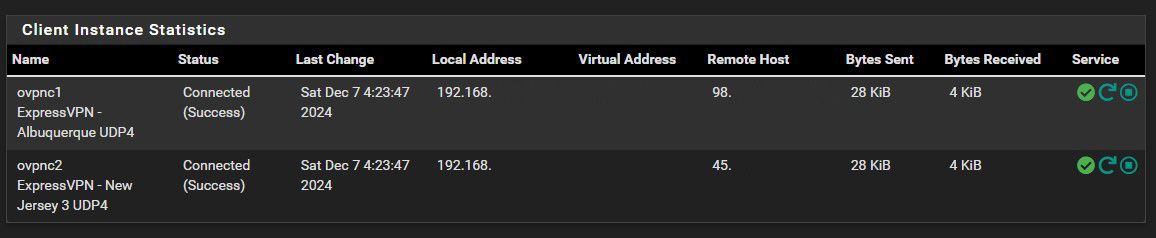
Setting up ExpressVPN using OpenVPN
-
@marksinister said in Setting up ExpressVPN using OpenVPN:
You mean this?
link text
No sure.
This https://www.expressvpn.com/support/vpn-setup/pfsense-with-expressvpn-openvpn/#routeThat guide is somewhat older now, true.
The last time I tried it, it 'worked' - but I'm pretty sure that "doing things" by the letter will create a none working setup, as things 'do change'. -
Sorry for the late reply. Here are the screen shots for firewall rules.
Firewall Rules LAN page

The rule with the Red "X" was the first time I tried to follow the tutorial before I called ExpressVPN for help. I disabled that one, or I hope it's disabled here.
Next is the QNCNet Aliases page.

Next is the ExpressVPN Gateway setting for the New Jersey 3 connection.

Next is the ExpressVPN NJ Rule.
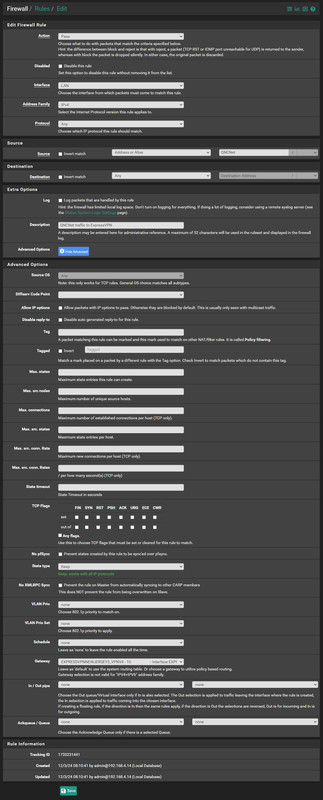
And Last is the LAN edit page

Let me know if I missed anything?
-
@Gertjan That is why ExpressVPN pointed me to this forum to try to resolved the problem. Because when they were walking me through it. They notice that most of the setting were not showing up in the new version.
I just submitted screenshots of my firewall rules to stephenw comment post if you want to take a look at it. Any advice would be very helpful.
-
Ok, well that should work as long as the EXPRESSVPNNEWJERSEY3 gateway is on-line and your are testing from a client within the QNCnet alias (192.168.4.0/24).
What is the QNCnet alias? Why not just use the LAN subnet there?
The rule shows only one state and 10k of traffic so it is matching something, but not much.
That rule you have with the red X on it can never match anything, I assume that's why it's disabled. And has the red X!
-
Let's see your outbound NAT settings too.
The ExpressVPN walkthrough has you edit the WAN rule which would disable traffic leaving the WAN dircetly. That's what many customers would want but I always advise against it. However you are still seeing traffic leave the WAN and get replies so your rules must still include that.
-
This :
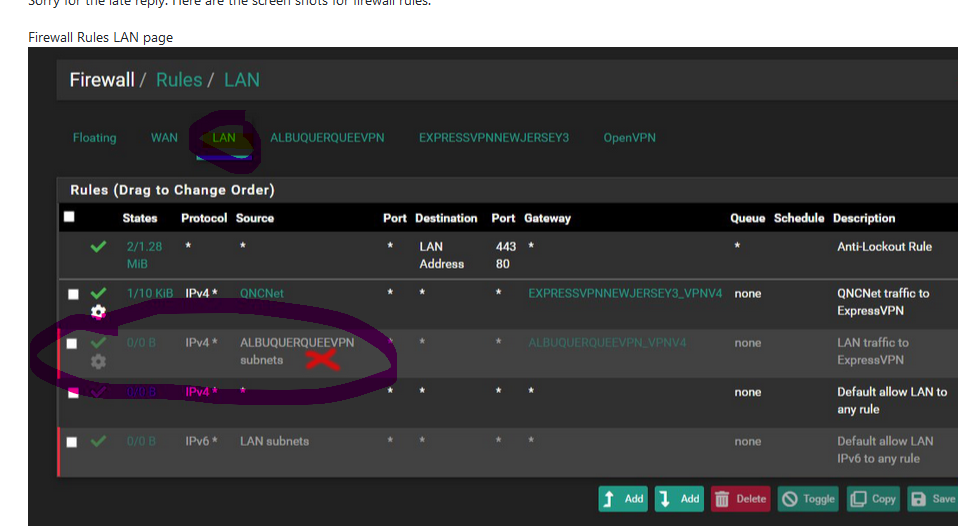
comes from where ?
Your pfSense LAN uses 192.168.1.x/24 with pfSense LAN being 192.168.1.1.
So, every device on that LAN will use something between 192.168.1.2 to 192.168.1.254 ?
Right ?Yet you introduced a rule on the LAN interface that says : allow only traffic coming from a source IP named (alias) ALBERCURQUIVPN. I don't know what that alias stands for but I"m pretty sure it isn't 192.168.1.1/24 so that rule can never match/apply.
After all, the source IP can only be, on your pfSense LAN : 192.168.1.2 to 192.168.1.254.
Right ? -
"Your pfSense LAN uses 192.168.1.x/24 with pfSense LAN being 192.168.1.1."
My LAN is 192.168.4.x. The machine that connects to the internet through PFSense uses 192.168.4.35, The PFSense LAN IP is actually 192.168.4.188. It's a long story why it's that. But anyway my computer connects fine to the internet. I just have no VPN connection.
"Yet you introduced a rule on the LAN interface that says : allow only traffic coming from a source IP named (alias) ALBERCURQUIVPN."
No that was from my first ExpressVPN tutorial attempt. When they said to give it a description I didn't know what name to call my LAN that was connecting to the "Albuquerque Server" so I name my LAN that so I could know what server it is connecting to. I was planning to make a bunch of different connections, such as one to New York, one to London, one to Japan, etc... So I didn't know if I would have to make a new LAN Subnet everytime I needed to make a VPN server connection.
The QNCNet Subnet was just a test name I use when I was walking through the tutorial with the ExpressVPN support guy.
If the connection worked and I had to make a Subnet for every connection I would've probably just append the server name to the end of it if I had to make a subnet everytime I needed to make a VPN server. That's what I thought. -
"What is the QNCnet alias? Why not just use the LAN subnet there?"
QNCNet Alias should be my Subnet. It was just a description. I didn't understand what to name it. I didn't want to put something generic like LAN Subnet because I didn't know if I would have to make a new subnet evertime I wanted to make a different VPN server setup.
I didn't know if I made a connection to New York Server if I would have to make a LAN Subnet - New York, and if a made a London Server I woudl have to make a LAN Subnet - London, and so on and so on.
I was planning to make a connection to bunch the ExpressVPN servers so I can switch to different ones when I needed too.
"That rule you have with the red X on it can never match anything, I assume that's why it's disabled. And has the red X!"
This was my first attempt at following the tutorial. When I contacted ExpressVPN support they told me to start over from scratch. So I just disabled that from there (I hope it's disabled) and they walked me through the other connection that I made.
I didn't delete anything because I didn't want to delete a setting and then my machine wouldn't connect to the internet at all. The only thing I had working was the machine on the network can get on the internet. So I didn't want to delete anything just in case I can't figure out how to get my machine back on the internet.
-
@stephenw10 said in Setting up ExpressVPN using OpenVPN:
The ExpressVPN walkthrough has you edit the WAN rule which would disable traffic leaving the WAN dircetly. That's what many customers would want but I always advise against it. However you are still seeing traffic leave the WAN and get replies so your rules must still include that.
I'm kind of confused about this? I don't want to connect through the internet through the WAN. I want to connect to the internet through the VPN. When I tried disabling the WAN I have no internet access at all. So When I leave it enable I get internet access. But no VPN security.
Here's the Outbound settings. I'm only going into the New Jersey VPN since it's suppose to be a clone of the WAN connection. I'm going to post every setting from Top to bottom.
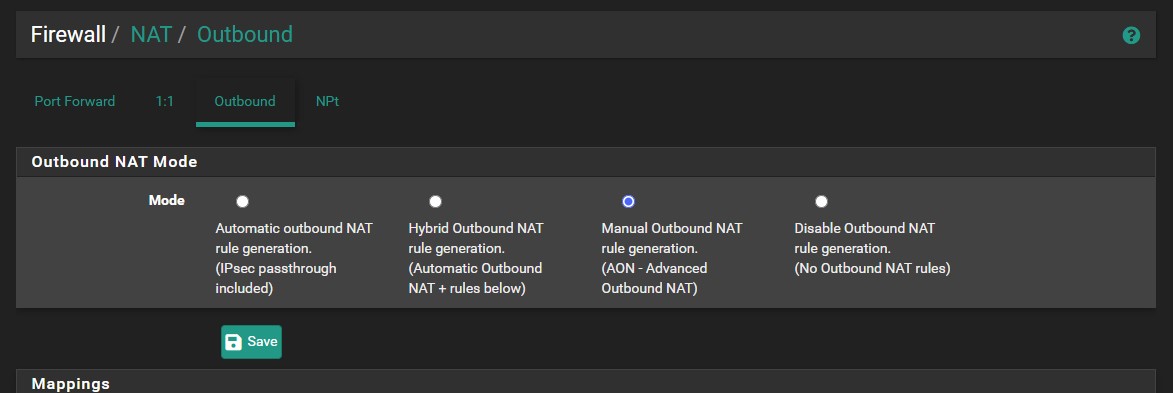







That should be all 6 connections cloned from the WAN connection.
-
Ok the problem is that in the cloned outbound NAT rules the translation address is still set to
WAN addressand it should beEXPRESSVPNNEWJERSEY3 address.You almost certainly don't need to IPSec specific port 500 rules on any interface. Those are only used if you have IPSec clients behind the firewall.
-
Hi, I changed all the clones to the ExpressVPN New Jersey Translastion address instead of WAN but it still saying my local ISP address on all the MyIP websites.


I really thought that was my mistake. But it seems it was not.

I didn't change the IPSec because I didn't know what to change it to.
-
You can just remove those IPSec specific rules. They don't do anything unless you have IPSec clients behind the firewall.
The rules translating traffic from LAN out of the VPN look correct now though.
So are the firewall rules still the same? So you see data/connections against the policy routing rules?
-
@stephenw10 said in Setting up ExpressVPN using OpenVPN:
You can just remove those IPSec specific rules. They don't do anything unless you have IPSec clients behind the firewall.
So you're saying just delete it out and leave it blank?
@stephenw10 said in Setting up ExpressVPN using OpenVPN:
So are the firewall rules still the same? So you see data/connections against the policy routing rules?
I didn't change anything since the last set of screenshots. The only thing I changed was the clones that you told me to change.
How to I check to see data/connections against the policy routing rules? The only thing I know to do is going on google and search for myip website to see if they can see my ISP IP address.
What am I suppose to look for when I check wherever I'm suppose to check?
-
@marksinister said in Setting up ExpressVPN using OpenVPN:
So you're saying just delete it out and leave it blank?
Yes, disable or remove them. I would disable them until I'm sure they weren't doing anything and then delete them.
@marksinister said in Setting up ExpressVPN using OpenVPN:
I didn't change anything since the last set of screenshots. The only thing I changed was the clones that you told me to change.
Those were the NAT rules though. The firewall rules are also unchanged?
You can see the states and traffic that a rule has passed in the rules list. If it's matching traffic there you will see it.
If it shows 0 states or traffic that something else is passing it. -
@stephenw10 said in Setting up ExpressVPN using OpenVPN:
Yes, disable or remove them. I would disable them until I'm sure they weren't doing anything and then delete them.
This part is kind of confusing?
Do you want me to delete these?
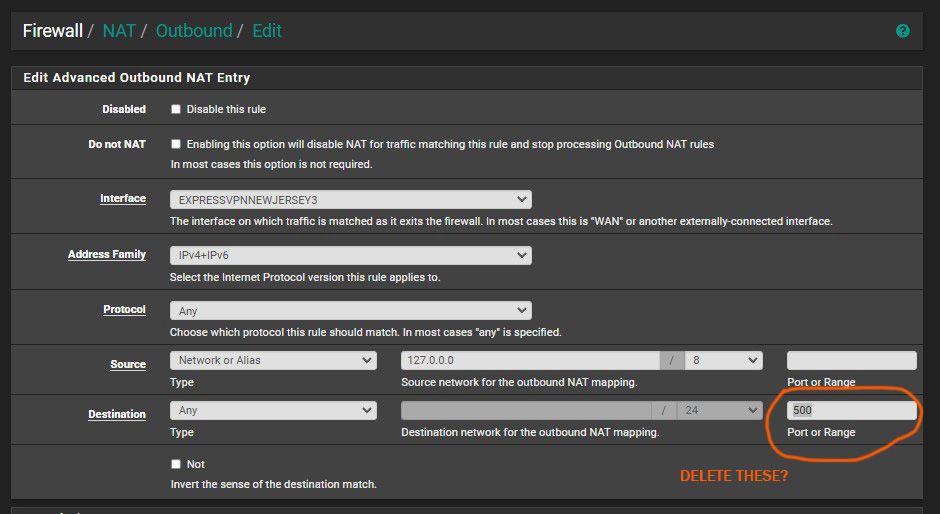
or do you want me to delete or disable these?
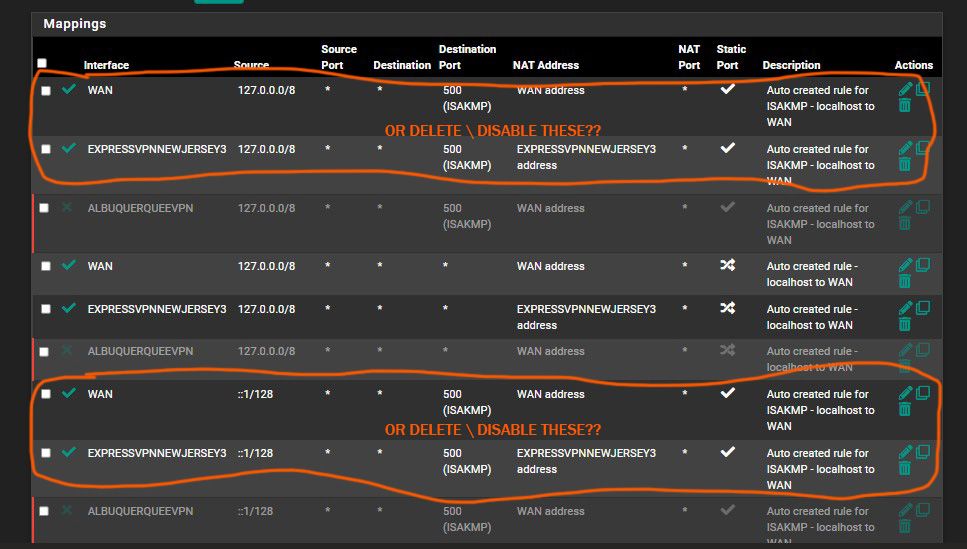
Also should I still have the WAN version enabled at all? I mean since I'm trying to only use the ExpressVPN connection should it still be enabled?
@stephenw10 said in Setting up ExpressVPN using OpenVPN:
Those were the NAT rules though. The firewall rules are also unchanged?
Here are the Screenshots for the Firewall Rules
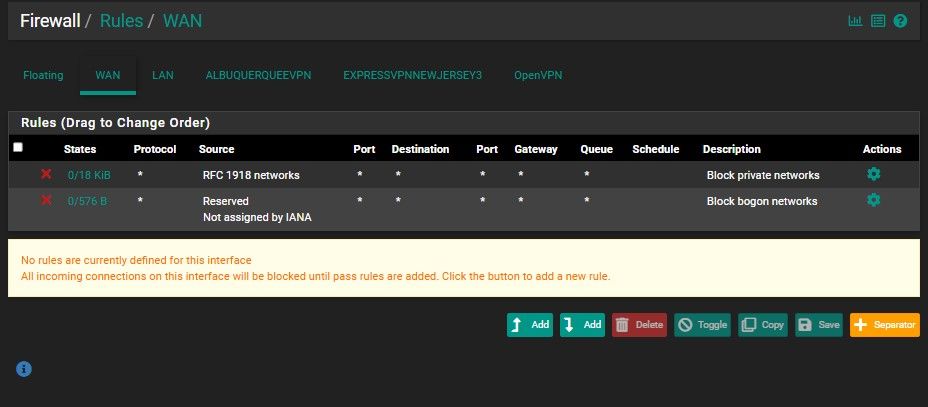
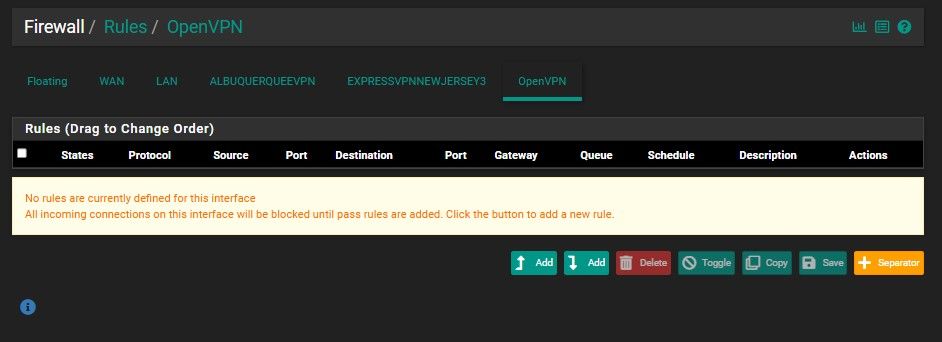
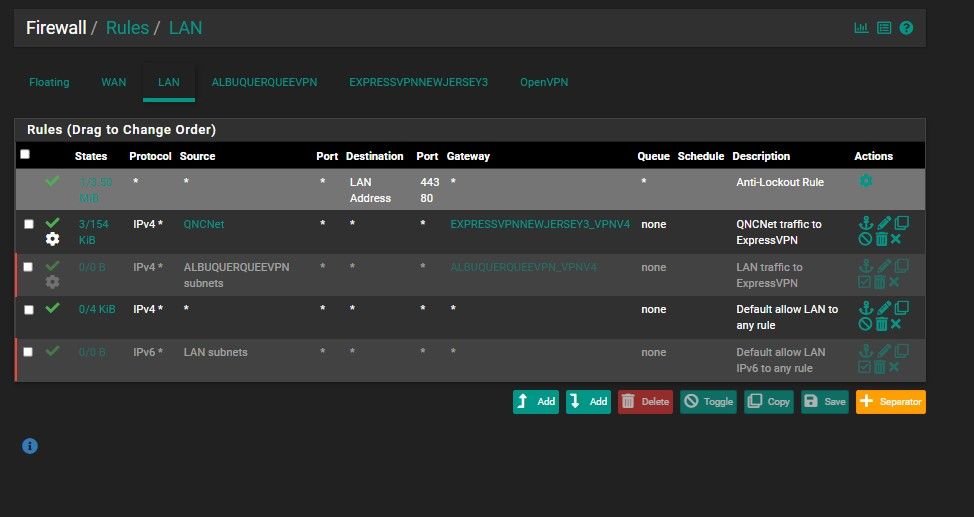
Those are the screen shots you wanted right?
-
Yes just disable all the outbound NAT rules that have destination port 500 in them. They are not needed and just make it more difficult to read.
Those firewall rules look good. As long as you are testing from a client inside the QNCNet alias and the EXPRESSVPNNEWJERSEY3_OVPN4 gateway is up traffic should go via the VPN.
-
@stephenw10
That worked thank you very much!One last question I have a connection to New Jersey. How will I be able to make connections to other locations like Canada, Japan, Mexico and other locations? Will I need to do all the steps again or can I just copy the NJ settings and change the VPN codes?
I'm just wondering if I have to do the same thing for all the other locations that I would like to switch to when I need to?
-
You can setup multiple tunnels and enable/disable policy routing rules as required. However it's common to find a VPN provide ruses the same tunnel subnet for all servers which then creates a routing conflict in pfSense. If ExpressVPN does that you would need to enable only one VPN client at a time.
-
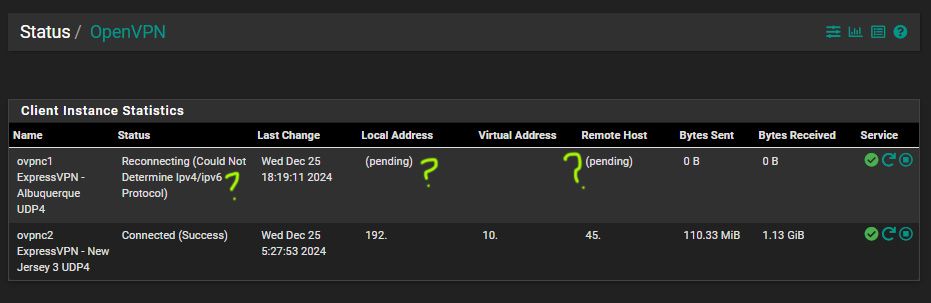
Yeah this is what kind of confusing right now.
Before I asked for help I had an Albuquerque that I disabled. But if you notice in the very beginning it was some what working the same as the New Jersey connection. Now that the New Jersey Connection is working I can't seem to get the status for the Albuquerque VPN to start back working. I think I disabled something somewhere and I don't know how to reenable it. I don't want to poke around and lose my New Jersey connection in the process.
-
Well there it's not connecting. Check the OpenVPN logs to see what error is shown.
You don't need to redact those private IP addresses (192.168.x.x, 10.x.x.x) they are not publicly routable. That 45.x.x.x address is ExpressVPNs server address which is public anyway. The only thing you might redact is your own public IP.