Simple GEO-IP test?
-
@focaccio lets see your rules..
Rules are evaluated top down, first rule to trigger wins, no other rules are evaluated.
-
@johnpoz this is also another test that should fail:
C:\Users\Greg>ping route-server.gvt.net.br Pinging route-server.gvt.net.br [200.146.0.1] with 32 bytes of data: Reply from 200.146.0.1: bytes=32 time=202ms TTL=43 Reply from 200.146.0.1: bytes=32 time=199ms TTL=43 Reply from 200.146.0.1: bytes=32 time=199ms TTL=43 Ping statistics for 200.146.0.1: Packets: Sent = 3, Received = 3, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 199ms, Maximum = 202ms, Average = 200ms Control-C ^C C:\Users\Greg> -
@focaccio I can not help you figure out what is going on without seeing your rules. Also did you do the test, and then put in the block rule - if so a state would already exist and allow the traffic.
-
@johnpoz understood thanks, will work on getting that uploaded. have to step away for a bit.
-
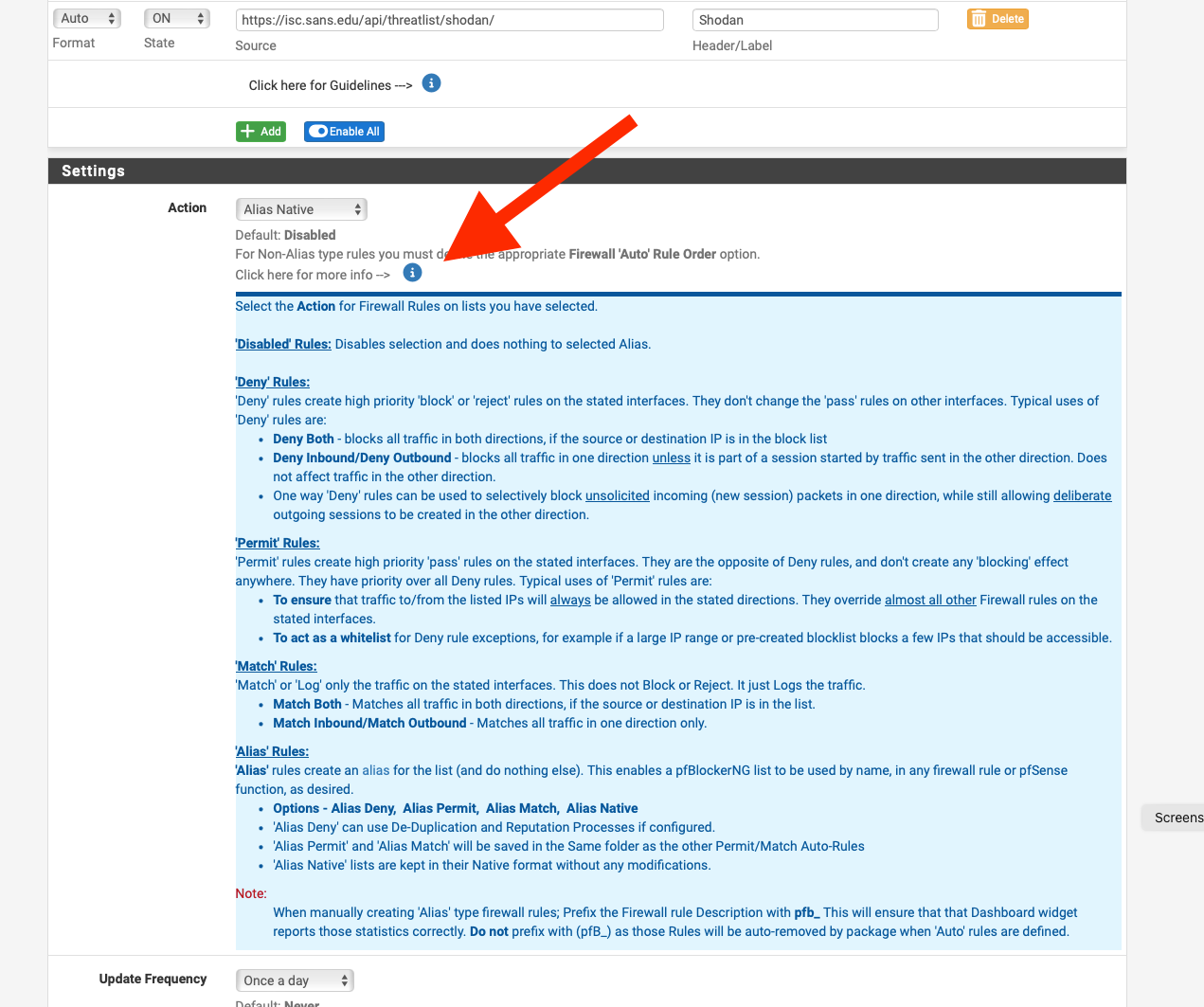
@focaccio so here I just created an alias that contains brazil, added it to a rule that blocks. Checked that the table had networks in it..
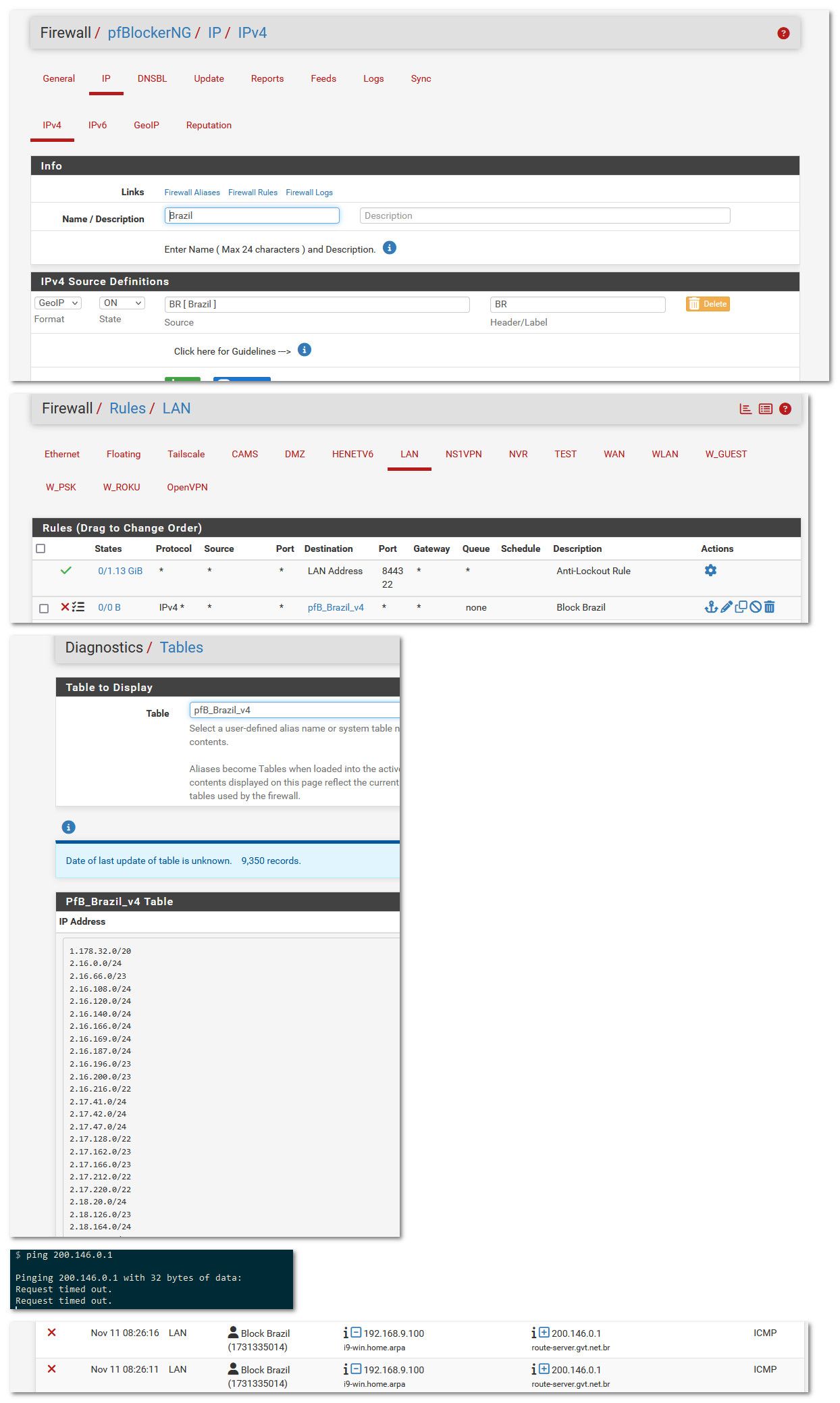
If your trying to use the South America geoip, did you actually go in and select what countries you want included? And then validate the table populated. You might have to run the update in pfblocker, etc
-
@johnpoz thanks for those tips, i think the key piece was seeing i needed to use ALIAS NATIVE instead of what I had as DENY BOTH in the GeoIP part of blocker.
It is working now:
C:\Users\Greg> C:\Users\Greg>ping route-server.gvt.net.br Pinging route-server.gvt.net.br [200.146.0.1] with 32 bytes of data: Request timed out. Request timed out. Request timed out. Request timed out. Ping statistics for 200.146.0.1: Packets: Sent = 4, Received = 0, Lost = 4 (100% loss), C:\Users\Greg> -
Look also at what regex can do you.
See here for more.I'm pretty sure you could filter for "dot cn" (thus the TLD).
Be careful : this is a sledge hammer solution.
Or like the missile that explodes even before you launch it.
Be aware that most if not all "dot cn" sites also have their "dot com" equivalent, so block "dot com" also while you are at it
Personally, the method that worked best for me : as soon as I discover that I have devices (== users) on my networks that visit scary web sites, I lock them up in a full controlled network (captive portal or worse). From then on, I let them have it all : the crypto scammer soft, the spams, the viruses, the big total. This was known before as "let them learn" as thats works best. You'll do them a favor, believe me.
Even if it takes time, people will notices that when they go to a site that includes stuff from other sites, (and so on) they will loose at the end. They will learn (as their device becomes unusable at the end / or they loose everything 'all the time').Btw : joke aside, this morning I was wondering : let's put a 'tarif' on it ? ^^ (sorry ...)
-
@focaccio said in Simple GEO-IP test?:
I had as DENY BOTH in the GeoIP part of blocker.
I don't let pfblocker create any rules - that is another way to do it I guess. But I am not a fan of auto rules of any sort.. Oh a auto rule that allows dhcp when you enable dhcp is bit different then something that adds its own rule and what is in the rule, etc.
But maybe that is just me, but I know this way works - and don't have to worry about where some auto rule might be placed in the rule set order, etc. Or if that could get mixed up sometime, etc.
-
@johnpoz quick follow-up here: why do i see only one object when trying to build a rule, but there is more than one object created?
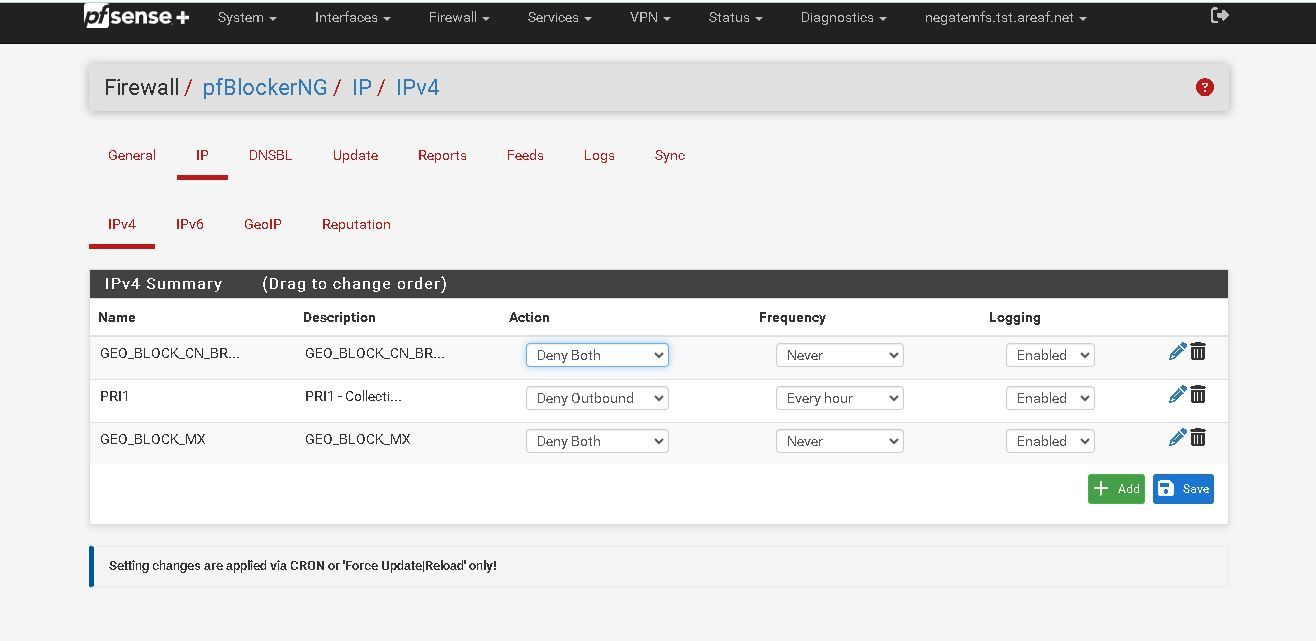
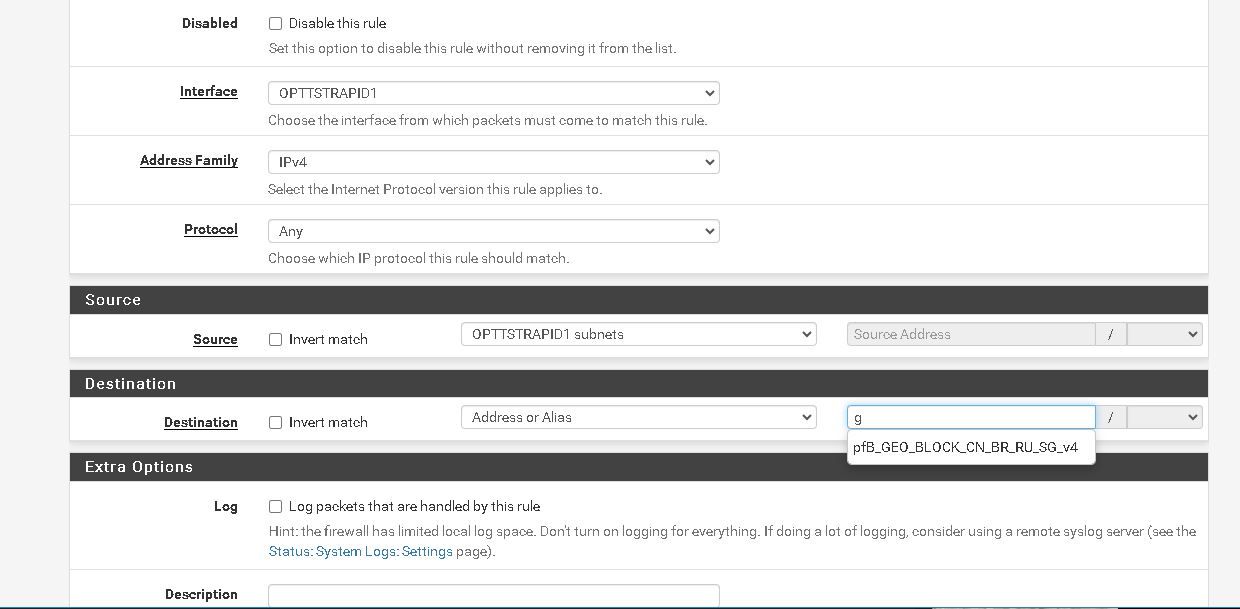 I rebooted after creating the second object just to make sure it "took".
I rebooted after creating the second object just to make sure it "took". -
@focaccio you can't assign those to your own rules - you need to use native alias if you want to be able to put them in your own rules.
-
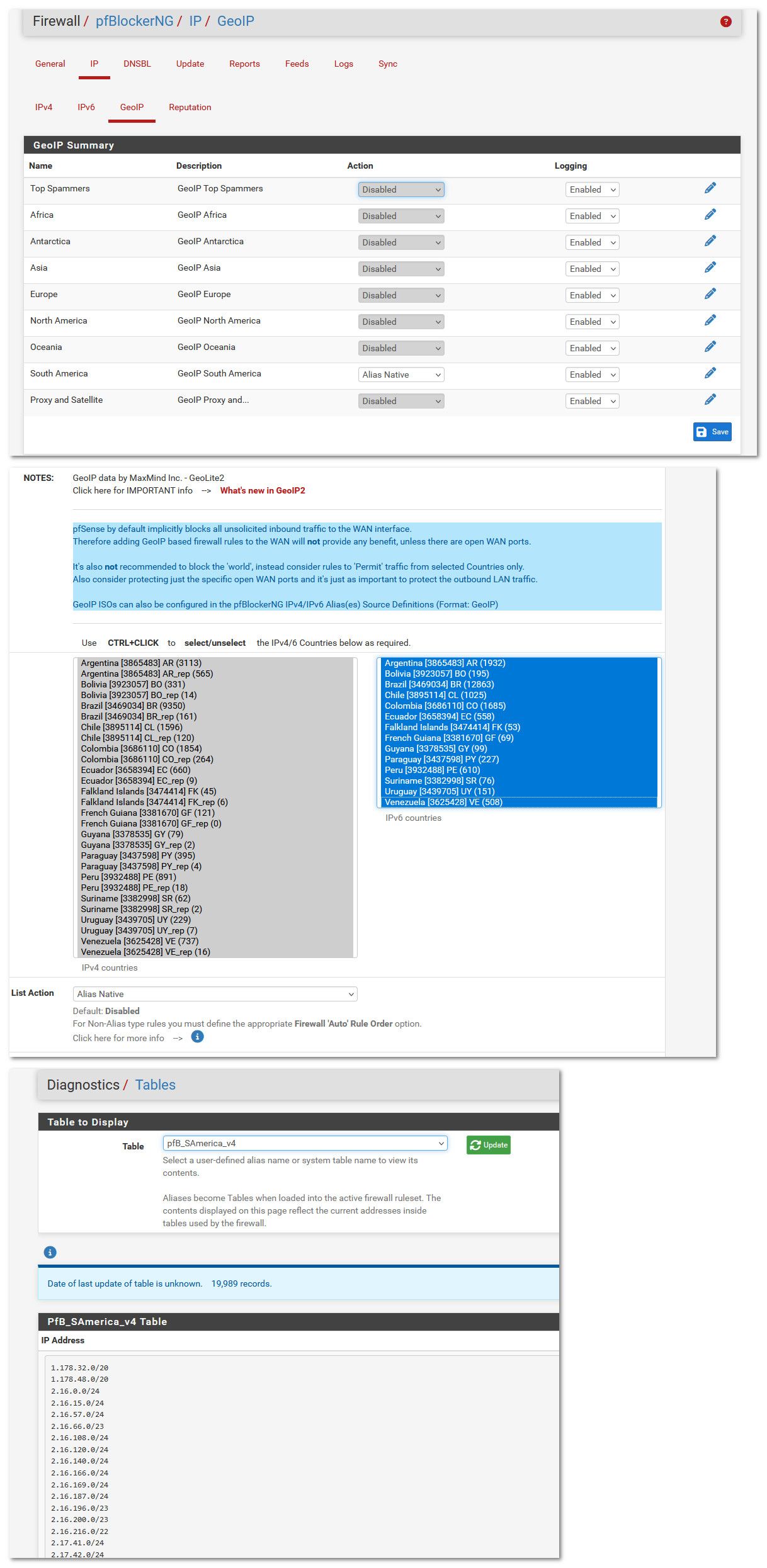
@johnpoz hi John, thanks again, still in (probably a long) orientation phase here, is there a simple way to describe (or documentation section) what the "Action" drop down options like native alias, match both, etc mean in the IP>GeoIP area of pfBlockerNG?
-
@focaccio only doc that I am aware of is
https://docs.netgate.com/pfsense/en/latest/packages/pfblocker.html#pfblocker-ng-package
-
You can also click on the (i) for more info.