520503 Apr 14 21:36 resolver.log.6
-rw------- 1 root wheel 420794 May 13 13:11 routing.log
-rw------- 1 root wheel 511585 May 12 20:36 routing.log.0
-rw------- 1 root wheel 511727 May 12 00:23 routing.log.1
-rw------- 1 root wheel 511438 May 11 04:48 routing.log.2
-rw------- 1 root wheel 511301 May 10 14:49 routing.log.3
-rw------- 1 root wheel 511427 May 9 17:45 routing.log.4
-rw------- 1 root wheel 511201 May 8 20:59 routing.log.5
-rw------- 1 root wheel 511650 May 8 00:47 routing.log.6
drwxr-x--- 2 squid squid 2 Dec 8 12:00 squid
-rw------- 1 root wheel 499970 May 13 13:10 system.log
-rw------- 1 root wheel 511110 May 11 17:43 system.log.0
-rw------- 1 root wheel 511097 May 8 21:12 system.log.1
-rw------- 1 root wheel 524351 May 5 20:28 system.log.2
-rw------- 1 root wheel 538069 May 3 17:41 system.log.3
-rw------- 1 root wheel 511115 Apr 29 04:47 system.log.4
-rw------- 1 root wheel 511124 Apr 25 05:23 system.log.5
-rw------- 1 root wheel 520145 Apr 16 12:59 system.log.6
-rw------- 1 root wheel 62742 May 11 20:11 userlog
-rw-r--r-- 1 root wheel 394 May 11 20:11 utx.lastlogin
-rw------- 1 root wheel 5112 May 11 20:11 utx.log
-rw------- 1 root wheel 0 May 11 20:11 vpn.log
-rw------- 1 root wheel 0 May 11 20:11 watchdogd.log
-rw------- 1 root wheel 0 May 11 20:11 wireless.log -
@techpro2004 said in ssh wan block bug:
-rw------- 1 root wheel 117458457 May 13 13:11 filter.log
-rw------- 1 root wheel 114864576 May 13 13:09 filter.log.0
-rw------- 1 root wheel 117943166 May 13 13:06 filter.log.1
-rw------- 1 root wheel 126299122 May 13 13:03 filter.log.2
-rw------- 1 root wheel 119374123 May 13 13:00 filter.log.3Those are rolling over ever what like 2-3 minutes..
Yeah you got something logging a lot of stuff.. And its rolling your log over.. What is showing in the log? You got a bunch of noise?
-
it is a ton of entries all similar to this.
May 13 14:00:00 pfSense newsyslog[45275]: logfile turned over due to size>500K
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,128,48031,0,none,17,udp,32,192.168.1.3,255.255.255.255,3000,2000,12
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,128,10479,0,none,17,udp,49,192.168.1.27,192.168.1.255,60686,32412,29
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,128,10478,0,none,17,udp,49,192.168.1.27,192.168.1.255,60688,32414,29
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,128,9469,0,none,17,udp,49,192.168.1.24,192.168.1.255,60687,32412,29
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,128,9468,0,none,17,udp,49,192.168.1.24,192.168.1.255,60689,32414,29
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,27614,0,none,17,udp,121,192.168.1.3,239.255.255.251,37810,37810,101
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,48715,0,DF,17,udp,863,192.168.1.4,239.255.255.251,37810,37810,843
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,34515,0,DF,17,udp,691,192.168.1.14,239.255.255.251,37810,37810,671
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,64642,0,DF,17,udp,691,192.168.1.16,239.255.255.251,37810,37810,671
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,9381,0,DF,17,udp,690,192.168.1.12,239.255.255.251,37810,37810,670
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,49402,0,DF,17,udp,691,192.168.1.18,239.255.255.251,37810,37810,671
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,20481,0,DF,17,udp,818,192.168.1.6,239.255.255.251,37810,37810,798
May 13 14:00:00 pfSense filterlog[7432]: 2,,,1000000101,ix0,match,block,in,4,0x0,,128,46560,0,none,17,udp,256,169.254.14.211,192.168.1.27,1900,60690,236
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,ix0,match,block,in,4,0x0,,64,25164,0,DF,6,tcp,52,192.168.1.45,44.239.252.140,60362,443,0,FA,1650631059,2175163242,727,,nop;nop;TS
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,41262,0,DF,17,udp,805,192.168.1.5,239.255.255.251,37810,37810,785
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,ix0,match,block,in,4,0x0,,64,25165,0,DF,6,tcp,52,192.168.1.45,44.239.252.140,60362,443,0,FA,1650631059,2175163242,727,,nop;nop;TS
May 13 14:00:01 pfSense filterlog[7432]: 4,,,1000000103,ix0,match,block,in,4,0x0,,64,25166,0,DF,6,tcp,52,192.168.1.45,44.239.252.140,60362,443,0,FA,1650631059,2175163242,727,,nop;nop;TS
May 13 14:00:01 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,50938,0,DF,17,udp,759,192.168.1.8,239.255.255.251,37810,37810,739
May 13 14:00:01 pfSense filterlog[7432]: 2,,,1000000101,ix0,match,block,in,4,0x0,,128,43430,0,none,17,udp,256,169.254.14.211,192.168.1.24,1900,60691,236
May 13 14:00:01 pfSense filterlog[7432]: 4,,,1000000103,ix0,match,block,in,4,0x0,,64,25167,0,DF,6,tcp,52,192.168.1.45,44.239.252.140,60362,443,0,FA,1650631059,2175163242,727,,nop;nop;TS
May 13 14:00:02 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,64,3621,0,DF,17,udp,235,192.168.1.127,255.255.255.255,48461,10001,215
May 13 14:00:02 pfSense filterlog[7432]: 6,,,1000000105,bridge0,match,block,in,6,0x00,0x58ab3,1,UDP,17,215,fe80::f6e2:c6ff:feac:ad00,ff02::1,39544,10001,215
May 13 14:00:02 pfSense filterlog[7432]: 4,,,1000000103,ix0,match,block,in,4,0x0,,64,25168,0,DF,6,tcp,52,192.168.1.45,44.239.252.140,60362,443,0,FA,1650631059,2175163242,727,,nop;nop;TS
May 13 14:00:03 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,64,10936,0,DF,17,udp,235,192.168.1.121,255.255.255.255,39840,10001,215
May 13 14:00:03 pfSense filterlog[7432]: 6,,,1000000105,bridge0,match,block,in,6,0x00,0x0d024,1,UDP,17,215,fe80::f6e2:c6ff:feac:cb23,ff02::1,43124,10001,215
May 13 14:00:05 pfSense filterlog[7432]: 4,,,1000000103,ix0,match,block,in,4,0x0,,64,25169,0,DF,6,tcp,52,192.168.1.45,44.239.252.140,60362,443,0,FA,1650631059,2175163242,727,,nop;nop;TS
May 13 14:00:05 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,7954,0,none,17,udp,165,192.168.1.19,239.255.255.250,61222,1900,145
May 13 14:00:05 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,128,10481,0,none,17,udp,49,192.168.1.27,192.168.1.255,60686,32412,29
May 13 14:00:05 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,128,10480,0,none,17,udp,49,192.168.1.27,192.168.1.255,60688,32414,29
May 13 14:00:05 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,128,9470,0,none,17,udp,49,192.168.1.24,192.168.1.255,60687,32412,29
May 13 14:00:05 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,128,9471,0,none,17,udp,49,192.168.1.24,192.168.1.255,60689,32414,29
May 13 14:00:05 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,64,32145,0,DF,17,udp,361,192.168.1.31,255.255.255.255,48029,10001,341
May 13 14:00:05 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,64,57897,0,DF,17,udp,361,192.168.1.30,255.255.255.255,36700,10001,341
May 13 14:00:07 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,27897,0,none,17,udp,129,192.168.1.27,239.255.255.250,60690,1900,109
May 13 14:00:07 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,10343,0,none,17,udp,129,192.168.1.24,239.255.255.250,60691,1900,109
May 13 14:00:07 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,128,48032,0,none,17,udp,32,192.168.1.3,255.255.255.255,58993,8602,12
May 13 14:00:08 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,2154,0,none,17,udp,68,192.168.1.27,224.0.0.251,5353,5353,48
May 13 14:00:08 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,34754,0,none,17,udp,68,192.168.1.24,224.0.0.251,5353,5353,48
May 13 14:00:08 pfSense filterlog[7432]: 2,,,1000000101,ix0,match,block,in,4,0x0,,128,43431,0,none,17,udp,256,169.254.14.211,192.168.1.24,1900,60691,236
May 13 14:00:09 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,128,48033,0,none,17,udp,32,192.168.1.3,255.255.255.255,58994,8600,12 -
the only bridge I have connects my wireguard interface to my lan
edit: I have no users currently connected to wireguard.
-
@techpro2004 I see a bunch of noise in there, you got multicast.. that stuff to 239.255.255.251, I see some directed broadcast traffic to 192.168.1.255, I see something with a APIPA address 169.254.x.x sending to sending to SSDP/UPnP (port 1900)..
Why do you have a bridge setup at all.. I don't use wireguard, but have tailscale setup and it doesn't have any bridge.. Not sure why you would bridge that - pretty sure WG is L3, bridging is at L2.. Not understanding why you would think you need a bridge?
-
I saw some instructions online a while ago that said to do it. Plus, i use wireguard to access my lan from my cellphone on the go
-
@techpro2004 Ultimately, logged blocks would be that pfSense is set to log the default block rule (the default setting), or log blocked bogons/RFC1918 (also default), or a rule is set to log the block. If you don't want the blocks logged you can turn those off. Or you can raise the max log file size so logs rotate less often. Or just ignore the sshguard notification.
(or in 24.03 it logs IGMP blocks)
-
@techpro2004 said in ssh wan block bug:
i use wireguard to access my lan from my cellphone on the go
Yeah that has nothing to do with a "bridge"
Not sure what "guide" you followed but you wouldn't setup a bridge in any scenario that I can think of.. I use my tailscale to access stuff on multiple networks locally while I am out and about - no bridge setup..
https://docs.netgate.com/pfsense/en/latest/recipes/wireguard-ra.html
-
bogons/rfc is disabled. the only rules that log is pfblocker auto rules.
-
@techpro2004 OK, so, don't do that? You have options of "log less," or "let the log files grow so they rotate less frequently." Or ignore the notification.
-
-
on the subject of logging less, How do I figure out where the filter logs are from.
-
I removed the bridge and wireguard still works and I am getting a lot less entries in the filter log.