How can i set client vlan to not communicate with management but management vlan can operate on client vlan?
-
My network is composed by:
- VLAN 99 (client) 172.17.99.0/24
- VLAN 30 (mgmt) 172.17.30.0/24
DHCP is enabled on the 2 vlans in the range from .100 to .150
i need to block access from client vlan to management vlan but let the management vlan operate on client vlan
I made the rule that block the access from the client vlan to the management vlan and i want to create a rule that allows access from management vlan to client vlan but i don't know how to do it. does anyone have any ideas?
-
@Stp well on your client vlan create a rule to block access to your mgmt vlan. You prob want to block access to pfsense IPs as well - to prevent access to the pfsense gui, etc..
here is an example of a locked down vlan
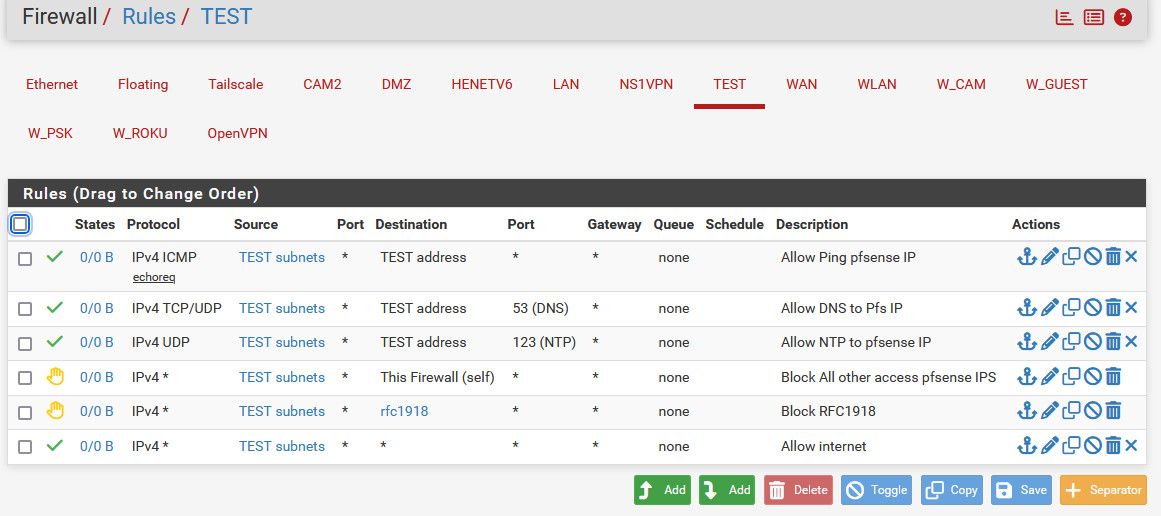
Rules are evaluated top down, first rule to trigger wins, no other rules are evaluated.
If you mgmt vlan rules allow access to the client vlan, the state would allow return traffic.
-
@johnpoz Thank you, i will try it, but first i have another problem because i changed WAN ip address from DHCP to static IP and i don't know how the vlans are not connecting to the web.
the WAN ip address is a private ip address because i have a test network in my company network, so i find out that i have to enter the gateway of my network to connect wan to the internet, but it doesn't work anyway.
tell me if i need to create another question apart of this argument or not. thanks a lot.
-
@Stp set it back to dhcp then.. Clearly if the static you put in isn't working you put it in wrong, wrong mask, wrong gateway.. Your dns isn't working? can you ping 8.8.8.8?
-
@johnpoz i can ping 8.8.8.8 from all the interfaces (vlan client, vlan mgmt and wan). i also checked the dhcp and it's working correctly
-
@Stp well if you can ping 8.8.8.8 then internet is working.. Your problem is prob dns related.