Setting ip VPN with release 2.7.2
-
I'm trying to setup a basic VPN connection. When makeing an connection from the client there is always the TLS Error: TLS key negotiation failed. Check your network connection.
I can see that udp connection is being formed because in the logfile off the VPN server this is recorded:
Jun 2 14:58:55 openvpn 86674 I/O WAIT status=0x0020
Jun 2 14:58:55 openvpn 86674 MULTI: REAP range 16 -> 32
Jun 2 14:58:55 openvpn 86674 SCHEDULE: schedule_find_least NULL
Jun 2 14:58:55 openvpn 86674 PO_CTL rwflags=0x0001 ev=6 arg=0x002ce6d8
Jun 2 14:58:55 openvpn 86674 PO_CTL rwflags=0x0001 ev=5 arg=0x002cd6a4
Jun 2 14:58:55 openvpn 86674 PO_CTL rwflags=0x0001 ev=4 arg=0x002cd6a8
Jun 2 14:58:55 openvpn 86674 PO_CTL rwflags=0x0001 ev=10 arg=0x002cd6ac
OpenVPN config file:
dev tun
persist-tun
persist-key
data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC
data-ciphers-fallback AES-256-CBC
auth SHA256
tls-client
client
resolv-retry infinite
remote 184.125.xx.xx 1194 udp4
nobind
verify-x509-name "open_vpn" name
auth-user-pass
pkcs12 pfSense-UDP4-1194-Marcel.p12
tls-auth pfSense-UDP4-1194-Marcel-tls.key 1
remote-cert-tls server
explicit-exit-notify
I'v set up a Certificate Auth: Internal_cert_Auth
There is a OpenVPN_cert1 that is inuse for the OpenVPN Server
There is a user certificate: cert_van_Marcel as a user certificate.14:58:55 openvpn 86674 PO_CTL rwflags=0x0001 ev=6 arg=0x002ce6d8
This error message looks like the openVPN server is using a client certificate instead of a server certificate.Question: how can I solve this problem?
server_Config_OpenVPN.xml -
@Roko59 said in Setting ip VPN with release 2.7.2:
Question: how can I solve this problem?
Start from scratch.
Use this less then 8 minutes official guide : Configuring OpenVPN Remote Access in pfSense Software.
It will work.Make changes from there. Step back when things start to 'break'.
-
Dear Gert-Jan,
This is a good tip; I removed everything that has something to do with the VPN, even the certificates..
Unfortunately this also doesn't work.
it ended up in to the errror message:
Sun Jun 9 15:26:21 2024 OpenVPN 2.6.7 [git:v2.6.7/53c9033317b3b8fd] Windows [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] [DCO] built on Nov 8 2023
Sun Jun 9 15:26:21 2024 Windows version 10.0 (Windows 10 or greater), amd64 executable
Sun Jun 9 15:26:21 2024 library versions: OpenSSL 3.1.4 24 Oct 2023, LZO 2.10
Sun Jun 9 15:26:21 2024 DCO version: 1.0.0
Sun Jun 9 15:26:33 2024 TCP/UDP: Preserving recently used remote address: [AF_INET]84.25.144.32:1194
Sun Jun 9 15:26:33 2024 UDPv4 link local: (not bound)
Sun Jun 9 15:26:33 2024 UDPv4 link remote: [AF_INET]xx.xx.xx.xx:1194
Sun Jun 9 15:27:33 2024 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Sun Jun 9 15:27:33 2024 TLS Error: TLS handshake failed
Sun Jun 9 15:27:33 2024 SIGUSR1[soft,tls-error] received, process restartingThis is very strange because i made several VPN (sit to site en client to site) connections with OpenVPN using FreeBSD 11 and 12. Now I want to use Pfsense because of the (graphical interface) and the standardisation.
pftop looks like all traffic is being blocked by the pfsense firewall:
udp In 84.28.110.177:58813 192.168.1.1:1194 NO_TRAFFIC:SINGLE 00:00:16 00:00:24 11 462
udp Out 84.28.110.177:58813 192.168.1.1:1194 SINGLE:NO_TRAFFIC 00:00:16 00:00:24 11 462
What could go wrong then? Because configuring OpenVPN is pretty strait forward..Any help would be very welcome because debugging this problem is not easy..
-
@Roko59 said in Setting ip VPN with release 2.7.2:
Windows version 10.0 (Windows 10 or greater), amd64 executable
OpenVPN 2.6.7 [git:v2.6.7/53c9033317b3b8fd] Windows ....
Windows version 10.0 (Windows 10 or greater), amd64 executableExplain de windows executable on a Freebsd system.
I understood that you want to set up a OpenVPN server.
Not a client (on pfSense)@Roko59 said in Setting ip VPN with release 2.7.2:
pftop looks like all traffic is being blocked by the pfsense firewall:
You have a WAN firewall rule like this :
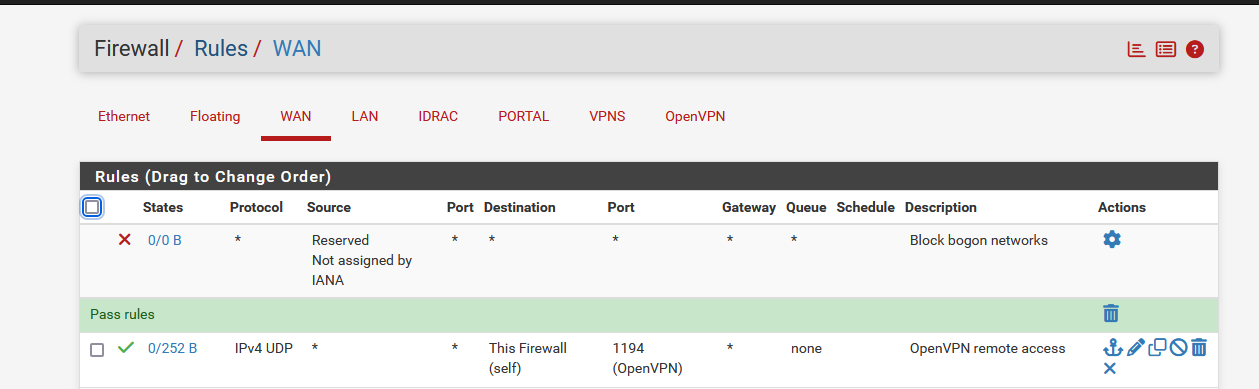
traffic counters, under 'States' show you when the rules is matched = used. If they stay 0/0 the traffic never reached the pfSense WAN interface.
-
Windows version 10.0 (Windows 10 or greater), amd64 executable
OpenVPN 2.6.7 [git:v2.6.7/53c9033317b3b8fd] Windows ....
Windows version 10.0 (Windows 10 or greater), amd64 executableExplain de windows executable on a Freebsd system.
I understood that you want to set up a OpenVPN server. > this is correct. the OpenVPN server is executed on the pfsense Firewall.
Not a client (on pfSense)The client is running the OpnVPN client on a Windows 10 notebook.
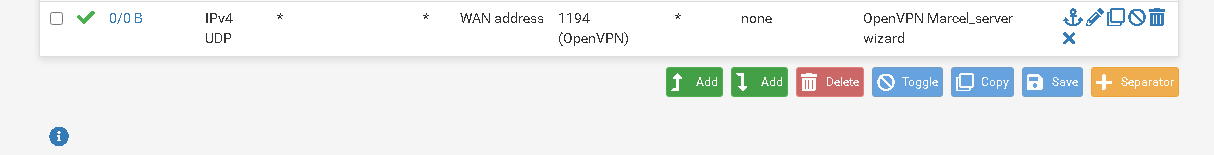
This rule is added by the wizard.
Now I changed the destination address from WAN Address to "This Firewall(self).
The traffic counter stays on 0. the error message is still the same.
pftop is displaying als the same message.
So the firewall is blocking all the VPN traffic.I think about resetting the whole firewall and starting over again.
Adding a new netwok interface is also the cause of new problems: DHCP is not working on this interface. So ther are more problems with this PFsSense installation.
Thank you for your help sofar! -
@Roko59 said in Setting ip VPN with release 2.7.2:
I think about resetting the whole firewall and starting over again.
Wrong. I mentioned the issue already. It's not pfSense !!
This :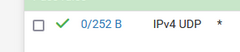
means : no traffic ever reaches pfSense.
Consider this : even if there are some settings wrong with your OpenVPN pfSEnse server, traffic will still reach your WAN IP, using port 1194, protocol UDP. So the counters (States) will indicate that : they will rise.
Yours don't. So, again traffic doesn't reach your pfSense WAN port.What is in front of pfSEnse ? An ISP router ? (and by consequence your WAN IP is RFC1918) In that case : you need to put a NAT rule in place in that router.
@Roko59 said in Setting ip VPN with release 2.7.2:
Adding a new netwok interface is also the cause of new problems: DHCP is not working on this interface. So ther are more problems with this PFsSense installation.
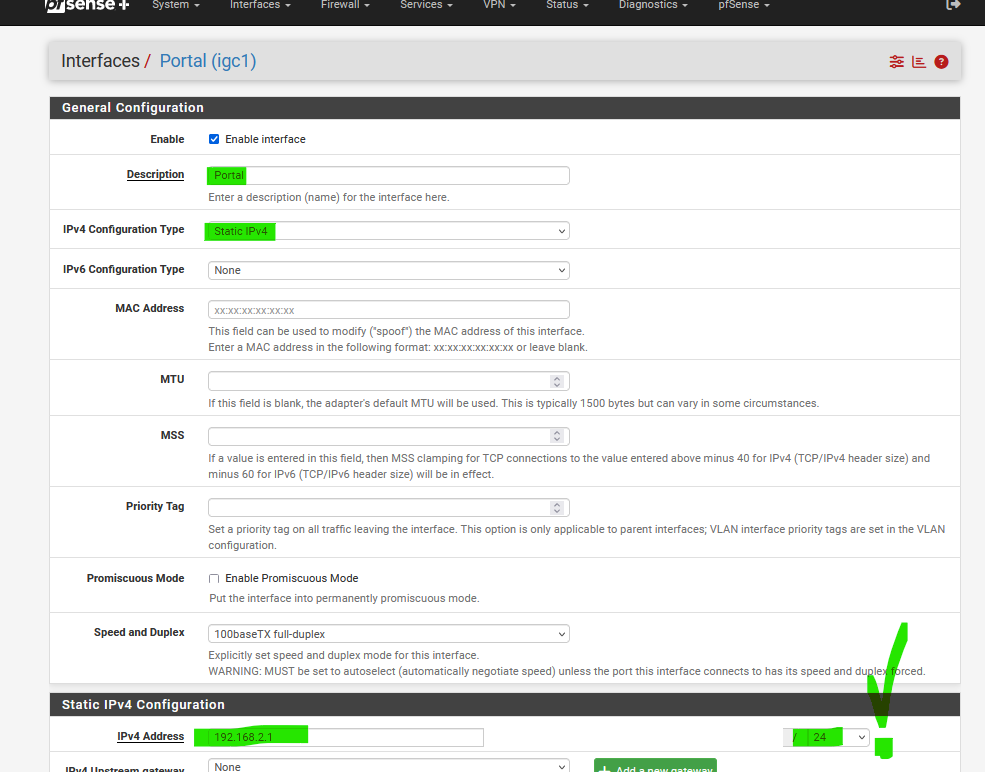
Another interface :
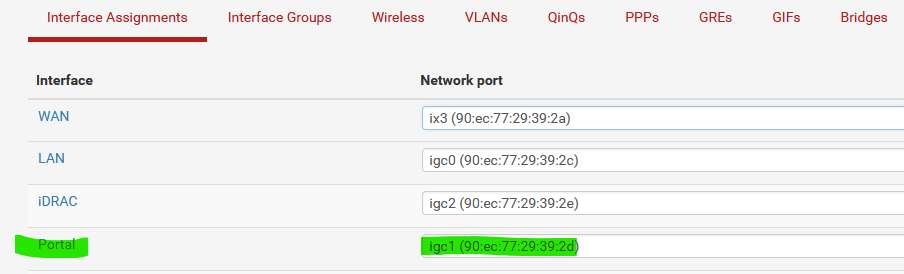
Instead of keeping OPT2, I called mine "Portal".
AN IP addresses, and a /24 ( !! ) network :
Activate DHCP :
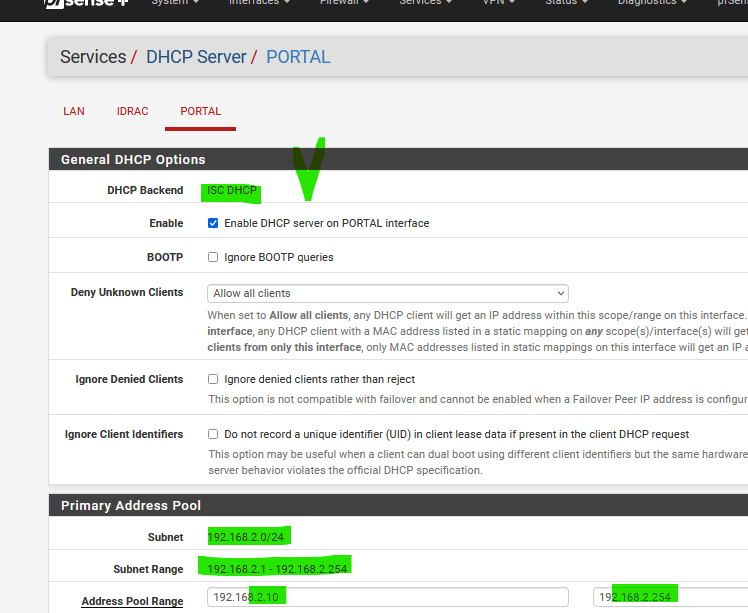
and nearly done.
Add a pass-all firewall rule on the OPT (Portal) interface :
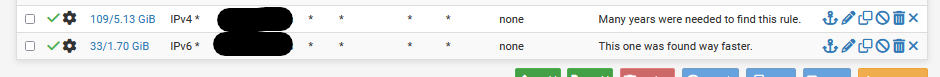
( the black bars are OPT2-subnets or Portal-subnets )
-
Dear Gert-Jan,
There is a bridged router in front of the PfSense so the WAN side of the firewall has the WAN ip-address.
today I see that the counter is no longer zero:
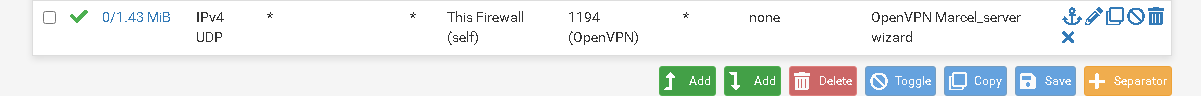
now I try to make a connection with my phone on the 4G network. This is working like charm! Incredible.. So it looks like my ISP is blocking the communication because I made contact with wifi direct to the Wifi router that is connected to the internet. What I don't understand is why is UDP communication displayed in PFTop on the VPN server site? So the server site must see the UDP packets..
I'm confused by this... But the good news is that there's nothing wrong with the VPN server.The DHCP issue is something that I'm going to address tomorrow..
Thank for your help!
-
@Roko59 said in Setting ip VPN with release 2.7.2:
So it looks like my ISP is blocking the communication because I made contact with wifi direct to the Wifi router that is connected to the internet.
You mean : you connect to your VPN while you are already at the site ?
See it like this : when using a plain old telephone (the one with a line) : when at home : call your home number.
To make a long story short : don't do that.
Don't use your own WAN IP while you are connected behind that WAN connection.
More analogy : don't call your front door bell while your at home (well, you can, but it's "strange").@Roko59 said in Setting ip VPN with release 2.7.2:
So the server site must see the UDP packets.
What is a server site ?
@Roko59 said in Setting ip VPN with release 2.7.2:
There is a bridged router in front of the PfSense so the WAN side of the firewall has the WAN ip-address
The device in front of pfSense isn't routing (converting one range of IP addresses to another).
It's just a bridge or 'modem', concerting one type of media, to another.
Like : coax cable to ethernet, or fibre to ethernet, or pots to ethernet. -
Hi Gertjan,
You mean : you connect to your VPN while you are already at the site ? >NO
See it like this : when using a plain old telephone (the one with a line) : when at home : call your home number.
To make a long story short : don't do that. > I know this
Don't use your own WAN IP while you are connected behind that WAN connection.
More analogy : don't call your front door bell while your at home (well, you can, but it's "strange").
No, I'm making connection from another site(this is my home site) to the customer site. My homesite router is blocking acces to the VPN server at the client site. So this is a pretty normal situation with a not so normal result.
This router is a:
Hardware version : 4.01
Software version : CH7465LG-NCIP-6.15.32p3-NOSH
MAC-adres : 54:67:51:D3:A7:19
Serialnumber Connect Box : DDAP62010E3E
This router is configured with a DMZ. When I make contact to this router with Wifi I have normal fast internet but I cannot make a VPN connection.
In the DMZ I configured a PfSense firewall: I cannot make a VPN connection.
Do have any idea where to search? Because when I make a VPN connection with my phone on the 4G network there is no problem..What is a server site ? > this is OpenVPN server site(the client site)