surfshark guide for pfsense wireguard
-
@Bob-Dig LOL YES! But insomnia always wins so I'm always up ALL night!
I watch them literally every morning, spot check during the day, and at night.
I make it a ritual to constantly check because I have Wireguard on my devices to 'remote' to my pfSense to take advantage of pfBlockerNG and Surfshark/IVPN VPN services.
I did not include ANY kill switches like IVPN suggests (not too sure if the Surfshark had that on their guide). I only included static routes and rules to allow from VPN server to WAN - although IDK if this is needed since this was part of the kill switch.
I am constantly checking on dnsleaktest.com for any leaks.. but so far so good, only the DNS I specified have been popping up. But I am thinking of just removing VPN DNS servers and hosting it 'in-house.'
I will add Germany to my list and monitor. I am curious as IVPN has been behaving but I see Surfshark has been a bit crazy with latency and packet loss...
I get a good 1.21Gbps - 1.25Gbps, I pay my ISP for 1.2Gbps.. so I call it good! :)

I have about 8 VPN connections on my pfSense and make sure I have a monitor IP on them to check latency and all that good stuff:


-
@rtorres said in surfshark guide for pfsense wireguard:
I did not include ANY kill switches like IVPN suggests (not too sure if the Surfshark had that on their guide).
So there is one option in pfSense you really should tick: Skip rules when gateway is down (SystemAdvancedMiscellaneous)

For my setup, it looks like BERLIN has continuous problems but also I have not seen the same flakiness now having a "Killswitch" for OpenWRT. So for me it could still be a problem in pfSense.
-
Yes, I have a very good tutorial in PDF format specifically created for surfshark wireguard on Pfsense.
Apparently you can't attach files here so I put it on my Google drive.
[Bad link removed]
-
Your link is restricted, I can't open it.
-
@Irontalon said in surfshark guide for pfsense wireguard:
Yes, I have a very good tutorial in PDF format specifically created for surfshark wireguard on Pfsense.
Apparently you can't attach files here so I put it on my Google drive.
snipped link
It says "You need access"
Can u please modify the settings to allow the access for all? -
@savostian333 you have a 1 post wonder give some random link to a pdf, Not sure why anyone would follow that link
-
@johnpoz But he also is. I would delete both users/posts if I would be in charge, better save than sorry.
-
Mmm, killed it for now. Let's see...
-
@johnpoz said in surfshark guide for pfsense wireguard:
@savostian333 you have a 1 post wonder give some random link to a pdf, Not sure why anyone would follow that link
I was interested. Is that an issue?

-
It could be legit. Link was broken and we wait for an update from the poster....
-
danger will robinson, danger
-
https://www.wundertech.net/how-to-set-up-wireguard-on-pfsense/
https://www.reddit.com/r/PFSENSE/comments/lmv1cp/how_to_setup_wireguard_on_pfsense_252102_with/
https://www.youtube.com/watch?v=CXFbEbzFEXw
https://www.paolotagliaferri.com/create-wireguard-vpn-tunnel-with-pfsense-2-5-0/
https://coygeek.com/docs/pfsense-wireguard/ - 404
These are the links I found most helpful.
-
Conversation I had with technician at Surf Shark about two WireGuard tunnels simultaneously:
another question can I use the same tunnel and have multiple gateways(Peers) going to different surfshark servers through the same tunnel?
Saul Buchanan
's avatar
Not at the same time, but you can use the same tunnel with different peers, yes.
Okay, can I create individual tunnels for each peer (Surfshark server) I wish to use as a gateways.
I have done this using the openvpn protocol
Saul Buchanan
's avatar
Essentially yes.
Isn't the problem generating keys for each tunnel?
Saul Buchanan
's avatar
Not really, as you can use the same private keys with multiple tunnels. I would just like to emphasize that multiple connections at a time from the same device will most likely encounter issues.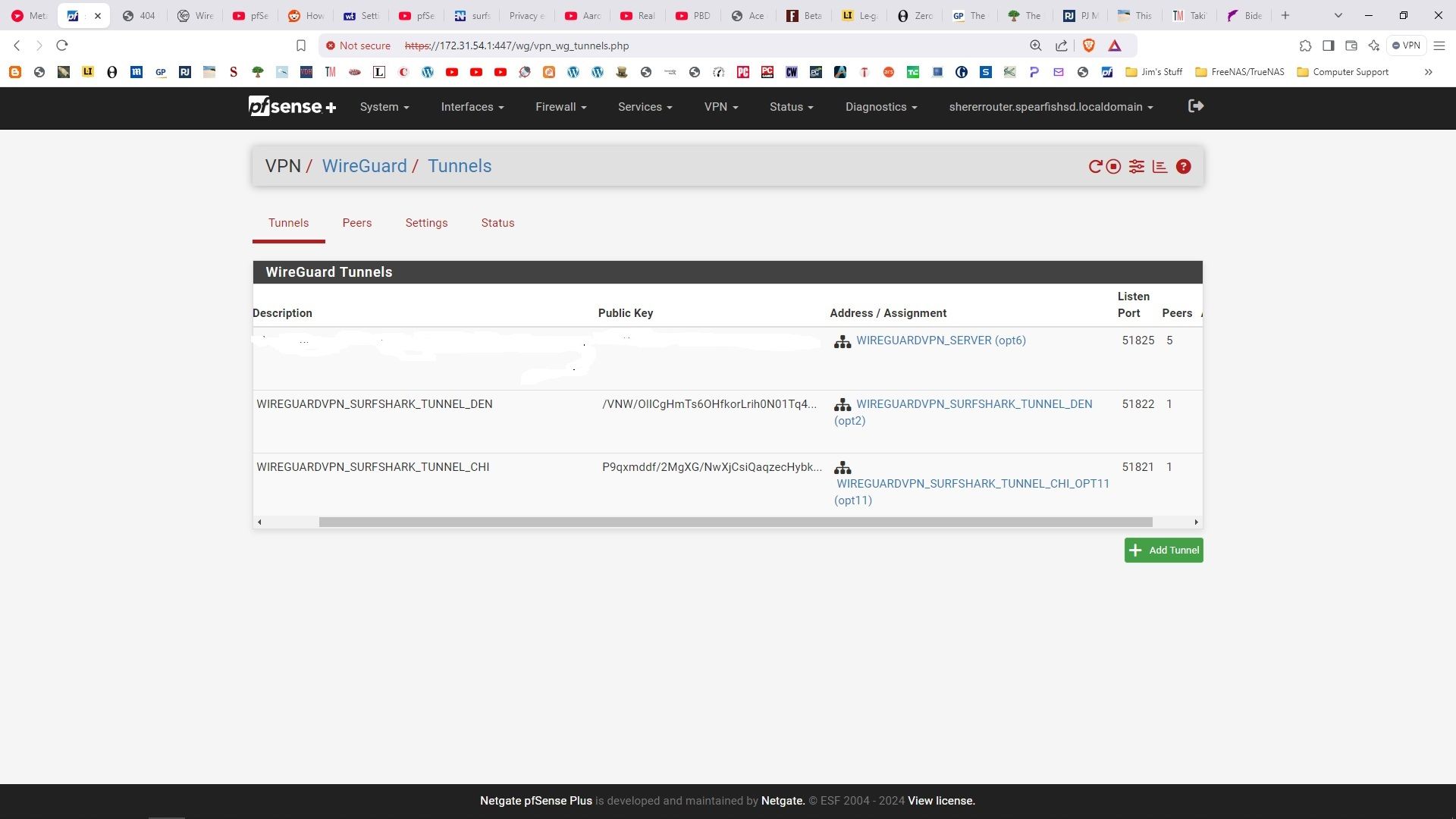
The challenge I ran into was thinking the endpoint port (51820) had to match the tunnel port.. It cannot be changed - obviously it is set by SurfShark, but it means both tunnels share the same endpoint port.
It seems to work:
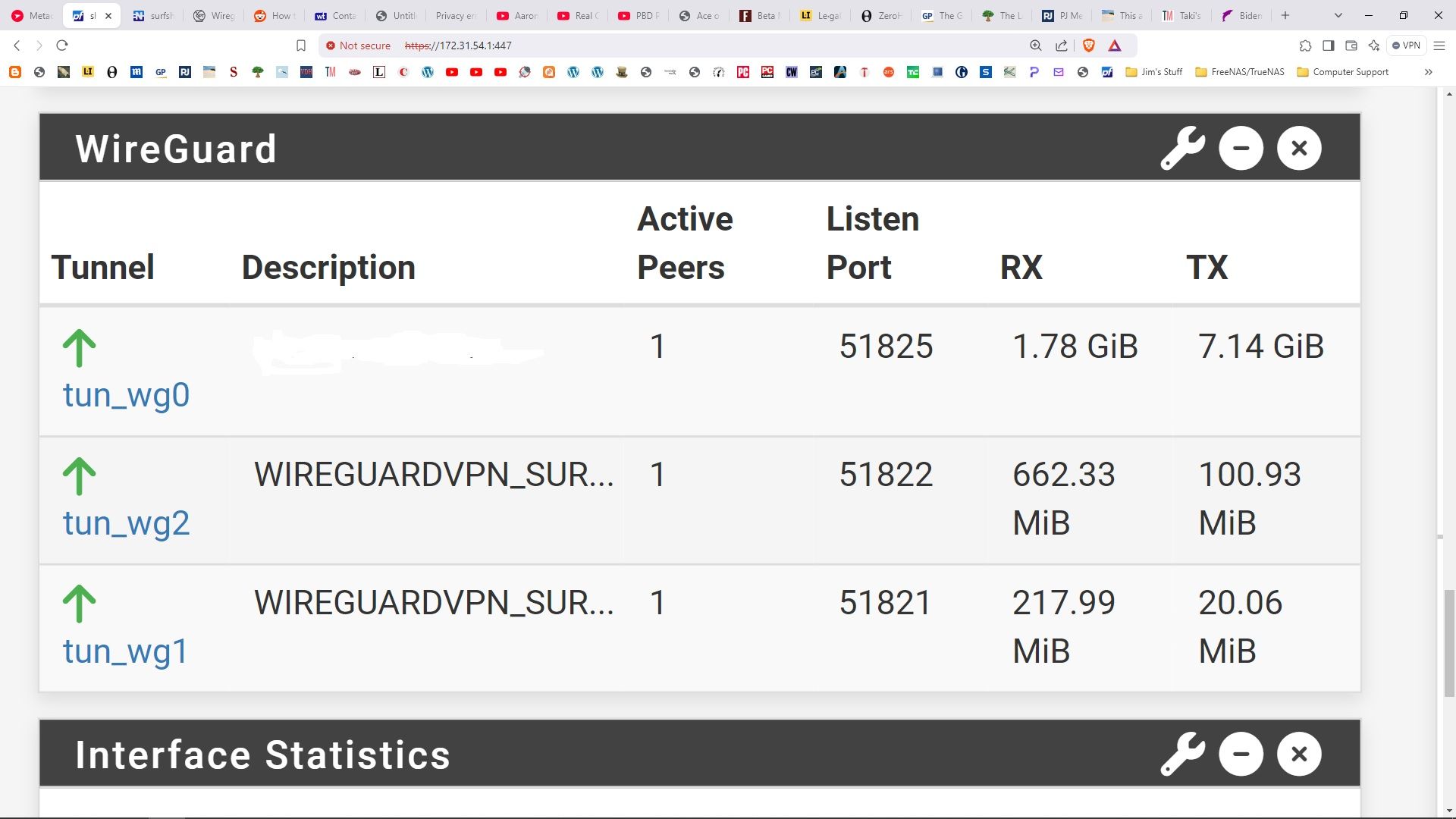
-
T The Party of Hell No referenced this topic on