Quesiton about the alert system on Suricata
-
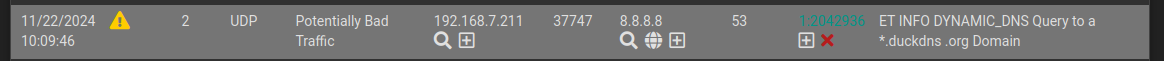
Hi Currently i have a quick question using suricata and i see many alerts which i assume there are false postives but my question is this, in the picture we see server 192.168.7.211 trying to accessing the duckdns.org domain but using DNS 8.8.8.8 wouldn't that mean that suricata would block 8.8.8.8?
and only using these rules
 and all the emerging rules
and all the emerging rules
Thanks -
@killmasta93 said in Quesiton about the alert system on Suricata:
wouldn't that mean that suricata would block 8.8.8.8?
No. This rule, 1:2042936, merely alerts (or blocks if configured to do so) on individual packets containing a DNS query for any .duckdns.org sub/domain.
It has nothing to do with the DNS server any such packet is destined for—in this case 8.8.8.8.
-
@tinfoilmatt said in Quesiton about the alert system on Suricata:
No. This rule, 1:2042936, merely alerts (or blocks if configured to do so) on individual packets containing a DNS query for any .duckdns.org sub/domain.
This is not 100% correct. In the pfSense package, it depends on whether the user has enabled blocking mode and WHICH particular blocking mode is chosen.
Legacy Blocking Mode does in fact result in a BLOCK on any IP that triggers a rule - even if that rule has the ALERT action instead of DROP.
There is an optional mode of Legacy Blocking Mode that causes the custom blocking plugin to only block traffic that matches a rule having the DROP action. This mode is enabled by checking the box to "Block on DROP only".
Finally, if using Inline IPS Mode blocking, then only rules whose action verb the user has specifically changed to DROP will block (or drop) traffic.
Also note that Legacy Mode Blocking works by adding the offender's IP address to a hidden
pftable that is the target of a hidden block rule in pfSense. Any IP address added to that table is blocked by the firewall. In the alert given by the OP, then indeed the Google DNS IP of 8.8.8.8 would indeed get blocked for ALL hosts once it was added to thepftable. Pass Lists are used to create IP lists that do not get blocked.And for the benefit of the OP and others, those ET INFO rules should not generally be enabled when you are using Legacy Mode Blocking unless you specifically enable the optional "Block on DROP only" feature. Those rules are simply informative in nature. They do not represent malicious behavior. Those rules are simply meant to give the admin a picture of different traffic traversing the network. Not all of that traffic is malicious.
Read through all the Sticky Posts at the top of this forum to gain a better understanding of the various blocking modes available in the Suricata package.
-
@bmeeks said in Quesiton about the alert system on Suricata:
Also note that Legacy Mode Blocking works by adding the offender's IP address to a hidden pf table that is the target of a hidden block rule in pfSense. Any IP address added to that table is blocked by the firewall. In the alert given by the OP, then indeed the Google DNS IP of 8.8.8.8 would indeed get blocked for ALL hosts once it was added to the pf table.
Yikes! I was actually pretty far off 100%. You're too kind.

So 8.8.8.8 ends up blocked in this scenario if using Legacy Blocking Mode, the rule's default ALERT action isn't modified, and "Block on DROP only" is not checked...
But if using Inline IPS Mode, is it true that 8.8.8.8 would NOT end up blocked in this scenario, even if the rule action was modified to DROP? Merely the offending packets would be dropped? (I.e., the "custom blocking plugin" only functions under Legacy Blocking Mode?)
-
@tinfoilmatt said in Quesiton about the alert system on Suricata:
But if using Inline IPS Mode, is it true that 8.8.8.8 would NOT end up blocked in this scenario, even if the rule action was modified to DROP? Merely the offending packets would be dropped? (I.e., the "custom blocking plugin" only functions under Legacy Blocking Mode?)
Reply
Correct. Legacy Blocking Mode is something that existed before Inline IPS Mode with netmap was available. It works by copying the offender's IP address into a
pftable (the snort2c table). A hidden firewall rule created by pfSense when it initializes the packet filter then blocks all traffic to and from any IP address loaded into that table.Legacy Blocking Mode can "leak" packets because the initial traffic gets through until Suricata has enough data to raise the ALERT. That alert is intercepted by the custom blocking plugin and the plugin copies the IP address into the snort2c table via an API call. Inline IPS Mode is better because it does not "leak" any initial traffic, and it blocks only specific packets and not all packets.
Inline IPS Mode drops only individual specific packets that trigger a DROP rule. Legacy Blocking Mode, on the other hand, works by completely blocking all traffic to or from a target IP address.
-
@bmeeks o wow thanks so much for the reply currently only have it monitoring not blocking, So in other words in inline IPS mode would only blog the destination duckdns.org right?
-
@killmasta93 said in Quesiton about the alert system on Suricata:
@bmeeks o wow thanks so much for the reply currently only have it monitoring not blocking, So in other words in inline IPS mode would only blog the destination duckdns.org right?
Inline IPS Mode (assuming you went in and changed the default rule action from ALERT to DROP) would drop only packets destined for the IP that duckdns.org resolved to.
Understand that all rules ship by default from the rule creators with their action set as ALERT. That is "monitor only". If you want a rule to instead drop traffic that matches, then you must change the rule's action from ALERT to DROP. You can do that using the tools available on the SID MGMT tab in the Suricata package. There are example conf files there to get you started. Also spend some time reading the Sticky Post threads I've created at the top of this sub-forum.
-
@bmeeks THank you so much will do thanks