NordVPN Client - not working
-
Hello community,
I am following the journey into making pfsense do everything the older router could do, only better :)
The idea is to connect users in my network to NordVPN and apply a Kill-Switch. I followed this guide from Lawrance:
https://www.youtube.com/watch?v=ulRgecz0UsQ
As well as the instructions from NordVPN for pfsense 2.5:
https://support.nordvpn.com/hc/en-us/articles/20382523899281-pfSense-2-5-Setup-with-NordVPNThe client connection seems to be working fine. Here I had to rely mostly on the NordVPN instruction, since Lawrance was configuring PIA. The only thing I adopted from Lawrance was the "Don't pull routes" option. I checked that one, despite NordVPN telling me not to.
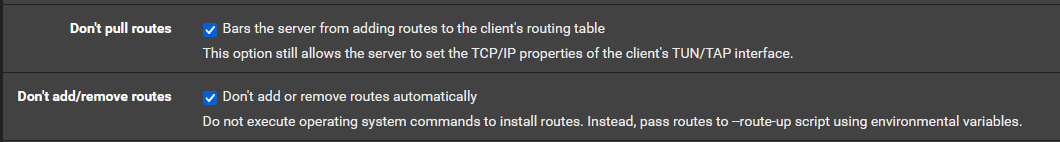
The rest of the NordVPN config I ignored, because they are changing DNS settings and making the whole router divert all traffic through their service, which is obviously not my intention.
So I follow Lawrance into his changes to NAT and Firewall Rules.1- I assigned the Interfaces. Easy enough.
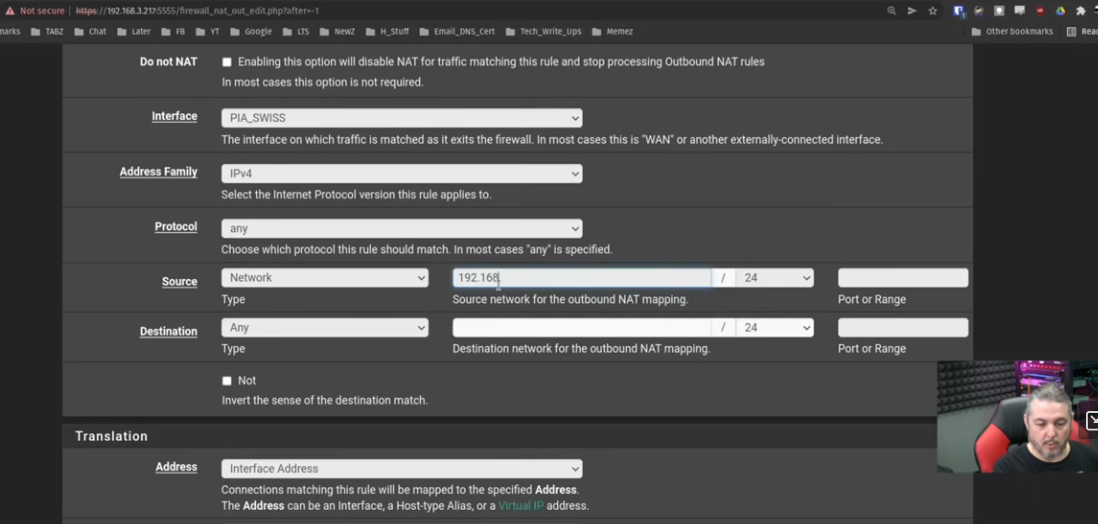
2- Then I configure the outbound NAT Rule.
I am configuring it like Lawrance for an entire Subnet (192.168.22.0/24), which is the subnet of a VLAN in my network.
The screen from Lawrance shows the Translation Address as "Interface Address" and I don't have this option. And to be very honest I am not understanding what this rule does. I used WAN Address instead, as it was the default. But I would love for someone to explain that one for me.
3- I then use the Firewall Alias and single out one user in that subnet for testing purposes. That was easy as well.
4- Now the Firewall Rule. I set the Rule on the VLAN Interface of that subnet I mentioned (192.168.22.0), since this is the subnet that has the one client that should go through NordVPN. But here I get some questions:- IPv4+IPv6: I am setting the rule to v4 and blocking v6, since the interface is configured for both, works on both, and the NordVPN connection is only for IPv4. Otherwise I imagined the user could go through my IPv6 gateway and avoid the NordVPN connection. I added a TAG like Lawrance does.
From my point of view this should be ok.
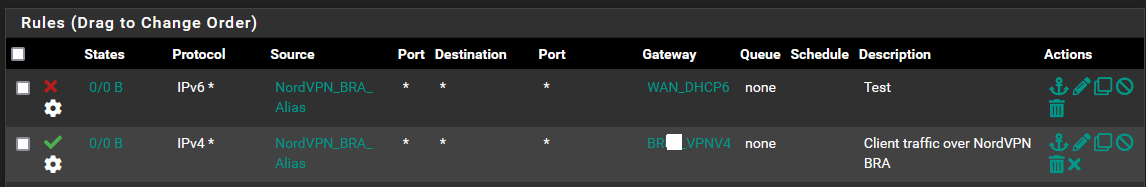
5- At last I create the Floating rule to block everything on WAN with that TAG.
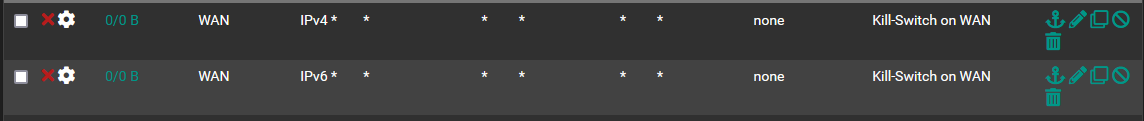
What happens in the end is a total failure. Absolutely nothing worked as supposed.
That client defined by the Alias still goes into the Internet through the default gateway, not NordVPN. And since that is the case, I would expect the Kill-Switch to kill it, but it does not. -
@br8bruno Try killing the firewall states.
Get it working without the kill switch first as its doesn't look right as it's not Quick.
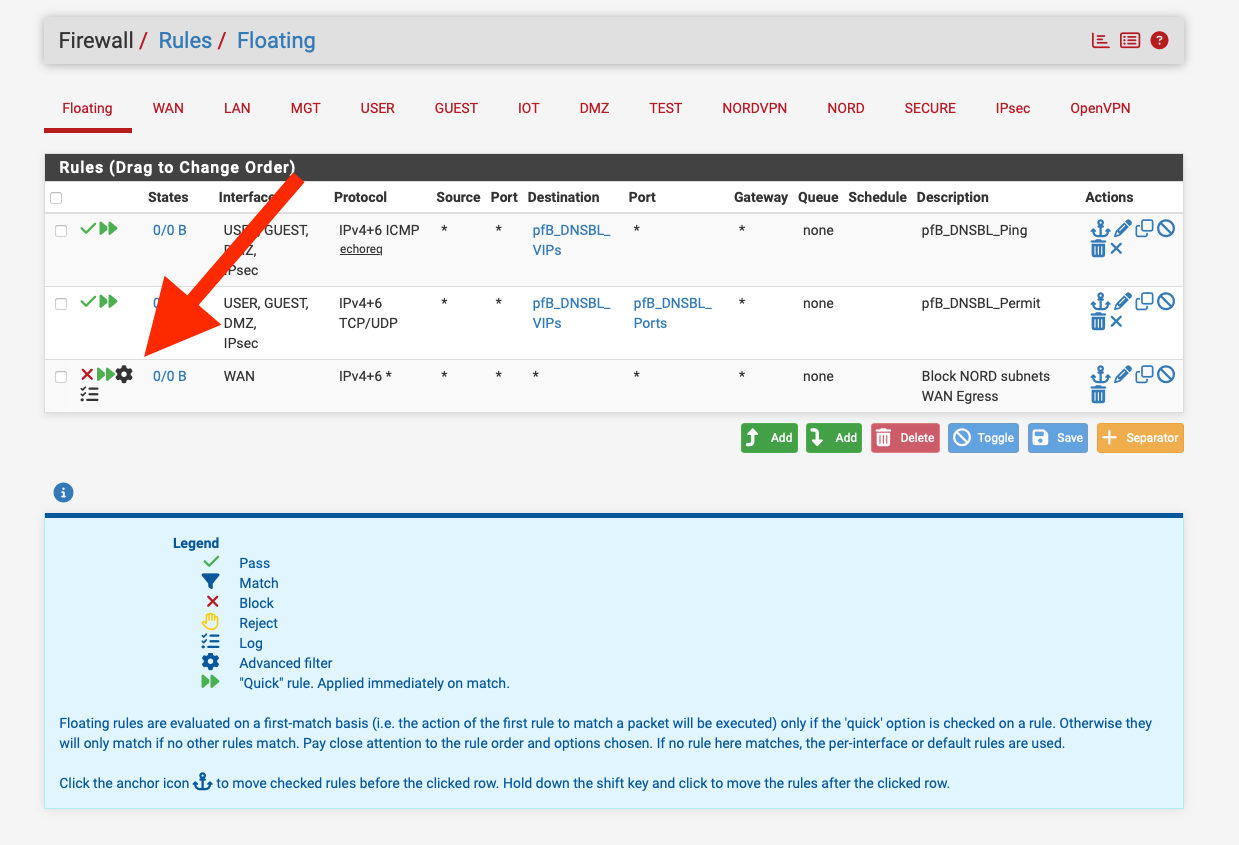
I'd also remove the IPv6 stuff, I don't think Nord support it.
Also having two Nord connections is asking for trouble as they quite often hand out the same IP address to clients from different OVPN servers.
-
Ok, thanks! Killing the states worked. I also corrected the NAT Rule changing the "WAN Adress" to "Interface Adress", being "Interface" the name of the Interface I created for that VPN connection.
I implemented the Killswitch now and it also seems to work.BUT, and this is a big BUT... things got messed up with IPv6 and the second VPN connections.
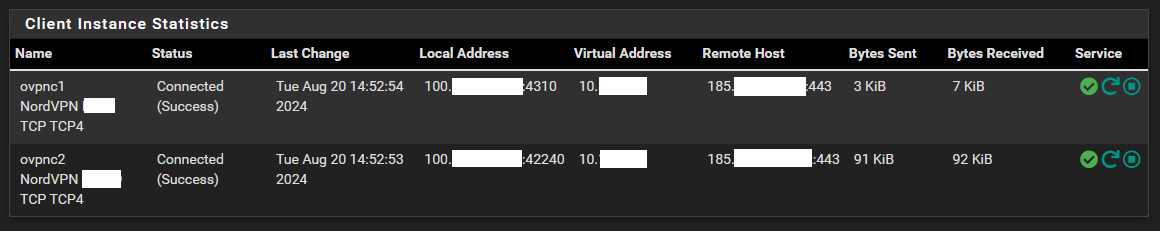
So I first took one user from VLAN2 and told it to go through the NordVPN Brazil server Gateway. And that worked.
Then I took another user from VLAN1 and told it to go through the NordVPN Germany server Gateway. But it also goes through the Brazil server, not the Germany server.
Both connections are up and they receive different IPs from NordVPN. But the Virtual IP for both is the same.
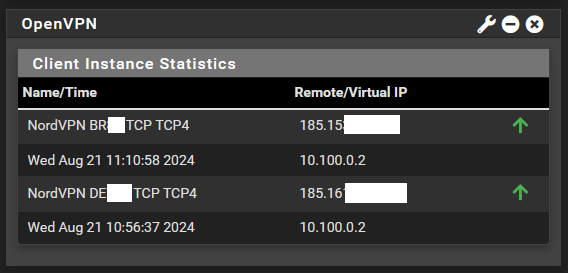
It seems like this is a NordVPN problem and it has no solution, according to this link I could find:
https://www.reddit.com/r/PFSENSE/comments/1clbgfw/multiple_open_vpn_clients_same_vpn_provider/
This kind of makes NordVPN a no-go for me and I will change provider. -
Now a different post for the IPv6 problem.
I got traffic going through the VPN for at least one of the servers as I described above.
But NordVPN handles only IPv4. All rules are made for IPv4. And I removed everything IPv6 as suggested above for troubleshooting.Now, as I expected, I have 2 pathways to internet on the same device.
When I connect to a IPv6 service it sends me through my ISP. When I connect to a IPv4 service, then it connects me through the NordVPN Brazil server.
In my understanding this is a privacy risk and it defeats the purpose of the VPN. -
Is the "NordVPN intercepts all my DNS" issue been resolved ?
See the other Nord/DNS thread, a while ago. -
To be honest I don't know how to even check which DNS are being used and if I am having this issue. I will try to research more on the topic.
Nonetheless I did not configure NordVPN as per their tutorial completely. All DNS configurations I left without.
Here they are: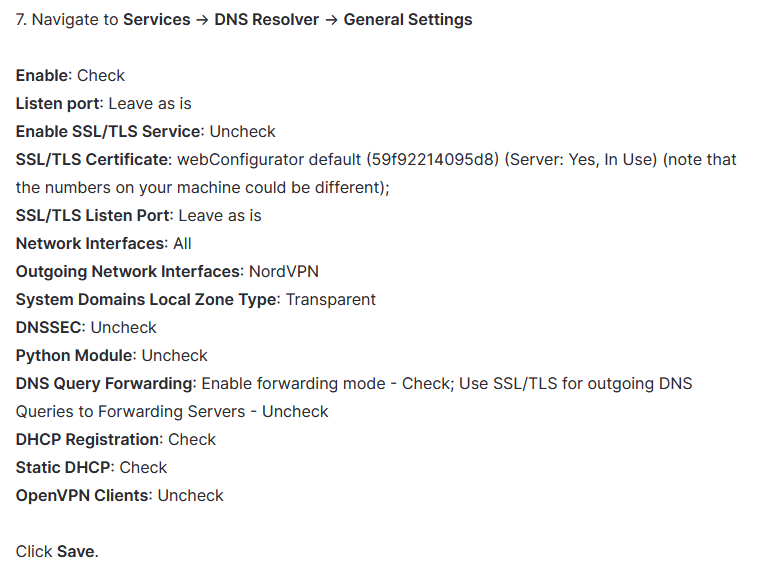
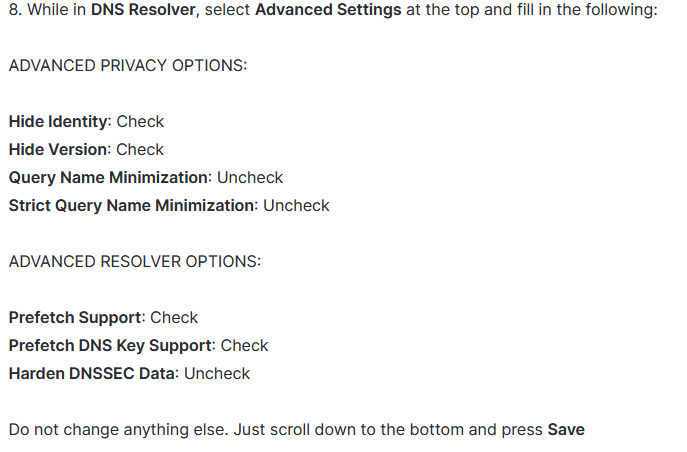
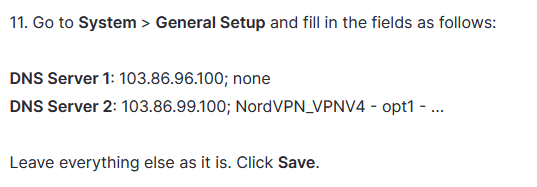
This seems to me like they are trying to avoid DNS leaks, which makes sense. But they also put your entire internet access through VPN, which I don't want to do.
I will try to make it work first, then search for protection against DNS leaks in that connection.I connected to their server as they say I should. Then I configured NAT and Firewall Rules. This solves the problem of IP Geolocation for me at first.
But no attention was given to how this connection handles DNS. I would appreciate any hint on how to check and get more information regarding this. -
@br8bruno said in NordVPN Client - not working:
I will try to research more on the topic.
Don't.
This issue was something this :
From a PC device on your LAN you can do thisdig @1.2.3.4 google.comwhere this DNS request was routed over the Nord connection.
where 1.2.3.4 isn't a DNS server at all, but Nord got you covered : you get a reply anyway. ( ....
....  )
)
That's solid for "we intercept your DNS".
They've acknowledged the issue (of course) leaving us with "ideas about the why part".
Knowing that your DNS data is worth $$ ... I think the "why" part is covered.Btw : This is me being a bit sarcastic, of course, and may be this issue is already 'solved'.
-
Thank you for the tips. Although I needed help from ChatGPT to understand your suggestion, I was still able to test and confirm your suspicion.
Both 8.8.8.8 and 1.2.3.4 don't work when I have NordVPN off. Only the DNS from my gateway resolves.
But when NordVPN is on... then anything gets through. The same thing happens when I use the NordVPN app under windows. It always resolves no matter what.
Take a look: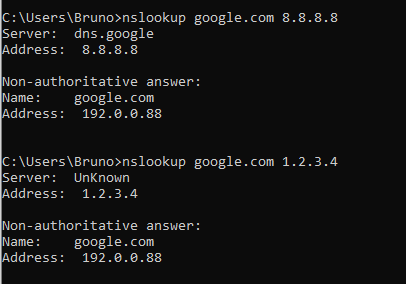
The question now is what to do? Is this something that can be capped with pfsense? Or is that a NordVPN problem?
-
Here what NordVPN support says when confronted about this in the chat:
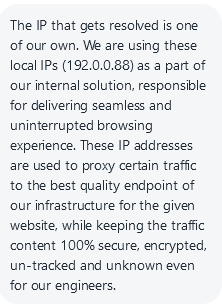
-
@br8bruno so gibberish that has zero to do with their interception of dns.
The only thing you could do to avoid interception would be to use say doh, or dot might not be intercepted or blocked and you would know if intercepted because there is no way you would trust the cert they send back. Unbound can forward to dot. But with normal resolving dns traffic is sent via 53, which they are intercepting.
Part of doh and dot is avoiding interception. And actually validating your talking to the NS you want to talk too. I have no issues with the technology in general, and sure it has some valid use cases. The problem I have with doh is how browsers and apps are turning it on without explicit user acknowledgement and signoff.. And make it difficult to block if you as the admin of your network do not want devices on your network using it. This is easy with dot, you can just block port 853 - but with doh it uses 443.. Which without knowing the actual endpoint they are going to talk to, is impossible to block without breaking the internet for your devices on your network.
Use some other vpn service is what I would do.. One that doesn't mess with your dns.