pfBlockerNG not blocking ADs
-
@wc2l said in pfBlockerNG not blocking ADs:
https://forum.netgate.com/topic/149343/pfblockerng-maxmind-registration-required-to-continue-to-use-the-geoip-functionality
Already 5 years go ...

But yeah, that's the one I used to upgrade me GeoIP account.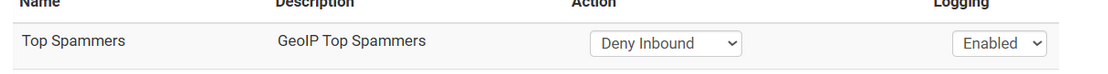
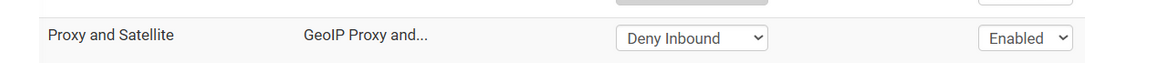
How do you use this ?
My case :
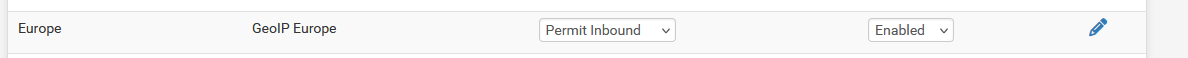
and I use these list with 'french' IPs so I can use it like this :
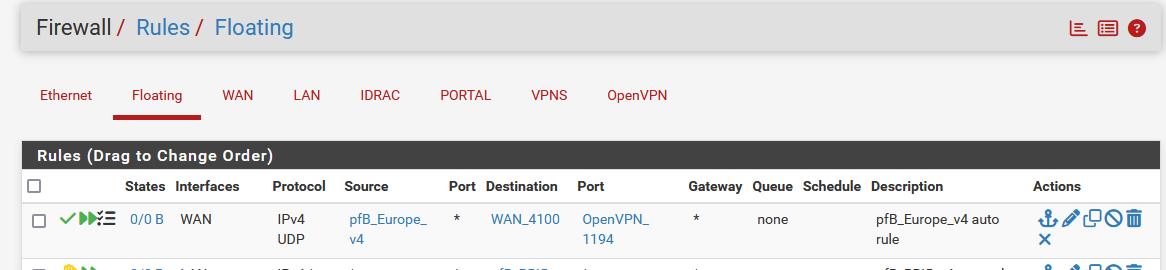
My goal is to allow only french IPv4 to access my OpenVPN port.
Why would you "Deny Inbound" ?
Why not using "the build in free of maintenance, good for everybody" default block all rule (on your WAN interface).if the context of this "Deny Inbound" is used for your WAN (it is, right ?) that, normally', everybody and everything is already blocked.
Except : your exceptions, like NAT rules.
Why do you make exceptions for "Top Spammers" ? Do you host a mail server behind pfSense or something like that ? -
@Gertjan
Here is my floating rules:
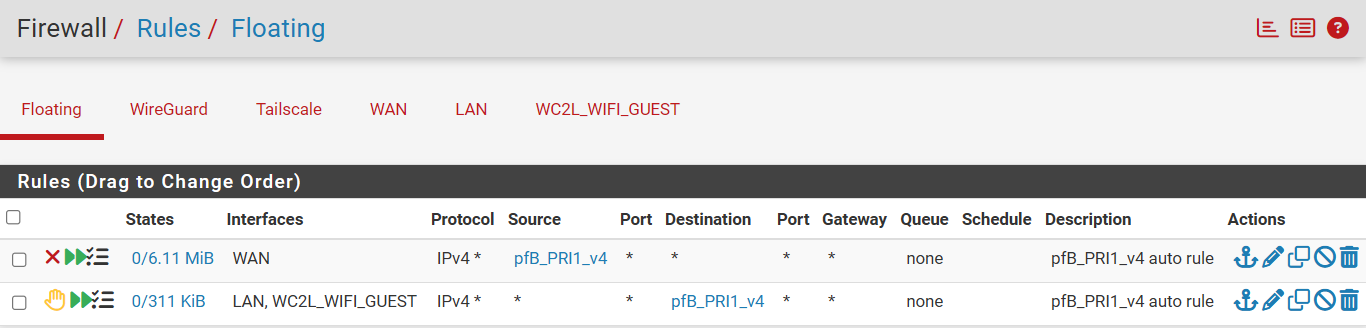
I don't remember changing or why changed the GeoIP Stuff
Now I have switched it back.
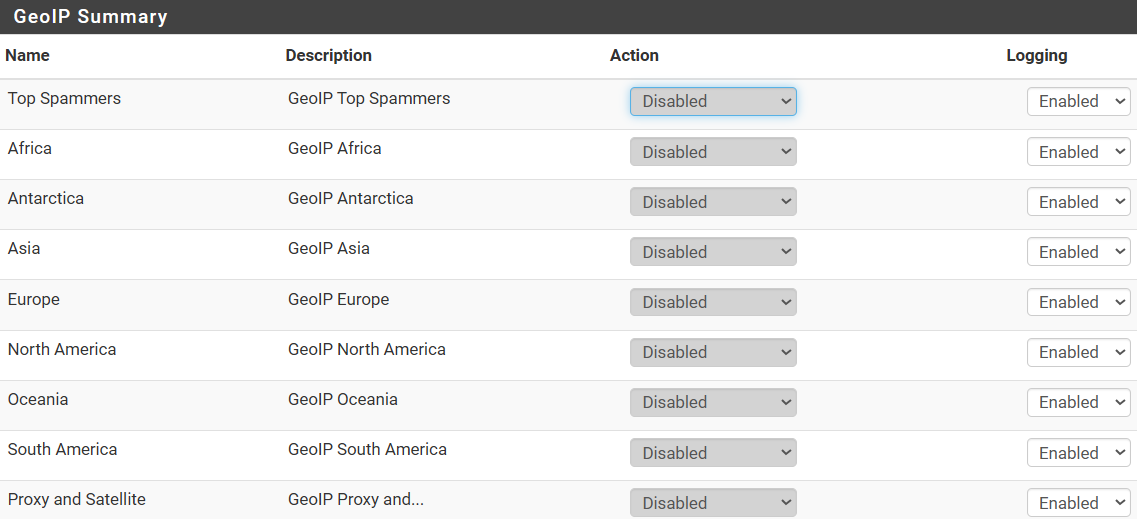
Now to chase down the DNSBL & Maxmind issues.
When I run the command: nslookup www.marrketstrategy.com
The results are:
Server: one.one.one.one
Address: 1.1.1.1
Non-authoritative answer:
Name: marrketstrategy.com
Address: 209.38.99.34
Aliases: www.marrketstrategy.com[ MaxMind_BD_Proxy_v4 ] Downloading update .. 403 Forbidden
[ pfB_PRI3_v4 - MaxMind_BD_Proxy_v4 ] Download FAIL
DNSBL, Firewall, and IDS (Legacy mode only) are not blocking download.
The Following List has been REMOVED [ MaxMind_BD_Proxy_v4 ] -
It looks like Doh is being utilized. Maybe in your DNS settings or in your web browser.
My result using resolver
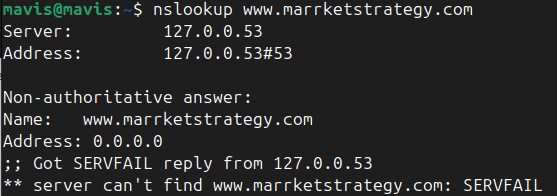
Look here for some insight into firefox Doh: https://forum.netgate.com/topic/133679/heads-up-be-aware-of-trusted-recursive-resolver-trr-in-firefox
-
@Uglybrian
I wasn't using Firefox.
That was just a PS terminal.. I will reread stuff.So what are you using for DNS servers? ISP?
Do you point your clients to your Netgate device?
Maybe that is what has changed in mine?? -
@wc2l said in pfBlockerNG not blocking ADs:
When I run the command: nslookup www.marrketstrategy.com
The results are:
Server: one.one.one.one
Address: 1.1.1.1
Non-authoritative answer:
Name: marrketstrategy.com
Address: 209.38.99.34
Aliases: www.marrketstrategy.comLol.
You control your pfSense, you can install things like pfBlockerng and do all kind of nifty DNS trick ...
And then some one decides that your LAN devices should use 1.1.1.1 as their DNS (1.1.1.1 is not pfSense) thus totally bypassing your DNS, so pfBlocker would never be able to see, and act upon your DNS request (from this LAN device).
Go call 1.1.1.1 and ask if they can install pfBlockerng on their system for you ?
(ok, was joking )You can also remove this one :
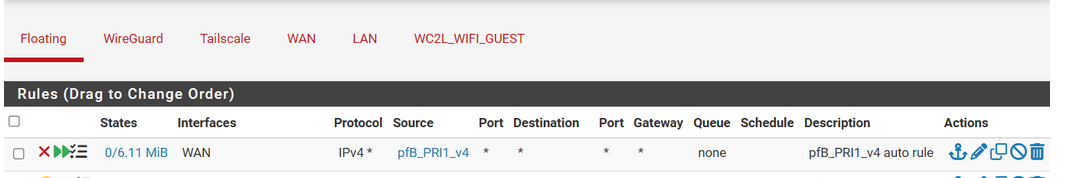
as this floating rule operates on WAN, traffic coming from the alias IP list "pfB_PRI_v4".
All these IPs will be blocked anyway. You should lose any CPU cycles on them. -
I am using the authoritative name servers directly via the PF Sense resolver. Instead of asking Google or my ISP and having them answer either by their cache or them asking the name servers for me. I just use PFS to go to the name servers directly.PFS will answer from its cash or ask the name servers. I have no other typed in DNS servers And all clients point to PFS for their DNS. In addition, I also have firewall rules blocking all known Doh servers along one rule blocking the Dot port.
And all web browsers have an option for Doh usage that is usually switched on by default. You have to go into the browser settings and manually turn it off. This is not just on Firefox, but every web browser. -
@Uglybrian
I made sure there was nothing being added to my DHCP server, I need to figure out what is happening. Maybe I will open a ticket and see if that can help. Something is amiss...pfBlockerNG update is still giving me errors not matter what I do. I will go back and look again. Still getting the ADs in one of the pages that used to be blocked :-(
-
Does your resolver settings look like this?
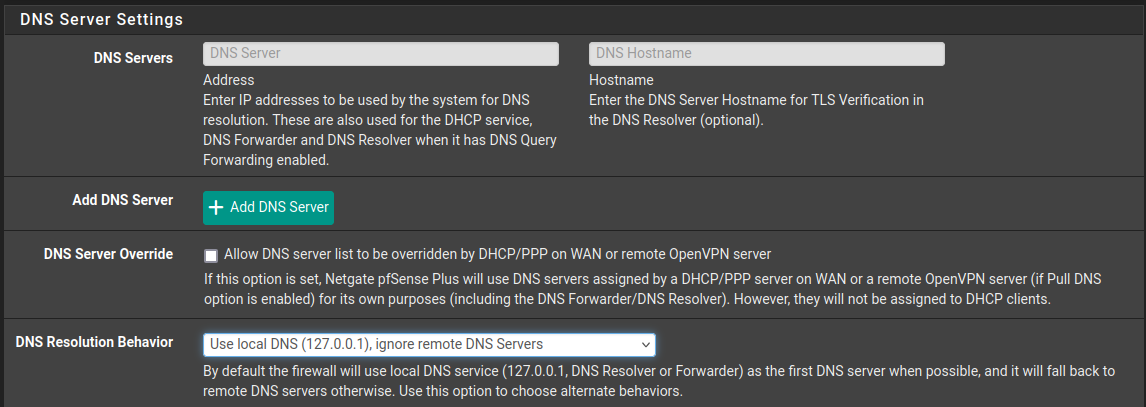
From what I see you have something on your network using Cloudflare DNS, thus bypassing PFBlocker as Gertjan has pointed out.
I also use this firewall rule found in the PFS configuration recipes
https://docs.netgate.com/pfsense/en/latest/recipes/dns-block-external.htmlAnother layer I have is a floating firewall rule blocking DOH servers in the outbound direction.
-
@Uglybrian
Took me a bit to figure where "DNS Resolution Behavior" was.. Mine was to "fall back to remote". I may have to clear cache and few other things. I need to look at the other settings yet. -
@wc2l said in pfBlockerNG not blocking ADs:
I made sure there was nothing being added to my DHCP server, I need to figure out what is happening. Maybe I will open a ticket and see if that can help. Something is amiss...
On a device on your LAN :
When I run the command: nslookup www.marrketstrategy.com The results are: Server: one.one.one.one Address: 1.1.1.1so that device uses 1.1.1.1 as it DNS source.
1.1.1.1 can come from two sources :- The device user has set up the device with static DNS parameters, he entered 1.1.1.1.
- It was given by the pfSense (?) DHCP server. So the admin has set that "1.1.1.1" as the DNS to be given to the LAN DHCP clients.
For both reasons, there is no need to open a ticket

You said that 2) isn't possible, so you have to deal with device's owner.
Or use a firewall rule ^^
"On LAN, block all DNS requests that are not directed to pfSense" and bye bye the 1.1.1.1 issue.The owner of the device will ask for you very soon, and a discussion will take place.
He wants to circumvent your pfSense DNS.
You want his DNS requests to go to to pfSense, so you can filter it with pfBlockerng.As the device's user is using your network, you will win. The discussion will end with : "if not happy, go elsewhere" as you can decides what happens on your network.
-
@Gertjan
Looks like the issue is resolved. changing from "fall back to remote" to "ignore remote". I also made sure that there was NO other references for external DNS servers.I've also been working on making sure that all of the downloads are working. I have found that some have changed policies or paths.
THANK YOU!