Upgrade existing Site to Site Open VPN Tunnels Shared Key to TLS
-
Hello everyone !
I would need some comments and suggestions on site to site tunnels that need to be updated, according to pfSense recommendations.
My setup is site to multisite setup, Open VPN Tunnels with shared key.
The pfSense versions are mixed: 2.4.5, 2.5, 2.6. (1 server, many clients)Since i never did this setup in the past, my main concern is:
- Do i have to create certificate authority and CA on the server for each client, or 1 for all clients.
- Do i have to export the certificate on file form, and pass it to the client ? (like remote access Open VPN), or just the TLS Key?
- When those certificates need to renew ? and how to update the client ?
- what else do i have to pay attention to ? Thanks for any suggestions.
-
@bambos said in Upgrade existing Site to Site Open VPN Tunnels Shared Key to TLS:
Do i have to create certificate authority and CA on the server for each client, or 1 for all clients.
You need to create a CA for the VPN server. Then generate a server cert and one cert for each client with this CA.
Do i have to export the certificate on file form, and pass it to the client ? (like remote access Open VPN), or just the TLS Key?
You need also to import the certificates on the clients. In pfSense you can use the "import an existing certificate" method and edit and copy the certificate and private key from the server and paste them on the client using the clipboard.
When those certificates need to renew ? and how to update the client ?
When generating a client cert, pfSense requests the livetime.
pfSense will remember you, when the expiration comes near.what else do i have to pay attention to ? Thanks for any suggestions.
You can generate all necessary certificates and import them on the clients, while you still use the shared key VPN. If all is done, switch over to TLS, but ensure that you copy and paste also the TLS key to each client, before saving the settings.
-
@viragomann Thanks for your directions.
On the server i have already created CA and Server certificate.
How to create client certificate? From certificates tab, or from certificate revocation ?On the client site, i have pasted the TLS key, and i'm about to import the certificate. (*.crt file). During the configuration on the client, it asks also for CA , revocation and client certificate. not clear there how to import from the .crt file, since on the import certificate tab ask for certificate data and private key data.
Thank you for your help. -
@bambos said in Upgrade existing Site to Site Open VPN Tunnels Shared Key to TLS:
How to create client certificate?
On the Certificates tab hit Add, the "create internal certificate" method is already selected by default. Select the proper CA and enter the desired settings.
On the client site, i have pasted the TLS key, and i'm about to import the certificate. (*.crt file). During the configuration on the client, it asks also for CA , revocation and client certificate.
On the client you need to import the CA and the client certificate with the private key.
You can simply copy and past the data via clipboard.For the CA, edit the CA on the server, on the client hit Add on the CA tab and select import method. Then copy the content of the "Certificate data" box to the client. The private key is not needed on the client.
You can the same with the client cert, but here you also need the private key data.
-
@viragomann Thanks ! for your help, works like a charm.
I just notice something i don't know how come, seems strange to me.
When i had shared key setups (site to site), i gain access to both client and server by connecting to the server using Remote Access OpenVPN (added routings on the remote access VPN server). Before, it needs to have on the VPN clients Remote Networks text box, except the Local Networks also the virtual tunnel network of the remote access VPN (so it creates the routing).
With this new setup now, this extra remote network on the client side (for the remote access vpn tunnel) is NOT needed, and i'm able to access networks on the clients side over the remote access VPN just by the remote access routing.
Does this difference has to do with the VPN Site to Site Tunnel ?
What might be the difference ? -
@viragomann Hello !
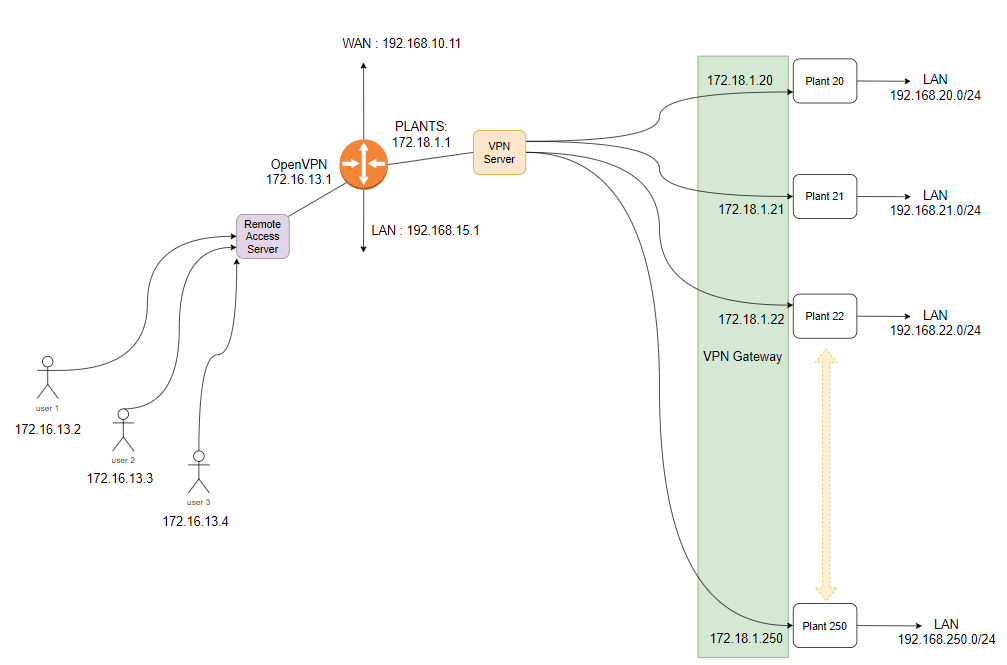
i have a new implementation with your suggestion, having common CA and per client certificate, using the below topology:
Even i use the client specific overrides and adding specific ip for the client (for example 172.18.1.20) the remote network (192.168.20.0/24), is not going to the system routes, and i have to add manually the gateway (for example 172.18.1.20) and then manually add static route for the remote network. (like that is Working!)
Is this supposed to be like that ?? or i have something configured wrong ?
-
@Bambos
No, routes should be added automatically by OpenVPN. It's recommended to not create static routes for OpenVPN remote sites.In OpenVPN you have to state the remote networks twice. Once in the server settings and a second time in the CSO.
Presumed you have multiple clients, which you want to access the networks behind, connecting to a single server, you have to enter all remote networks in the server settings, but only the respective ones in the CSO.Note that you cannot see the correct remote IPs in the servers routing table. Instead all routes go to the first clients address. The particular routing is done inside OpenVPN then.
If you think, you have configured this correctly, but it doesn't work, maybe the CSO is not applied due to wrong settings.
Ensure that the common name in the CSO is equal to the CN in the client certificate.To verify if the CSO is applied properly, enhance the servers log verbosity level to 4, reconnect the client and check the log after.
-
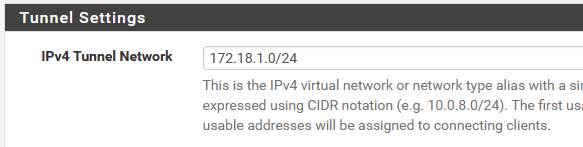
@viragomann i have 2 sites online now for the test. 30 and 31.
Server Tunnel
Remote Networks in server settings:
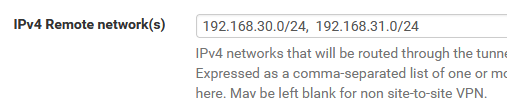
CSO Client 30
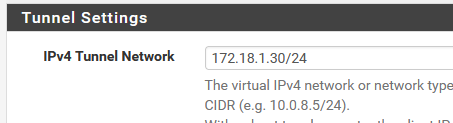
CSO remote networks
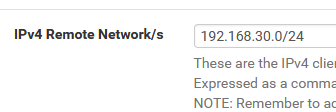
The CSO Policy seems to apply correctly, since the clients are getting the intended IP.
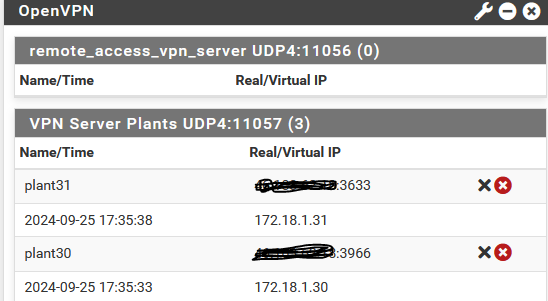
Diagnostic -> Routes (It looks like are created but with the wrong gateway)

It seems that is following site to site VPN, while the pfsense is IP 1 and the client is IP2. (like shared key site to site with dedicated VPN Server). But with this topology obviously is creating something wrong. That's why i go the route of gateway creation and static route.
Please comments !!
-
@Bambos said in Upgrade existing Site to Site Open VPN Tunnels Shared Key to TLS:
The CSO Policy seems to apply correctly, since the clients are getting the intended IP.
Read my post above, please.
-
@viragomann I have set the verbosity of OpenVPN server to 4 and check the openvpn logs :
i'm not able to understand exactly all the logs, but there is a point when the gateway is created with IP 2 (the wrong gateway), and a point that the ip is assigned. (the correct according CSO)
Also there is a read client specific options line.
What we searching for ?Sep 25 18:54:08 openvpn 4548 plant30/publicIP:44210 MULTI_sva: pool returned IPv4=172.18.1.2, IPv6=(Not enabled)
Sep 25 18:54:08 openvpn 4548 plant30/publicIP:44210 OPTIONS IMPORT: reading client specific options from: /var/etc/openvpn/server3/csc/plant30
Sep 25 18:54:08 openvpn 4548 plant30/publicIP:44210 MULTI: Learn: 172.18.1.30 -> plant30/publicIP:44210
Sep 25 18:54:08 openvpn 4548 plant30/publicIP:44210 MULTI: primary virtual IP for plant30/publicIP:44210: 172.18.1.30
Sep 25 18:54:08 openvpn 4548 plant30/publicIP:44210 MULTI: internal route 192.168.30.0/24 -> plant30/publicIP:44210
Sep 25 18:54:08 openvpn 4548 plant30/publicIP:44210 MULTI: Learn: 192.168.30.0/24 -> plant30/publicIP:44210 -
Sorry, I quoted the wrong line above.
Shoould be this one:
@Bambos said in Upgrade existing Site to Site Open VPN Tunnels Shared Key to TLS:Diagnostic -> Routes (It looks like are created but with the wrong gateway)
The point is
@viragomann said in Upgrade existing Site to Site Open VPN Tunnels Shared Key to TLS:Note that you cannot see the correct remote IPs in the servers routing table. Instead all routes go to the first clients address. The particular routing is done inside OpenVPN then.
-
@viragomann ok, i got it !! thank you.
-
@Bambos said in Upgrade existing Site to Site Open VPN Tunnels Shared Key to TLS:
Sep 25 18:54:08 openvpn 4548 plant30/publicIP:44210 MULTI: Learn: 192.168.30.0/24 -> plant30/publicIP:44210
BTW: this is the line showing, that the route was set inside OpenVPN.