Remote Log DNS Reply
-
@Lockie This is one of the very large downsides to pfSense DNS. There is no “good” way to get proper DNS logging of replies.
On the one hand you can get Unbound to log replies in the resolver.log (and syslog to remote) by setting log-replies:yes in advanced settings. But that doesn’t log that actual IP addresses of the answer, only the name, so not really usefull for correlation lateron.
On the other hand you can get pfBlockerNG to log replies - in it’s own logfile. But this is done in a horrible format, and you cannot natively syslog it off to a remote host. You can then install the syslog-ng package and have that monitor the reply.log file, but pfBlockerNG rotates log files the wrong way, so at every rotate you will have all loglines replayed again to your syslog server.
There is no single good solution on what everybody wants:
Remote syslog - in standard syslog format - of DNS replies that includes the IP addresses given in the response. -
@keyser said in Remote Log DNS Reply:
. But that doesn’t log that actual IP addresses of the answer, only the name, so not really usefull for correlation lateron.
This should be changing once unbound reaches 1.20, if reading the updated doc correctly, not sure what version in 24.03? I know 1.20 is not in 23.09
https://nlnetlabs.nl/documentation/unbound/unbound.conf/
log-replies: <yes or no>
Prints one line per reply to the log, with the log timestamp and
IP address, name, type, class, return code, time to resolve,
from cache and response size. Default is no. Note that it
takes time to print these lines which makes the server (signifi-
cantly) slower. Odd (nonprintable) characters in names are
printed as '?'. -
@johnpoz Unbound is at v1.19 in 24.03, but unfortunately I think you are incorrect. Your text snip is exactly identical to the 1.xx help files of Unbound, and the IP address they reference in the text is the IP of the client making the query. That goes into the log file. But the logfile does not contain the IP address(es) of the name asked in the response
-
@keyser Its possible yeah.. But when I looked at the current documentation it seemed different to me, like they were adding the answer IP..
But logging what is the actual reply sent to the client is normally not logged to be honest..
-
K I'm a bit confused as to if it is or is not possible. I was hoping there might be a written up guide on how to if it was possible.
I think ideally I'd like it if I only logged certain local IPs and there DNS replys. To keep the logs smaller and more focused.
-
@Lockie You can log queries and replies.. But yeah I believe Keyser is correct that it doesn't log what was the IP returned to the client..
Lets say 192.168.1.100 asks for www.domain.com, you will see that they got a reply for www.domain.com and it was say an A record, etc. but you won't see for example that the answer was IP 1.2.3.4..
-
@Lockie Yeah, its not possible straight up to have it logged to a remote server. The best you can achieve is ask pfBlockerNG to do reply logging. That will record what you are looking for - but only to a local logfile.
To me it seems quite logical to want the DNS reply IP addresses logged as well. That way you can correlate “near real time” IPFIX flow data to what DNS names the client requested to inititate that session. Without the IP, your SIEM could try and reverse lookup the IPs in flow data (not really working AT ALL), so that leaves having the siem do all the DNS requests again when enriching the flowdata for a client, and then Round Robin DNS or other distributed host resolution methods becomes a HUGE problem - leaving IPs in flow data that cannot be correlated.
-
@keyser this part
"Lets say 192.168.1.100 asks for www.domain.com, you will see that they got a reply for www.domain.com and it was say an A record, etc."
Is all I want. I'm not interested in the IP of the domain. If I've understood correctly.
-
@Lockie Okay - sure. That is intirely possible:
In SERVICES -> DNS RESOLVER under custom options add:
This will add DNS replies in your resolver.log. You can syslog that to a remote host using the built in syslog feature in the pfSense log setup (STATUS - SYSTEM LOG -> SETTINGS)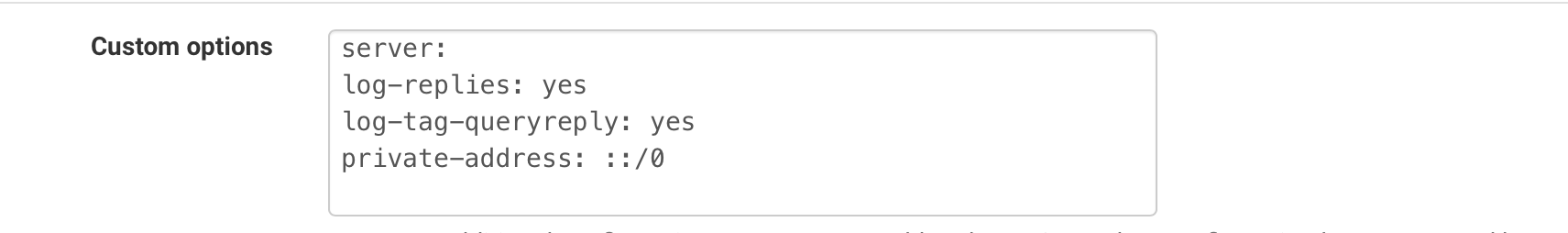
You do not need the pivate-address part. Thats in mine to prevent response and logging of IPv6 names (I’m IPv4 only)
-
@Lockie said in Remote Log DNS Reply:
"Lets say 192.168.1.100 asks for www.domain.com, you will see that they got a reply for www.domain.com and it was say an A record, etc."
Another approach.
Install and activate pfBlockerng.
No need to add any DNSBL or IP feeds.From now on :
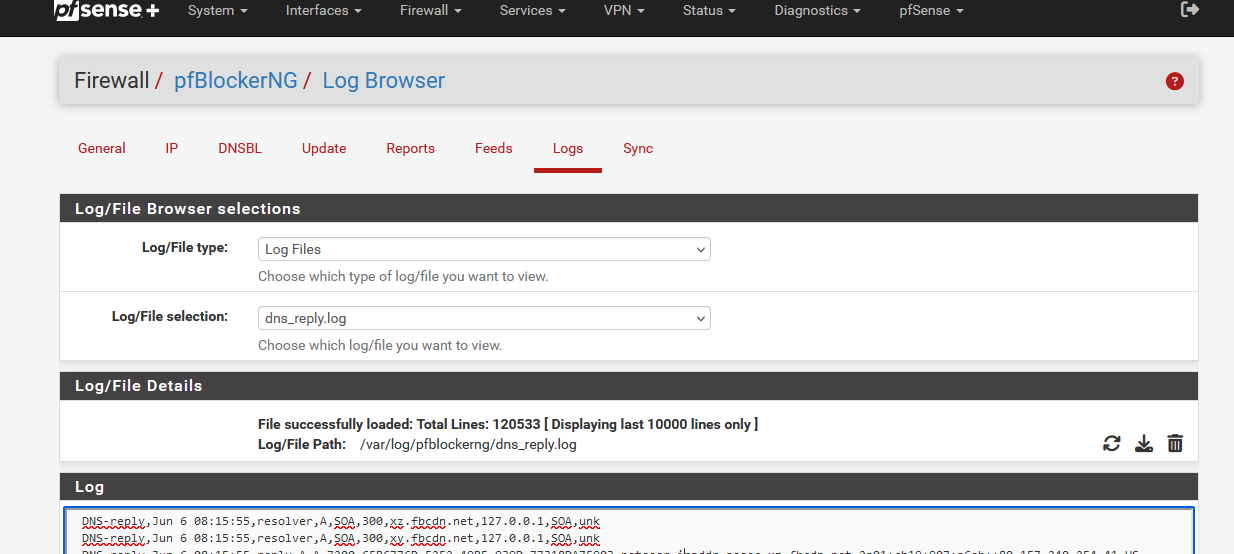
This dns_reply file contains info like :
DNS-reply,Jun 6 08:16:09,cache,A,A,3125,devices.liveradio.fr,192.168.1.124,90.84.243.75,FRThe device 192.168.1.124 was asking for the A record of "devices.liveradio.fr" and it got back, from the cache, "90.84.243.75".
As pfBlockerng is 100 % open source, it won't need rocket science to add to the place where lines are added to this /var/unbound/var/log/pfblockerng/dns_reply.log file so it also send out to the local syslog, the one you've set up to also do remote logging to a remote syslog server.
edit : humm. @keyser solution seems simpler

-
@keyser out of interest, would this have negative performance impacts in any significant way?
-
@Lockie the logging of replies and or queries would put a hit on the overall performance of unbound. But to be honest unless you doing a crazy amount of dns - I mean crazy amount I don't see how it would be of concern.
Generally speaking, dns is not an overall resource intensive sort of thing.. Even in an enterprise with 1000s of clients I don't see how it could be much of an issue.. Now if you got something going bat shit insane with the amount of queries its doing... My alexas lost their minds when the internet was out for a bit, and they had done millions of queries each in less than 24 hours.. Unbound was still answering.. But glad I wasn't logging all of those ;)
-
@johnpoz K thank you thats good to know.
-
Currently struggling to setup remote log receiving on my NAS :( grr, I don't appear to be getting anything into my Synology NAS in terms of the logs I setup on pfsense. Here are the NAS settings:
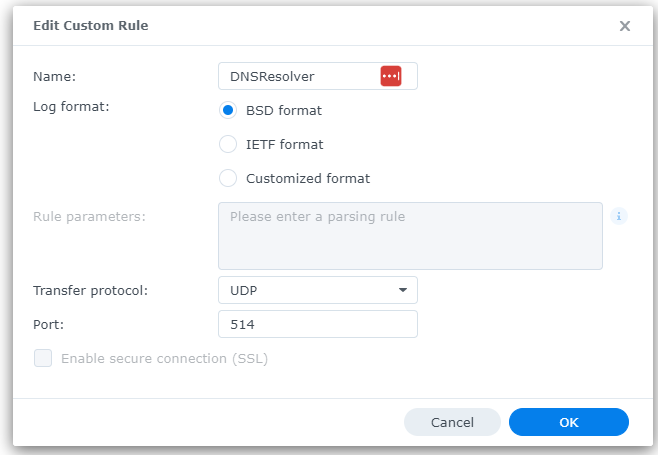
Here is pfsense:
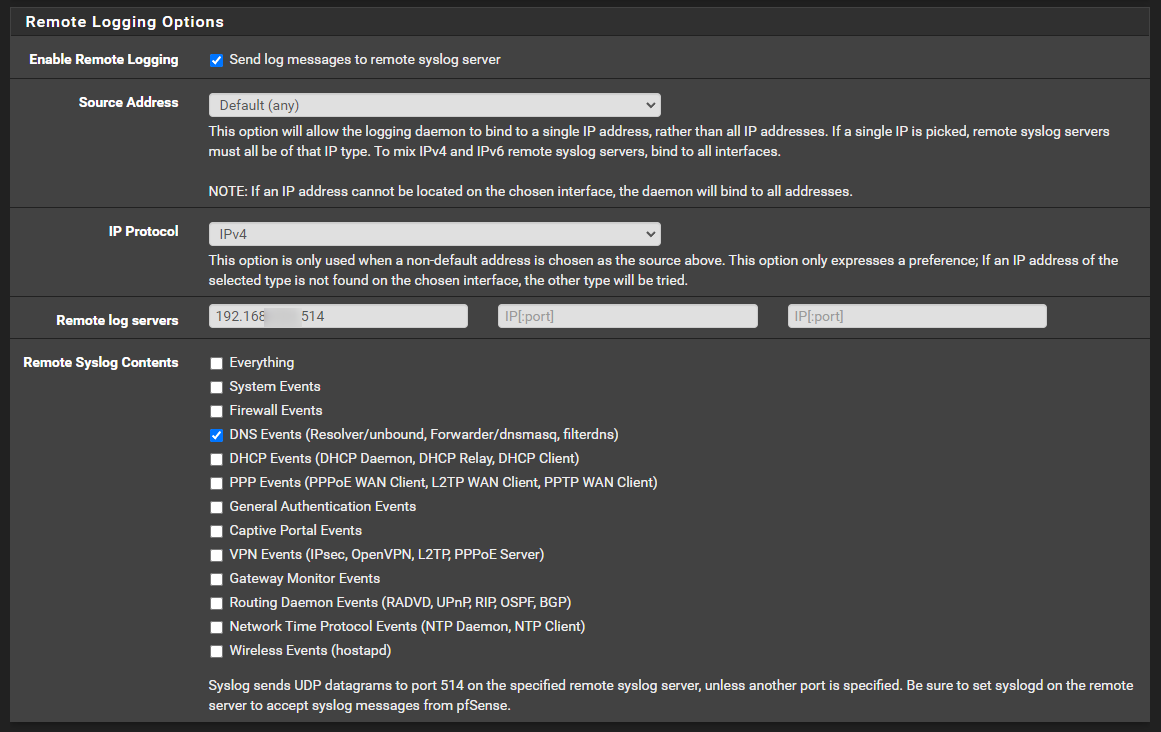
See anything obviously wrong?
-
@Lockie I just turned on logging to my nas.. And seems to be working
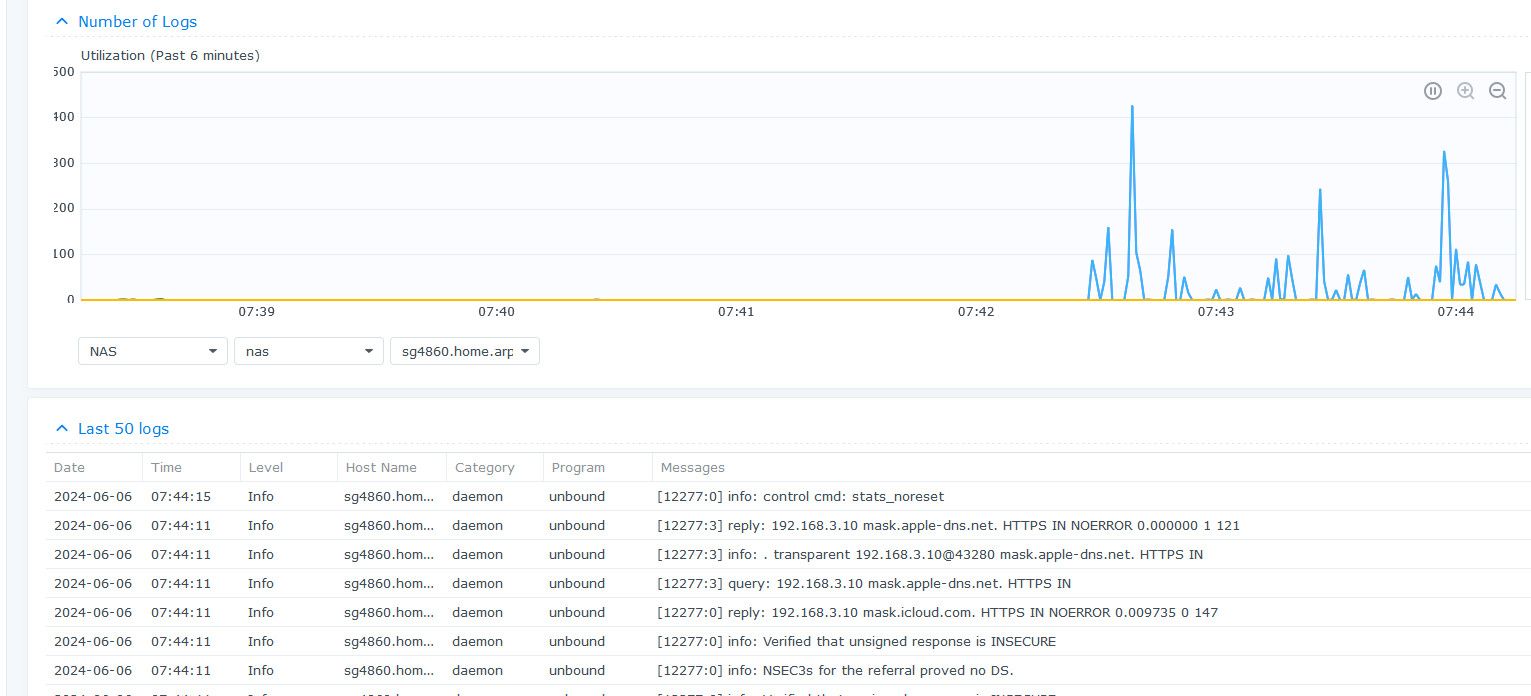
Are you seeing entries in your local log when when you go to logging and pick the resolver?
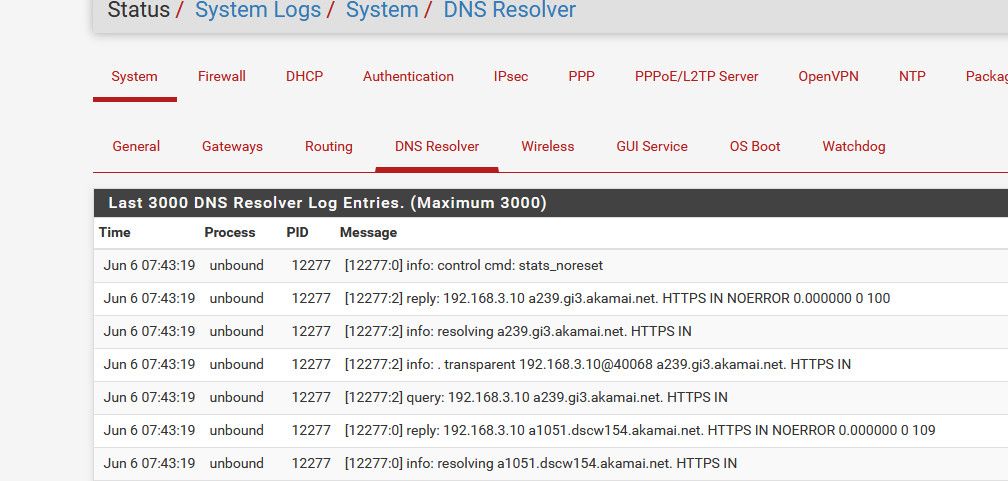
-
I picked 'LAN' as my Syno is on my LAN.
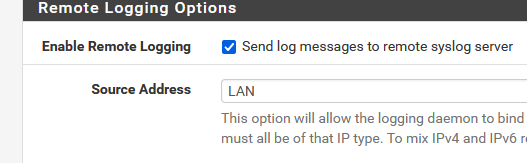
'Any' might seem fine, but what if it decides to use IPv6 ?
Or using another interface ?
I'm not sure, but sure about the fact that the interface is LAN (for me).I added the Syno IPv4 :
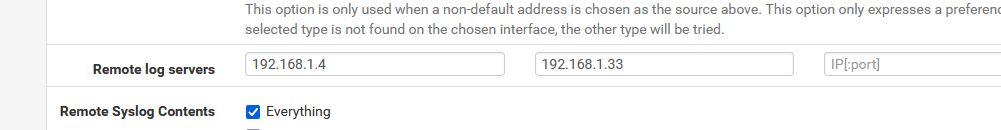
192.168.1.4 is my actual log collector.
I added 192.168.1.33, my Syno.My Syno told me I had to install this first :
The first time adding a "Logs receiving" setup, Syno asked me to assigne a folder to store the logs.
These are my settings :
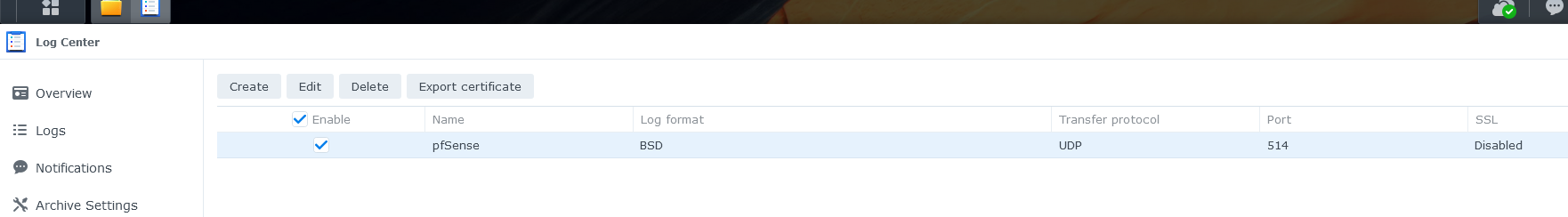
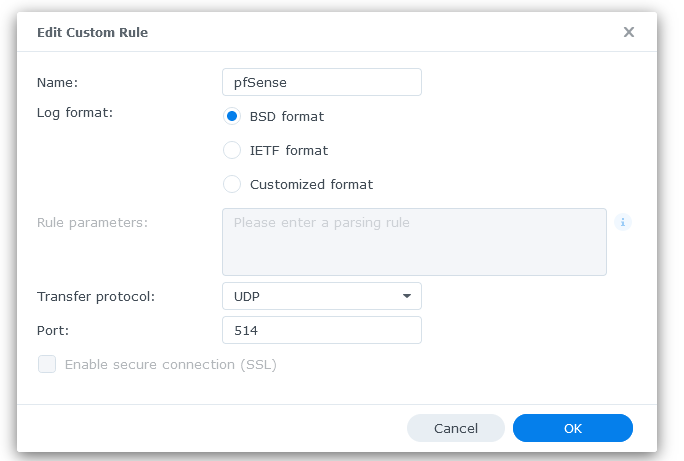
From now on, my Syno start to receive logs from pfSense :
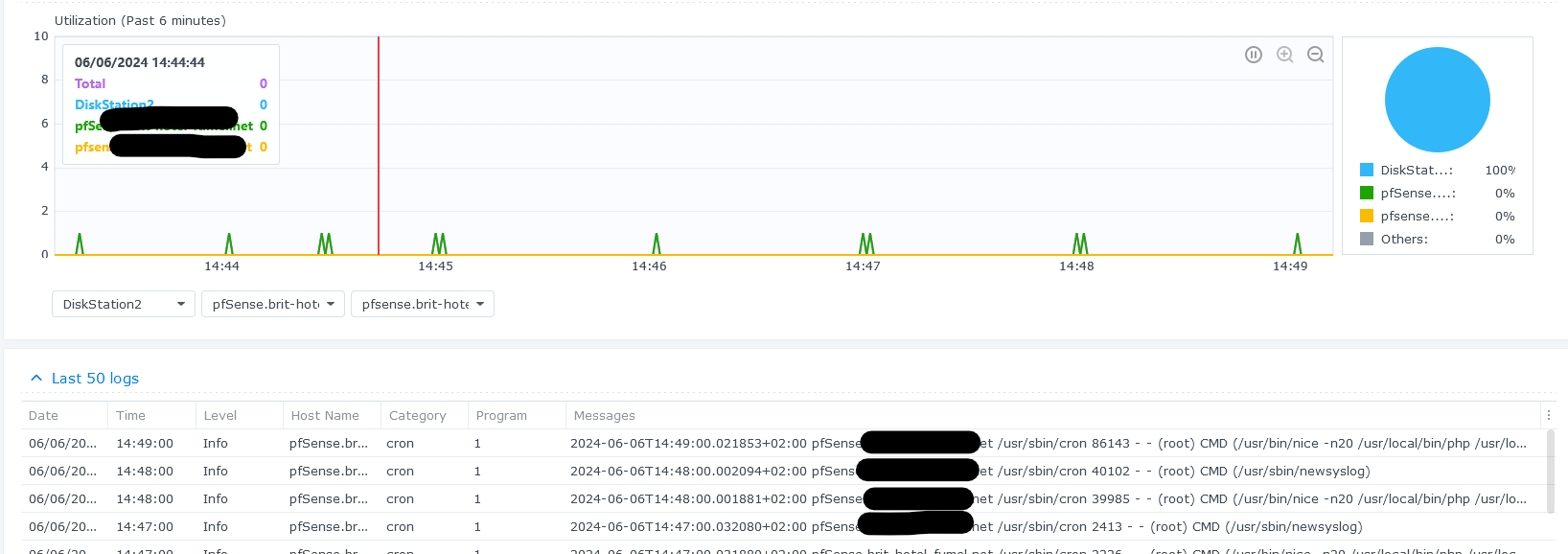
edit #metoo ! it works.
-
Thanks all, you've been so helpful.
Switched it to LAN and I've now go what I needed.
Many Thanks ALL!!!
-
@keyser said in Remote Log DNS Reply:
but only to a local logfile.
Not entirely correct if you are willing .. anything is possible
@johnpoz said in Remote Log DNS Reply:
would put a hit on the overall performance of unbound. But to be honest unless you doing a crazy amount of dns - I mean crazy amount I don't see how it would be of concern.
for the record - I run about 60 clients behind a 2100 and there are no speed issues with dns resolution. I'd like to define crazy
 but at the level of about 10,000/hour I'm not there yet ...one day when I'm feel bored I might load it up and see where it breaks -- just for fun.
but at the level of about 10,000/hour I'm not there yet ...one day when I'm feel bored I might load it up and see where it breaks -- just for fun.This is from my Graylog server and is in real time.
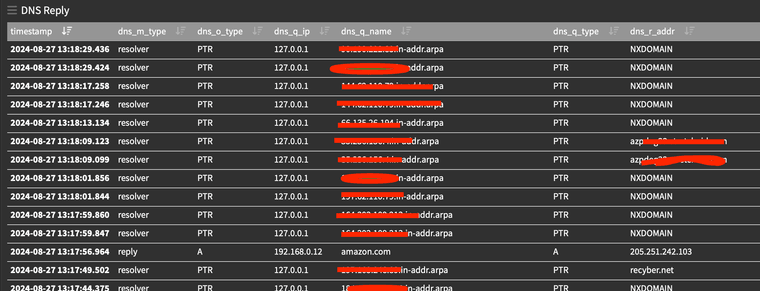
While you are there, may as well grab DNSBL goodies as well.
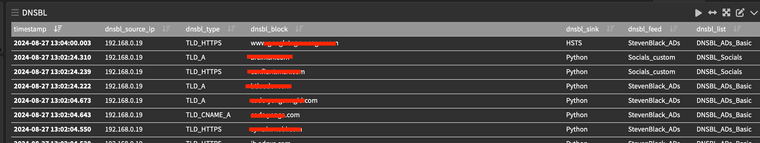
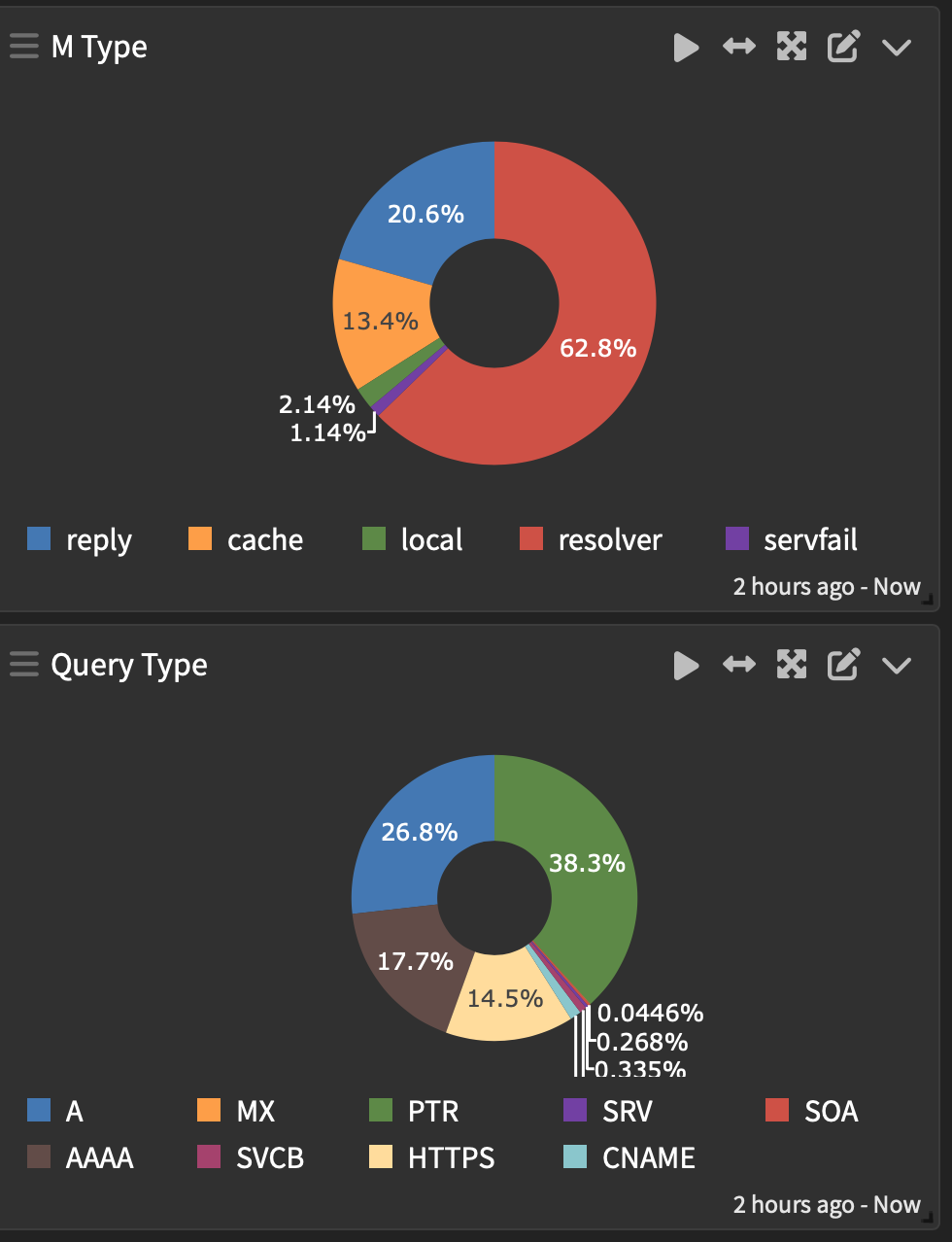
Based on the DNS Reply you can make all kinds of pretty graphs..
May as well grab unified while your at it ..
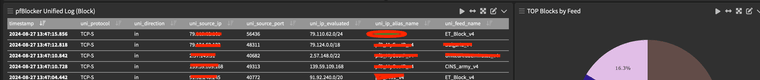
And finally the Synology (we run a small DNS on this device for some "special" use case, and the volume of "hits" is very low, but it is real time and has no issues "Feeding the data to the Graylog". Synology provides no way to send DNS records to another logging server, pretty much everything else but not DNS.. again if there is a will there is a way.
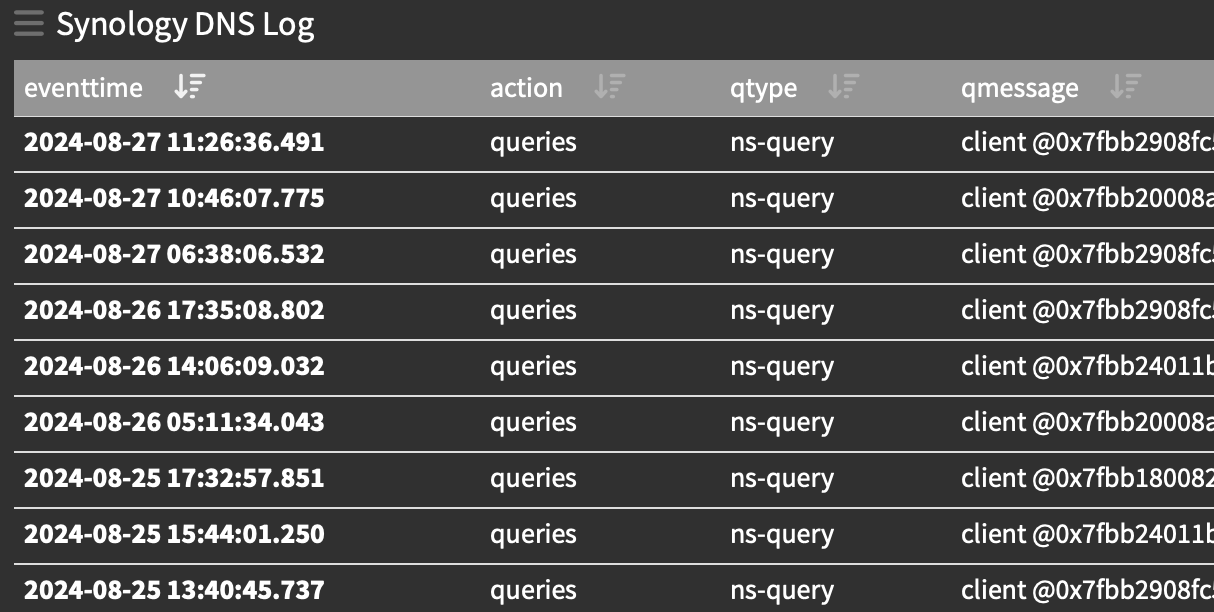
 only / maybe 10 lines or less of code to make the magic happen. I'm okay with that, for accomplishing the goal go logging.
only / maybe 10 lines or less of code to make the magic happen. I'm okay with that, for accomplishing the goal go logging.Bottom line for me is "Can't do that, is simply not an option"
-
@jrey can you share how you are sending DNS data to graylog ?
I've trying to accomplish that without any success.