Wireguard and DNS/LAN Firewall rules
-
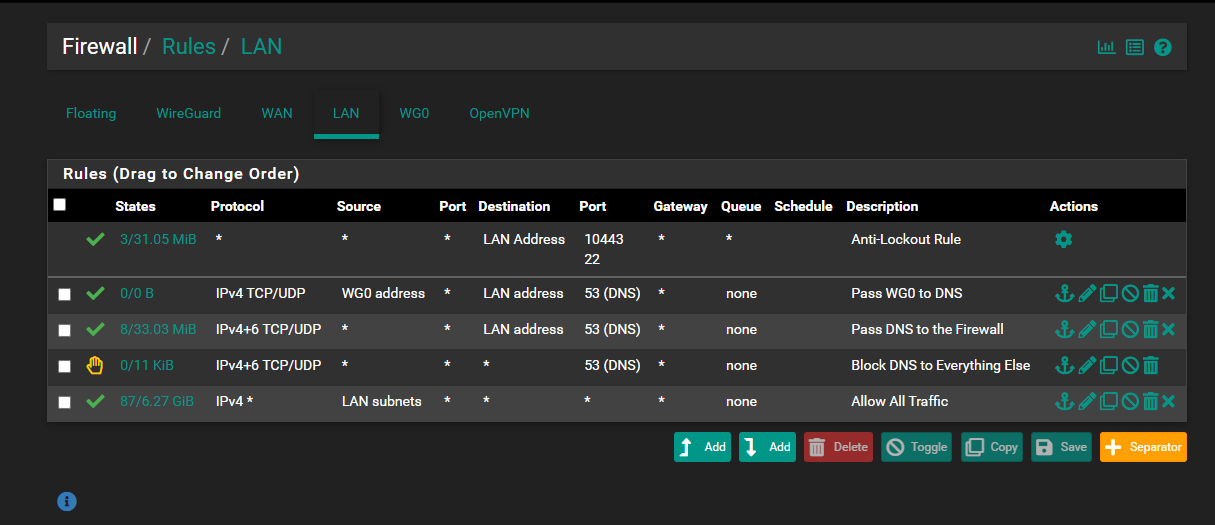
I recently stood up WG and I could connect to my network, but traffic wouldn't flow from my iPhone client to pfSense server. Checking the system logs for firewall, I could see the "Default deny rule IPv4" occur for the iPhone to the server on port 53. After reviewing my firewall rules, I had the WG and WAN rules to all traffic, but my LAN firewall rules were the issue. I have a "Pass DNS to the Firewall" to allow IPv4+6 TCP/UDP from Any source to 'LAN address', port 53(DNS). Below it I have a "Block DNS to Everything Else" to Reject IPv4+6 TCP/UDP from Any source to Any destination via port 53.
The resolution I am testing is adding a rule above the "Pass DNS to the Firewall" as "Pass WG0 to DNS" where IPv4 TCP/UDP from 'WG0 address' source to 'LAN address' via port 53(DNS). WG0 interface is the (tun_wg0) assignment for WG. It seems to resolve correctly. My PiHole DNS server blocks ads, I can receive my home network's IP address, ping devices on my network, etc.
My question, is this logical? Does this actual solve this issue, or is it a façade and needs attention for a better solution? Does the WG0 interface need firewall rules to resolve the issue? Any input or recommendations would be appreciated.
-
@Tenorbro Your rule is useless. For your phone, if it is connected via wireguard, you have to create its rules on the "WG0" interface.
-
@Tenorbro Yeah, don't know what else you did but that rule didn't fix it.
The rule right below it has ANY as source so that rule already does what the new rule is doing.
What rules are on the WG interface? -
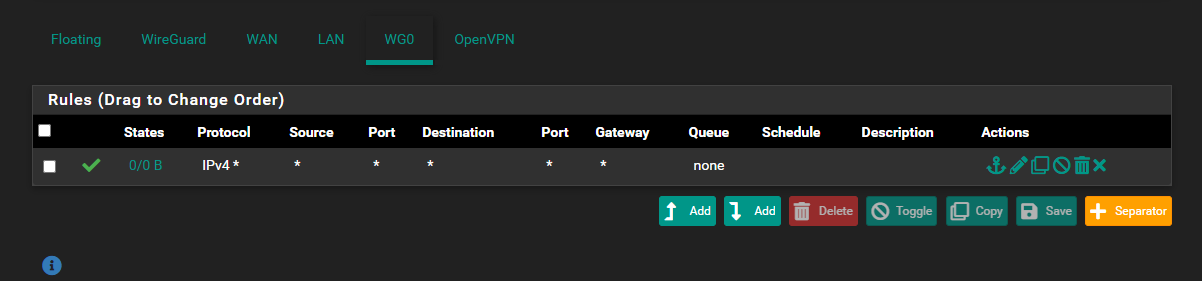
@Jarhead Taking @Bob-Dig reply into consideration, I removed the "Pass WG0 to DNS" from the LAN rules and added this pass rule to the WG0 interface. It seems to work too and I see traffic across the WG0
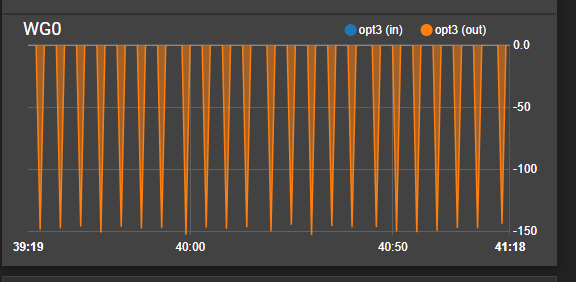
Edit: I notice without a client connect, consistent traffic is sent out of the WG0 interface.
-
@Tenorbro That's normal. Do a packet capture on the interface and you'll see what it is.
So you had no rules on the WG interface? That would be the problem. You can fine tune the rules there just for WG clients if needed.
-
@Jarhead Thank you. As a follow-up question, I've watched several videos where the Assignment is not specified for the interface configuration. If the WG0 interface is not specified, will it still not work? In other words, does the interface assignment need to always be assigned?
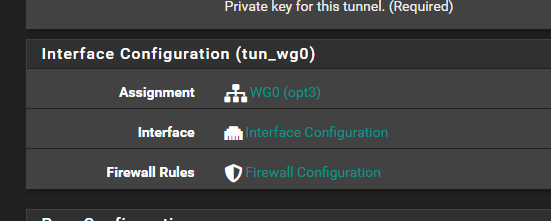
https://docs.netgate.com/pfsense/en/latest/recipes/wireguard-ra.html#firewall-rules
-
@Tenorbro It does not need to be assigned but that changes the rules. You would then not have a discreet interface to put rules on and only use the Wireguard group for rules. This could be problematic if you have a few tunnels so it's easier to assign an interface just because of the rules.
This also depends on the WG setting "Interface Group Membership".