Acme DNS-NSupdate / RFC 2136 issue
-
OK, I missed a couple bits. I just pushed ACME pkg v 0.6.2 which should work now. I didn't test it completely but I did confirm at least that the zone makes it into the account config and logs where it was missing before.
-
Working now after upgrade to 0.6.2
Many thanks jimp!
-
 N NollipfSense referenced this topic on
N NollipfSense referenced this topic on
-
 N NollipfSense referenced this topic on
N NollipfSense referenced this topic on
-
 N NollipfSense referenced this topic on
N NollipfSense referenced this topic on
-
The problem is still present in the latest version. 0.8_1.
Failures on expected a TSIG or SIG(0) even though it's implemented.
Regards
-
Humm. I'm using 'nsupdate' = DNS-NSupdate / RFC 2136.
Works just fine.nsupdate didn't change for years.
-
@Gertjan are you using BIND9?
-
@Gertjan are you using BIND9?
-
-
@Gertjan could you post your config?
-
@VioletDragon said in Acme DNS-NSupdate / RFC 2136 issue:
@Gertjan are you using BIND9?
Yes.
Debian 11.10... no .11 just right now.
I can't re test my acme renewal, as I'm in the grace period : a renewal will work and no DNS checks will be done.
But : I'm also using RFC2136 for my pfSense WAN side host name = DynDNS.
Logs on server = bind9 side :
01-Sep-2024 13:21:27.416 update-security: client @0x7f4884148ed0 82.127.99.108#59810/key update: signer "update" approved 01-Sep-2024 13:21:27.416 update: client @0x7f4884148ed0 82.127.26.108#59810/key update: updating zone 'bhf.tld/IN': deleting rrset at 'home.bhf.tld' A 01-Sep-2024 13:21:27.416 update: client @0x7f4884148ed0 82.127.26.108#59810/key update: updating zone 'bhf.tld/IN': adding an RR at 'home.bhf.tld' A 82.135.26.118 01-Sep-2024 13:21:27.416 update: client @0x7f4884148ed0 82.127.26.108#59810/key update: updating zone 'bhf.tld/IN': deleting rrset at 'home.bhf.tld' AAAA 01-Sep-2024 13:21:27.416 update: client @0x7f4884148ed0 82.127.26.108#59810/key update: updating zone 'bhf.tld/IN': adding an RR at 'home.bhf.tld' AAAA 2a01:cb19:beef:dead:92ec:77ff:fe29:392a -
@Gertjan how did you set it up? As I got it working with Certbot but not Acme.
-
@Gertjan Problem seems to be with the acme.sh package, works fine with Certbot with the HMAC key but Acme seems to be ignoring the Key whether you put the key in or not.
Error that keeps showing dns_request_getresponse: expected a TSIG or SIG(0)
same happens with acme.sh on a fresh install of BSD so i think the package is broken.
-
The last acme.sh update is several or more weeks old.
nsupdate or RFC2136 is probably the most used update method.
It's also the very first, most documented update method.The pfSense acme packet uses probably not the latest 3.0.8
The nsupdate method itself hasn't been update for a long time.@VioletDragon said in Acme DNS-NSupdate / RFC 2136 issue:
Error that keeps showing dns_request_getresponse: expected a TSIG or SIG(0)
Imho, that's not a message from acme.sh ....
Can you show in what context this message is shown ? -
I can do better. This is the full log taken from acme.
Sat Aug 31 13:52:37 BST 2024] response='{"identifier":{"type":"dns","value":"domain.uk"},"status":"pending","expires":"2024-09-07T12:52:36Z","challenges":[{"type":"http-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/18bUeQ","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"},{"type":"dns-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"},{"type":"tls-alpn-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/AUEJVQ","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"}]}' [Sat Aug 31 13:52:37 BST 2024] response='{"identifier":{"type":"dns","value":domain.uk"},"status":"pending","expires":"2024-09-07T12:52:36Z","challenges":[{"type":"http-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/18bUeQ","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"},{"type":"dns-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"},{"type":"tls-alpn-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/AUEJVQ","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"}]}' [Sat Aug 31 13:52:37 BST 2024] _d='domain.uk' [Sat Aug 31 13:52:37 BST 2024] _authorizations_map='domain.uk,{"identifier":{"type":"dns","value":"domain.uk"},"status":"pending","expires":"2024-09-07T12:52:36Z","challenges":[{"type":"http-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/18bUeQ","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"},{"type":"dns-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"},{"type":"tls-alpn-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/AUEJVQ","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"}]}#https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/13812135463 ' [Sat Aug 31 13:52:37 BST 2024] d='domain.uk' [Sat Aug 31 13:52:37 BST 2024] Getting webroot for domain='domain.uk' [Sat Aug 31 13:52:37 BST 2024] _w='dns_nsupdate' [Sat Aug 31 13:52:37 BST 2024] _currentRoot='dns_nsupdate' [Sat Aug 31 13:52:37 BST 2024] _is_idn_d='rdomain.uk' [Sat Aug 31 13:52:37 BST 2024] _idn_temp [Sat Aug 31 13:52:37 BST 2024] _candidates='domain.uk,{"identifier":{"type":"dns","value":"domain.uk"},"status":"pending","expires":"2024-09-07T12:52:36Z","challenges":[{"type":"http-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/18bUeQ","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"},{"type":"dns-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"},{"type":"tls-alpn-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/AUEJVQ","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"}]}#https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/13812135463' [Sat Aug 31 13:52:37 BST 2024] response='{"identifier":{"type":"dns","value":"domain.uk"},"status":"pending","expires":"2024-09-07T12:52:36Z","challenges":[{"type":"http-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/18bUeQ","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"},{"type":"dns-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"},{"type":"tls-alpn-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/AUEJVQ","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"}]}#https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/13812135463' [Sat Aug 31 13:52:37 BST 2024] _authz_url='https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/13812135463' [Sat Aug 31 13:52:37 BST 2024] base64 single line. [Sat Aug 31 13:52:37 BST 2024] entry='"type":"dns-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"' [Sat Aug 31 13:52:37 BST 2024] token='ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs' [Sat Aug 31 13:52:37 BST 2024] uri='https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw' [Sat Aug 31 13:52:37 BST 2024] keyauthorization='ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs.Gs37H2DRQn4anpJP0dteohxeHULcMh5JS5ssdIbWSlM' [Sat Aug 31 13:52:37 BST 2024] dvlist='domain.uk#ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs.Gs37H2DRQn4anpJP0dteohxeHULcMh5JS5ssdIbWSlM#https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw#dns-01#dns_nsupdate#https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/13812135463' [Sat Aug 31 13:52:37 BST 2024] d [Sat Aug 31 13:52:37 BST 2024] vlist='domain.uk#ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs.Gs37H2DRQn4anpJP0dteohxeHULcMh5JS5ssdIbWSlM#https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw#dns-01#dns_nsupdate#https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/13812135463,' [Sat Aug 31 13:52:37 BST 2024] d='domain.uk' [Sat Aug 31 13:52:37 BST 2024] _d_alias [Sat Aug 31 13:52:37 BST 2024] txtdomain='_acme-challenge.domain.uk' [Sat Aug 31 13:52:37 BST 2024] base64 single line. [Sat Aug 31 13:52:37 BST 2024] txt='F93-7roSbnc3rfj9muIr3C5aVkahuRGFQFiSpc-FdFI' [Sat Aug 31 13:52:37 BST 2024] d_api='/usr/local/pkg/acme/dnsapi/dns_nsupdate.sh' [Sat Aug 31 13:52:37 BST 2024] dns_entry='domain.uk,_acme-challenge.domain.uk,,dns_nsupdate,F93-7roSbnc3rfj9muIr3C5aVkahuRGFQFiSpc-FdFI,/usr/local/pkg/acme/dnsapi/dns_nsupdate.sh' [Sat Aug 31 13:52:37 BST 2024] Found domain api file: /usr/local/pkg/acme/dnsapi/dns_nsupdate.sh [Sat Aug 31 13:52:37 BST 2024] dns_nsupdate_add exists=0 [Sat Aug 31 13:52:37 BST 2024] Adding txt value: F93-7roSbnc3rfj9muIr3C5aVkahuRGFQFiSpc-FdFI for domain: _acme-challenge.domain.uk [Sat Aug 31 13:52:37 BST 2024] APP [Sat Aug 31 13:52:37 BST 2024] 5:NSUPDATE_SERVER='ns1.domain.uk' [Sat Aug 31 13:52:37 BST 2024] APP [Sat Aug 31 13:52:37 BST 2024] 6:NSUPDATE_SERVER_PORT='' [Sat Aug 31 13:52:37 BST 2024] APP [Sat Aug 31 13:52:37 BST 2024] 7:NSUPDATE_KEY='/tmp/acme/domain/domain.uknsupdate_acme-challenge.domain.uk.key' [Sat Aug 31 13:52:37 BST 2024] APP [Sat Aug 31 13:52:37 BST 2024] 8:NSUPDATE_ZONE='' [Sat Aug 31 13:52:37 BST 2024] adding _acme-challenge.domain.uk. 60 in txt "F93-7roSbnc3rfj9muIr3C5aVkahuRGFQFiSpc-FdFI" [Sat Aug 31 13:52:37 BST 2024] error updating domain [Sat Aug 31 13:52:37 BST 2024] Error add txt for domain:_acme-challenge.domain.uk [Sat Aug 31 13:52:37 BST 2024] _on_issue_err [Sat Aug 31 13:52:37 BST 2024] Please check log file for more details: /tmp/acme/domain/acme_issuecert.log [Sat Aug 31 13:52:37 BST 2024] _chk_vlist='domain.uk.uk#ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs.Gs37H2DRQn4anpJP0dteohxeHULcMh5JS5ssdIbWSlM#https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw#dns-01#dns_nsupdate#https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/13812135463,' [Sat Aug 31 13:52:37 BST 2024] start to deactivate authz [Sat Aug 31 13:52:37 BST 2024] Trigger domain validation. [Sat Aug 31 13:52:37 BST 2024] _t_url='https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw' [Sat Aug 31 13:52:37 BST 2024] _t_key_authz='ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs.Gs37H2DRQn4anpJP0dteohxeHULcMh5JS5ssdIbWSlM' [Sat Aug 31 13:52:37 BST 2024] _t_vtype [Sat Aug 31 13:52:37 BST 2024] =======Begin Send Signed Request======= [Sat Aug 31 13:52:37 BST 2024] url='https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw' [Sat Aug 31 13:52:37 BST 2024] payload='{}' [Sat Aug 31 13:52:37 BST 2024] Use cached jwk for file: /tmp/acme/domain/ca/acme-staging-v02.api.letsencrypt.org/directory/account.key [Sat Aug 31 13:52:37 BST 2024] base64 single line. [Sat Aug 31 13:52:37 BST 2024] payload64='e30' [Sat Aug 31 13:52:37 BST 2024] _request_retry_times='1' [Sat Aug 31 13:52:37 BST 2024] Use _CACHED_NONCE='vfo-J0TvfjHlz2bMKE551YAvMUFYuZqkrhfz2naON64CEGmUrLI' [Sat Aug 31 13:52:37 BST 2024] nonce='vfo-J0TvfjHlz2bMKE551YAvMUFYuZqkrhfz2naON64CEGmUrLI' [Sat Aug 31 13:52:37 BST 2024] protected='{"nonce": "vfo-J0TvfjHlz2bMKE551YAvMUFYuZqkrhfz2naON64CEGmUrLI", "url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw", "alg": "RS256", "kid": "https://acme-staging-v02.api.letsencrypt.org/acme/acct/161503273"}' [Sat Aug 31 13:52:37 BST 2024] base64 single line. [Sat Aug 31 13:52:37 BST 2024] protected64='eyJub25jZSI6ICJ2Zm8tSjBUdmZqSGx6MmJNS0U1NTFZQXZNVUZZdVpxa3JoZnoybmFPTjY0Q0VHbVVyTEkiLCAidXJsIjogImh0dHBzOi8vYWNtZS1zdGFnaW5nLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvY2hhbGwtdjMvMTM4MTIxMzU0NjMvaHBFTER3IiwgImFsZyI6ICJSUzI1NiIsICJraWQiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9hY2N0LzE2MTUwMzI3MyJ9' [Sat Aug 31 13:52:37 BST 2024] base64 single line. [Sat Aug 31 13:52:37 BST 2024] _sig_t='FkRiy7U2h9RGIiziq5LU9NeGSJln9tIRLLGVDvlYo2Gp4PB/eaLi2zxZMn2GEfP9SGOn7hmxE9hbkd7bQkuFKSIwCUgnrrAVQ3IZ/IrCFH401qZ/Vbi56mGb260pIZhIpY2xV8lLya+7x9KxkUKEkn42wTqPyXOypl4e4Wws4ENwrg1npmn8dGxVxM5l1s8raRToUIHzB3ueibZnkv6wGiQsW43nbPFnfr9E3fb9vDF995h4fxpqW1IdgAuaH766GKPLaMdFowOcNtu+E3ep7QVB64/s9uUr5cdtu4LvrJs3g7TF1GWMi56Cn7aOiMqOcZ+/xg4C2Gesbz6Mij75xCdOO36asmC7VUK03MEMprZKk3l3gwXCz7xIo9ak3/dcV08K5GfrsMwwtOfbuzcQKAtRqNQwwjPTqANswue3jWpZLdKx97QFlEH8AQ9jw6vjSsEqNpTMrGbwp/GrG2Y9kzx6B5G1Ivp4iUQgC7b4PfIFeC8d+rPpQ7tOesTHK7EgZ5obK/L6UsS5G1fAf9ajx05rCkpk5ivYOpTS6p55X9nHSV+TGsADegxts4I7Zl40wSEaZAG70hI0xSK7mns/d70lb99SOYGKwGIKAZjCuG7U++28kvjjWk6jLNPrV7Rj6uPzDAl4xjcrsbzSzDnkgZMQZGAfHPLQZkQtV+czkdw=' [Sat Aug 31 13:52:37 BST 2024] sig='FkRiy7U2h9RGIiziq5LU9NeGSJln9tIRLLGVDvlYo2Gp4PB_eaLi2zxZMn2GEfP9SGOn7hmxE9hbkd7bQkuFKSIwCUgnrrAVQ3IZ_IrCFH401qZ_Vbi56mGb260pIZhIpY2xV8lLya-7x9KxkUKEkn42wTqPyXOypl4e4Wws4ENwrg1npmn8dGxVxM5l1s8raRToUIHzB3ueibZnkv6wGiQsW43nbPFnfr9E3fb9vDF995h4fxpqW1IdgAuaH766GKPLaMdFowOcNtu-E3ep7QVB64_s9uUr5cdtu4LvrJs3g7TF1GWMi56Cn7aOiMqOcZ-_xg4C2Gesbz6Mij75xCdOO36asmC7VUK03MEMprZKk3l3gwXCz7xIo9ak3_dcV08K5GfrsMwwtOfbuzcQKAtRqNQwwjPTqANswue3jWpZLdKx97QFlEH8AQ9jw6vjSsEqNpTMrGbwp_GrG2Y9kzx6B5G1Ivp4iUQgC7b4PfIFeC8d-rPpQ7tOesTHK7EgZ5obK_L6UsS5G1fAf9ajx05rCkpk5ivYOpTS6p55X9nHSV-TGsADegxts4I7Zl40wSEaZAG70hI0xSK7mns_d70lb99SOYGKwGIKAZjCuG7U--28kvjjWk6jLNPrV7Rj6uPzDAl4xjcrsbzSzDnkgZMQZGAfHPLQZkQtV-czkdw' [Sat Aug 31 13:52:37 BST 2024] body='{"protected": "eyJub25jZSI6ICJ2Zm8tSjBUdmZqSGx6MmJNS0U1NTFZQXZNVUZZdVpxa3JoZnoybmFPTjY0Q0VHbVVyTEkiLCAidXJsIjogImh0dHBzOi8vYWNtZS1zdGFnaW5nLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvY2hhbGwtdjMvMTM4MTIxMzU0NjMvaHBFTER3IiwgImFsZyI6ICJSUzI1NiIsICJraWQiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9hY2N0LzE2MTUwMzI3MyJ9", "payload": "e30", "signature": "FkRiy7U2h9RGIiziq5LU9NeGSJln9tIRLLGVDvlYo2Gp4PB_eaLi2zxZMn2GEfP9SGOn7hmxE9hbkd7bQkuFKSIwCUgnrrAVQ3IZ_IrCFH401qZ_Vbi56mGb260pIZhIpY2xV8lLya-7x9KxkUKEkn42wTqPyXOypl4e4Wws4ENwrg1npmn8dGxVxM5l1s8raRToUIHzB3ueibZnkv6wGiQsW43nbPFnfr9E3fb9vDF995h4fxpqW1IdgAuaH766GKPLaMdFowOcNtu-E3ep7QVB64_s9uUr5cdtu4LvrJs3g7TF1GWMi56Cn7aOiMqOcZ-_xg4C2Gesbz6Mij75xCdOO36asmC7VUK03MEMprZKk3l3gwXCz7xIo9ak3_dcV08K5GfrsMwwtOfbuzcQKAtRqNQwwjPTqANswue3jWpZLdKx97QFlEH8AQ9jw6vjSsEqNpTMrGbwp_GrG2Y9kzx6B5G1Ivp4iUQgC7b4PfIFeC8d-rPpQ7tOesTHK7EgZ5obK_L6UsS5G1fAf9ajx05rCkpk5ivYOpTS6p55X9nHSV-TGsADegxts4I7Zl40wSEaZAG70hI0xSK7mns_d70lb99SOYGKwGIKAZjCuG7U--28kvjjWk6jLNPrV7Rj6uPzDAl4xjcrsbzSzDnkgZMQZGAfHPLQZkQtV-czkdw"}' [Sat Aug 31 13:52:37 BST 2024] POST [Sat Aug 31 13:52:37 BST 2024] _post_url='https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw' [Sat Aug 31 13:52:37 BST 2024] body='{"protected": "eyJub25jZSI6ICJ2Zm8tSjBUdmZqSGx6MmJNS0U1NTFZQXZNVUZZdVpxa3JoZnoybmFPTjY0Q0VHbVVyTEkiLCAidXJsIjogImh0dHBzOi8vYWNtZS1zdGFnaW5nLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvY2hhbGwtdjMvMTM4MTIxMzU0NjMvaHBFTER3IiwgImFsZyI6ICJSUzI1NiIsICJraWQiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9hY2N0LzE2MTUwMzI3MyJ9", "payload": "e30", "signature": "FkRiy7U2h9RGIiziq5LU9NeGSJln9tIRLLGVDvlYo2Gp4PB_eaLi2zxZMn2GEfP9SGOn7hmxE9hbkd7bQkuFKSIwCUgnrrAVQ3IZ_IrCFH401qZ_Vbi56mGb260pIZhIpY2xV8lLya-7x9KxkUKEkn42wTqPyXOypl4e4Wws4ENwrg1npmn8dGxVxM5l1s8raRToUIHzB3ueibZnkv6wGiQsW43nbPFnfr9E3fb9vDF995h4fxpqW1IdgAuaH766GKPLaMdFowOcNtu-E3ep7QVB64_s9uUr5cdtu4LvrJs3g7TF1GWMi56Cn7aOiMqOcZ-_xg4C2Gesbz6Mij75xCdOO36asmC7VUK03MEMprZKk3l3gwXCz7xIo9ak3_dcV08K5GfrsMwwtOfbuzcQKAtRqNQwwjPTqANswue3jWpZLdKx97QFlEH8AQ9jw6vjSsEqNpTMrGbwp_GrG2Y9kzx6B5G1Ivp4iUQgC7b4PfIFeC8d-rPpQ7tOesTHK7EgZ5obK_L6UsS5G1fAf9ajx05rCkpk5ivYOpTS6p55X9nHSV-TGsADegxts4I7Zl40wSEaZAG70hI0xSK7mns_d70lb99SOYGKwGIKAZjCuG7U--28kvjjWk6jLNPrV7Rj6uPzDAl4xjcrsbzSzDnkgZMQZGAfHPLQZkQtV-czkdw"}' [Sat Aug 31 13:52:37 BST 2024] _postContentType='application/jose+json' [Sat Aug 31 13:52:37 BST 2024] Http already initialized. [Sat Aug 31 13:52:37 BST 2024] _CURL='curl --silent --dump-header /tmp/acme/domain/http.header -L -g ' [Sat Aug 31 13:52:37 BST 2024] _ret='0' [Sat Aug 31 13:52:37 BST 2024] responseHeaders='HTTP/2 200 server: nginx date: Sat, 31 Aug 2024 12:52:37 GMT content-type: application/json content-length: 193 boulder-requester: 161503273 cache-control: public, max-age=0, no-cache link: https://acme-staging-v02.api.letsencrypt.org/directory;rel="index" link: https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/13812135463;rel="up" location: https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw replay-nonce: VFujB6i1Gj9UXVGZtCBP2Gip24W5U0wZDJQCsFzinwHOc366KPo x-frame-options: DENY strict-transport-security: max-age=604800 ' [Sat Aug 31 13:52:37 BST 2024] code='200' [Sat Aug 31 13:52:37 BST 2024] original='{ "type": "dns-01", "url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw", "status": "pending", "token": "ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs" }' [Sat Aug 31 13:52:37 BST 2024] _json_decode [Sat Aug 31 13:52:37 BST 2024] _j_str='{ "type": "dns-01", "url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw", "status": "pending", "token": "ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs" }' [Sat Aug 31 13:52:37 BST 2024] response='{"type":"dns-01","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/13812135463/hpELDw","status":"pending","token":"ExZOHBOLdZQNMQwI53B9xUHYKu_HzSBAYS_UuXFciGs"}' [Sat Aug 31 13:52:37 BST 2024] pid [Sat Aug 31 13:52:37 BST 2024] No need to restore nginx, skip. [Sat Aug 31 13:52:37 BST 2024] _clearupdns [Sat Aug 31 13:52:37 BST 2024] dns_entries [Sat Aug 31 13:52:37 BST 2024] skip dns. -
Here :
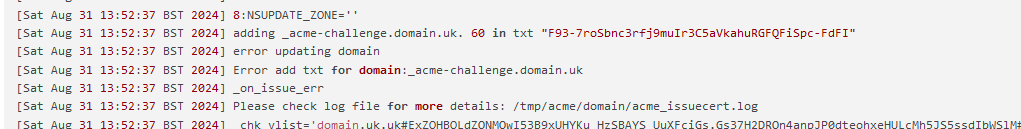
Thats between :
and
where the nsupdate instruction file is created. The executed ... and fails to authenticate.
The parameters look fine.
So, as always, your secret key is wrong.
This one is mine :key "update" { algorithm hmac-sha512; secret "eYQiVAutEEAF......./ ....................DCaJwzkuZp0w=="; };Make sure bind is using the key, mine is called 'update'. That encoding is correct both sides etc
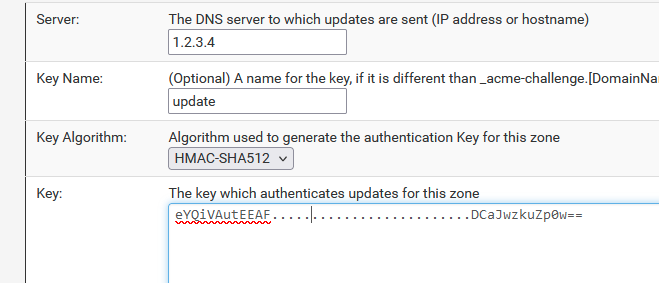
And : look at your bind debug log. You will see the update (add) request - and why it fails.
-
@Gertjan Yeah that is how i've configured it, HMAC has been removed from dnssec, the key i am specifying to Acme is the same key for certbot which works for Certbot but not Acme on pfSense.
Now the big question is, does the name server require DNSSec to be enabled for this to work?
This is the config I have on the master Name server the config that handles the HMAC key is as follows,
key "api." { algorithm hmac-sha512; secret "private key from the file Kcertbot.+165+?????.private"; }; zone "_acme-challenge.mydomain.com" { type master; file "/var/lib/bind/db._acme-challenge.mydomain.com"; check-names warn; update-policy { grant certbot. name _acme-challenge.mydomain.com. txt; }; };To me it feels like the Acme package isn't picking the key up although Certbot does. I tested with a wrong HMAC key on Acme and it fails to connect with the correct key the logs on the Name Server show's acme is communicating and it does create the TXT Record but I get the error with Acme on pfSense
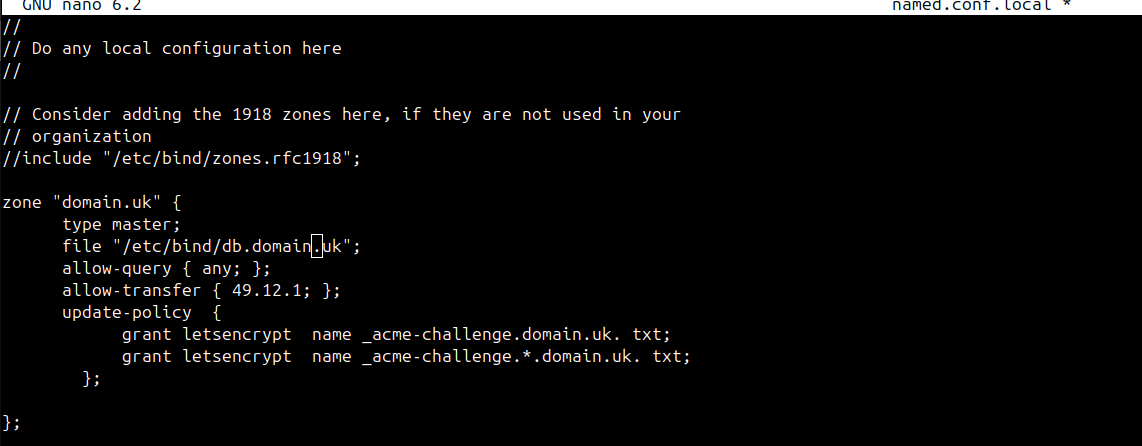
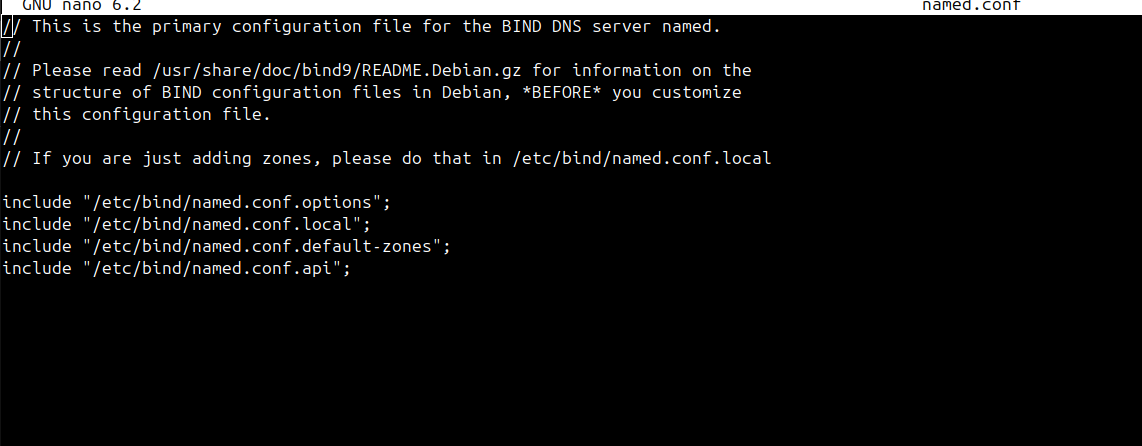
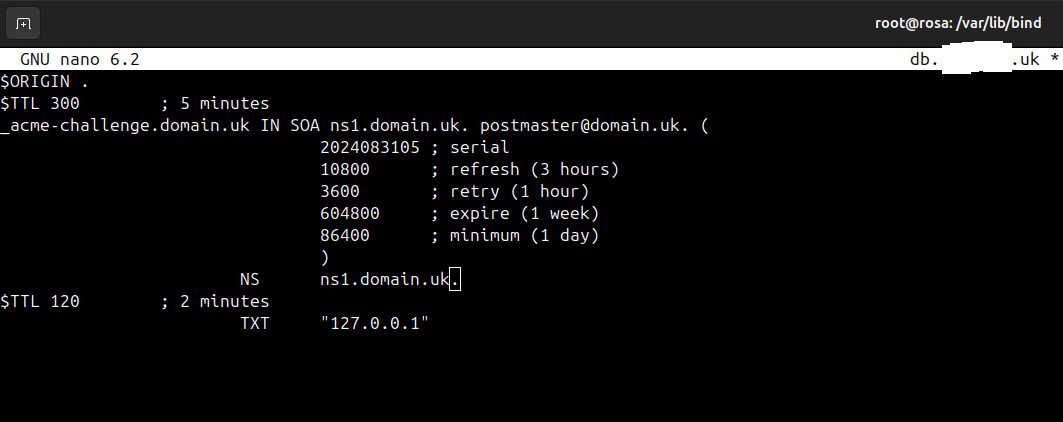
Regards
-
@VioletDragon said in Acme DNS-NSupdate / RFC 2136 issue:
Now the big question is, does the name server require DNSSec to be enabled for this to work?
DNSSEC has nothing to do with "RFC 2136".
RFC 2136 or 'nsupdate' is an (my words) access method to the master domain name server so you can add or delete zones like
www.your-domaine.TLD A 1.2.3.4;or
www.your-domaine.TLD TXT "a text here";Btw : all my domains have DNNSEC - and all my domains uses acme.sh to get certificates from LE.
edit :
zone "bhf.tld" { type master; file "/etc/bind/zones/db.bhf.tld"; allow-transfer { "ns-internal-net"; }; masterfile-format text; notify-source 1.2.3.4; notify explicit; allow-update { key "update";}; };where bhf.tld is the domain name.
"ns-internal-net" is the list with my domain name slave servers, as these are allowed to sync with the master.
1.2.3.4 is the IP 'A' of my domain name.
I use the imho easier to use "allow-update" method. I've already shown the key called 'update' above.I'm debug-logging the nsupdate methods anyway, and have a fail2ban looking at the log lines. If some attack (abuse) is detected, the attacking IP will get fire-walled for a while.
-
@Gertjan I will give your config you attached ago and see what happens. I will post back in a few hours
Just out of interest. Have you tried this with certbot?
Regards
-
@VioletDragon said in Acme DNS-NSupdate / RFC 2136 issue:
Have you tried this with certbot?
Why would I ?
pfSense isn't a "install whatever app or package you want" device, it has a 'pfSense' package (that uses acme.sh) that makes it possible to obtain a cert.Btw :
pfSense will score a 0 (wrong ! it has ssh if you activate it) out of 100 here.
edit : I'm not saying certbot is any good. I actually used it in the early years of 'LE' on my public servers.
-
@Gertjan With the config you attached it is the same problem,
[Mon Sep 2 14:39:57 BST 2024] Adding txt value: OhjjaFGykQB6NOmc4aclaxSc3JrEKBTILGG9-DChOOA for domain: _acme-challenge.domain.uk [Mon Sep 2 14:39:57 BST 2024] adding _acme-challenge.domain.uk. 60 in txt "OhjjaFGykQB6NOmc4aclaxSc3JrEKBTILGG9-DChOOA" dns_request_getresponse: expected a TSIG or SIG(0) [Mon Sep 2 14:39:57 BST 2024] error updating domain [Mon Sep 2 14:39:57 BST 2024] Error add txt for domain:_acme-challenge.domain.uk [Mon Sep 2 14:39:57 BST 2024] Please check log file for more details: /tmp/acme/Route94/acme_issuecert.logLog from BIND,
Sep 02 14:38:07 ns1.uk named[2868]: client @0x7f1bf0007cf8 172.70.84.154#26600 (_acme-challenge.domain.uk): query: _acme-challenge.domain.uk IN A -E(0)D (10.5) Sep 02 14:38:19 ns1.domain.uk named[2868]: client @0x7f1be8002318 49.12#58200 (domain.uk): query: domain.uk IN SOA -E(0) (10.) Sep 02 14:39:57 ns1.domain.uk named[2868]: client @0x7f1bf818bdb8 172.70.84.152#22383 (ns1.domain.uk): query: ns1.domain.uk IN A -E(0)D (10.5) Sep 02 14:39:57 ns1.domain.uk named[2868]: client @0x7f1be8002318 172.70.84.152#35214 (ns1.domain.uk): query: ns1.domain.uk IN A -E(0)D (10.5) Sep 02 14:39:57 ns1.domain.uk named[2868]: client @0x7f1bf0007cf8 172.69.43.40#10557 (ns1.domain): query: ns1 IN A -E(0)D (10.5) Sep 02 14:39:57 ns1.domain.uk named[2868]: client @0x7f1be8002318 172.69.43.40#39038 (domain.uk): query: ns1.domain.uk IN AAAA -E(0)D (10.5) Sep 02 14:39:57 ns1,domain.uk named[2868]: client @0x7f1bf4005058 172.69.43.40#41326 (domain.uk): query: domain.uk IN DNSKEY -E(0)D (10.5) Sep 02 14:39:58 ns1.domain.uk named[2868]: client @0x7f1bf818bdb8 23.178.112.107#11581 (_aCMe-CHALlenGE.domain.UK): query: _aCMe-CHALlenGE.domin.UK IN TXT -E(0)DC (10.5) Sep 02 14:39:58 ns1,domain.uk named[2868]: client @0x7f1bf4005058 23.178.112.107#36831 (ns1.domain.UK): query: ROSA.Ns1.domain.UK IN AAAA -E(0)DC (10.5) Sep 02 14:39:58 ns1.domain.uk.uk named[2868]: client @0x7f1bf818e788 23.178.112.107#55833 (ns1.domain.UK): query: ns1.domain.UK IN AAAA -E(0)DC (10.5)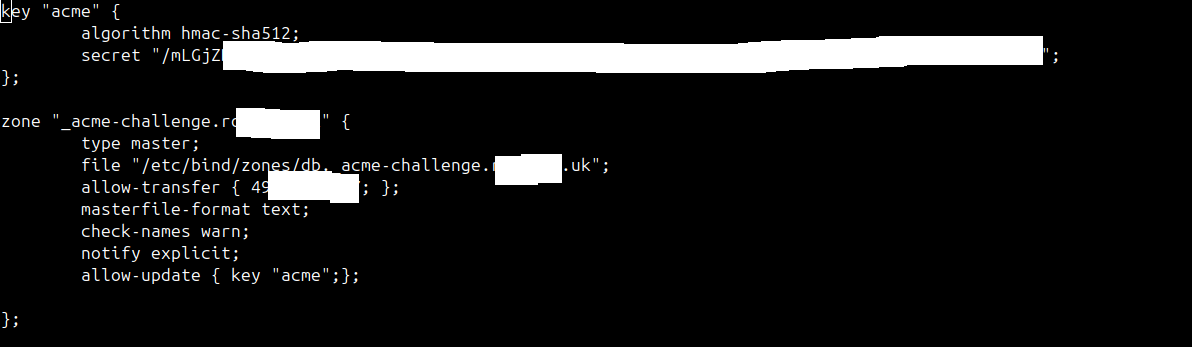
-
My logs are somewhat different :
First : as I ask for a wild card certificate, so two TXT records to add :07-Aug-2024 07:53:10.411 update-security: client @0x7ff5325d5070 82.127.xx.108#55966/key update: signer "update" approved 07-Aug-2024 07:53:10.411 update: client @0x7ff5325d5070 82.127.xx.108#55966/key update: updating zone 'domain.tld/IN': adding an RR at '_acme-challenge.domain.tld' TXT "JLJQnIUFDoiQKHfN6iyFvHIuMMhF_-h7I5-mWcaZGX4" 07-Aug-2024 07:53:10.719 update-security: client @0x7ff5325d5070 82.127.xx.108#65112/key update: signer "update" approved 07-Aug-2024 07:53:10.719 update: client @0x7ff5325d5070 82.127.xx.108#65112/key update: updating zone 'domain.tld/IN': adding an RR at '_acme-challenge.domain.tld' TXT "Rmcf8iJ7-R7joIpa_hEMgfYBm9jpt_YuSP3eyBjSfq4"Then, a dnssleep of 3 minutes.
During this time LE checks the "_acme-challenge.domain.tld' TXT" on the master, or one of my DNS slaves, or all of them ?When done, it's clean up time:
07-Aug-2024 07:55:17.432 update-security: client @0x7ff5325d5070 82.127.xx.108#57576/key update: signer "update" approved 07-Aug-2024 07:55:17.432 update: client @0x7ff5325d5070 82.127.xx.108#57576/key update: updating zone 'domain.tld/IN': deleting rrset at '_acme-challenge.domain.tld' TXT 07-Aug-2024 07:55:17.596 update-security: client @0x7ff528513520 82.127.xx.108#55196/key update: signer "update" approved 07-Aug-2024 07:55:17.596 update: client @0x7ff528513520 82.127.xx.108#55196/key update: updating zone 'domain.tld/IN': deleting rrset at '_acme-challenge.domain.tld' TXTwhere 82.127.xx.108 is my pfSense WAN IP, from where the acme.sh pfSEnse package runs.
Also : in "named.conf.options" I have this animal :
logging { category "lame-servers" { lame; }; channel "lame" { file "/var/log/bind9/lame.log" versions 10 size 5m; print-time yes; print-category yes; severity dynamic; }; category "default" { "debug"; }; category "database" { "debug"; }; category "security" { "debug"; }; category "config" { "debug"; }; category "resolver" { "debug"; }; category "client" { "debug"; }; category "unmatched" { "debug"; }; category "network" { "debug"; }; category "update" { "debug"; }; category "dispatch" { "debug"; }; channel "debug" { file "/var/log/bind9/debug.log" versions 10 size 5m; print-time yes; print-category yes; severity dynamic; }; category "dnssec" { "dnssec"; }; channel "dnssec" { file "/var/log/bind9/dnssec.log" versions 10 size 5m; print-time yes; print-category yes; severity dynamic; }; channel "xfer" { file "/var/log/bind9/xfer.log" versions 10 size 5m; print-time yes; print-category yes; severity debug; }; category "xfer-in" { "xfer"; }; category "xfer-out" { "xfer"; }; category "notify" { "xfer"; }; channel "general" { file "/var/log/bind9/general.log" versions 10 size 5m; print-time yes; print-category yes; severity dynamic; }; category "general" { "general"; }; channel "b_query" { file "/var/log/bind9/query.log" versions 10 size 5m; print-time yes; print-category yes; severity dynamic; }; category "queries" { "b_query"; }; };which throws all the update (RFC1236 ?) stuff into the debug log