IKEv2+radius AD+CA+MacOS
-
Я настраивал VPN вот в этом топике
https://forum.netgate.com/topic/188460/pfsense-ca-openvpn-l2tp-ipsec-gre-ipsec-ad-radius
Мне там очень помогли с настройкой.
Пока ВПН требовался только на винде проблем не было, но сейчас мне нужно настроить впн на маке. С авторизацией по пользователю в АД.
Я сделал всё по этой инструкции.
https://docs.netgate.com/pfsense/en/latest/recipes/ipsec-mobile-ikev2-client-macos.html
Но у меня так ничего и не заработало)
Подскажите пожалуйста, где я не прав?)Sep 18 12:35:09 charon 54184 11[NET] <3481> received packet: from 178.176.76.143[29056] to 81.5.119.144[500] (604 bytes)
Sep 18 12:35:09 charon 54184 11[ENC] <3481> parsed IKE_SA_INIT request 0 [ SA KE No N(REDIR_SUP) N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) ]
Sep 18 12:35:09 charon 54184 11[CFG] <3481> looking for an IKEv2 config for 81.5.119.144...178.176.76.143
Sep 18 12:35:09 charon 54184 11[CFG] <3481> candidate: 81.5.119.144...0.0.0.0/0, ::/0, prio 1052
Sep 18 12:35:09 charon 54184 11[CFG] <3481> found matching ike config: 81.5.119.144...0.0.0.0/0, ::/0 with prio 1052
Sep 18 12:35:09 charon 54184 11[IKE] <3481> local endpoint changed from 0.0.0.0[500] to 81.5.119.144[500]
Sep 18 12:35:09 charon 54184 11[IKE] <3481> remote endpoint changed from 0.0.0.0 to 178.176.76.143[29056]
Sep 18 12:35:09 charon 54184 11[IKE] <3481> 178.176.76.143 is initiating an IKE_SA
Sep 18 12:35:09 charon 54184 11[IKE] <3481> IKE_SA (unnamed)[3481] state change: CREATED => CONNECTING
Sep 18 12:35:09 charon 54184 11[CFG] <3481> selecting proposal:
Sep 18 12:35:09 charon 54184 11[CFG] <3481> no acceptable ENCRYPTION_ALGORITHM found
Sep 18 12:35:09 charon 54184 11[CFG] <3481> selecting proposal:
Sep 18 12:35:09 charon 54184 11[CFG] <3481> no acceptable ENCRYPTION_ALGORITHM found
Sep 18 12:35:09 charon 54184 11[CFG] <3481> selecting proposal:
Sep 18 12:35:09 charon 54184 11[CFG] <3481> no acceptable ENCRYPTION_ALGORITHM found
Sep 18 12:35:09 charon 54184 11[CFG] <3481> selecting proposal:
Sep 18 12:35:09 charon 54184 11[CFG] <3481> no acceptable INTEGRITY_ALGORITHM found
Sep 18 12:35:09 charon 54184 11[CFG] <3481> selecting proposal:
Sep 18 12:35:09 charon 54184 11[CFG] <3481> no acceptable ENCRYPTION_ALGORITHM found
Sep 18 12:35:09 charon 54184 11[CFG] <3481> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1536, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Sep 18 12:35:09 charon 54184 11[CFG] <3481> configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024
Sep 18 12:35:09 charon 54184 11[CFG] <3481> looking for IKEv2 configs for 81.5.119.144...178.176.76.143
Sep 18 12:35:09 charon 54184 11[CFG] <3481> candidate: 81.5.119.144...0.0.0.0/0, ::/0, prio 1052
Sep 18 12:35:09 charon 54184 11[IKE] <3481> remote host is behind NAT
Sep 18 12:35:09 charon 54184 11[IKE] <3481> received proposals unacceptable
Sep 18 12:35:09 charon 54184 11[ENC] <3481> generating IKE_SA_INIT response 0 [ N(NO_PROP) ]
Sep 18 12:35:09 charon 54184 11[NET] <3481> sending packet: from 81.5.119.144[500] to 178.176.76.143[29056] (36 bytes)
Sep 18 12:35:09 charon 54184 11[IKE] <3481> IKE_SA (unnamed)[3481] state change: CONNECTING => DESTROYING
Sep 18 12:35:09 charon 54184 11[NET] <3482> received packet: from 178.176.76.143[29056] to 81.5.119.144[500] (604 bytes)
Sep 18 12:35:09 charon 54184 11[ENC] <3482> parsed IKE_SA_INIT request 0 [ SA KE No N(REDIR_SUP) N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) ]
Sep 18 12:35:09 charon 54184 11[CFG] <3482> looking for an IKEv2 config for 81.5.119.144...178.176.76.143
Sep 18 12:35:09 charon 54184 11[CFG] <3482> candidate: 81.5.119.144...0.0.0.0/0, ::/0, prio 1052
Sep 18 12:35:09 charon 54184 11[CFG] <3482> found matching ike config: 81.5.119.144...0.0.0.0/0, ::/0 with prio 1052
Sep 18 12:35:09 charon 54184 11[IKE] <3482> local endpoint changed from 0.0.0.0[500] to 81.5.119.144[500]
Sep 18 12:35:09 charon 54184 11[IKE] <3482> remote endpoint changed from 0.0.0.0 to 178.176.76.143[29056]
Sep 18 12:35:09 charon 54184 11[IKE] <3482> 178.176.76.143 is initiating an IKE_SA
Sep 18 12:35:09 charon 54184 11[IKE] <3482> IKE_SA (unnamed)[3482] state change: CREATED => CONNECTING
Sep 18 12:35:09 charon 54184 11[CFG] <3482> selecting proposal:
Sep 18 12:35:09 charon 54184 11[CFG] <3482> no acceptable ENCRYPTION_ALGORITHM found
Sep 18 12:35:09 charon 54184 11[CFG] <3482> selecting proposal:
Sep 18 12:35:09 charon 54184 11[CFG] <3482> no acceptable ENCRYPTION_ALGORITHM found
Sep 18 12:35:09 charon 54184 11[CFG] <3482> selecting proposal:
Sep 18 12:35:09 charon 54184 11[CFG] <3482> no acceptable ENCRYPTION_ALGORITHM found
Sep 18 12:35:09 charon 54184 11[CFG] <3482> selecting proposal:
Sep 18 12:35:09 charon 54184 11[CFG] <3482> no acceptable INTEGRITY_ALGORITHM found
Sep 18 12:35:09 charon 54184 11[CFG] <3482> selecting proposal:
Sep 18 12:35:09 charon 54184 11[CFG] <3482> no acceptable ENCRYPTION_ALGORITHM found
Sep 18 12:35:09 charon 54184 11[CFG] <3482> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1536, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Sep 18 12:35:09 charon 54184 11[CFG] <3482> configured proposals: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024
Sep 18 12:35:09 charon 54184 11[CFG] <3482> looking for IKEv2 configs for 81.5.119.144...178.176.76.143
Sep 18 12:35:09 charon 54184 11[CFG] <3482> candidate: 81.5.119.144...0.0.0.0/0, ::/0, prio 1052
Sep 18 12:35:09 charon 54184 11[IKE] <3482> remote host is behind NAT
Sep 18 12:35:09 charon 54184 11[IKE] <3482> received proposals unacceptable
Sep 18 12:35:09 charon 54184 11[ENC] <3482> generating IKE_SA_INIT response 0 [ N(NO_PROP) ]
Sep 18 12:35:09 charon 54184 11[NET] <3482> sending packet: from 81.5.119.144[500] to 178.176.76.143[29056] (36 bytes)
Sep 18 12:35:09 charon 54184 11[IKE] <3482> IKE_SA (unnamed)[3482] state change: CONNECTING => DESTROYING -
На андроиде тоже не работает.....)
Я предполагаю что проблема где то с настройкой сертификатов или на радиусе...подскажите пожалуйста, на винде то всё ок -
@nzlv
Как я Вам говорил , используйте Apple Configurator для таких настроек . Все четко и наглядно (у Вас несовпадение комбинации настроек фазы 1 )
Для примерафаза 1 PF / Apple Configurator
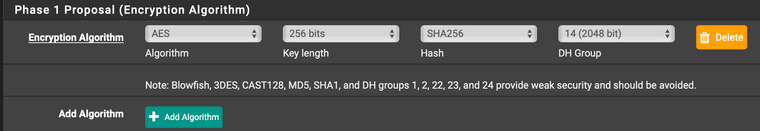
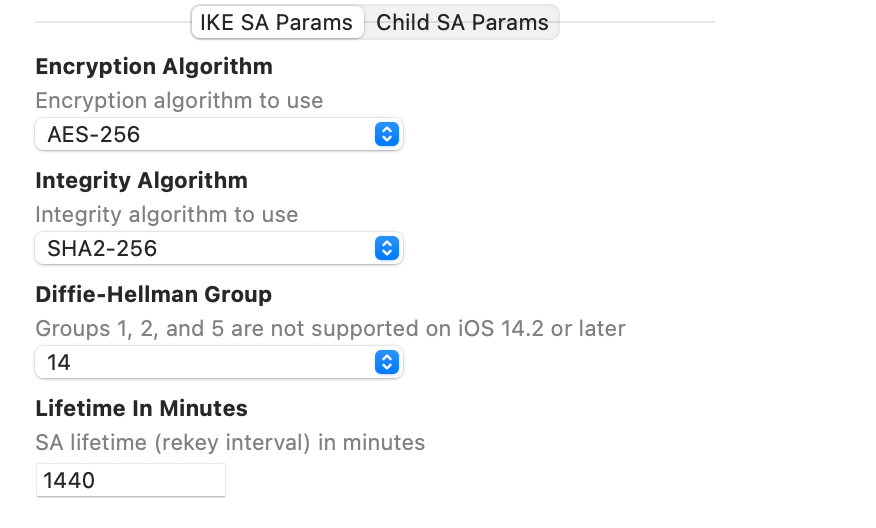
все совпадает , фаза-2 аналогично
и соединение успешно устанавливается
Вы используете стандартного клиента Apple , который использует свои собственные настройки фазы-1 / фазы-2 , и эти настройки просто не совпадают с Вашими