Acme DNS-NSupdate / RFC 2136 issue
-
@VioletDragon said in Acme DNS-NSupdate / RFC 2136 issue:
HMAC key
HMAC**-SHA512**, right ?
The nsupdate tool that acme.sh uses isn't from acme.sh, but from the OS ( ? ).
The acme.sh update method called "DNS-NSupdate" uses the nsupdate binary, that should be able to talk to bind, on the other side.
@VioletDragon said in Acme DNS-NSupdate / RFC 2136 issue:
Did a fresh install with Debian, when running nsupdate -k on the physical name server I get the same error,
You mean you couldn't even run nsupdate on the debian server itself ?
The nsupdate tools that comes with the bind package can't 'talk' to bind ? -
@Gertjan update. The configuration for Acme and Certbot is different. Will report back when I’ve done the configuration.
-
@Gertjan I've made progress nsupdate now works but the problem I keep getting is on pfSense side,
; TSIG error with server: tsig verify failure update failed: NOTIMP -
@Gertjan It seems that acme on pfSense has a problem, tested acme.sh on a Debian VM and it works, not sure what the deal is with acme on pfSense though very strange.
Regards
-
There is something that you can test :
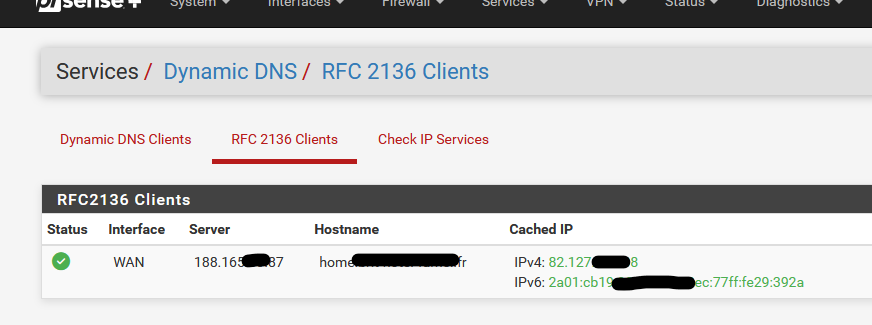
as it uses the same 'nsupdate' thus exactly the same parameters :
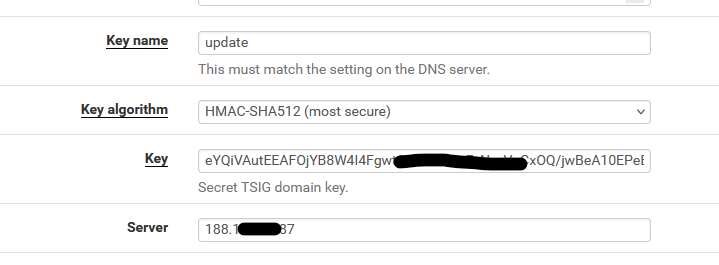
-
@Gertjan how would that work for Acme SSL Certs ?
-
Not at all.
Services > Dynamic DNS > RFC 2136 Clients uses exacly the same DNS server zone update mechanism by using the 'nsupdate' executable.
Exactly like acme.sh, with the DNS dns_nsupdate method.
acme.sh adds TXT records.
"Services > Dynamic DNS > RFC 2136 Clients" adds A and AAAA records.
Both use the same nsupdate executable on pfSense.
Both use the same key, key name, algorithm, server IP (your domain name master DNS server. -
@Gertjan okay sweet I will try that later after doing some work and I will report back.
Do you think that this problem I’m facing is caused by the acme package ? As acme.sh works on Debian, same with Certbot. When running nsupdate that works too just acme package is causing me some problems.
Regards
-
@Gertjan Update, This can be marked as solved.
I tried the method you replied above but no dice.
I ended up going with Nginx Reverse Proxy and Certbot with RFC2136 which seems to work better.
Regards
-
@VioletDragon for what it's worth:
# named -v BIND 9.18.29 (Extended Support Version) <id:> # freebsd-version 14.1-RELEASE-p4That just happens to be my current nameserver, prior versions were earlier BIND versions running on CentOS. I have not had issues with the Acme package doing RFC 2136 updates on any of the BIND/OS versions that I've run. I also use HMAC-sha512 keys, but have used others without issue. Sorry, no solution to offer you, just confirmation from another user that Acme/RFC-2136/BIND works well. The only issue I did have when initially getting Acme set up was to make sure I was using a long enough DNS-sleep.
--Larry
-
@LarryFahnoe yep. I’ve switched away from Haproxy and acme on pfsense due to needing more power under the hood and security reasons.
BIND9 with 2 Nginx Reverse Proxy and RFC2136 works well.
Regards.