Lan and Vlan using the same subnet on the same physical interface
-
Hello everyone,
I'm in the process of consolidating multiple non-managed switches into one managed switch for simplicity and so the traffic moving from various interfaces and VLAN subnets to other subnets isn't having to go through the firewall on multiple physical interfaces but rather just through the switch and then have the pFsense firewall just managing internet traffic.
In order to facilitate the switch, is it possible to have one of the Physical Interfaces (LAN) that is currently in the subnet of 192.168.2.0/24 share its subnet also on a VLAN 10 that would be on that same physical interface that the VLAN is on?
Physical interface IGB0 currently: 192.168.2.0/24.
and VLAN 10 on IGBO0 would be also on the subnet: 192.168.2.0/24Thanks,
Steve
-
@LunchBoxSteve how many devices on specific vlans that your creating? Are you going to run acls on the L3 switch..
I ask because if your not going to filter traffic between vlans. Isolating them to their own vlans really only prevents broadcast and multicast between the vlans. If you don't have a lot of hosts, you prob better off just putting them all on the same network for simplicity.
Since just routing them on your managed switch doesn't provide the firewall between your vlans that pfsense would allow for. And even if you do plan on creating ACLs between your vlans on your switch - they are a pita compared to how easy to do on pfsense.
Your going to run into some sort of asymmetrical issues if you try and use 192.168.2 as your transit network between pfsense and your switch, and also as another segment on switch.
What exactly is the problem your trying to solve currently? Is pfsense not up to the routing of your traffic flow between your current physical segments? While yes its better to consolidate to 1 larger port density switch and use vlans vs physically isolated dumb switches. If your going to do the routing at the L3 switch, you prob going to loose the flexibility and ease of firewall between your segments.
-
@johnpoz While I appreciate the thoughtfully complicated reply, I was just looking for a simple answer, if sharing a subnet between a physical interface and vlan on the same interface is possible.
It's a temporary situation as to why I would need to do it this way.
Thanks
-
And I answered that
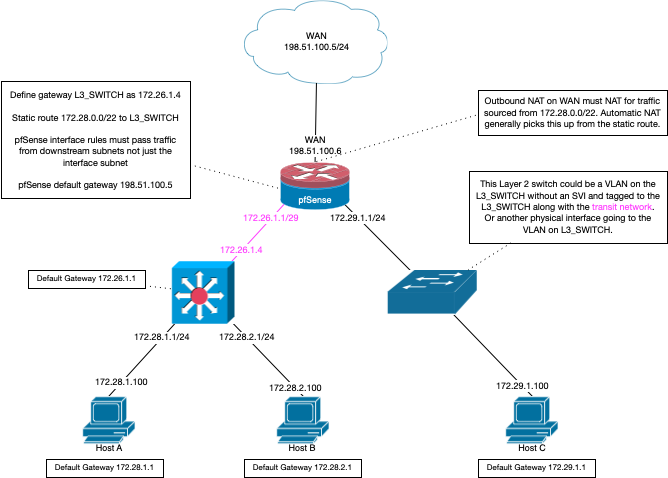
Your going to run into some sort of asymmetrical issues if you try and use 192.168.2 as your transit network between pfsense and your switch, and also as another segment on switch.
Your going to have issues.. you wouldn't be able to talk to the other 192.168.2 addresses, and your routing even if your IP on pfsense was different than the 192.168.2 svi on the switch..
Even if you sent traffic to switch from a client to switch IP on the 2 address, and the switch somehow knew that should send it to the 192.168.2.x IP.. When pfsense sent to reply to the clients 192.168.2.y address he would think that is just local to his lan network.
Change either your transit network (pfsense lan) to your routing switch on pfsense or change the 192.168.2 devices to some other IP range so you don't overlap like that.
If your going to do downstream routing, ie your L3 switch.. Then there should be a transit network between pfsense and the switch, and this network should not have any hosts on it.
-
@LunchBoxSteve said in Lan and Vlan using the same subnet on the same physical interface:
I was just looking for a simple answer, if sharing a subnet between a physical interface and vlan on the same interface is possible.
No it's not. A subnet can be on only one interface and a VLAN is a separate interface from the physical one. Also, traffic between the LAN & VLAN has to be routed, either with pfSense or a layer 3 switch. How can they route between devices supposedly on the same subnet?
-
First, the short answer to your question is no, it won't work.
Second, there is a difference between using a "managed switch" and a switch set up to function as a layer 3 device. Setting up a managed switch acting as a layer 2 device will still require that all inter-VLAN traffic (traffic crossing between different VLANs) go through the router. So your idea that simply using managed switches will allow the router to handle only internet traffic isn't how it typically works.
That being said, I'm not suggesting that you set up your switch to act as a layer 3 device. Data traversing between devices on the same VLAN is already handled by the switch level even when the switch is set up as a layer 2 device. This means that PFSense is only routing data that travels between VLAns/network segments. In a typical home network, if you have a need to move a lot of data between two different VLANs, I would question why you simply don't put those devices on the same VLAN. Long story short, there is typically little difference in speed between using a layer 2 switch and a layer 3 switch with ACLs on a typical home network. Not only that, but setting up a layer 3 switch can certainly take a lot more effort and trial and error if it's not something you are familiar with.
Still, it is important that you understand the differences between a managed switch and a switch set up as a layer 3 device with ACLs, DHCP, etc.
-
@sic0048 well articulated and great points..