VLAN rules with lagg trunks
-
Hello,
I just set up 7 VLANs and 2 LAGG trunks on my pfSense firewall. What is the best practice for blocking traffic between VLANs? I was considering creating 7 aliases, each including all other VLANs, to block inter-VLAN traffic and then adding allow rules as needed for specific inter-VLAN routing. After that, I would create a general IPv4 any-to-any rule for each VLAN. The alias method seems more work than is needed.
Should I instead create a rule on each VLAN to block all traffic to any IP outside its own subnet?
Does the LAGG interface typically require any rules?
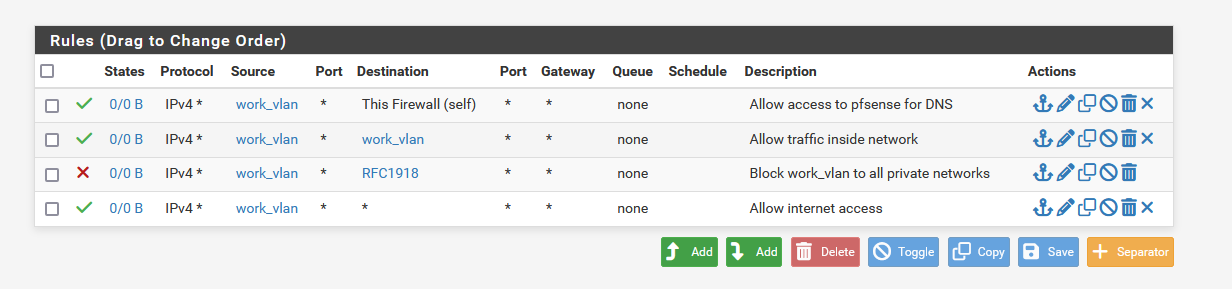
What is best practice for VLAN rules? Is the below generally correct?
I allow access to my firewall as that is where DNS is managed. I block all connections to private networks and then I allow all internet traffic.
Thanks!
-
@CatSpecial202 I do not think you will get the effect you want.
Rule #1 allows full access to the firewall.
Rule #2 will have no effect, inter-vlan traffic does not touch the FW.
Rule #3 blocks all access to other VLANs. This looks correct.
Rule #4 allows access to the internet. This looks correct.Change #1 to be only port 53. I also allow 123 (NTP).
Add a rule after #1 to deny to This Firewall. This will block all other access to the FW including management but will not block internet access. The anti-lockout rule or similar will be needed to let you in.
Delete rule #2.Remember the rules apply top down. Access to other VLANs will need to be added before the block RFC1918 rule.
-
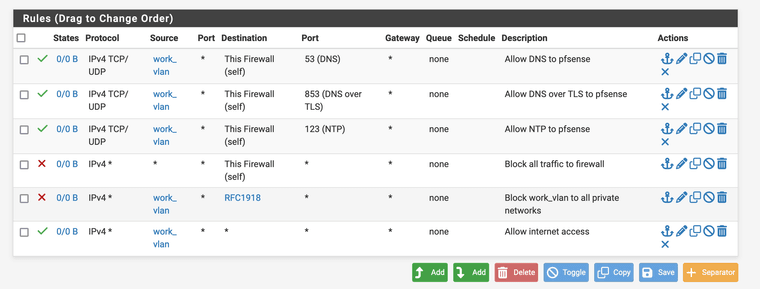
@AndyRH thank you for those recommendations. So, like this?
-
@CatSpecial202 That looks correct to me.