Suricata logging
-
Hi,
Is it possible to disable the repeated logging of Suricata from /Status/System/Logs/Firewall/Normal View?
Thanks for help.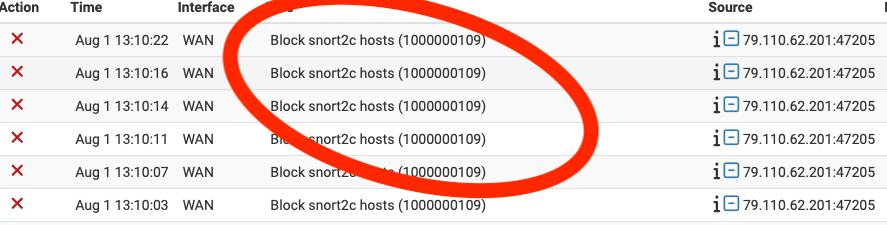
-
You can turn off logging of the hidden default firewall rules on the STATUS > SYSTEM LOGS > SETTINGS tab from the pfSense menu.
You can uncheck the Log firewall default blocks parameter under General Logging Options and save the change. That should remove the entries.
These log messages are not coming from Suricata itself. They are instead generated by the
pffirewall engine as a result of the default snort2c block rule provided by pfSense. All the Suricata package does is place IP addresses in the snort2c table. After that it is pfSense doing the blocking and logging of traffic. -
@bmeeks said in Suricata logging:
generated by the pf firewall
Thanks for reply.I don't want to disable the default blocks of the Log firewall :). I just want to disable entries from suricata.
I understand that it is generated by the pf firewall etc.
I have mini ddos from a couple of ips. I am resizing the table but there is a lot of entryes from these ips. It is not so comfortable because it is 10k entries from one IP. Hosting provider ignore emails. Still no help from CSIRT. The only other option is the police :). -
@Danil-0 said in Suricata logging:
I just want to disable entries from suricata.
Unfortunately there is no way to do that within the GUI. You could modify the pfSense PHP code that generates and loads the
pfrule for snort2c and turn off logging for that rule, but that requires modifying code in pfSense itself. And such a change would be overwritten with the next pfSense update.Not sure what you mean by "resizing the table". Are the blocked IP addresses changing? All I see in the log snippet you posted is the same IP address. That will not consume any extra space in the snort2c table. There will be just a single entry for each unique IP address entered. So, the 79.110.62.201 IP address will only consume a single entry in the snort2c table no matter how many times it results in a logged block. Or stated another way, the only time the number of entries in the snort2c table would grow is when different IP addresses get blocked.
-
@bmeeks said in Suricata logging:
@Danil-0 said in Suricata logging:
I just want to disable entries from suricata.
Unfortunately there is no way to do that within the GUI. You could modify the pfSense PHP code that generates and loads the
pfrule for snort2c and turn off logging for that rule, but that requires modifying code in pfSense itself. And such a change would be overwritten with the next pfSense update.It is not a solution.
Not sure what you mean by "resizing the table". Are the blocked IP addresses changing? All I see in the log snippet you posted is the same IP address. That will not consume any extra space in the snort2c table. There will be just a single entry for each unique IP address entered. So, the 79.110.62.201 IP address will only consume a single entry in the snort2c table no matter how many times it results in a logged block. Or stated another way, the only time the number of entries in the snort2c table would grow is when different IP addresses get blocked.
I mean firewall Log Rotation Size because It is not possible to view logs from Pfsense on the GUI for the last cca 10 hours, only through the terminal.
Anyway, Thanks for the explanation.
-
@Danil-0: just to be clear you understand --
The snort2c table is a construct that is provided by the pfSense code. It is not created by the Suricata package. In fact, the construct was originally created from what I can surmise to support the Snort package. pfSense creates a few special
pftables during initialization of the firewall rules. It creates snort2c for the IDS/IPS packages and a similar clamav entry for the anti-virus packages. Thosepftables are destination targets for sending IP addresses which the firewal should block. The pfSense code considers the rules creating and supporting those tables as part of the built-in defaults. Therefore the logging for those rules is controlled by the option I posted earlier.If you want that changed, you could create a Feature Request on the pfSense Redmine here: https://redmine.pfsense.org/projects/pfsense. Just be clear on any feature request that what you really want is the ability to selectively enable or disable logging for each of the default firewall rules (or at least for those default rules targeting a
pftable). If you just mention Suricata logging, the request is likely to get misrouted or be misunderstood. As I mentioned in my first post, the logging by that rule is not something the IDS/IPS packages can control. It requires changes within the base pfSense code that generates the default firewall rules. -
@bmeeks
 Thanks for help.
Thanks for help.