packet log being generated?
-
This works fine. Just tested in my virtual environment. Did you restart Suricata on the interface after making the configuration change? Any changes made under INTERFACE SETTINGS generally require a Suricata restart on the interface so that the running binary can become aware of the config change.
Here are two screenshots from my quick test this morning. I enabled Packet Logging and then used a Kali Linux VM to port scan a pfSense 2.7.2 CE VM. That generated alerts that were captured as shown below.
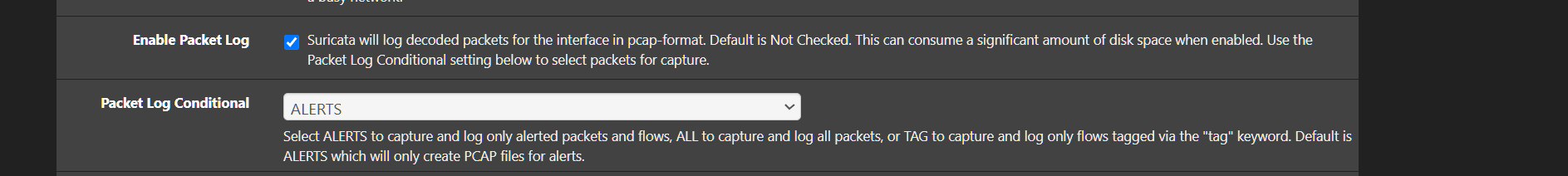
First, enable the Packet Log option by checking the box on the INTERFACE SETTINGS tab:
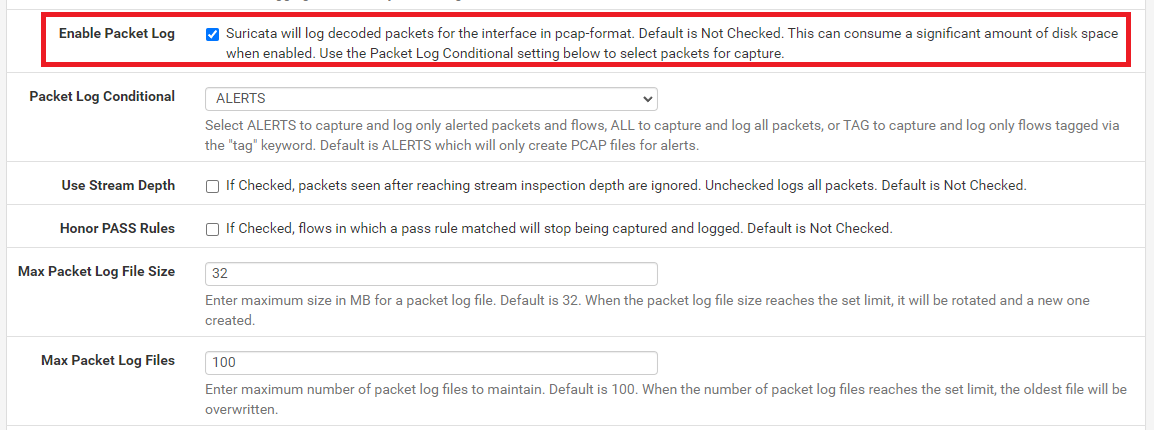
Restart Suricata on the interface and then either wait for alerts or generate them purposefully. Check the Suricata interface logging directory under
/var/log/suricata/. Each PCAP file is suffixed with a UNIX timestamp corresponding to the time the file was created. The options for Max Packet Log File Size and Max Packet Log Files determine how large each PCAP file is allowed to grow until a new one is started, and how many total PCAP files are allowed to accumulate in the PCAP logging directory: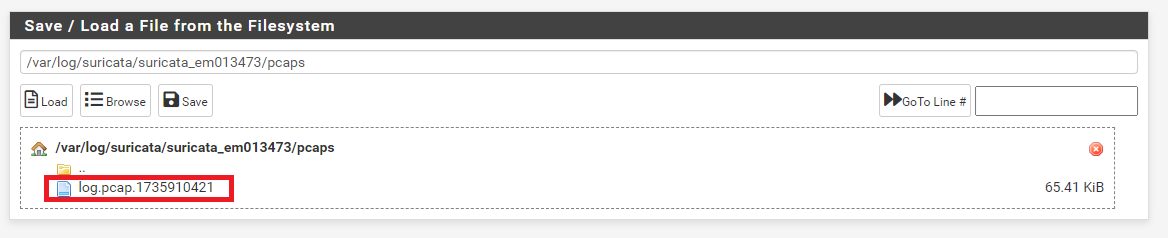
Notice there are several options related to packet logging that automatically unhide in the GUI when you enable PCAP file generation.
You can also independently enable packet logging/capture in the EVE JSON options. That will capture the packet data within an EVE JSON record that can then be digested by third-party EVE JSON collectors/analysis engines.
Just be aware that packet logging will consume a ton of disk space very quickly on a busy network.
-
@bmeeks Restarting Suricata was exactly what was needed so thank you for that.
I do have suggestions please let me know if its possible.
-
Provide a message under the settings tab that indicates "any changes here require restarting Suricata"
-
Provide an Export button to get the pcap out of the system in a more direct way. Right now the flow would require either ssh to the firewall and scp the file out to another system or through the GUI which is cumbersome i find.
I appreciate the added color about packet logging. The rules in place have been fine tuned to the best of what we can. So far any alerts generated are actionable. The key is to not run Suricata on Internet bound flows. Between datacenters is best as that's less likely to be encrypted (think mysqql for example).
-
-
@michmoor said in packet log being generated?:
I do have suggestions please let me know if its possible.
Provide a message under the settings tab that indicates "any changes here require restarting Suricata"
Provide an Export button to get the pcap out of the system in a more direct way. Right now the flow would require either ssh to the firewall and scp the file out to another system or through the GUI which is cumbersome i find.
Anything is possible and Pull Requests are always welcomed at https://github.com/pfsense/FreeBSD-ports/tree/devel/security/pfSense-pkg-suricata
 .
. -
@bmeeks Lets crack open this C++ for dummies book. haha
-
@michmoor said in packet log being generated?:
@bmeeks Lets crack open this C++ for dummies book. haha
Only need PHP for the GUI stuff.
-
@bmeeks all jokes aside. i think i may be able to chatGPT my way through it. I'll give it a shot.
Any pointers as to where to start? How do i look through the code and say "ok this is where i put my code " -
@michmoor said in packet log being generated?:
@bmeeks all jokes aside. i think i may be able to chatGPT my way through it. I'll give it a shot.
Any pointers as to where to start? How do i look through the code and say "ok this is where i put my code "The restart warning message is a simple addition to the existing INTERFACE SETTINGS tab code in
suricata_interfaces_edit.php.Creating something to export PCAP files would best be done with a completely new tab and associated PHP code. There's not existing functionality that you could logically tack that feature onto. You could model the new code page on the code Viktor Gurov wrote for the File Store tab a couple of years ago.
-
Should i add the following to the top of the code in the PHP file but below the initial comments?
<div style="background-color: #ffcc00; color: #000; padding: 10px; text-align: center; font-weight: bold; border: 1px solid #ffa500; margin-bottom: 20px;"> Any changes to the settings below will require a restart of the package. </div> -
@michmoor said in packet log being generated?:
Should i add the following to the top of the code in the PHP file but below the initial comments?
<div style="background-color: #ffcc00; color: #000; padding: 10px; text-align: center; font-weight: bold; border: 1px solid #ffa500; margin-bottom: 20px;"> Any changes to the settings below will require a restart of the package. </div>No, that will break the entire page and mess up the pfSense header and footer rendering. You will need to examine the existing PHP code files and learn by example. You can experiment in a VM running pfSense. If you have never programmed in PHP, and in particular within the pfSense PHP GUI environment, you need to take some time to learn the basics before jumping in and making changes.
-
@bmeeks said in packet log being generated?:
You will need to examine the existing PHP code files and learn by example
Thought so. @michmoor, you need the other book.
Click the image.
edit : or this one.