Replacing unifi usg pro 4 with pfsense vlan issue
-
I currently have a unifi network, consisting of a usg pro 4 router, unifi poe 16 port switch, unifi 6 lite access pointi have 2 vlans setup, 10 cams, and 20 is for iot, which work fine, I am trying to replace the usg router with pf sense...I am having issues with the vlans pulling correct ip subnets, they pull from the default network, 192.168.1.1.... on pfsense, I have created 2 vlans, vlan id 10, is cams, and vlan id 20 is IOT, each vlan was assigned interface, as well as set up on DHCP server, cams subnet is 192.168.10.1, and iot is 192.168.20.1... if I assign a port to iot vlan and connect a device, it wont pull 192.168.20.x address instead, instead pulls 192.168.1.x...from that device I can ping both vlan gateways, 192.168.20.1 and 192.168.10.1.
I don't understand how the device would to connect to the appropriate DHCP server, is it like this , device connects to port, traffic from device is not tagged, hits port is tagged with vlan id of 20 for iot, the router see vlan id and routes to appropriate DHCP server..
Not sure where things are going wrong.. -
@kdy1968 Your issue is not tagging the additional VLANs (10 + 20) correctly on the pfSense downlink and the switch uplink. That might include the switch downlinks to AP’s as well.
In reality you have a “shortcut” where VLAN 10 and 20 are untagged linked to the default VLAN, and thus both see the DHCP server in that VLAN instead.
The fact that you can ping 192.168.10.1 and 20.1 says nothing about the wrong VLAN tagging. That is just pfsense that allows pings (are you using default allow all traffic rule?) recieved from one client in the 192.168.1.x network to the other interface addresses.
-
@keyser thanks for the response, yes im using the default allow all firewall rules, to simply things, i will just work with one vlan iot, which i want a computer attached to port 10 to connect to...
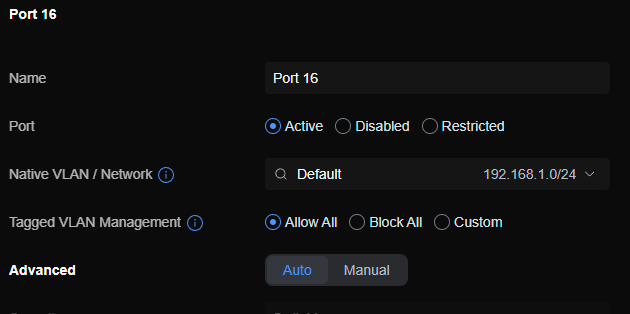
pfsense itself is installed on a minpc with two ports, wan goes to cable modem and lan goes to switch on port 16this is settings for port 10 on which computer connecting to this should be on vlan 20
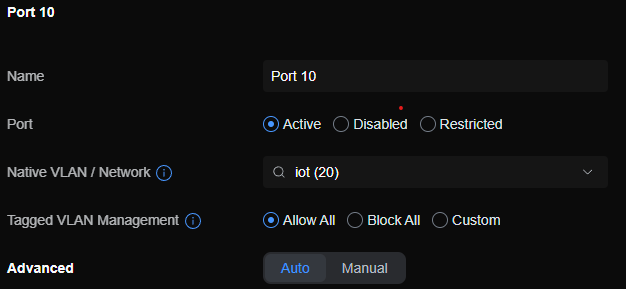
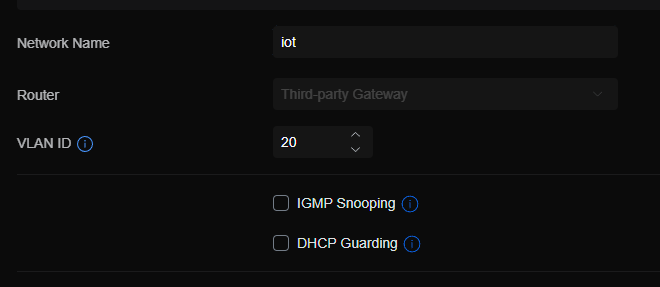
this is the setting for iot network:
port 16 is uplink port to pfsense:
on the pfsense router i created the vlan id...
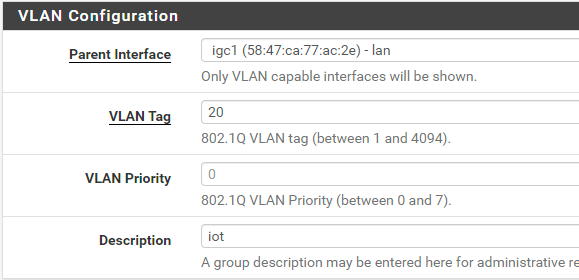
i assigned to a interface, gave it a static ip of 192.168.20.1/24
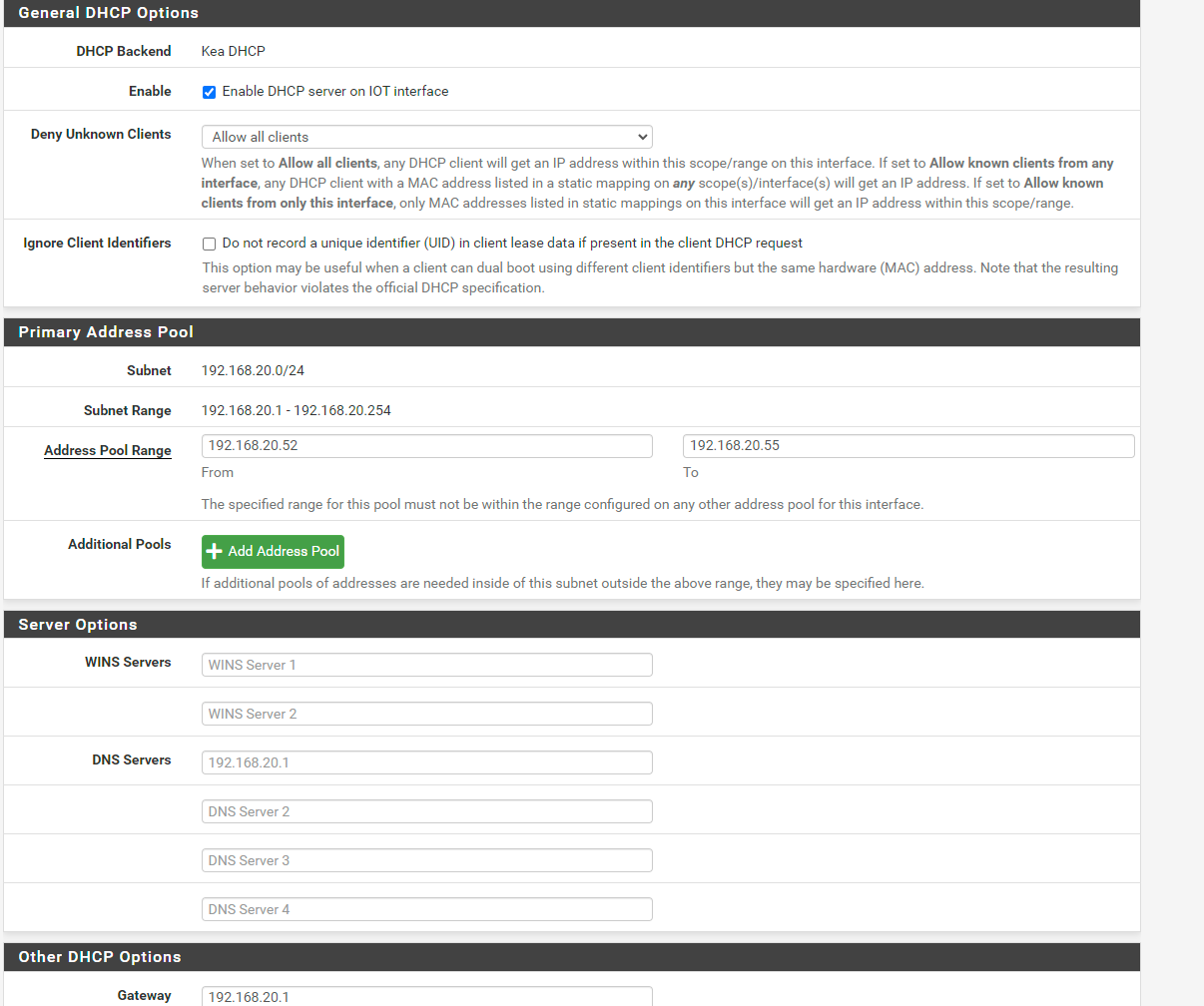
configured dhcp:
firewall rule is set to allow all
lan rules are default
happen to see what i might be missing
-
@kdy1968 I’m not very familiar with Unifi products, but your config does seem to be correct.
However - depending on the client OS on computer your issue might be that you are allowing the other VLAN’s (tagged) on switch interface 10 where the client is connected. That will cause the client to see all broadcasts in the other VLANs (tagged), and I have has many issues with different client OS’es that then still select the PVID marked VLAN in the switch as default.
Make sure to disable “trunking” on port 10, and set it to Access Vlan 20 only. -
@keyser seems like pfense suricata was some how bugged, i turned it off and everything started working turned it back on and everything is still working
-
actually its not working, appears to be a bug with suricata/netmap that breaks vlans, by remove the tag
-
running the following on pfsense shell ifconfig igb0 -vlanhwtag -vlanhwcsum -vlanhwfilter in shell will allow me run run suricata in inline mode, and vlan will still work....you can use the app shellcmd to automatically run the cmd at boot..