Site-to-Site OpenVPN with Mikrotik : all ok from mikrotik, can't access mikrotik from pfsense
-
@viragomann Correct. Not sure what his setup is, but he needs to allow from his LAN network. He wrote somewhere that 10.10.11.0/28 is LAN, but if 10.10.11.0/28 is his tunnel network, the correct allow should be from LAN.
-
HI to ALL
and FIRST :) ... Thank you to ALL@viragomann , tnx in advance, yes I wrote 10.10.11.0/28 is LAN ( but configured like Virtual IF on pfsense )
10.10.11.0 was the tunnel classneedings:
site B ( with internal lan 192.168.88.9/24 ) accessible from site A ( internal lan 192.168.1.0/24 same as the wan class for pfsense ). i had configure, in fact, virtual IF with OVPN peer2peer to use advanced routing configuration ( i know is very difficult use a p2p with only one interface on pfsense)
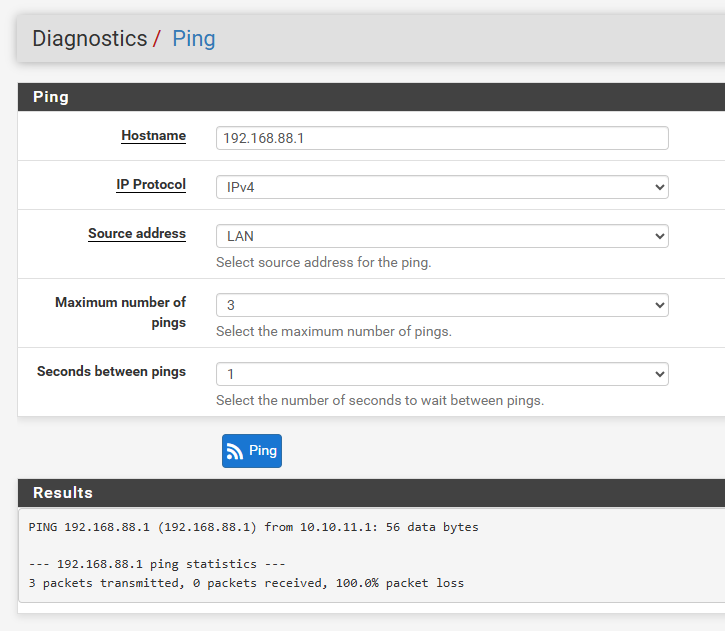
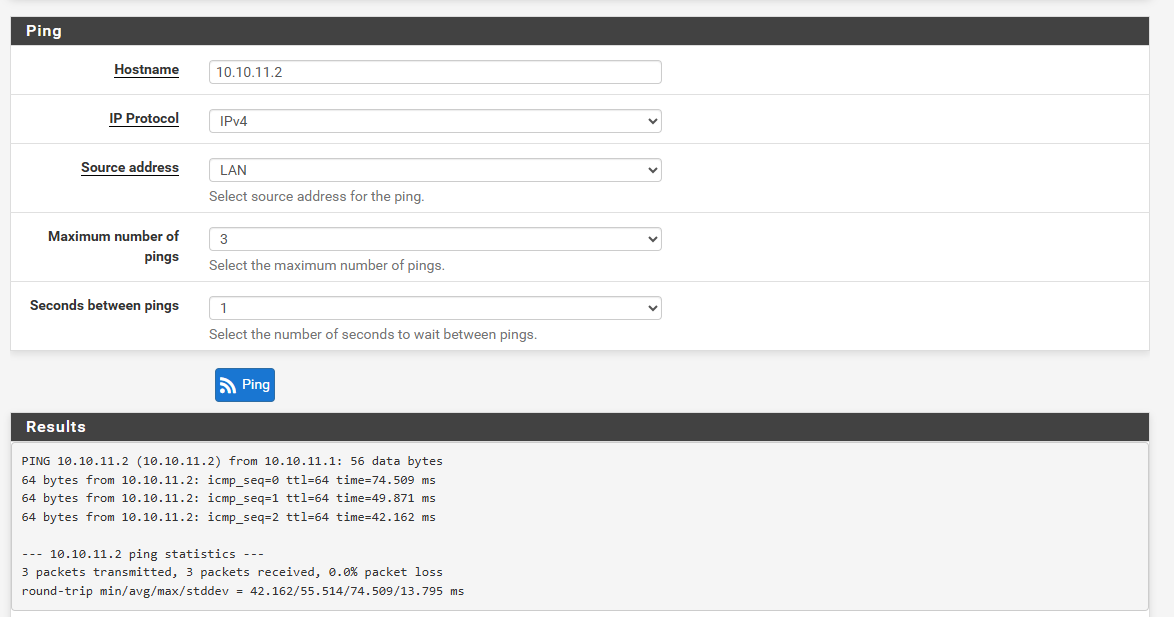
viceversa, at this time, was ok, i can ping and reach host at the site A.
at this time from PFSENSE can't ping from host pc, tunnel ip and destination lan.
it's important for me, reach both side of the VPN to share resource form point to other point.
Try the @peterzy config have no correct result :(
there is something that i can't see on pfsense..
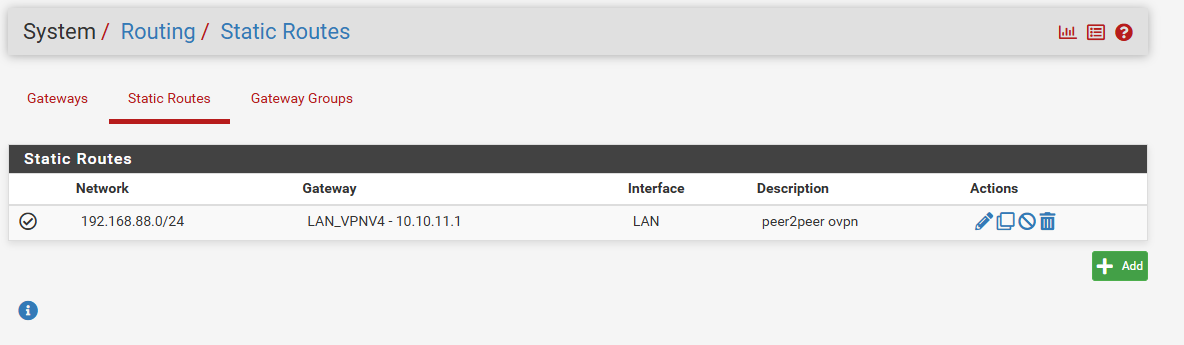
the problem i see was pfsense use always the router GTW instead of the vpn tunnel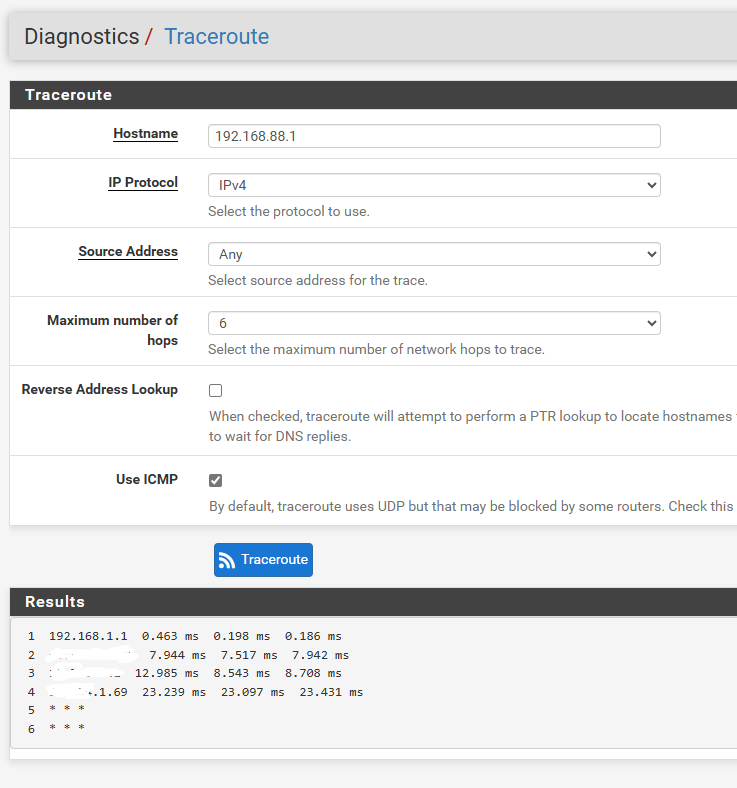
first hop 192.168.1.1 and not 10.10.11.1
try to add a static route but nothing
and in my ovpn config
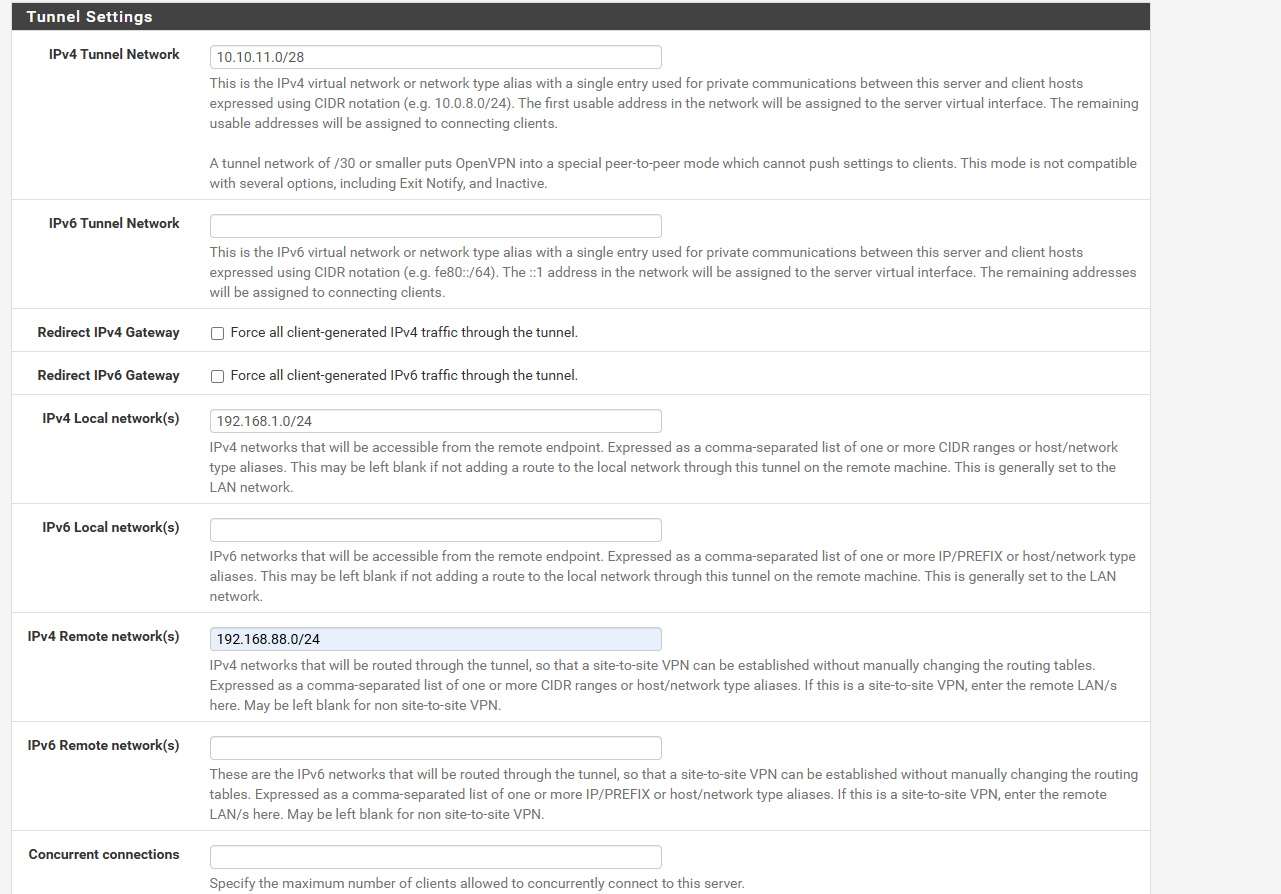
Regards!
-
@RoSs81_ct
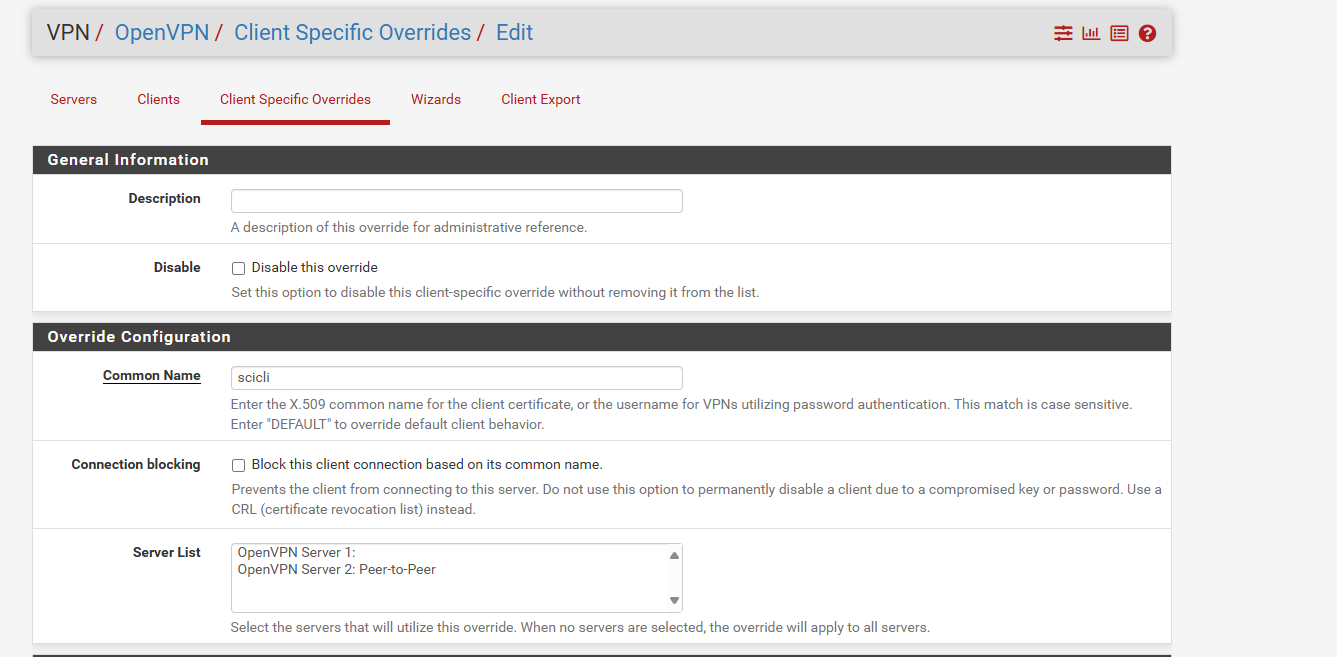
Are you missing the client specific override by any chance? -
sorry but I can't understand what you mean by your question
you mean: that I forced OVPN to use local and remote networks in a forced way? I can also remove them.
thank you in advance
-
@RoSs81_ct
VPN > OpenVPN > Client Specific Override
I assume, you've configured an SSL OpenVPN? With a shared key site-to-site this is not needed. -
-
@RoSs81_ct
Yes. -
-
@RoSs81_ct
In the server list you have to select the respective server for which you want to configure a CSO.You didn't reply to the VPN type. Maybe there is an easier solution.
-
unfortunately, nothing change :(
I'm considering the idea of adding a mikrotik at the other site and adding the IPs of a new internal lan to the necessary clients.
works on a pfsense with a single IF was stressful. :)
thank you so much to ALL :)
-
@RoSs81_ct
Still not clear, which authentication type you've configured.
If it's an SSL AND you don't need to connect multiple clients to the server you can simply set the tunnel mask to /30. With this the CSO isn't needed.Otherwise you have to ensure, that the CSO is applied properly and that the route are added. You can check this in the OpenVPN log, however, you have to enhance the verbosity level to 4 first and reconnect the client.
-
You are right, i forgot it.
Tls/ssl with certificate and pre shared keyConnection between the 2 side was ok, from site b ( internal lan 192.168.88.0 ) i can reach all the host of site A pfsense included .
I have one client on site A must accept 3 o 4 connection at same time, rdp session for a software.
Tomorrow, if I have time, i can post some other screenshot of pfsense vpn config for the p2p.
Best regards and thank you so much.
Have a nice WE!
-
Hi to all
so, little RECAP
SITE A:
Operator Router-> SWITCH -> ESXi with PFsense
Public IP -> Internal Lan 192.168.1.0/24 -> PFSENSE wan 192.168.1.240 with GTW 192.168.1.1 and virtual Interface ovpn peer2peerSITE B:
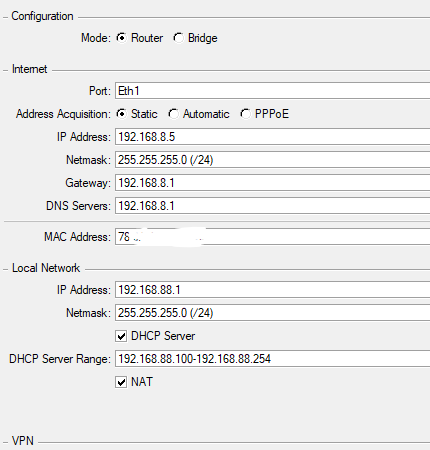
Operator Router-> Mikrotik -> Internal LAN
Public IP -> wan 192.168.8.1 - LAN 192.168.88.1 -> Internal Lan 192.168.88.1/24Peer to Peer tunnel 10.10.11.0/28 ( site A 10.10.11.1 / site B 10.10.11.2)
Connection OK between site
ping - other service from B to A -> OK
ping - other service from A to B -> KOPFSENSE CONFIG:
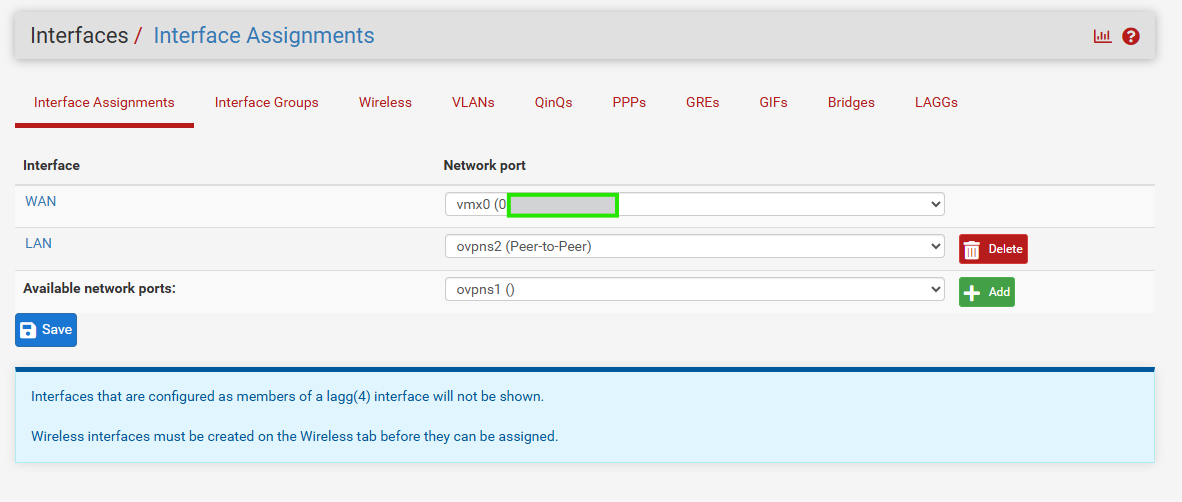
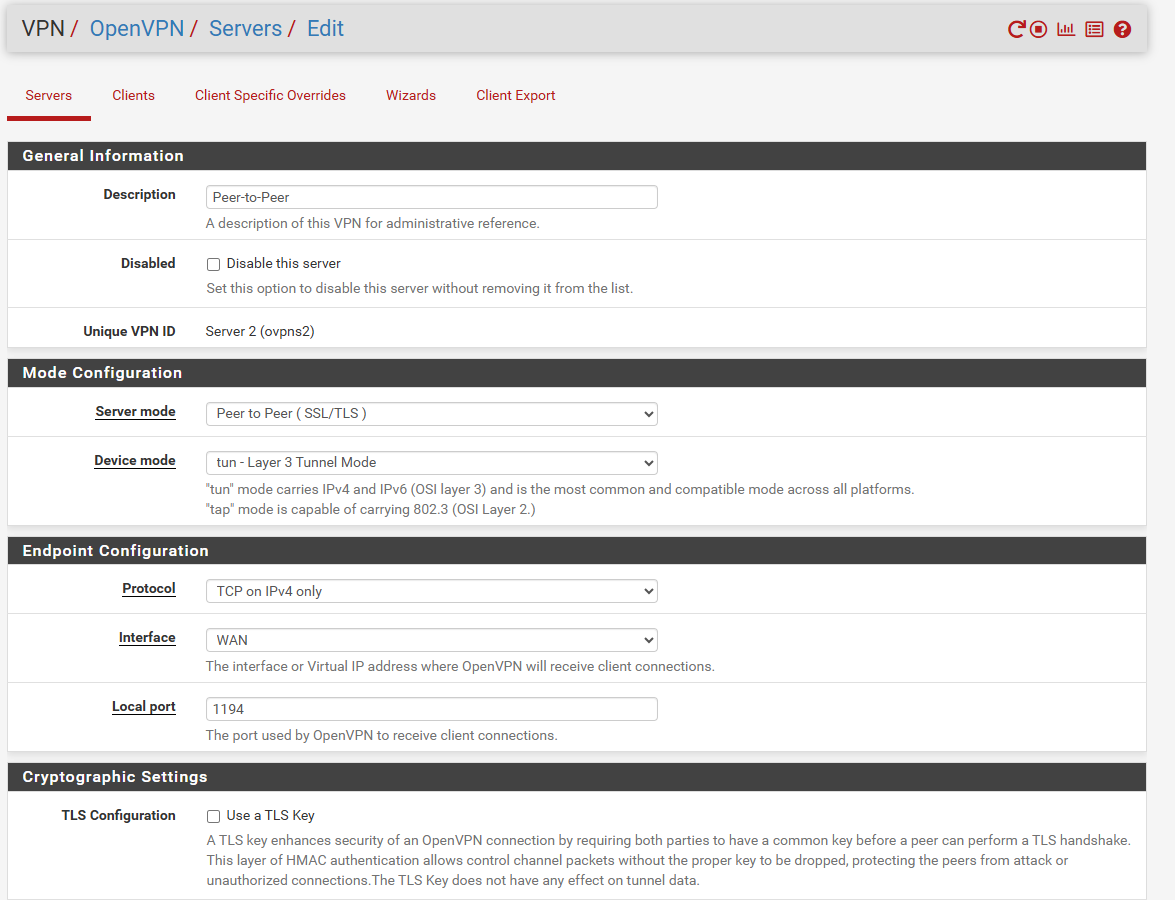
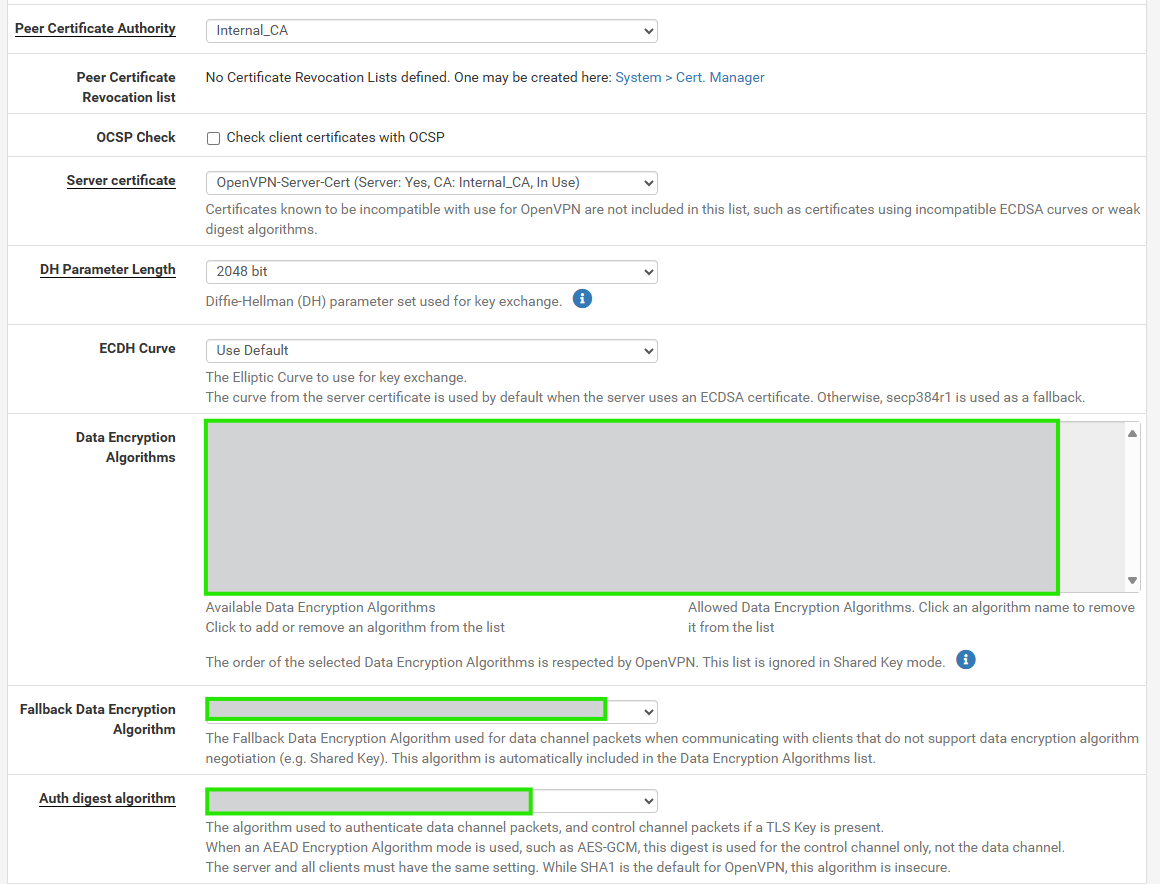
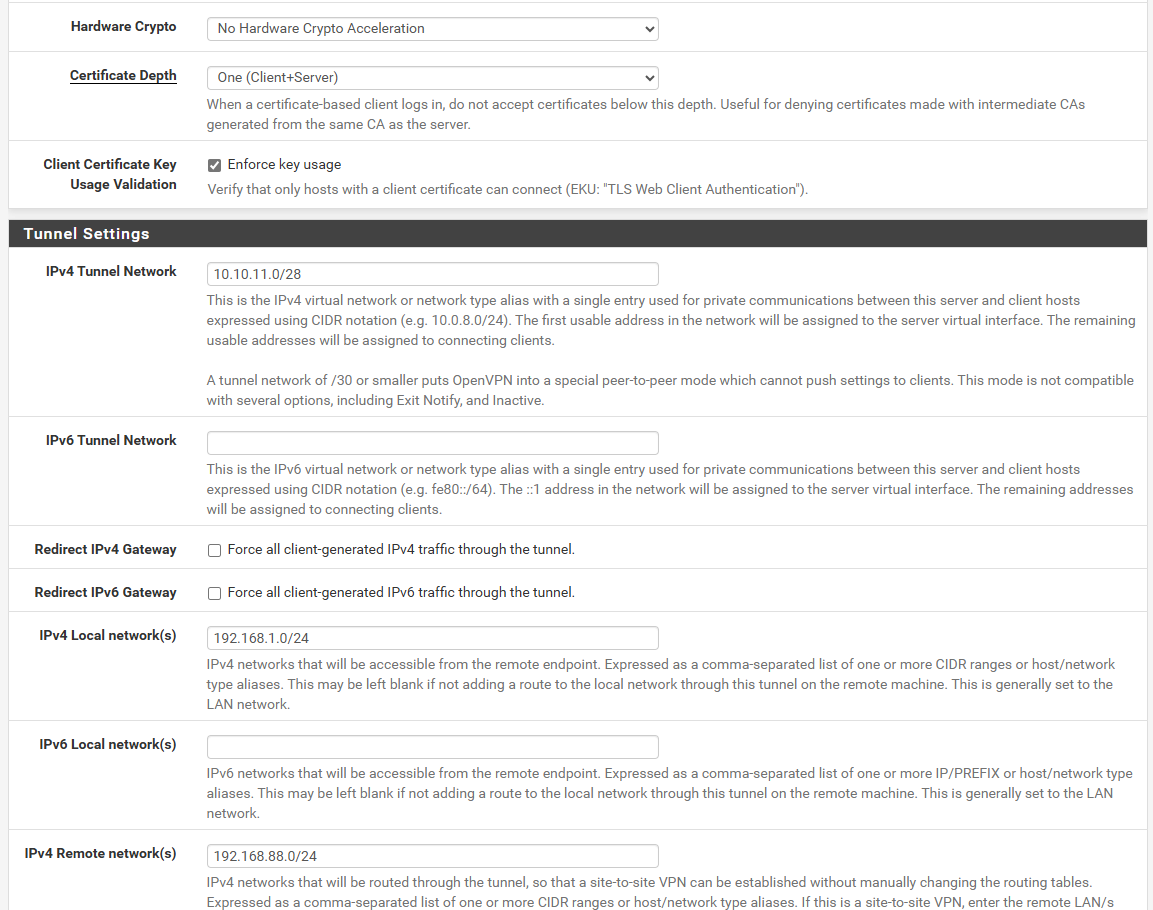
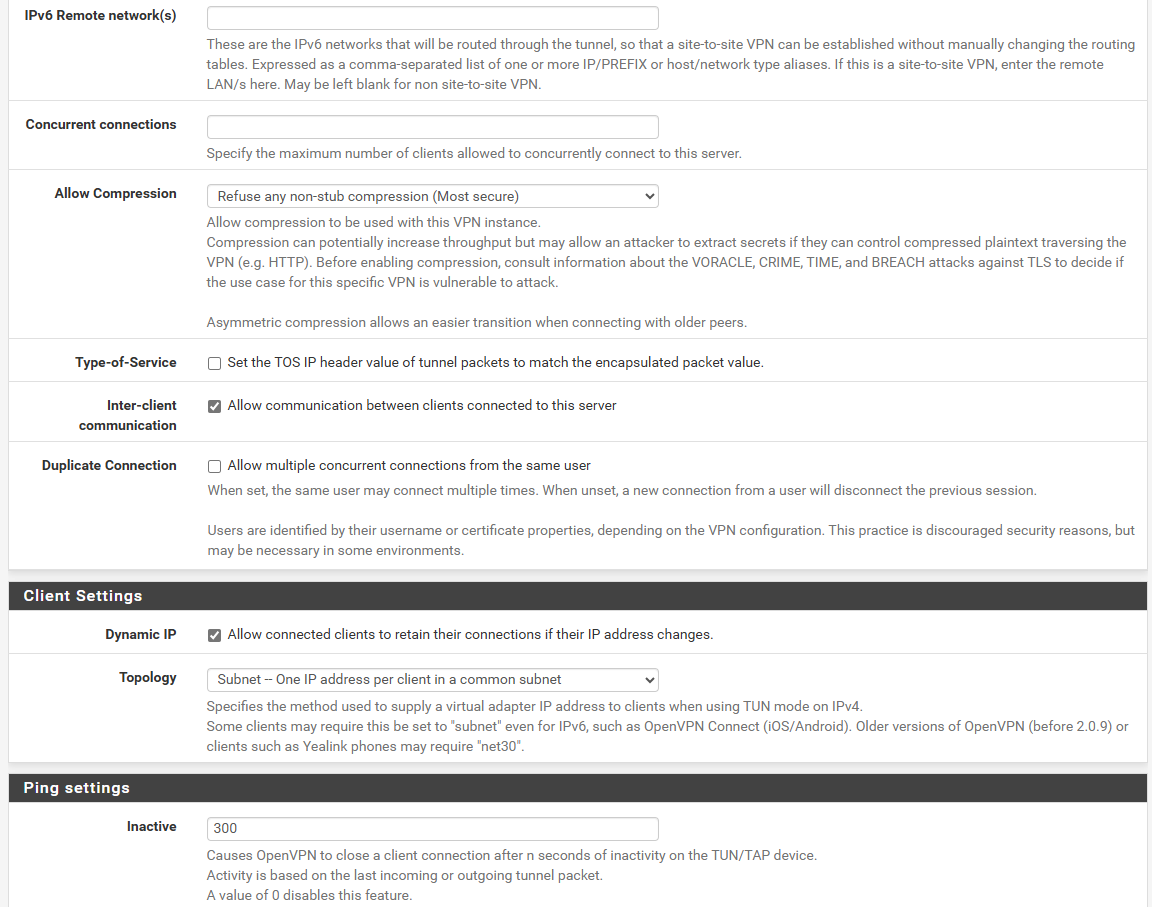
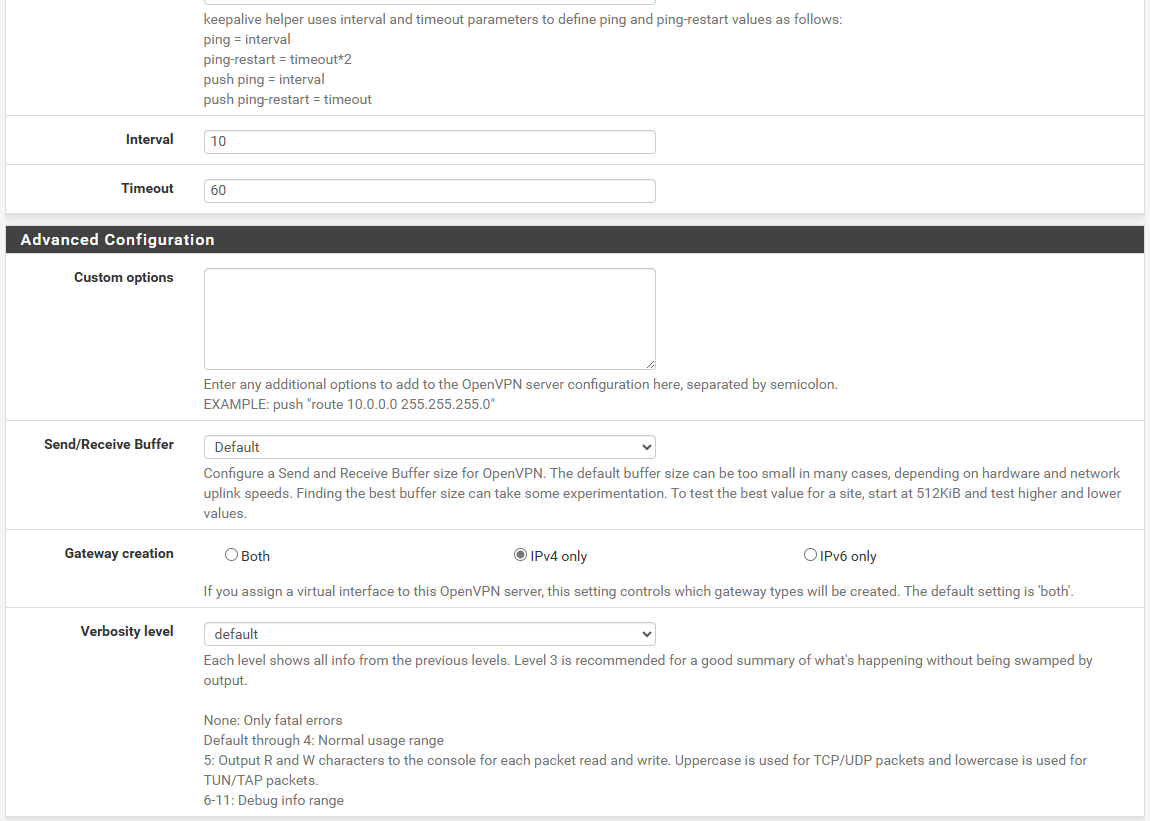
With and Without CSO tested, but nothing change.
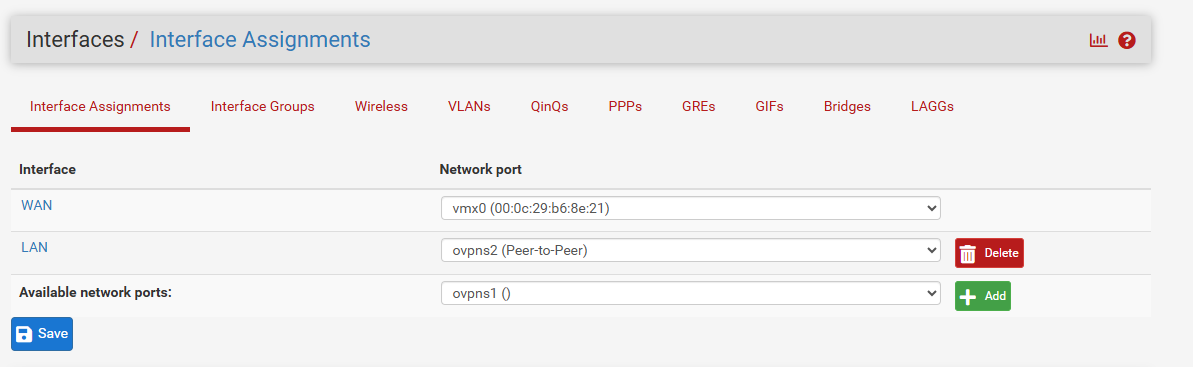
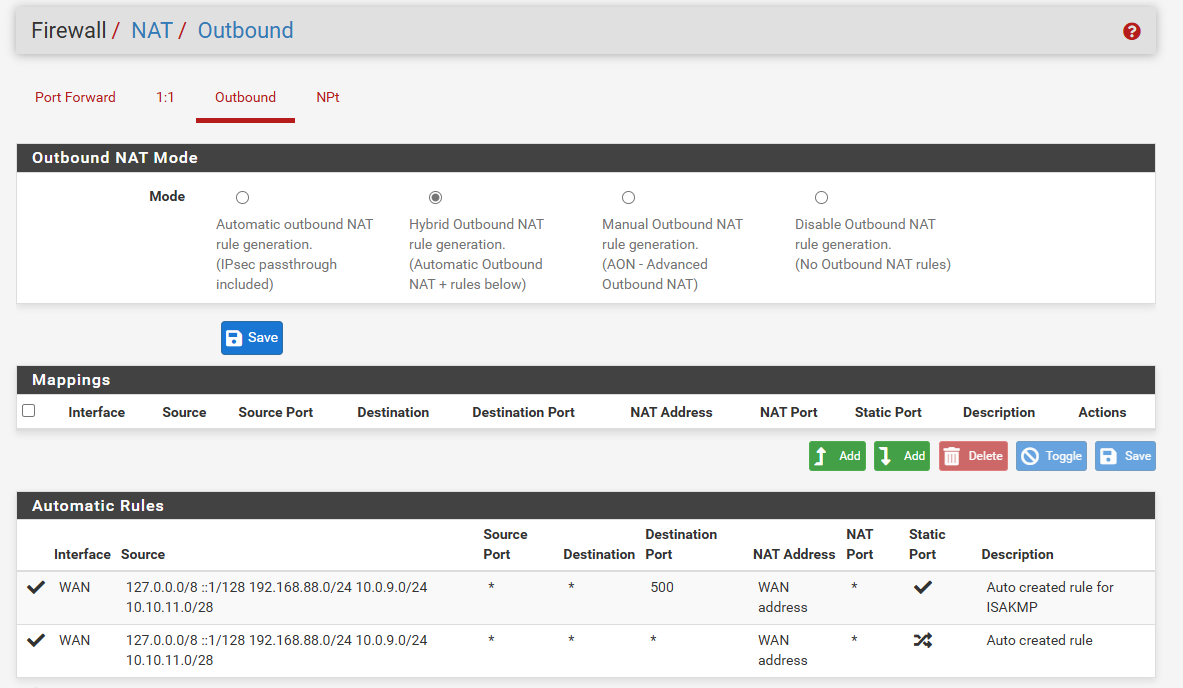
NAT
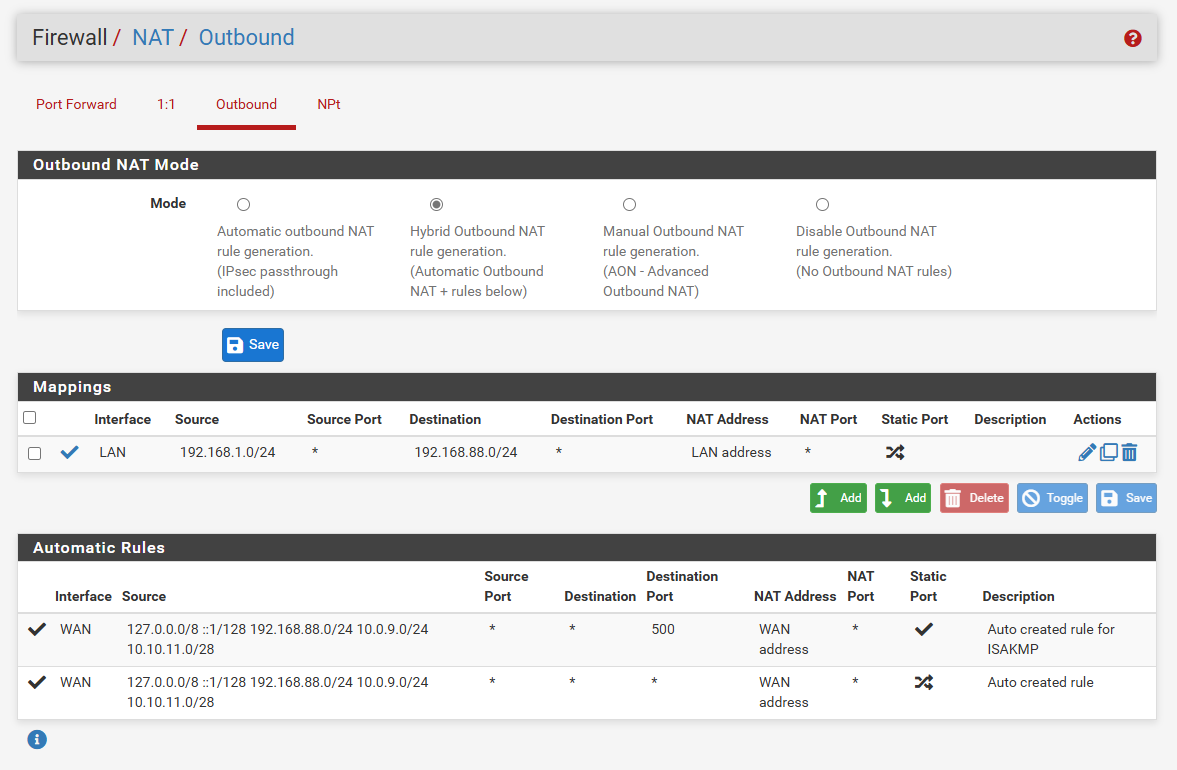
Rules
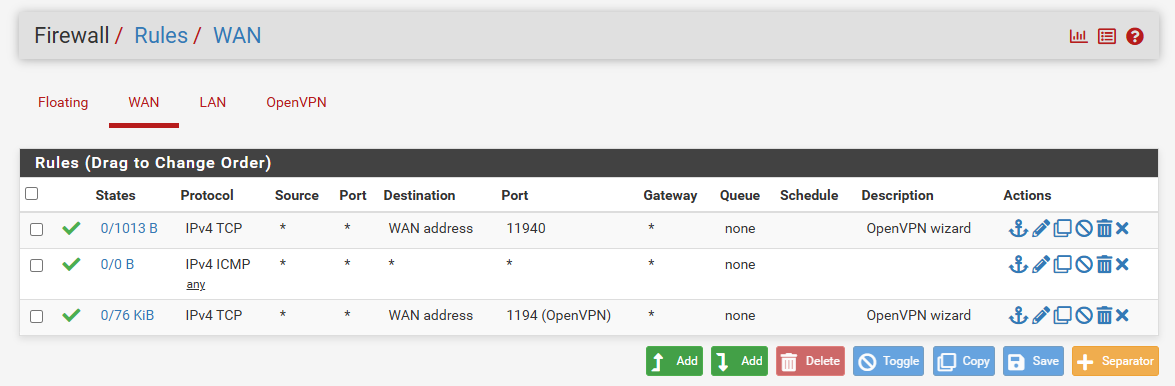
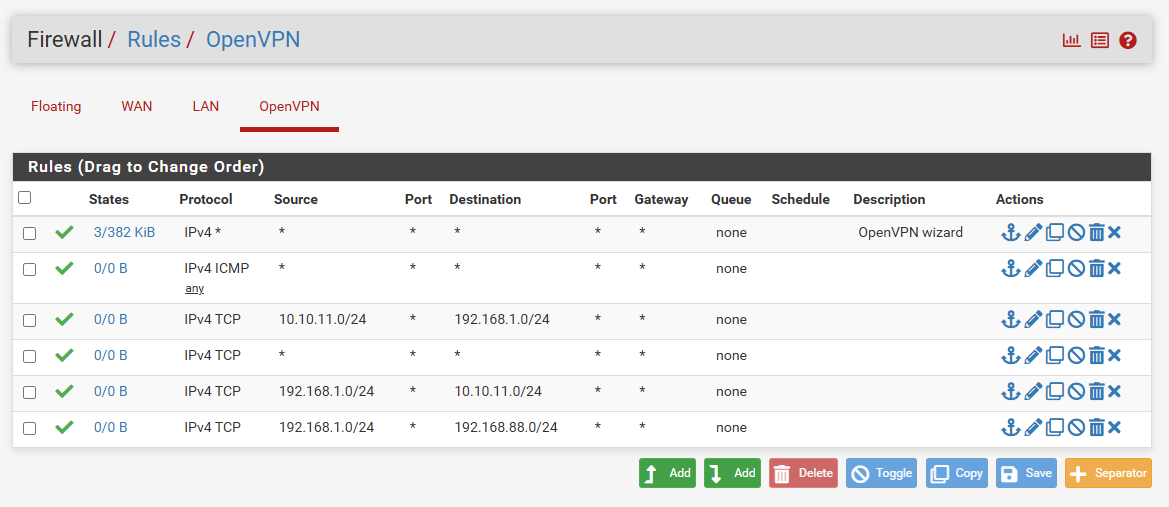
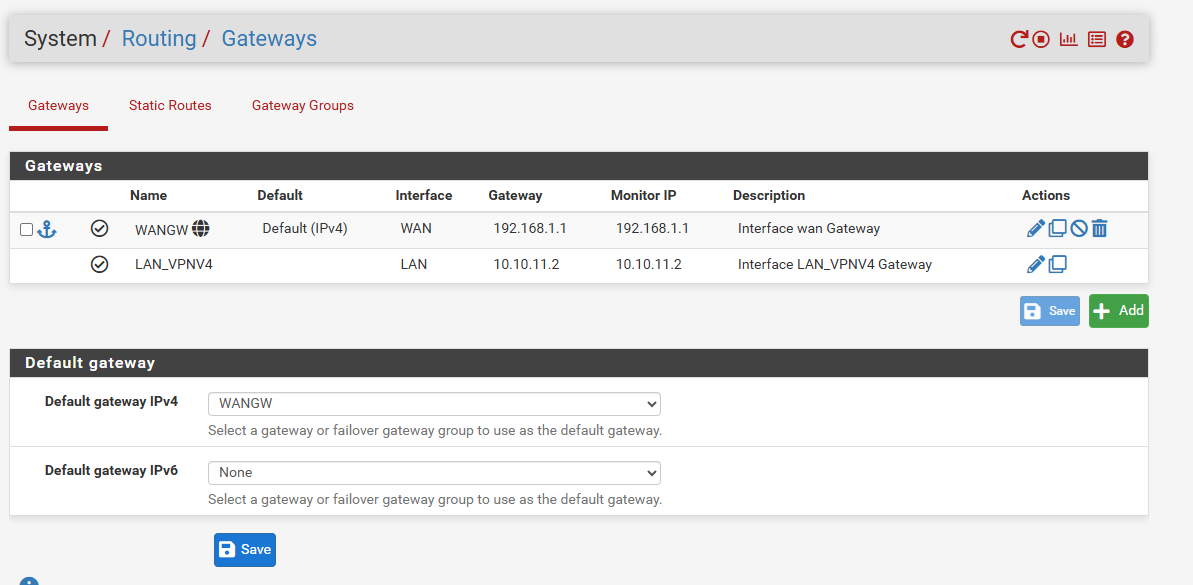
ROUTING
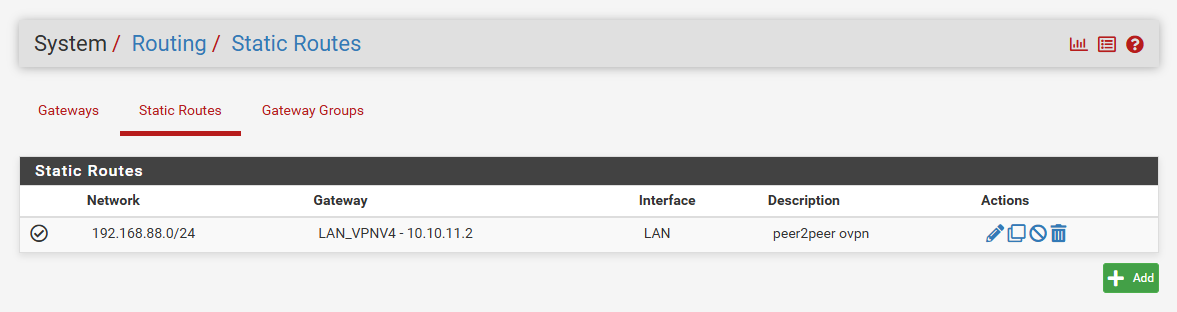
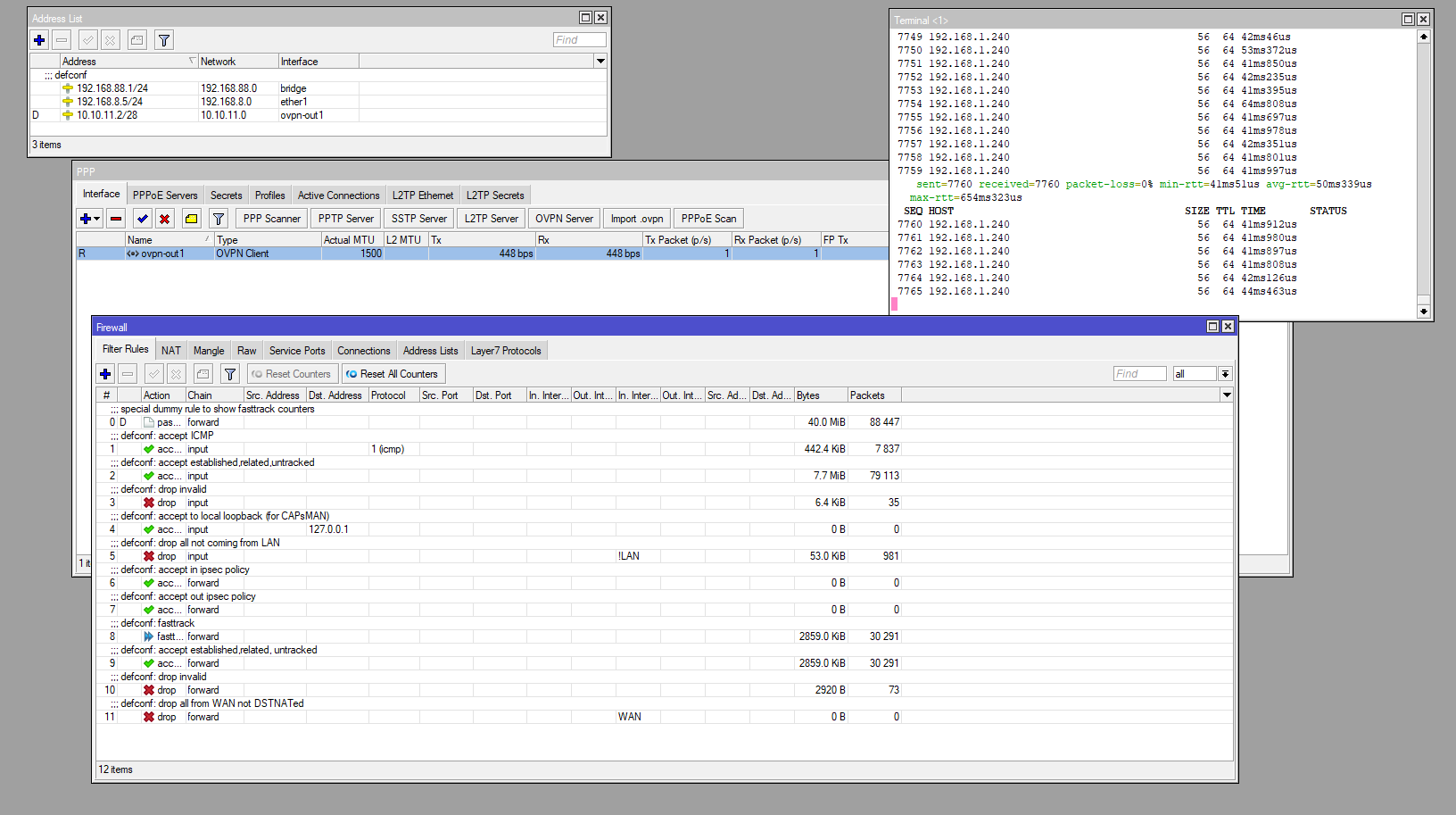
SITE B: MIKROTIK
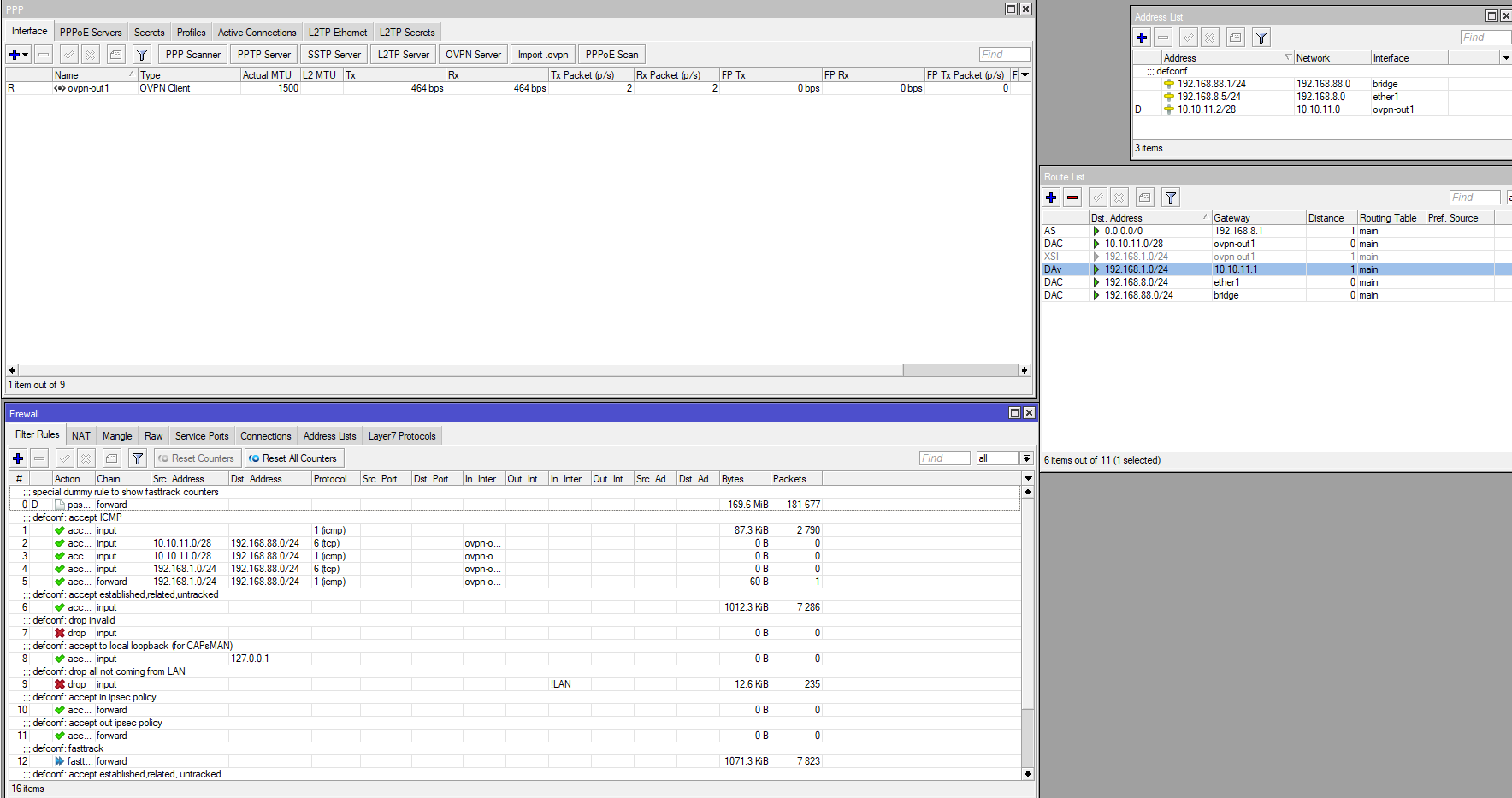
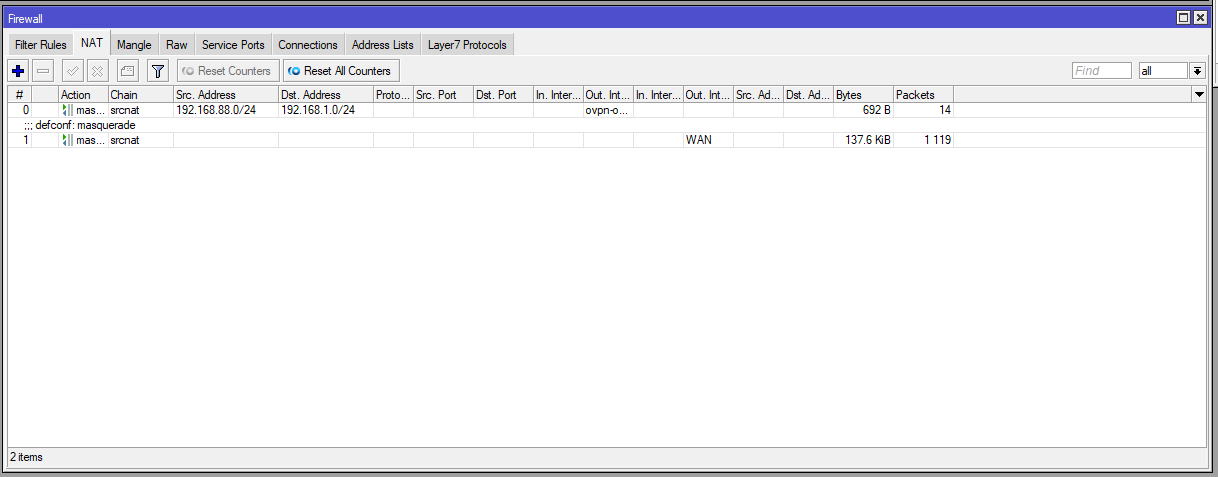
Sorry for all the photos, but, it's to understand how the 2 devices were configured.
Any help is welcome, I don't know what else to check or other configurations to try.
Esxi has no rules on the internal switch.**thank you so much for all the advice already writed, and have a nice new week.
ANDDD sorry for my English XD.**
REGARDS