Firewall rules do not work as expected - I assume I have an issue in understanding :)
-
Hi,
today I started playing around with pfsense again after many years.
So far I have a basic setup
only two Network Ports are used.
IGB0 (LAN)
IGB3 (WAN)IGB0 has following interfaces
LAN
NETWORK - VLAN11
IOT - VLAN21
GUEST - VLAN91
To IGB0 a TP-Link EAP 650 is plugged in. No switch. The EAP creates the VLANs according to the different SSID.Interfaces are setup and working - at least when it comes to DHCP. Connecting to each SSID I´ll get a different IP as expected.
Now I tried to define a few rules to test the ruleset.
Following rules on all interfaces exempt GUEST:
Protocol ANY / Source ANY / Destination ANY / Action PASSOn the GUEST interface I tried out the ruleset:
Protocol IPv4 UDP / Source GUEST net / Destination ANY / Port 53 / Action Pass
Protocol IPv4 TCP/ Source GUEST net / Destination ANY / Port 80 / Action Pass
Protocol IPv4 TCP / Source GUEST net / Destination ANY / Port 443/ Action Pass
Protocol ANY / Source ANY / Destination ANY / Action BlockWith this ruleset on GUEST interface I expected that I can open only a website. But I can access the pfsense Webif and in can open a FTP connection. Basically everything works. I can even open the EAP Webif which is on LAN interface.
What is wrong?
Thank you!
Frosch1482 -
@Frosch1482 well you have rules that say guest can go to ANY on 80 and 443.. Do you have pfsense gui on some othe rport. Because your rules allow to go anywhere.
A common misunderstanding I think with new users is a state.. If you go to xyz a state is created.. Even if you then create a rule that would block access to xyz.. Until that state goes away it would allow access.. Firewall rules prevent the creation of a state or allow for it. But if a state is there already the state is what allows the traffic.
That last rule is not really needed unless you don't want to log or something because by default if there is not a rule that allows, then the traffic is blocked by the default deny.
Also rules in floating are evaluated first, if you had some rule allowing even if your rules on the specific interface would not - the floating rule could be allowing the traffic.
As to ftp on port 21.. do you happen to have the ftp proxy installed?
-
I forgot to mention that I reset all states (Diagnostic --> States --> reset states)
I did a reboot as well just to make sure (Dummy approach)Nothing.
My first Idea was "old states" as well. Will give it another try :)
-
@Frosch1482 what port do you have pfsense gui listening on if its 80 or 443 your rules allow that access.. You sure your hitting that interface and not one of your any any interfaces..
When traffic is allowed, look in your state table.. What interface is allowing it?
-
Ok we can discuss about the webif. There you are probably right.
But this is wiered.GUEST tcp 10.0.91.2:50824 -> 44.241.66.173:21 ESTABLISHED:ESTABLISHED 19 / 21 2 KiB / 3 KiB
I still can establish a FTP connection on port 21.
I don´t get it....
Do you think a factory reset might solve the issue? The system had a lot of Interfaces which i deleted and recreated today.
-
@Frosch1482 do you have the ftp client proxy package installed?
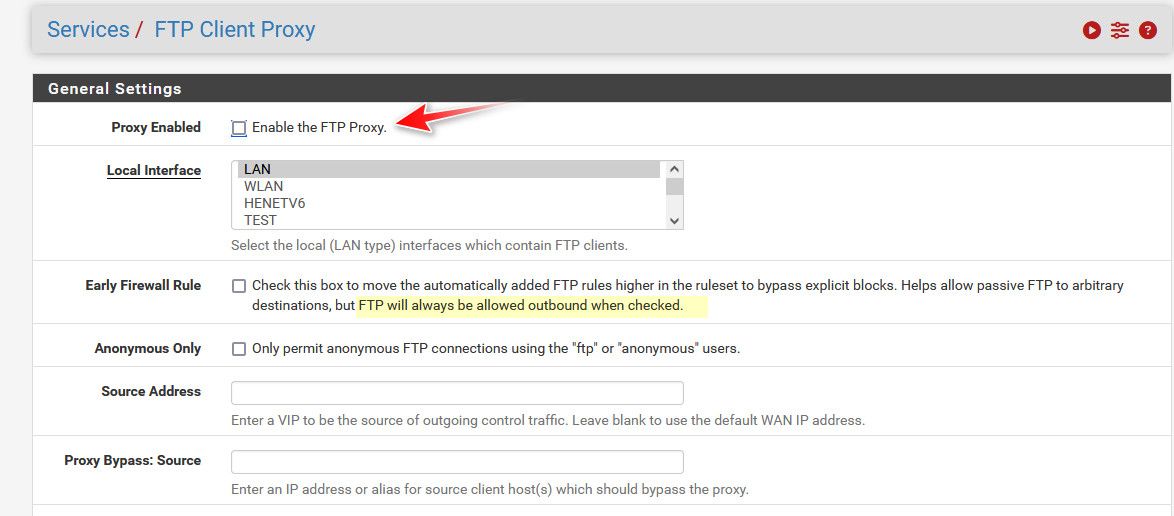
This would create a hidden rule
rdr pass on igb0 inet proto tcp from any to any port 21 -> 127.0.0.1 port 8021Which would allow ftp even if you didn't have a rule allowing 21
-
@johnpoz No I don´t have this package installed.
but anyhow after a reset to factory settings and update to 2.7.2 it seems to work better (at least port 80 / 443) is blocked if I do not configure a specific rule for it. This is good.
I´m currently testing. But somehow I can still reach out other addresses on VLANS or the LAN interface. need to check state tables :)
Status: Resolving address of ftp.dlptest.com Status: Connecting to 44.241.66.173:21... Error: Connection timed out after 20 seconds of inactivity Error: Could not connect to server Status: Waiting to retry...Now FTP looks good. Seems to work now.
Strange: Factory reset was needed to get that stuff working. Probably some broken config somewhere
-
@Frosch1482 highly unlikely unless you had that package installed for ftp..
To be honest posting text like that isn't always very helpful in helping you figure out the rules, screen shot is always better.
Or your rules were not actually being applied?
Your rules you posted would allow access to 80 or 443 on any IP, be it public or some other vlan.. Here is a example of locked down network that would not be allowed to talk to your other vlans
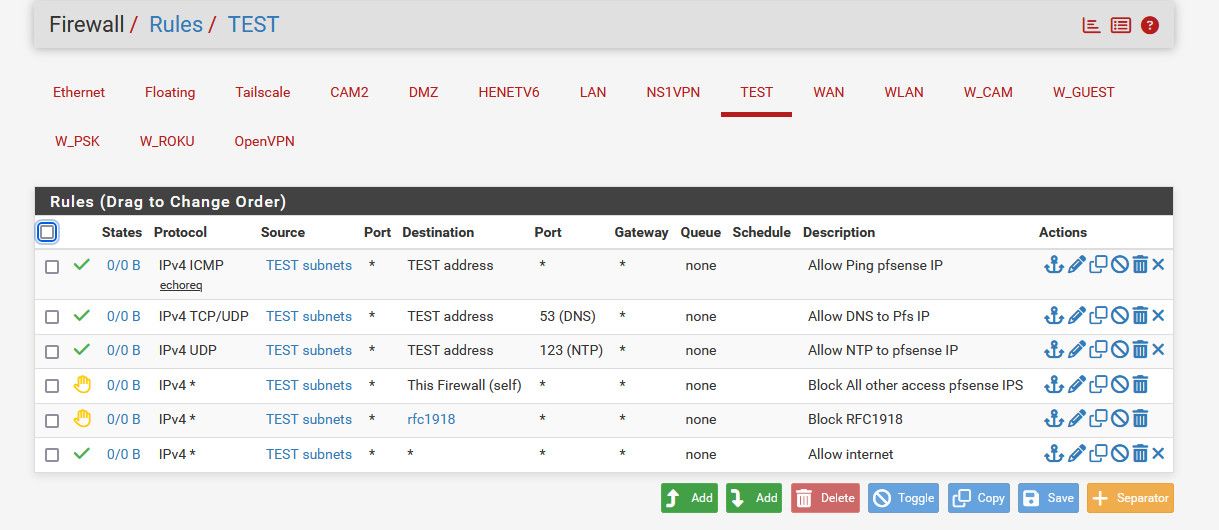
-
@johnpoz What is in the Alias RFC1918?
I suppose all other networks / Vlans that should not be reached.I think about a similar solution, but in this case i need to create several aliases. This doesn´t sound smart for me :)
-
@Frosch1482 the rfc1918 is just that, an alias that contains all the rfc1918 networks.. Are you other vlans not rfc1918?
Why would you need to create several to block rfc1918? You can have lots and lots of aliases if that is what makes sense for what your wanting to do.. Which you have not actually expressed in any sort of detail that would be helpful for someone wanting to help you.
I gave you an example of simple set of rules that would allow a "guest" sort of network to access the internet - but not any of your other network (if they are rfc1918) nor any pfsense gui IPs, even if the wan is public and changes.. That is the "this firewall" alias.
Those rules I gave as example could be adjusted to whatever your needs are.
Maybe you want to allow any dns? Maybe you don't want to allow ntp access or ping of pfsense IP on your guest network, etc.