Consolidating rules with NOT (invert) operator
-
I have device on a vlan I want to permit ftp access only to a specific server on a different vlan.
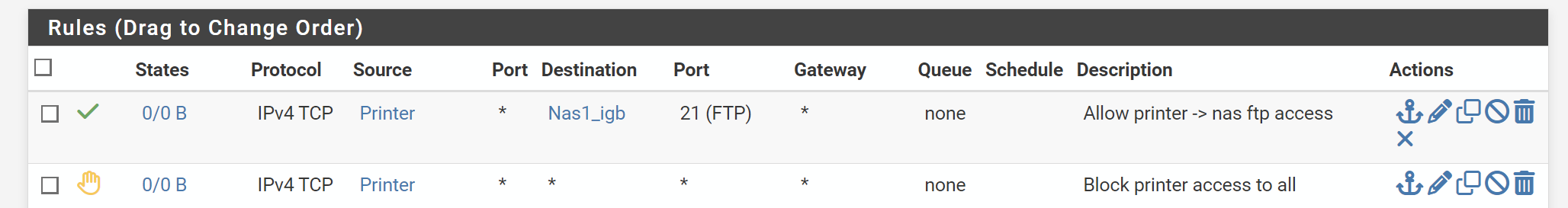
The above works well to permit printer to send ftp traffic to nas1, but everything else is blocked. I thought I could combine this into a single rule using not (!) operator.
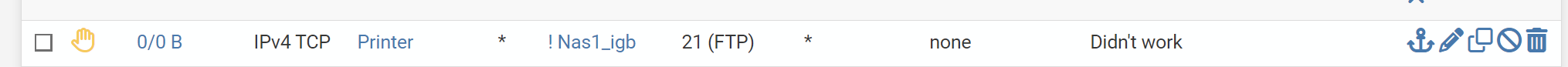
Meaning, block all traffic not going to nas1 using port 21. It does indeed block all traffic, but also traffic destined for nas1/port21.
If i'm understanding correctly, the reason being, firewall by default is block all, anywhere. Without explicit allow rule(s), this (single) rule does indeed block all traffic going anywhere but nas1, but doesn't permit traffic to nas1 either.
Is there a way of formulating the original 2 rules into a functional single rule?
-
@GPz1100 if there are no other rules, your second rule in example 1 is unnecessary because of the default block.
Your second example does not allow anything.
Note passive FTP requires a large number of additional ports allowed for the data connections.
-
@SteveITS There is a floating rule that allows basic traffic on all vlans (dns, ntp, http(s), etc), but it's NOT set as quick, so other block rules can override.
While I did not set or enable active ftp mode explicitly, it appears to allow it. The ftp server in question is part of truenas scale.
In fact, in testing, passive ftp would not transfer at all with just the first allow rule above.
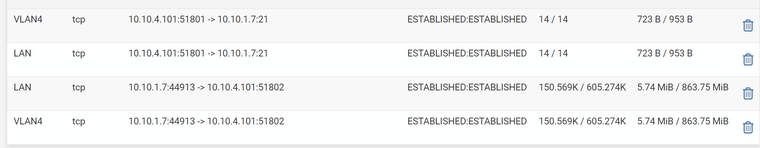
This is a snapshot of the state table when a transfer is in progress with the single allow rule. I'm not entirely clear why the last 2 states are permitted as there's no other rules pertaining to these 2 end points?
-
@GPz1100 I would guess your floating rule is allowing it if/since you're not blocking those ports otherwise. But, you say FTP transfer didn't work?
Passive FTP ports are controlled by the server. Some use all 1024 through 65535.
FWIW I usually prefer two rules just for clarity.
The floating vs interface rule order may be involved here, too:
https://docs.netgate.com/pfsense/en/latest/nat/process-order.html