Help with VLAN configuration
-
I currently have my 192.168.0.0/24 network working without issue.
I would like to add a VAP (172.16.0.0/24 VLAN 4) on the TP-Link Access Point and introduce the DIR-880L Access Point (192.168.1.0/24 VLAN3). I don't currently have any VLANs configured and only a single network cable running from the T1500G to the Archer C9 that is bridged via MOCA. I'm starting by attemptepting to get VLAN3 working first.
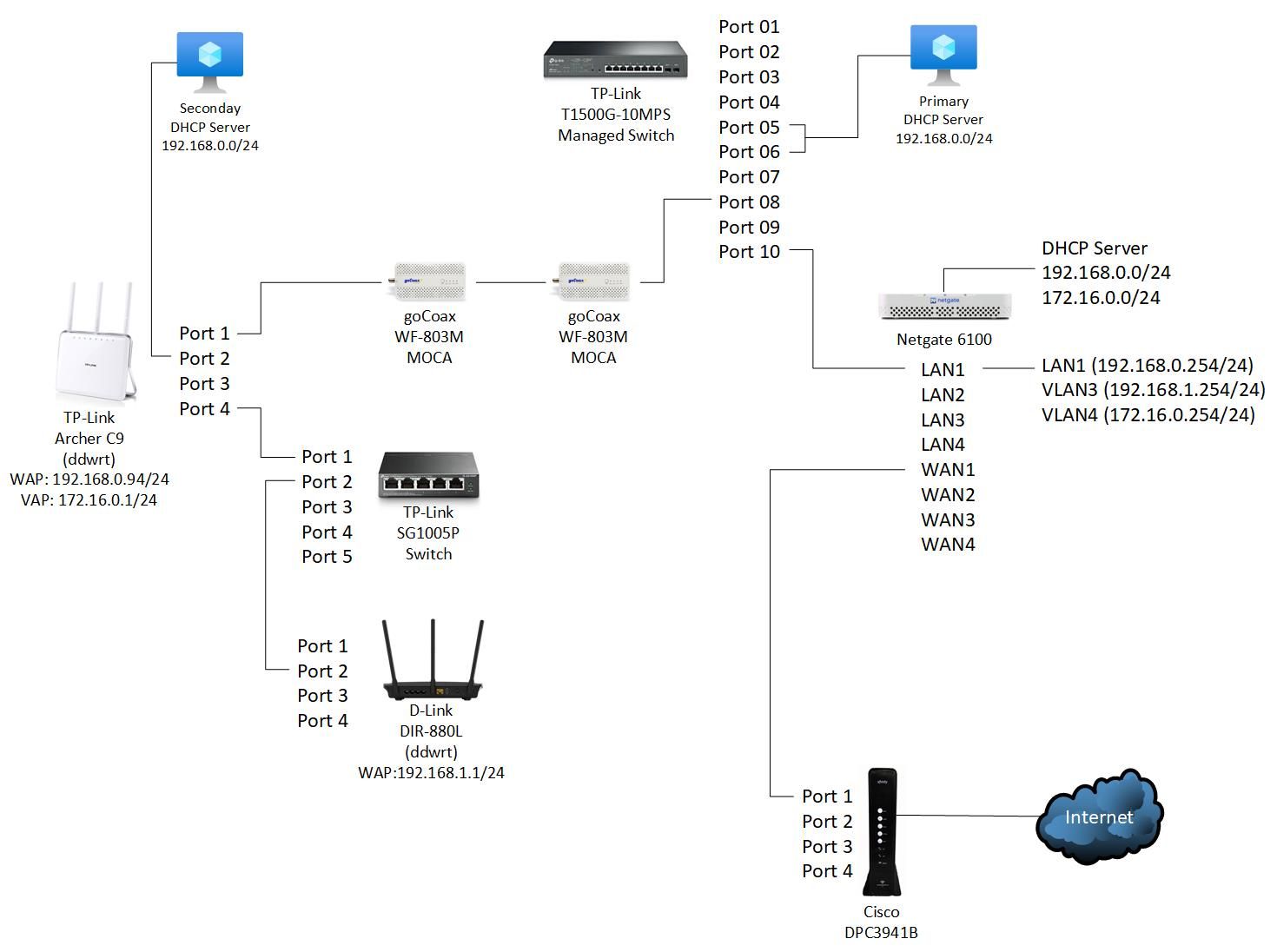
I have the Archer C9 configured as follows:
My assumption is that all traffic over Port 4 on the Archer to the SG1005SP will be tagged as VLAN3.
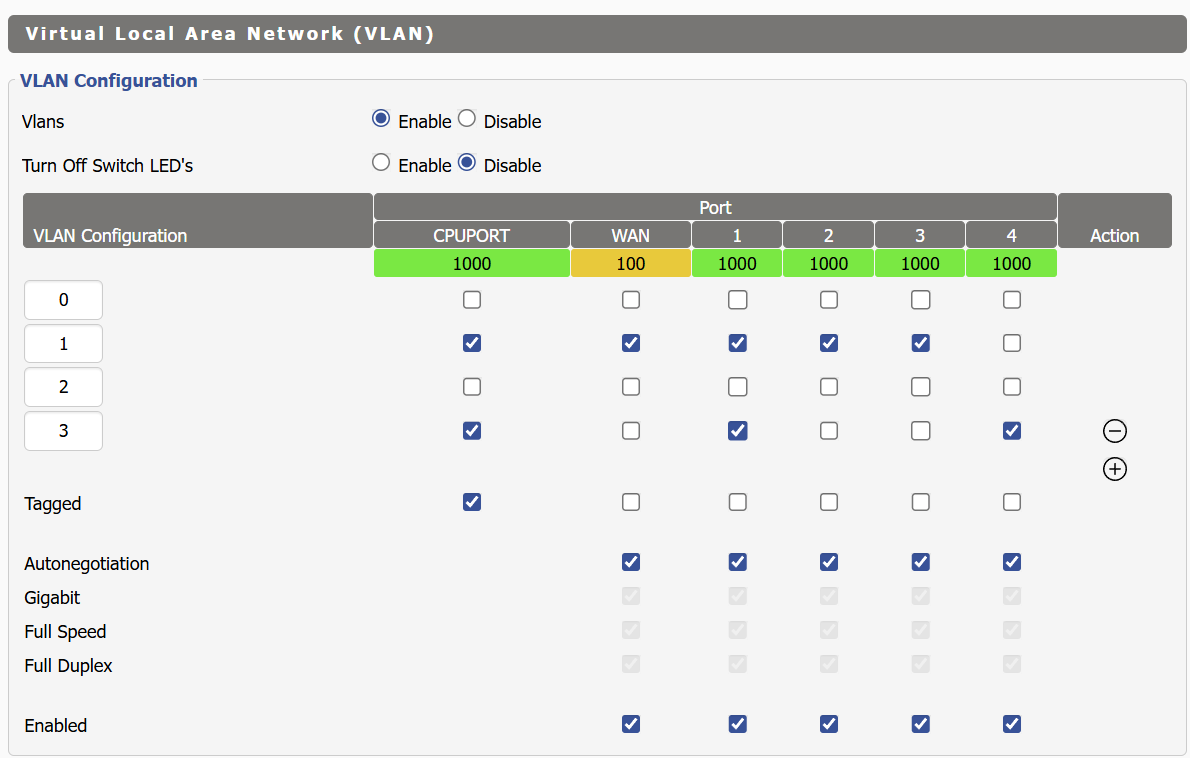
The DIR-880L is configured as follows:
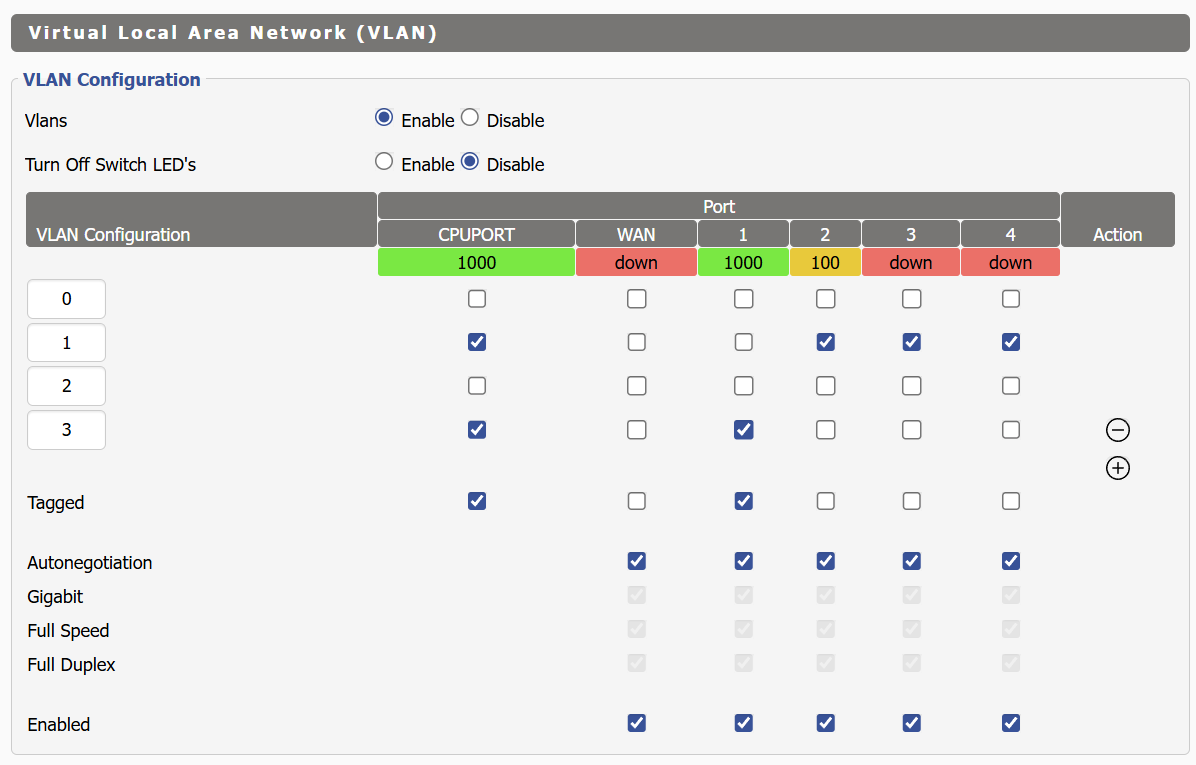
The T1500G-10MPS is configured as follows:
The Netgate 6100 setup as follows:
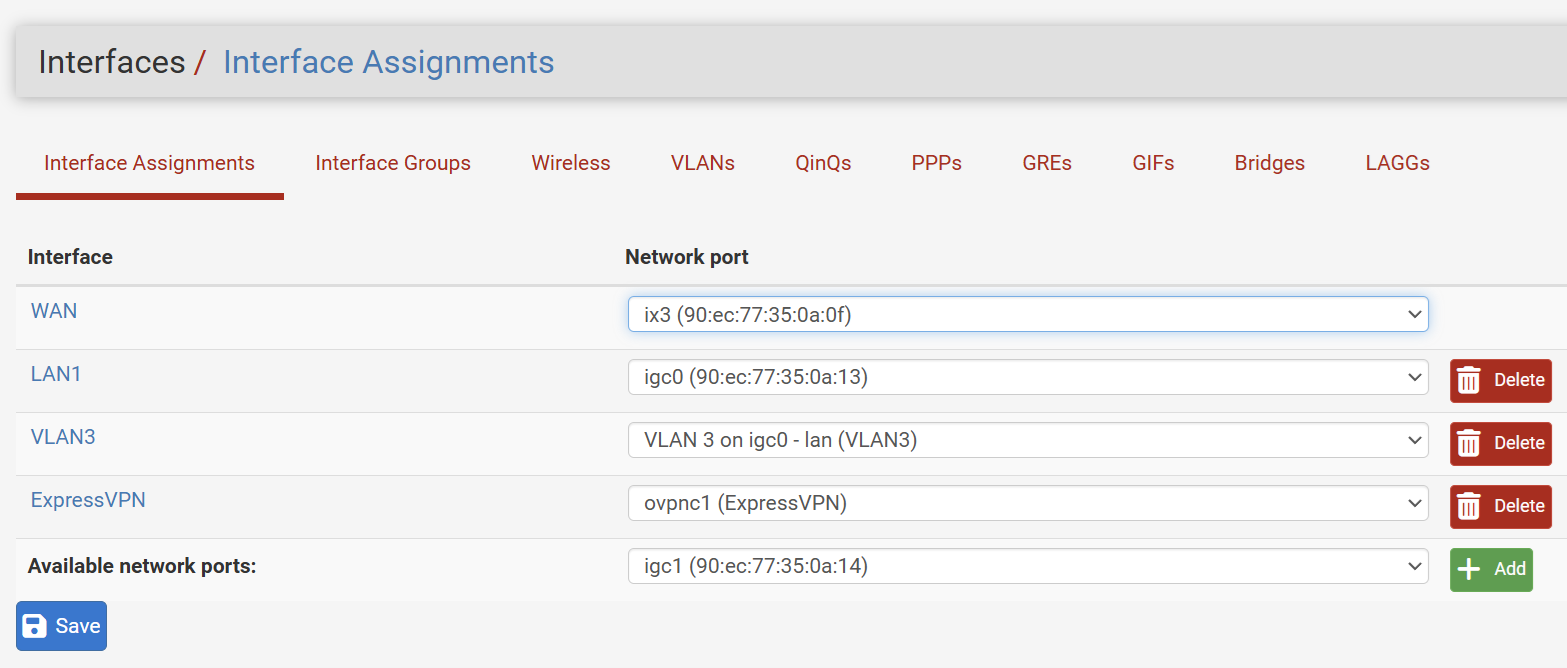
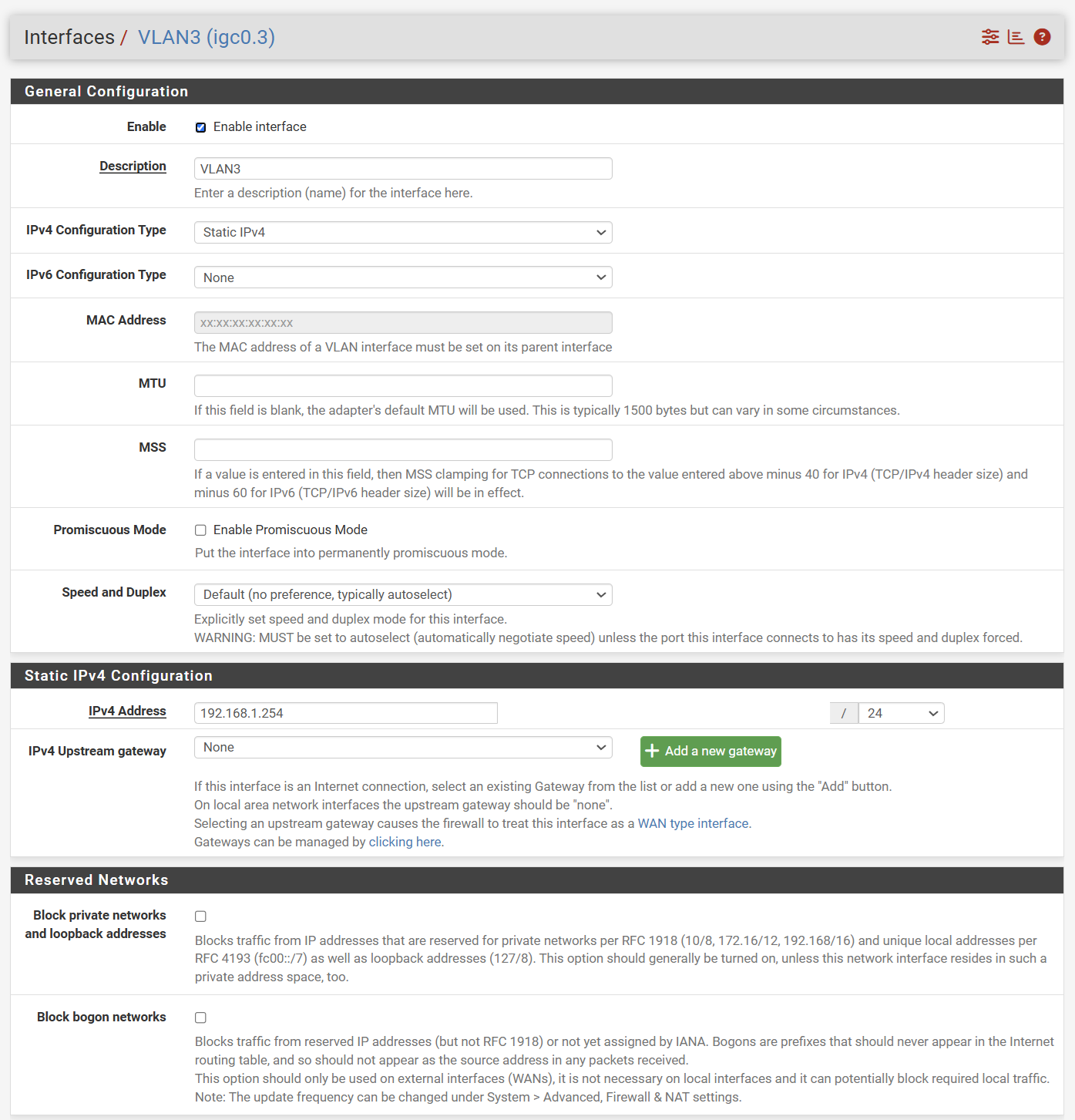
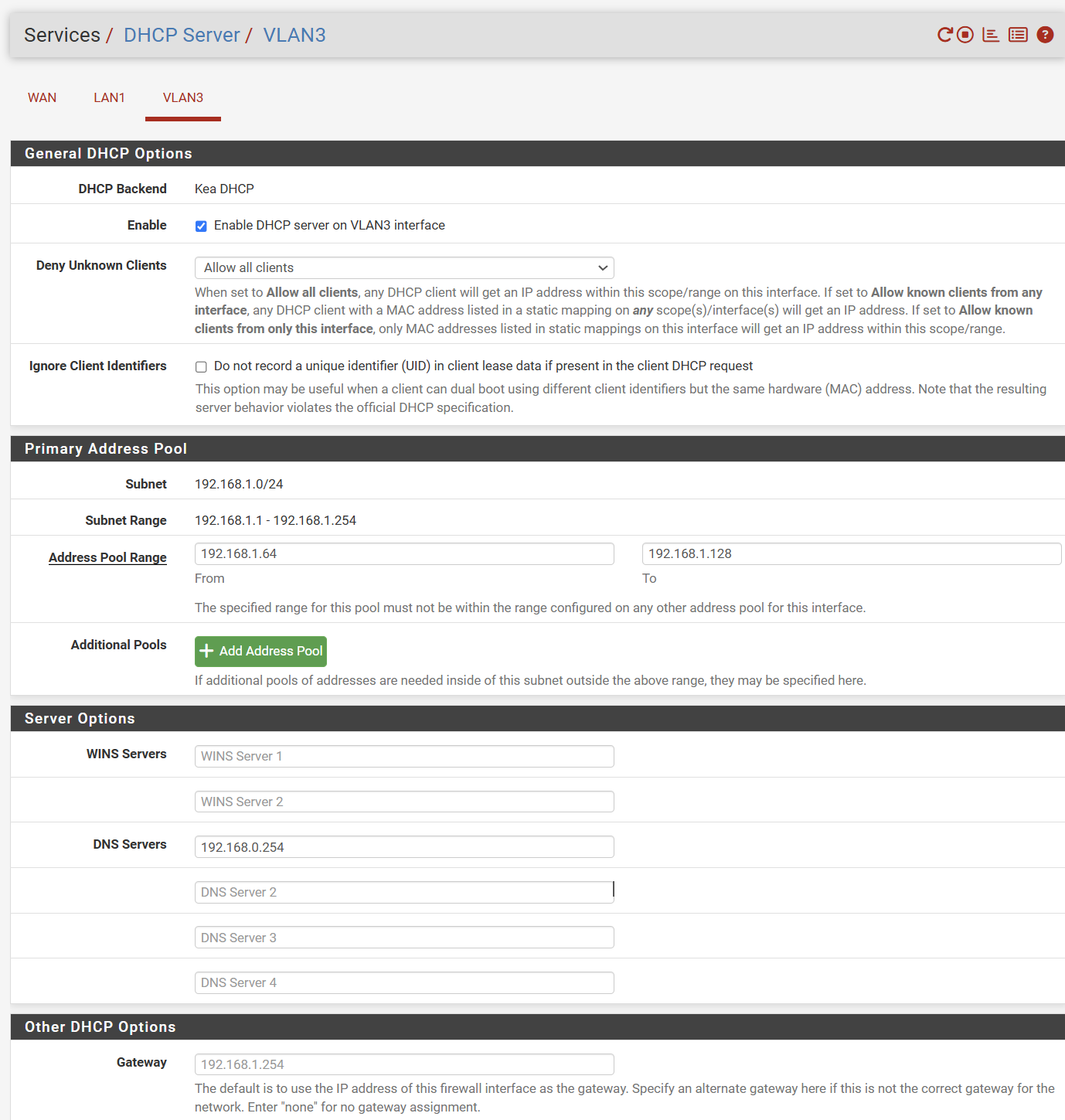
My problem is that When I connect to the DIR-880L wireless I am never assigned an IP address. I suspect I have something misconfigured in my VLAN configuration. I would appreciate some guidance.
-
@codechurn
The screenshot of the DIR-880L shows the VLAN 3 enabled on port 1, but the network diagram shows port 2 is connected to the switch.
However, this might be a typo.You have a config failure on the T1500, however. You have set the ports 8 and 10 as untagged. These must be tagged.
-
@viragomann
The original network diagram was wrong. The cable from the SG1005P is plugged into Port #1 on the DIR-880L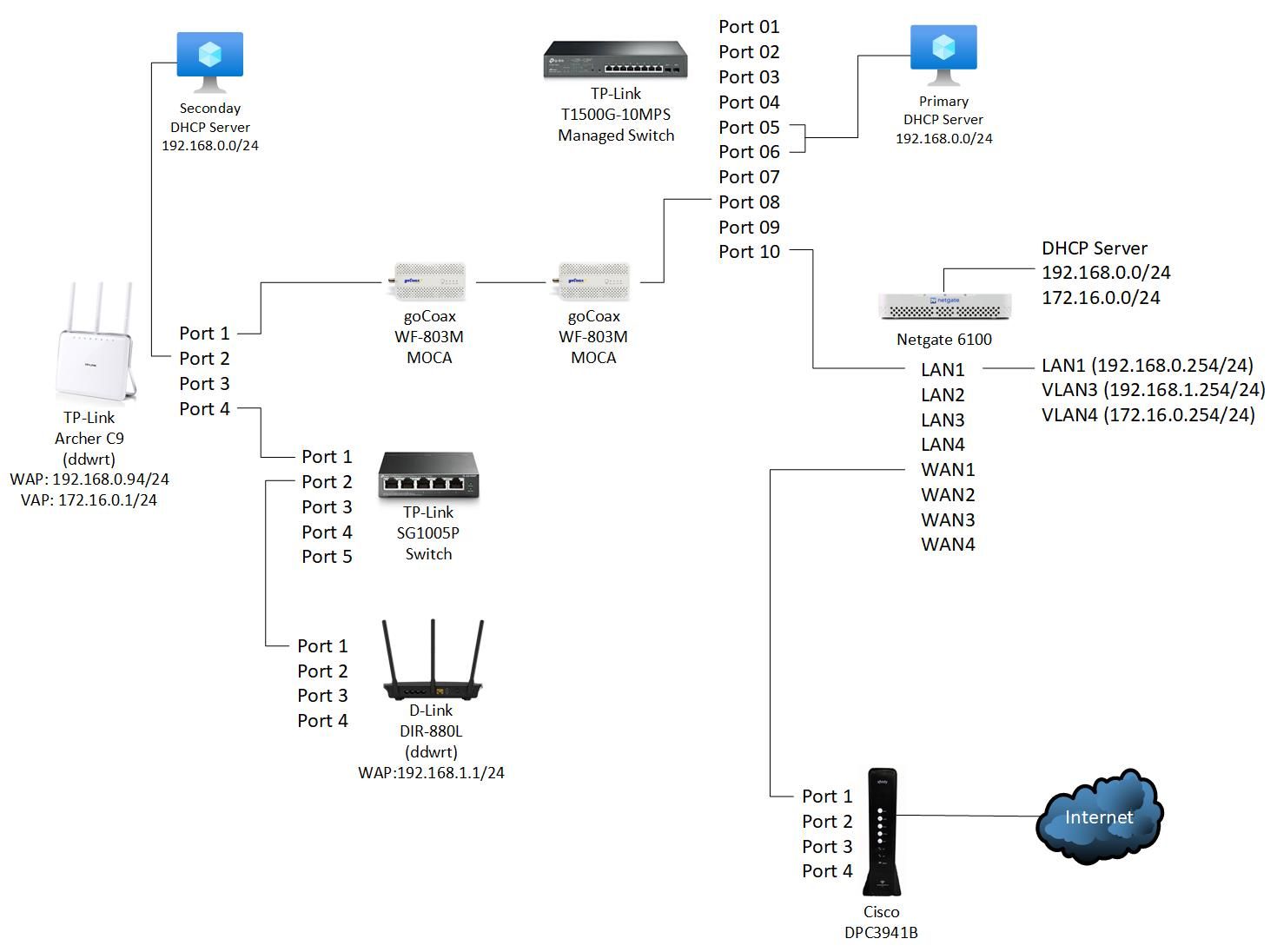
Additionally. on the T1500G-10MPS switch I configured I configured:
VLAN3 to be tagged on port 8 and 10
VLAN1 to be tagged on port 8, untagged on port 10.
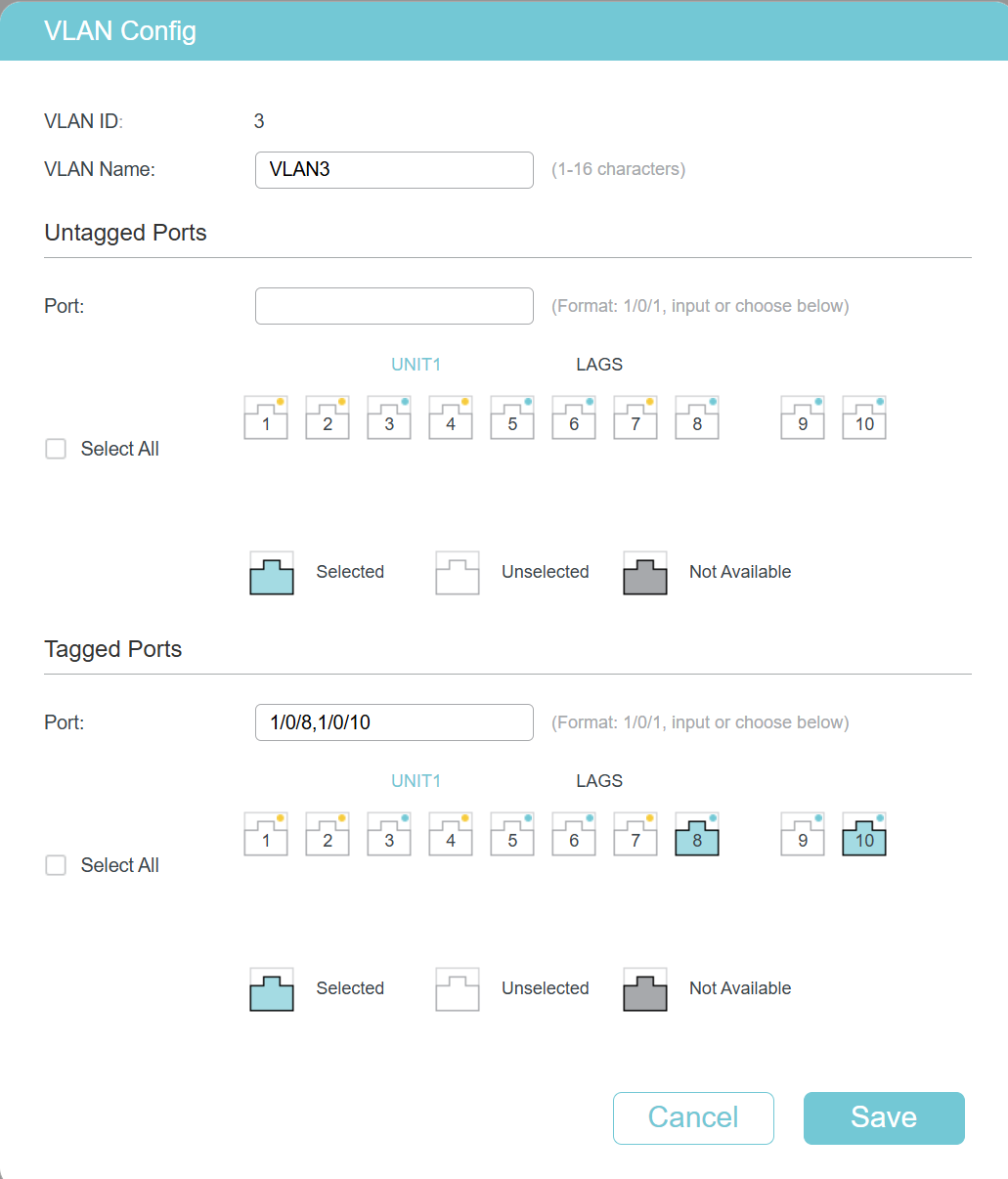
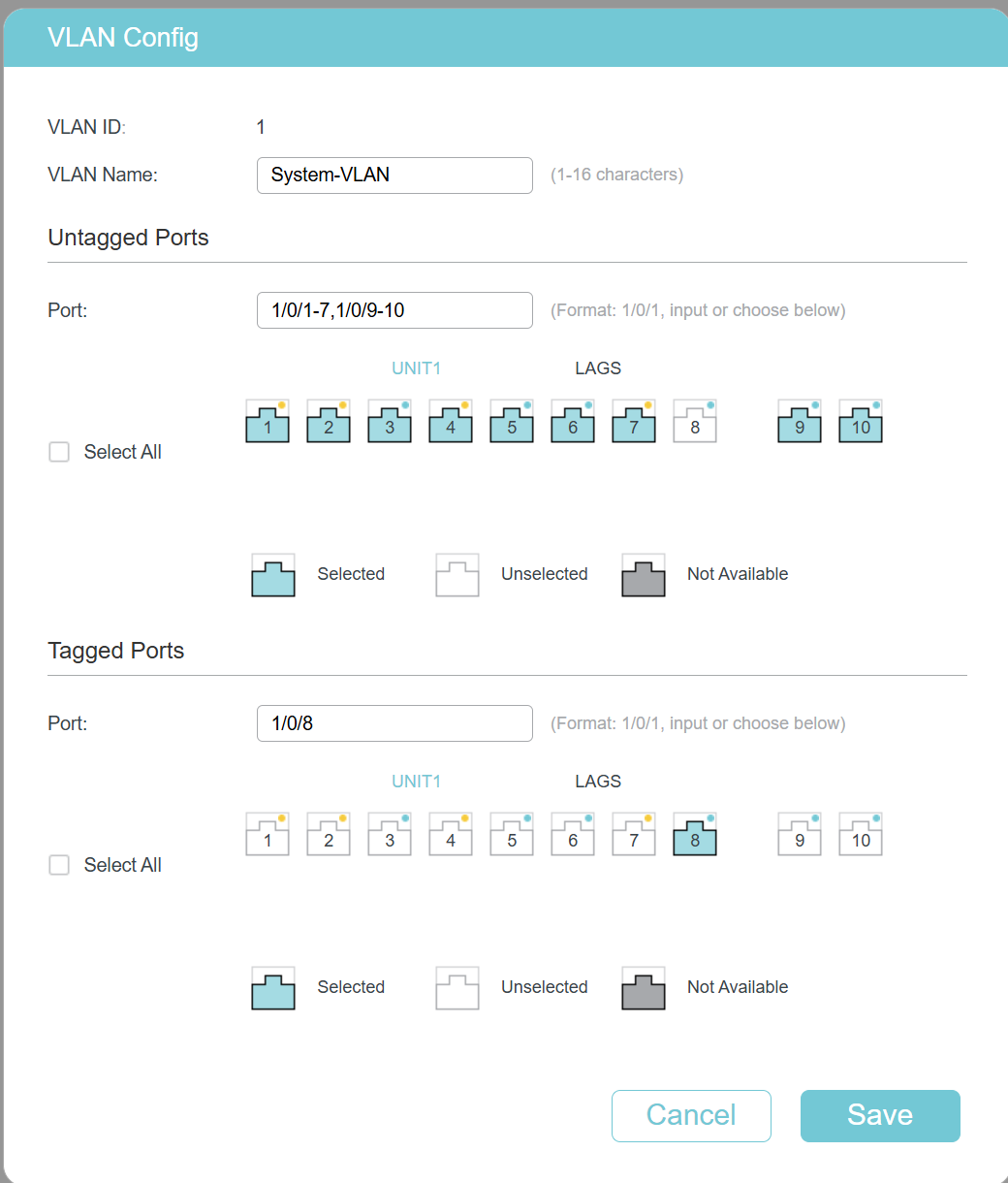
The Archer C9 is configured to tag Port 1
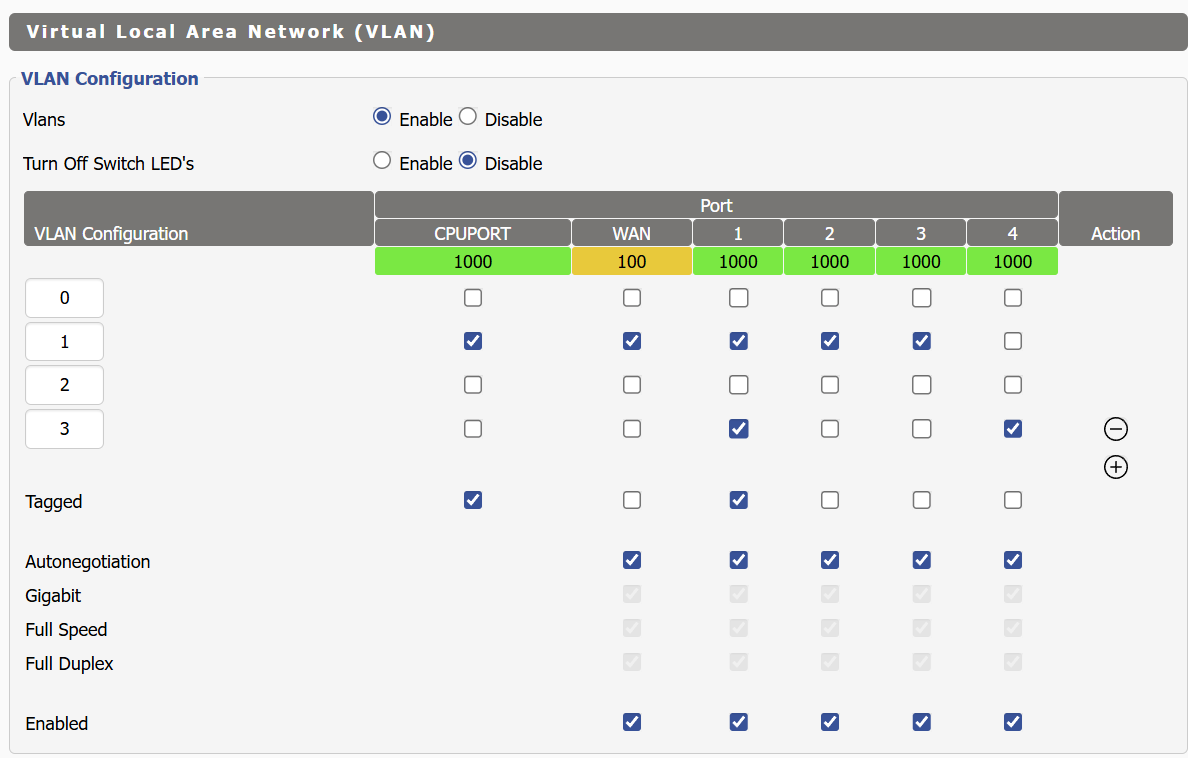
I have network connectivity on VLAN 1 via the Archer C9 to the Netgate 6100. I think I am missing something for VLAN3.
-
Port #1 on the 880L was configured to be tagged, whereas on the Archer C9 Port #1 was untagged. Once I changed Port #1 to be untagged on the DIR-880L I got a DHCP address served up to me by the Netgate 6100!
Next question: How do I route all non-local 192.168.1.0/24 traffic out through the ExpressVPN Interface on the Netgate?
-
@codechurn
Policy Routing ConfigurationNote that policy routing forces all matching traffic to the stated gateway.
To get access from the concerned sources to local hosts, e.g. DNS on pfSense, you have to add additions rules and put them above of the policy routing rule. -
@viragomann
I actually have been struggling setting up a Policy Based Rule to route the internet traffic from VLAN3 out the EXPRESSVPN interface.Here is what I have configured for rules:
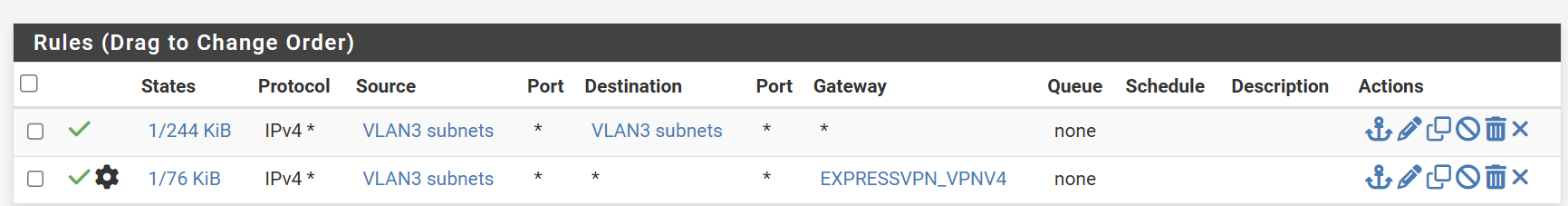
However, the internet is not accessible via EXPRESSVPN on this VLAN. I have a similar policy routing routing rule on LAN1and it works fine. What am I missing?
Looking at the state of the second rule, it seems like all connections are being blocked.
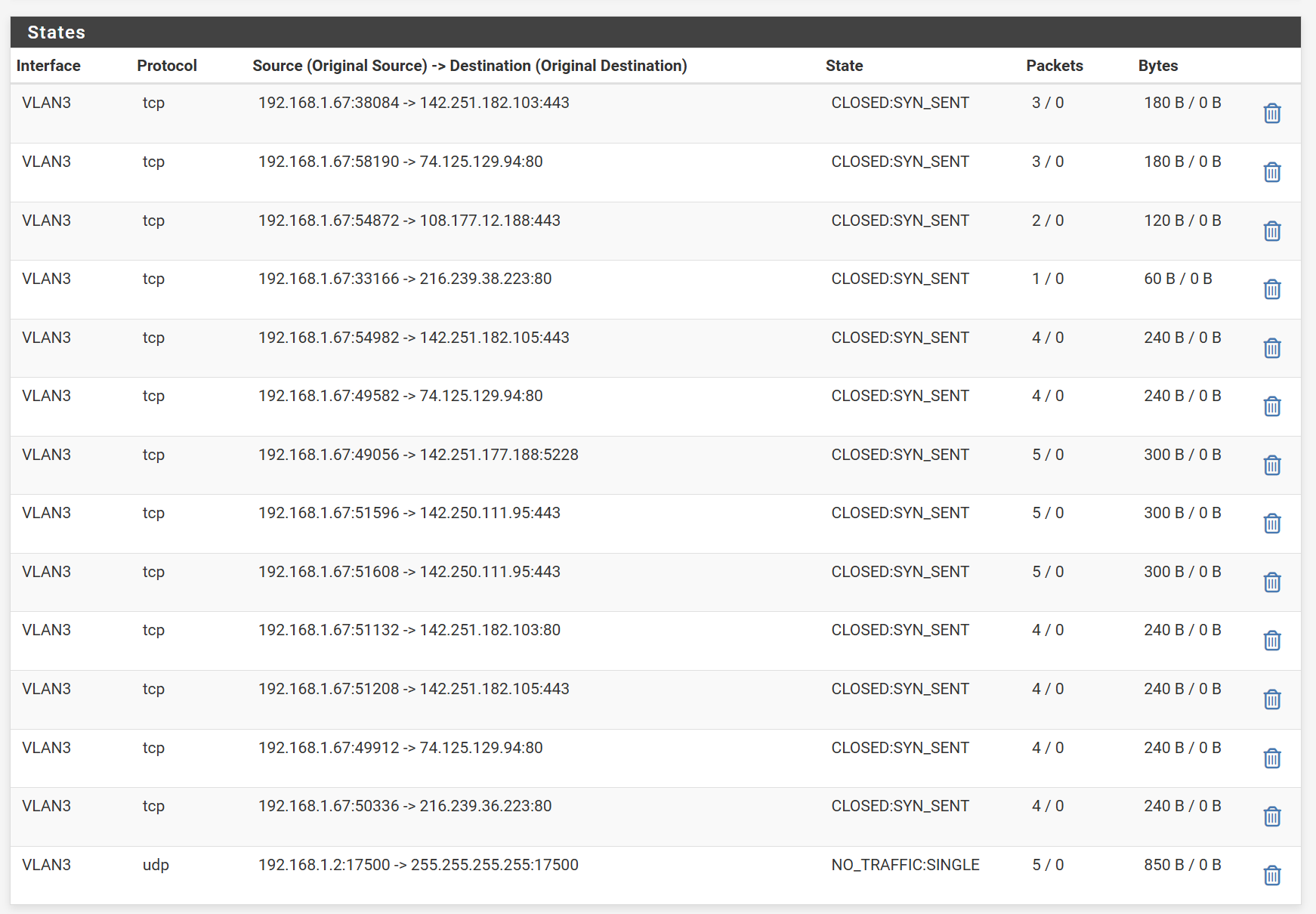
-
I think I figured this out, but perhaps youc an confirm. I believe I was missing the 192.158.1.0/24 source in the outbound NAT mappings for the ExpressVPN interface
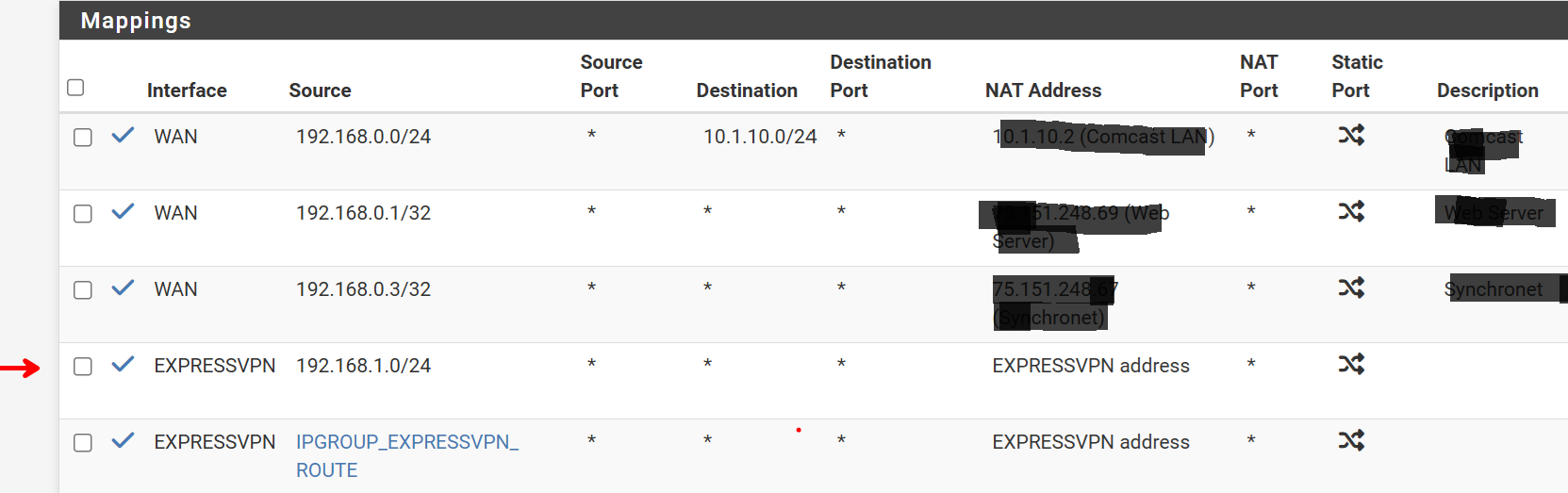
I've since added the range to the IP Group. Amaizing how quickly you forget things when you aren ot in there every day.
Also, If I want to prevent VLAN3 from being able to reach LAN1 do I need to add an explicit block rule? Seems like prior to me adding this rule I was able to access resources on LAN1, such as the pfSense web interface and some sites frontended by HAProxy on Pfsense.
-
@codechurn
Yes, you need an outbound NAT rule for the respective subnet on the VPN interface.To limit access to outside destinations only, best practice is to create an RFC 1918 alias, which includes all private IP ranges and use this one in the filter rule.
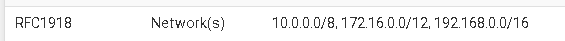
You can use this as destination with "invert match" checked in the policy routing (pass) rule. Or just insert a block rule above of it.
Used in a pass rule, it looks like this:
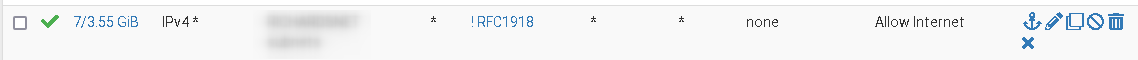
Also you should limit access in your first rule to services, which are needed like DNS.
If you also want to block access to HAproxy, which is listening on the WAN IP, you need an additional block rule for this.