Dynv6.com, how?
-
This post is deleted! -
Try port 80...
-
@Bob-Dig
In the Acme package UI I haven't seen anything even remotely related to a port ...
-
@flo-0 https://letsencrypt.org/docs/challenge-types/
-
@Bob-Dig
Ah, you are assuming I use the web root method.
Well, I don't. I want to use the Dynv6 API.
-
-
@Bob-Dig
The server for which I want the certificate to be created is not the same as my pfSense?
Because I don't want to open a machine to the internet which is not sufficiently secure for this?
Because I want to learn how to do it the right way?
-
You saw : ACME using dynv6 ?
edit : https://dynv6.com/docs/apis#dns-update : looks like they accpets / use the nsupdate method that acme.sh uses.
Afaik : In the past I was using nsupdate manually, and I gues it still works the same today.
Look at /usr/local/pkg/acme/dnsapi/dns_nsupdate.sh :Here (the delete part) - there is also an "add" part.:
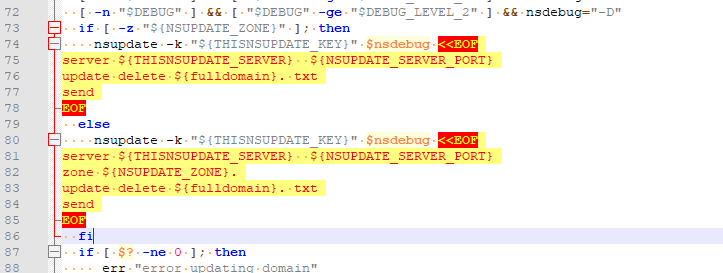
The "${THISNSUPDATE_SERVER} is the key file (have a look at it) with your TSIG secret code.
It's in the /tmp/acme/[your acme accont]
$nsdebug stand for -d or -D = debug option - why not ^^${THISNSUPDATE_SERVER} stands for the IP where the update command has to send send to.
I saw :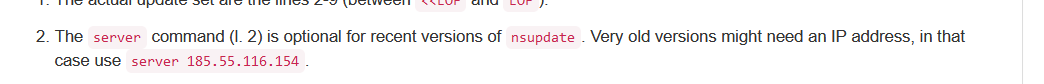
I just tried it myself - I created a file named 'commands' :
server 1.2.3.4 zone bhf.tld. update add bhf.tld. 60 IN TXT "Hello" sendwhere 1.2.3.4 is my own domain name server (bind9 on a Debian).
bhf.tld. is my domain name."Key" is the short file name I've created from this :
key "acme-pfsense-update." { algorithm HMAC-SHA512; secret "eYQiVAutEEAFOjsdfsgdfgsdf52454sdfSzFzNvyVoCxOQ/jwBeA10EPeE7vwEdFT11QYs1YhO9zDCaJwzkuZp0w==";Btw : this secret, the "algo" and the "key" must be known on the other side. In my case, my bind9 domain server, in your case @dynv6.com.
Let's do it :supdate -k key -d commandsBecause I have also the dns server (bind9) logs, I saw :
==> /var/log/bind9/debug.log <== 13-Nov-2024 18:42:38.824 update-security: client @0x7f3fea231fb0 82.127.77.108#49895/key update: signer "update" approved 13-Nov-2024 18:42:38.824 update: client @0x7f3fea231fb0 82.127.77.108#49895/key update: updating zone 'bhf.tld/IN': adding an RR at 'bhf.tld' TXT "Hello"Looks promising.
Let's check :dig bhf.tld TXT +short "Hello"Champagne !
-
@Gertjan said in Dynv6.com, how?:
Thank you!
I used the way described in the thread you referred to first. This works. So I was not required to work through the rest of your post.
I'm quite surprised how difficult all of this certificate stuff is still today. This requires scp-ing the correct shell script from github into the right directory in pfSense, adding a snippet of shell code into another big shell script on pfSense. I'm honestly questioning why I should use a package in pfSense for something like this. Recently I was required to install a certbot docker image to pull certificates on a linux box. Another example of how to solve a simple problem in the most impressive and complicated way.
Part of the problem is the incredible creativity of dns providers in creating an impressively high number of different ways to do the exact same thing. I mean it's not even that these providers actually provide the certificates. This is only about adding and deleting a simple text entry to a simple f***ing name server to prove I'm in control of that thing. Holy Cow, Acme has 159 different scripts to cover all of these! And I'm the lucky loser who needs to use the one which is apparently broken.
-
@flo-0 said in Dynv6.com, how?:
This requires scp-ing
You have SSH, right ?
I presume you already have Putty.
My advise, install WINSCP. Now you can 'explore' the pfSense file system like Explorer does on your Windows PC.
Install Notepad++, make it the default text editor (fire Notepad ^^) and now you can look at, edit, create file. -
@Gertjan
I wasn't complaining about the specific tools. I get along. The concern is rather: Do I remember what I changed in the system if it comes to the next upgrade and does it survive such an upgrade? Probably not. And are all people who I think should be enabled to have certificates created (think of the spirit of letsencrypt) capable of doing this in good confidence in the process and the results? I think not. As I said: I see not a pfSense fail, rather the DNS providers'.Regarding tools: I used Putty, WinSCP, Notepad++ in my time as a software engineer before retirement. Today I don't touch Windows with iron prongs (unless I need to rip a DVD which the producers failed to make according to the standard).
scp is actually a totally simple tool. It's really just an (encrypted and authenticated) cp to another machine. If you installed keys before it will not even bother you with a request for authentication.
And I was practically born with vi. Notepad++ might be quite ok. But vi is available everywhere. As a vi grognard I never think twice which editor to use. (I do admit I will not push vim off the edge of my bed for vi ...
 )
) -
@flo-0 said in Dynv6.com, how?:
I wasn't complaining about the specific tools. I get along. The concern is rather: Do I remember what I changed in the system if it comes to the next upgrade and does it survive such an upgrade? Probably not. And are all people who I think should be enabled to have certificates created (think of the spirit of letsencrypt) capable of doing this in good confidence in the process and the results? I think not. As I said: I see not a pfSense fail, rather the DNS providers'
Your setting will get saved and used for the eternity.
But true, every 'gadget' you activate has to be maintained. In this case : you have to make sure you can use your domain name, check settings on the host site, and if you change them, sync with the pfSense (acme) settings.
Like an emal : when you change the password on the email supplier side, you have to use the new password on your side, or inform all (!) your email clients.What Letsencrypt does, why it only works well when you automate it, what certificates are etc etc etc, you need (imho) to understand the why and what. Don't worry, Youtube exists, and you can understand everything pretty fast, you have to go through it.
@flo-0 said in Dynv6.com, how?:
I used Putty, WinSCP, Notepad++ in my time
When you use pfSEnse, or whatever other device with SSH, a GUI etc, you probably use these tools up until the day you retire from live ;)
vi ?
pkg install nano!