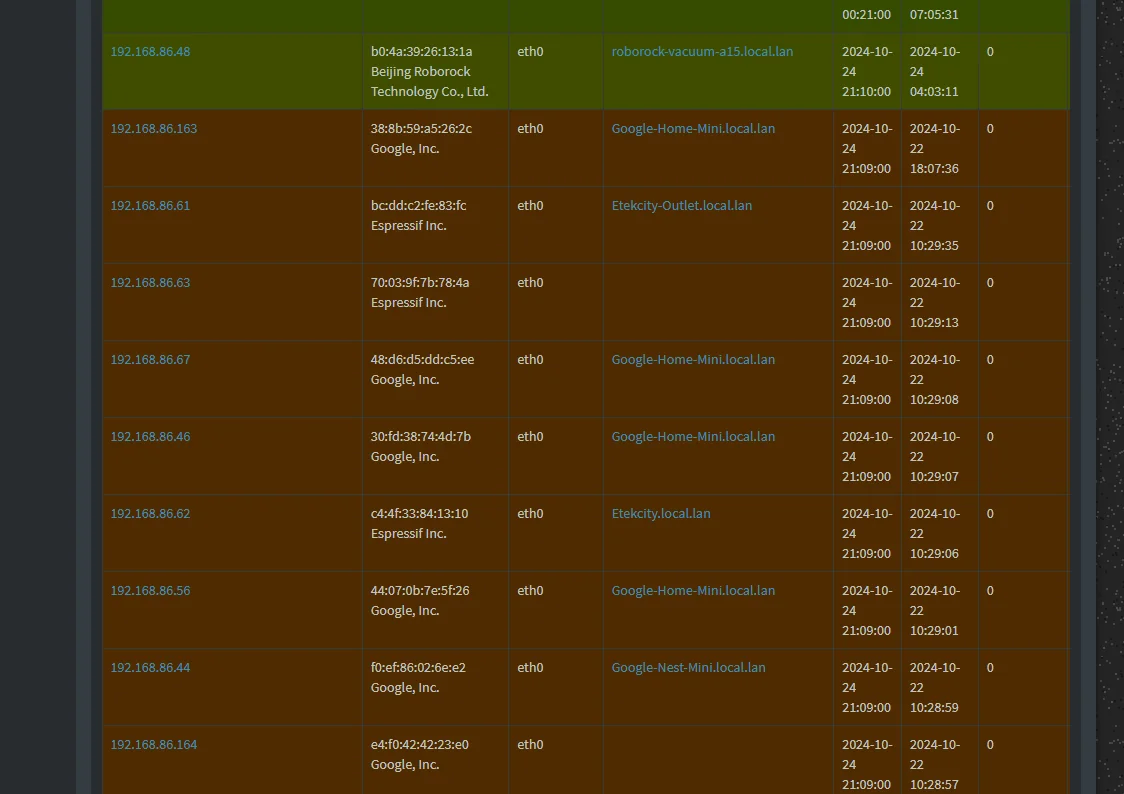
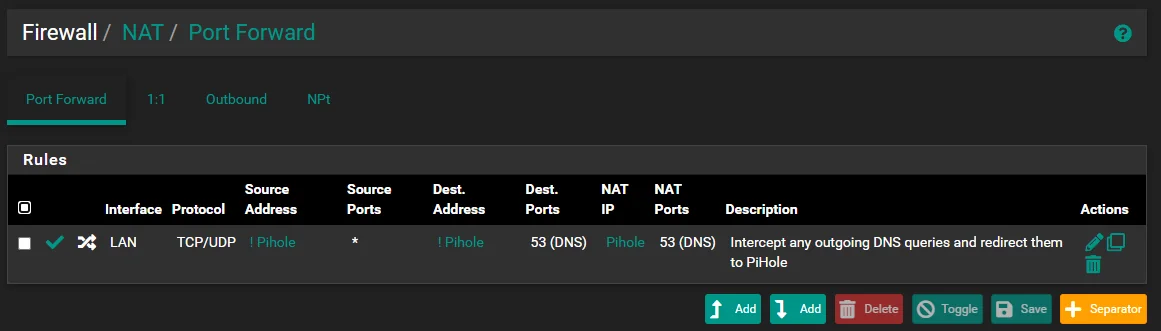
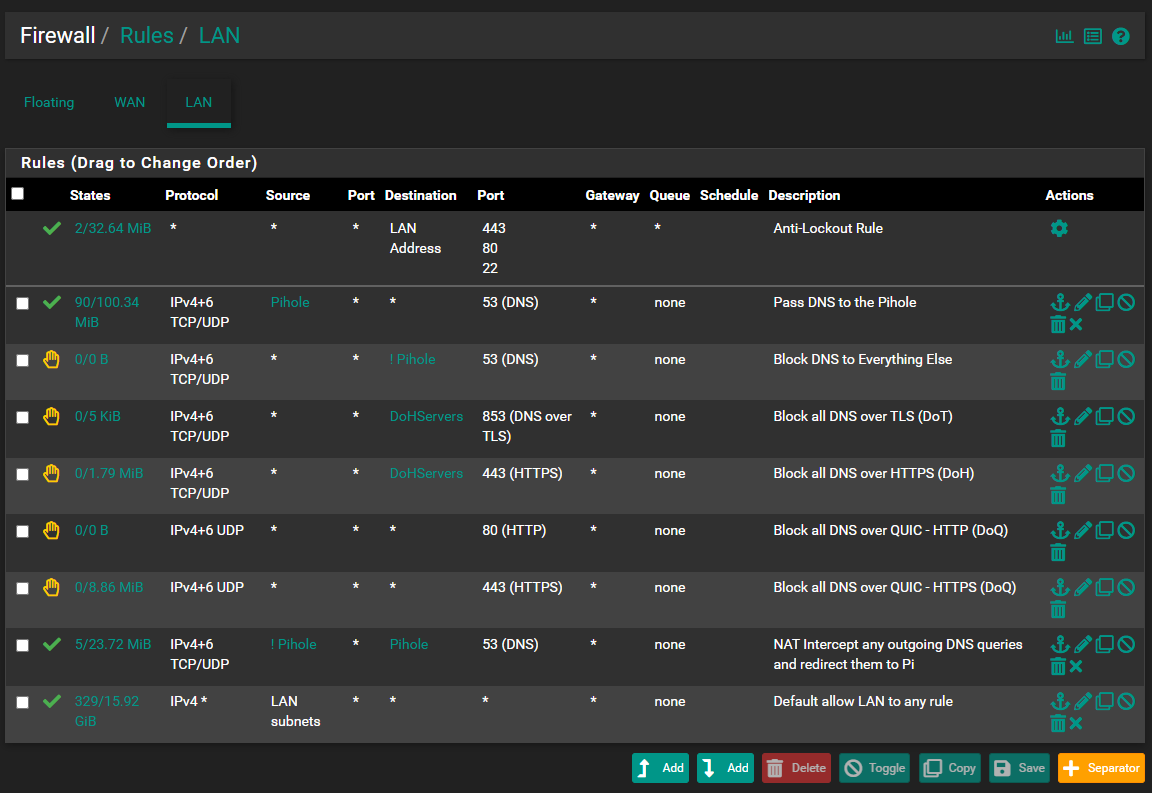
Redirected all DNS to pihole using pfSense. Pihole still showing some hosts as not using the DNS ?
-
Likely not relevant, but I use Pihole as the LAN DNS and forward to pfSense where it also hits pfBlocker and Unbound (Resolver).
-
@provels that is the better way to do it if you ask me.. That is what I do as well.. Clients ask pihole, pihole asks unbound on pfsense, unbound resolves.
-
@johnpoz Not to trash pfB, but I love the simplicity, efficiency, and ease of management of Pihole, especially when I see numbers like this from a minuscule VM.

-
@provels yeah not meaning to trash pfb either, I use it for my aliases and its great, but been using pihole long time, and yeah the eye candy is nice, etc. etc..
-
I agree with you guys, pi-hole pointing to pfsense unbound is my preferred setup too and what I suggested.
I'm so glad my friend got me to try out a pi-hole setup. Once you do, there is really no going back to pfblocker. They both are great tools, but the limitation of having to enter individual IP address for bypassing is a pretty big deal breaker on pfblocker. I used to be able to define a range or subnets which can bypass it via the custom resolver options, but that doesn't seems to work anymore. I'm sure I'm missing something but the fact that I had a hard time trying to find what I'm missing is enough to say pi-hole is the clear winner in that respect. I also love that I can turn it off for x amount of time for testing purposes. The visuals are for sure nice too.
-
@Raffi_ said in Redirected all DNS to pihole using pfSense. Pihole still showing some hosts as not using the DNS ?:
They both are great tools, but the limitation of having to enter individual IP address for bypassing is a pretty big deal breaker on pfblocker. I used to be able to define a range or subnets which can bypass it[ . . . ]
If LAN hosts are bypassing local network policy entirely, one might not be thinking about and/or doing it right. I can't think of a single use case where granular domain/address (including subnet) control isn't preferable to simply bypassing DNSBL/IP filtering altogether—which is definitely well-within pfB's capabilites. That one hasn't personally figured out how to configure one or the other the way they desire says nothing about the objective limitations of either software, except maybe user-friendliness.
Pi-hole is the clear winner in whatever aspect/s you've determined to be the case for you personally.
-
What about DoT or DoH ?
-
@JonathanLee If you're responding to me, both can be mitigated to the extent possible wih port filtering (DoT), NAT (DoH and DoT), and block lists (DoH and DoT).
And that has nothing to do with Pi-hole versus pfB. No DNS forwarder or resolver on its own can do anything about either.
-
@cyberconsultants I have a huge list I use to block them
-
@JonathanLee I've seen you post it. Huge indeed! I meant to use it as one of my DoH feeds last time I saw it on here in fact.
-
@cyberconsultants it’s like wackomole
-
@tinfoilmatt I get your point. Whether you think my approach or the approach of doing it the way pfblocker has it is kind of semantics. People are given tools, how those tools are used is up to them. I personally like the tool that gives me more flexibility and control over what can or can't be done on my networks as I see necessary. If pfblocker is capable, I would like to know the secret.
PS. I still love and use pfblocker, so I'm not bashing on it here. I use pfblocker in the office. If I had a choice, I probably would run pi-hole there too, but it's easier to just enable pfblocker within pfsense and not have a separate server just for that.