AES-NI or IPsec-MB
-
HELLO, WHAT SHOULD ME USE WITH OpenVPN DCO. BOTH OF THEM OR ONLY ONE OF THEM?SHOULD MEVKEEP ON IN ADVANCED SETTINGS, BOTH OF THEM?OR ONLY ONE OF THEM?
-
@Antibiotic There is a very good documentation @ https://docs.netgate.com/pfsense/en/latest/config/advanced-misc.html#cryptographic-thermal-hardware
If you have any doubts after reading it, feel free to ask.
Not that I'll know the answer, but someone else might. -
@mcury I HAVE READ THIS A LONG TIME AGO. THE QUESTION IS BOTH OF THEM KEEP ON. WHAT METOD WILL USE OPENVPN?OR HOW TO CHECK?
-
@Antibiotic said in AES-NI or IPsec-MB:
@mcury I HAVE READ THIS A LONG TIME AGO. THE QUESTION IS BOTH OF THEM KEEP ON. WHAT METOD WILL USE OPENVPN?OR HOW TO CHECK?
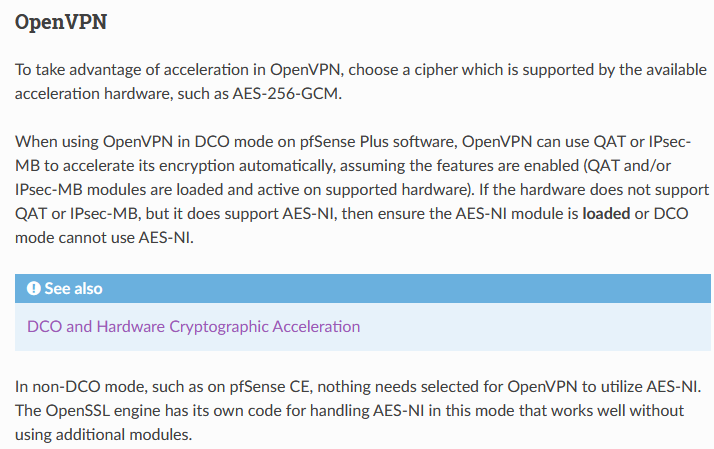
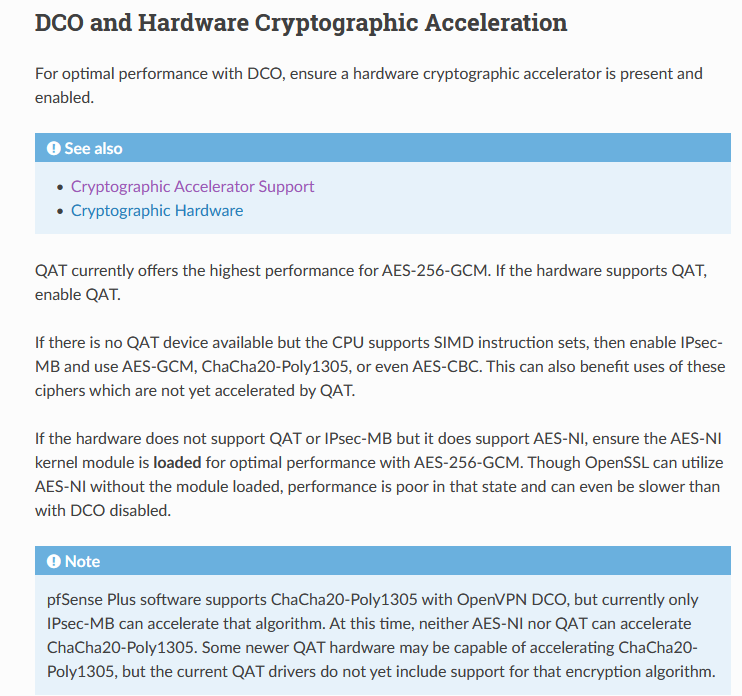
You don't have QAT, so ignore that.
If you are using OpenVPN DCO with ChaCha20-Poly1305, enable IPsec-MB.
If you are using OpenVPN DCO with AES-GCM, enable IPSec-MB.
If your device don't support both of the options above, enable AES-NI.I personally would run iperf tests to confirm which is better for your hardware.
-
@mcury said in AES-NI or IPsec-MB:
ChaCha20-Poly1305
thank you, will any benefits to use ChaCha20-Poly1305 instead AES-GCM, with PSec-MB regarding speed increasing?
-
@Antibiotic said in AES-NI or IPsec-MB:
thank you, will any benefits to use ChaCha20-Poly1305 instead AES-GCM, with PSec-MB regarding speed increasing?
The best way to find out is to create a openvpn server in pfSense, connect two devices to it in different networks, fire up openvpn at both sides to the openvpn server in pfSense and run iperf test, monitoring CPU usage of the firewall.
Take in consideration also the clients connecting to it, if there is no acceleration at the client side, ChaChaPoly-1305 would be easier for the client.
-
I use the SafeXcel and disable the IPsec-MB Crypto, it is much faster with OpenVPN connections that way for my 2100. I use to have both enabled but it caused a slower connection for some reason. The way I look at it, if you have a dedicated crypto chip use it and deactivate the other.