OpenVPN config - traffic not NATing
-
I have been fighting the good with a VPN provider using OpenVPN. I can connect to the VPN service, but the traffic is not being NAT'd. My IP is still showing as the IP given to me by my internet service provider.
I am still pretty green with this, which is making it pretty difficult.
I have a netgate3100 running on 24.03
I seem to have an interface named OpenVPN, and I have outbound auto generated outbound NAT firewall rules for said interface. Not sure what logs to look at to show what it is doing or not ....doing. :-)
Anyone have any thoughts?
-
@clazmania
Check to see the interface is enabled?
How do you know you are connecting to the vpn service?
You have a NAT outbound rule for the openVPN to go out the WAN?
Do you have NAT outbound rule for the LAN to go out the VPN tunnel? -
@clazmania
Did you check "Don't pull routes" in the OpenVPN client settings?
If so remove the check. -
Thank you for the reply.
The interface is enabled.
Under status > OpenVPN I see it with a status of connected (success) with a Virtual Address as well.The last 2 questions, are the confusing part.
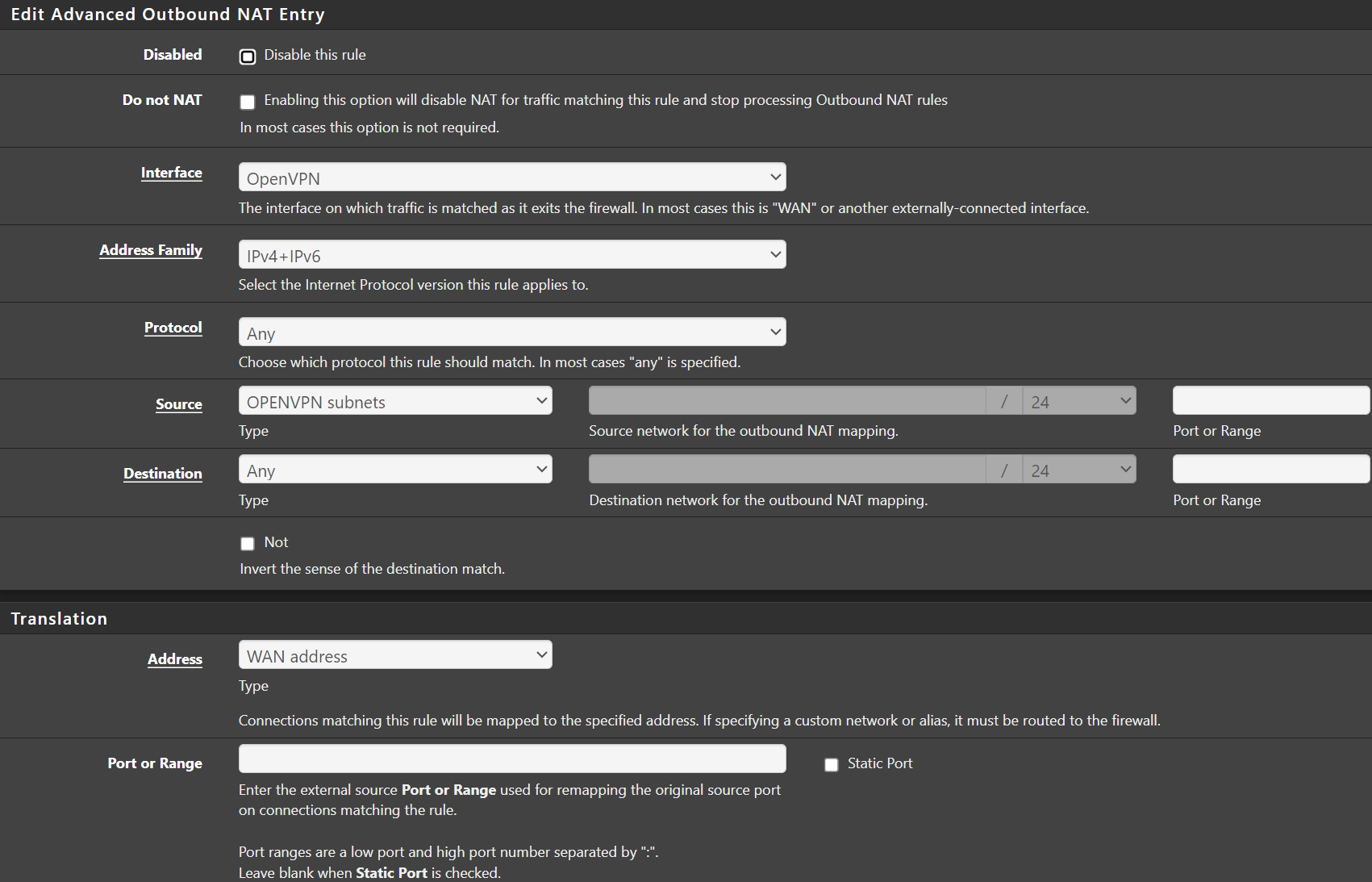
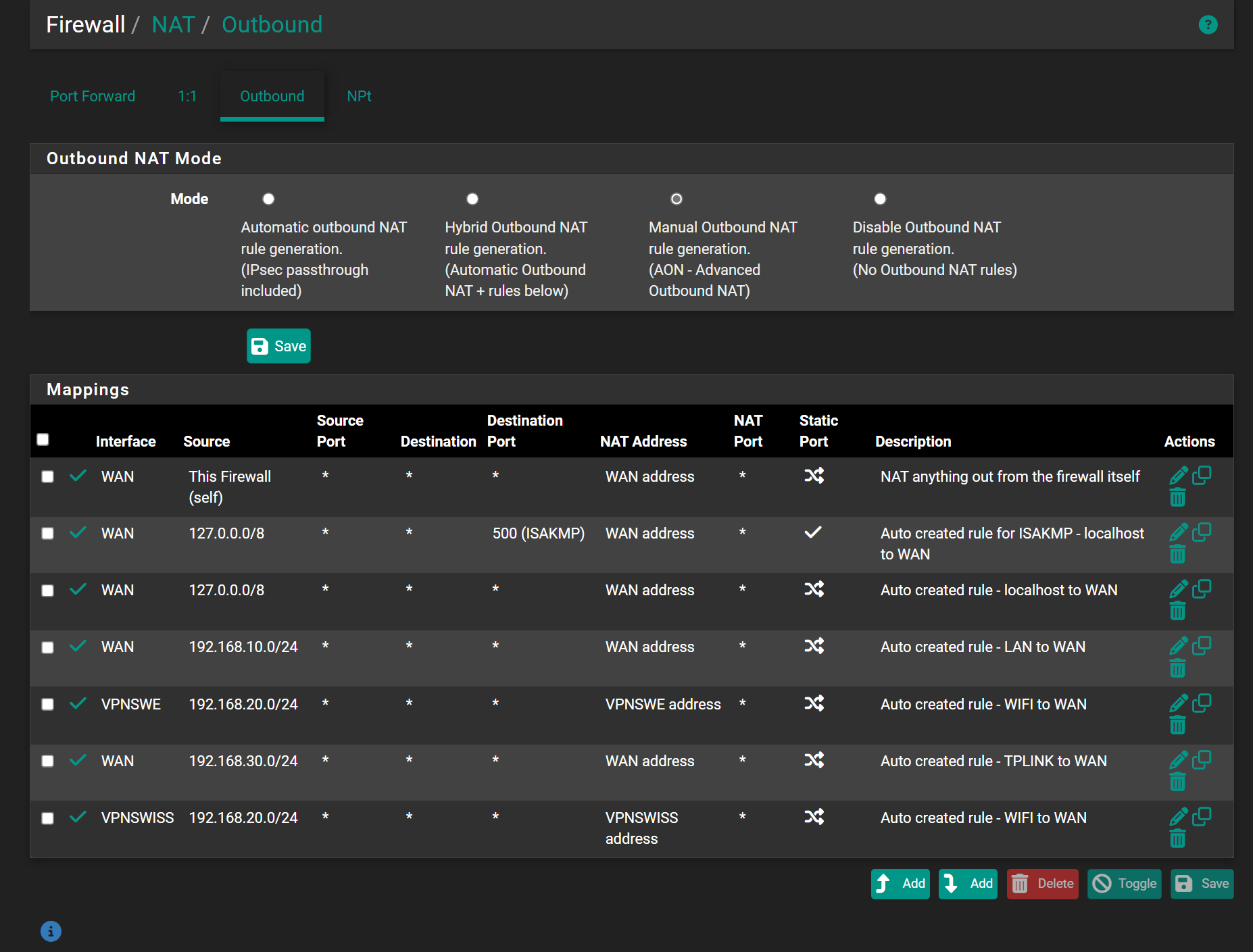
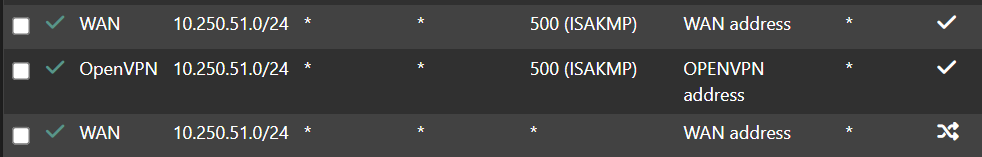
So I have a NAT entry, i have this for one of my internet nets:
nat on mvneta2 inet from 10.x.51.0/24 to any port = isakmp -> 98.162.x.x static-port
nat on openvpn inet from 10.x.51.0/24 to any port = isakmp -> (openvpn) round-robin static-port
nat on mvneta2 inet from 10.x.51.0/24 to any -> 98.162.x.x port 1024:65535 -
It is checked, but internet access breaks if I uncheck it. Leads me to believe I do have a NAT issue.
-
@clazmania
Yes, then presumably you're missing the outbound NAT rule.Is the outbound NAT in automatic mode?
I'd expect, that the required rule is generated automatically if it is.
Otherwise you have to add it manually. -
-
@clazmania
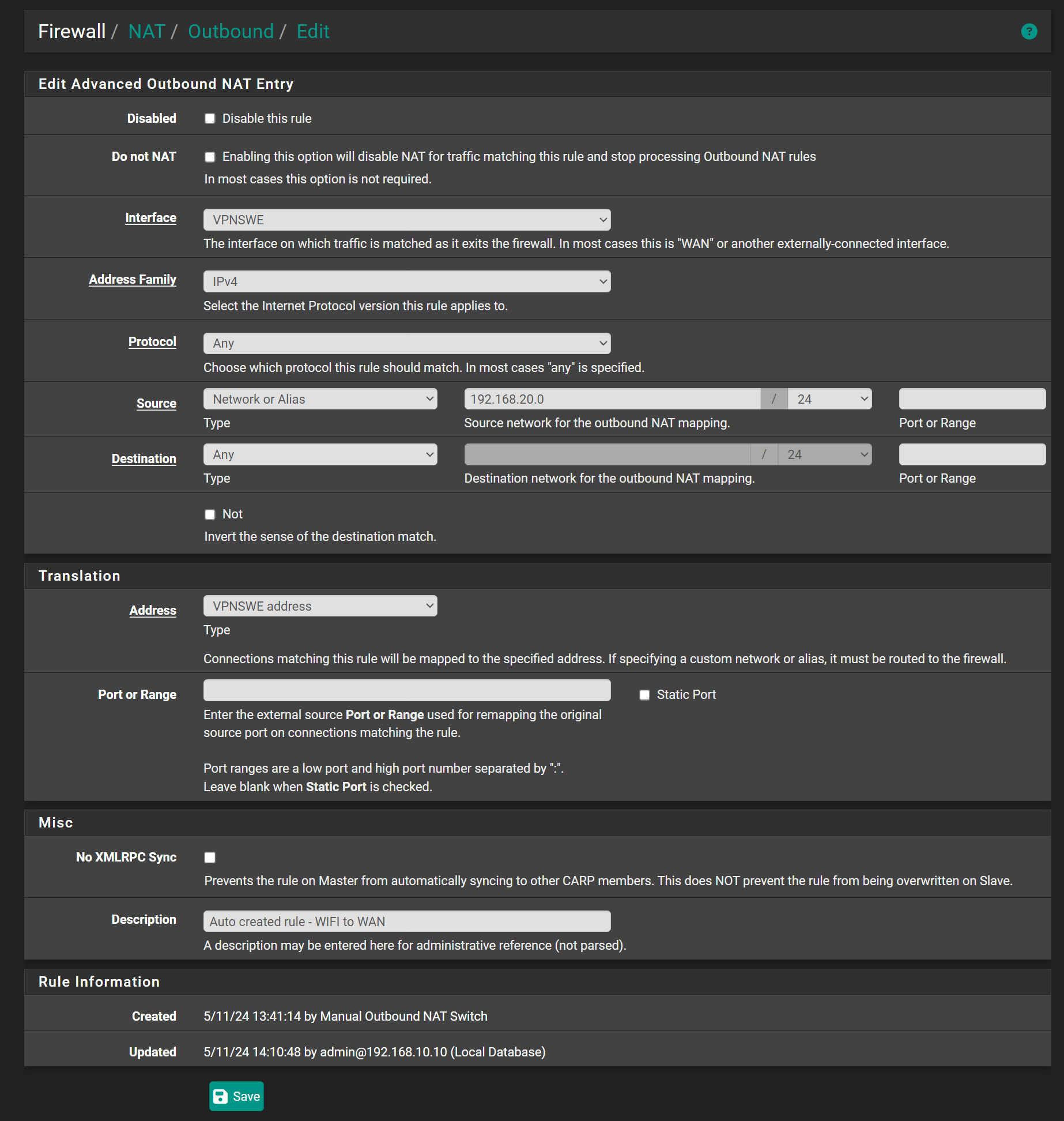
The source has to be your internal networks, e.g. "LAN subnets" and the translation address has to be the VPN clients address. pfSense might provide a variable for it in the drop-down. Otherwise you have to assign an interface to the VPN client instance to get it. -
-
-
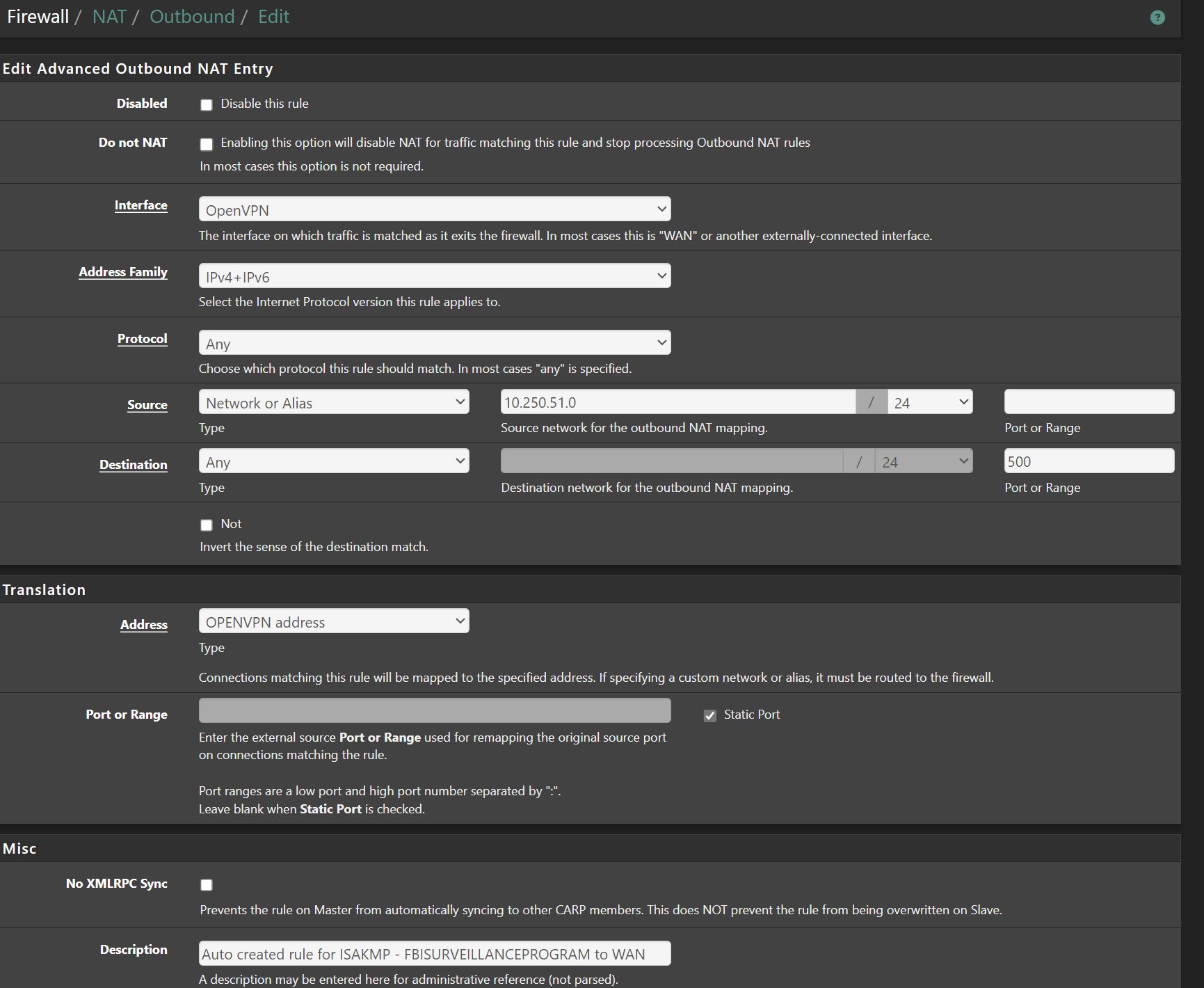
@Antibiotic Thanks, I do have a similar config. The only difference is the dst port, guessing due to ISAKMP.
-
This post is deleted! -
-
-
@clazmania Are you using IPSEC VPN?
Shoud be set VPN interface not a OpenVPN itself. IDK may by you called VPN interface as OpenVPN))) -
@Antibiotic I did call it OpenVPN and that may have been a mistake. Because I have an OPENVPN and OpenVPN and I think that is causing confusion for me. I guess I can remove the config and recreate with another name. Then revisit.
-
@clazmania said in OpenVPN config - traffic not NATing:
@Antibiotic I did call it OpenVPN and that may have been a mistake. Because I have an OPENVPN and OpenVPN and I think that is causing confusion for me. I guess I can remove the config and recreate with another name. Then revisit.
Reply Quote
0Ah ))) Good luck
-
@clazmania
I don't assume, that you want to edtablish an IPSec through the OpenVPN provider. That's the only thing the ISAKMP rule is good for, however. -
@clazmania ISAKMP only use for IPsec protocol , if you use openvpn protocol set as in my example
-
@Antibiotic I just wanted to follow up on this one. I found out the problem was that I had not changed the gateway for the firewall rule, which is listed in the advanced settings. After changing the gw, voila. Darn stupid mundane details...i swear.....
Anyway, thank you for helping....