optimize config with GeoIP Alias
-
On a Netgate 2100 we run pfblockerng-devel-3.2.0_18
I registered at Maxmind and defined a geoip-alias containing only the IPs of "DACH" = Austria, Germany, Switzerland.
The customer still runs legacy portforwardings for various server machines:
their clients access server vms via ~30 separate ports on WAN, forwarded to RDP on the target machines.
Yes, unsafe and bad.
I suggested to at least limit access to these ports to these 3 countries as we are located in AT, to avoid attacks from elsewhere.
Before anyone suggests this: they are in the process of switching all the customers to VPN-access already.
So we have NAT-rules like:
Source: geoip-alias "DACH"
Target: WAN-IP
Port: someport
forwarded to: internal IP, Port 3389 (MS RDP)works so far
It only slows down the WebGUI etc
I think of optimizing this ... maybe better define a list of all the exposed ports as Alias and add a single FW-rule above the NAT-rules ( under Firewall-Rules?) that allows traffic to these ports from the GeoIP-list only? And remove the GeoIP-list from the various NAT-rules?
hints welcome, I am sure this can be done much more efficient.
thanks -
@sgw said in optimize config with GeoIP Alias:
It only slows down the WebGUI etc
why would you think that would slow down the web gui?
-
@johnpoz well, it's slow ;-)
Editing NAT-rules takes a long time, load is high.
I assume generating the IP-lists for the mouse-overs takes time or so.
Surfing is OK, the routing and firewalling seems not to be slowed down (much ..?). -
@sgw I have never seen such a slow down.. I can call up a table that as 147k entries and it pops..
if I mouse over one of my aliases with over 120k entries in it - the mouse pop up is pretty much instant
Do your aliases have millions and millions of entries?
Those tables are not populated on the fly.. They get updated/populated on a schedule, native aliases that resolve stuff are like every 5 minutes.. A table of Ips that pfblock downloads will be updated per the schedule you setup in pfblocker..
If you mouse over one of your aliases and it take a long time to pop up, you got something else going on. There was some issues with pfblocker consuming large amounts of cpu, but I thought that was corrected?
https://forum.netgate.com/topic/190240/pfblockerng_devel-commit-reverse
-
when I click Firewall - NAT it takes around 25-30 seconds to open.
This might be longer with a cold browser cache, I am not sure.The mouseover shows 10k lines "only" ;-) ... unsure how to see how many lines the alias really contains.
The admin there was complaining, he edited a lot of the NAT entries yesterday and it took him a lot of time.
Maybe there other issues hidden.
The alias is of type "Alias Native" and updated once a day only, if that is relevant.
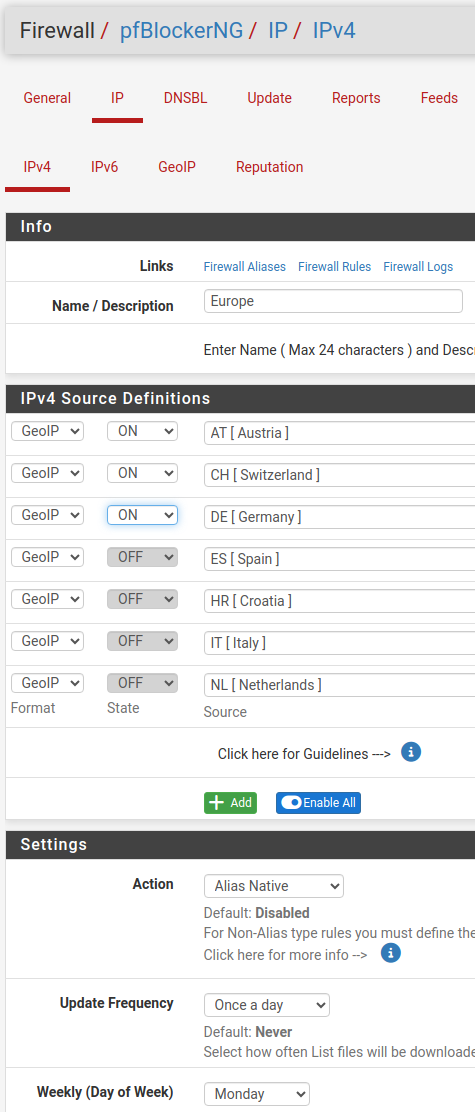
I might disable this restriction for some NAT-rules to test.
That's why I thought it might be more clever to filter ONCE for GeoIP on top and not for each NAT-rule in detail.
Or doesn't that make a difference in the overall load?
Remember: netgate-2100
... right now 22% of memory used, that's very ok. and 50-70% CPU.
That box might be too small anyway, there are ~20 ovpn-clients also connected all day long (I should mention this, sry). We consider upgrading hardware anyway for even more ovpn-connections (while getting rid of those legacy port-fwds).
EDIT: applied the patch from https://forum.netgate.com/post/1187377 now, checking things. thanks so far!
-
@sgw There is an option in System -> General Setup to disable Alias Popups
-
@NogBadTheBad this helps a lot, thanks!
applied the patch and rebuilt the geoip lists as mentioned also
looks better now
-
@sgw said in optimize config with GeoIP Alias:
and 50-70% CPU.
That seems high for the box doing nothing but routing and firewalling.. How many states do you have currently, how much traffic is being routed?
But yeah if your cpu is running at 50 some % - interaction with the gui in any form might be a little bogged down.
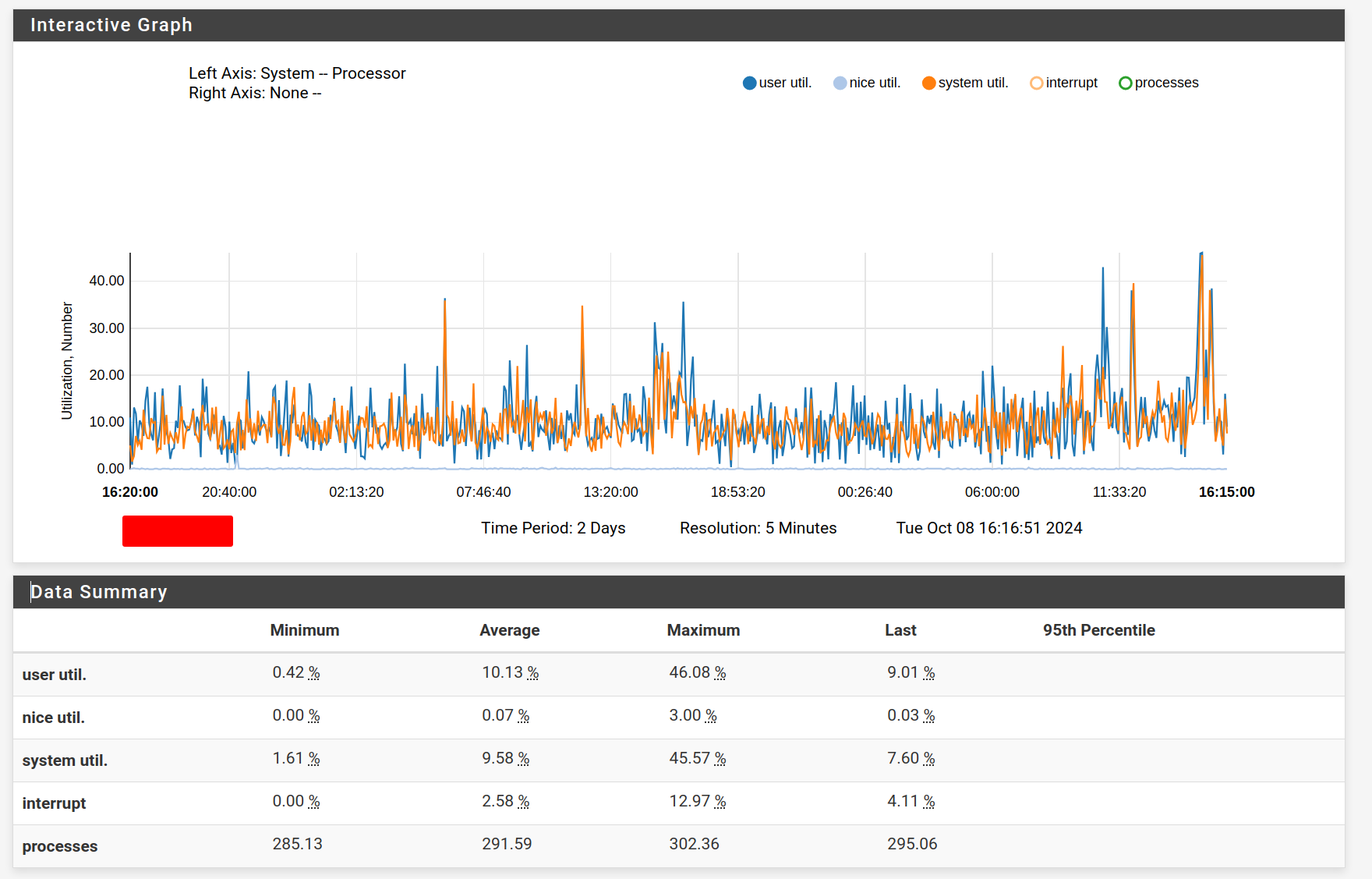
Can you post up your cpu monitoring graph.. Example here is mine over 2 days, not showing the interrupts and processes so can see cpu
-
-
@sgw well that doesn't seem all that crazy.. But you do have something going on for sure if takes you 20-30 seconds to call up a rule.. Does that delay happen when just a normal rule or nat without any aliases in it?
If I go to edit this port forward
Its pretty much instant.
-
@johnpoz I get back here tmrw ... it's late already in my timezone.
Thanks so far!edit: currently sick since monday ... I'll get back here asap